FSSLA: A Fuzzy-based scheme for slice service level agreement in 5G wireless networks and its performance evaluation
Abstract
The Software-Defined Network (SDN) with Network Slicing will be a good approach for admission control in the Fifth Generation (5G) wireless network, which is planned to be adaptable to meet user requirements. The system’s resources are limited, and the number of devices is growing much faster than it can handle. So, the overloading problem will be a very critical problem. To deal with these problems, this paper presents a Fuzzy-based Scheme for Service Level Agreement (SLA) evaluation (FSSLA). We compare two models: FSSLA1 and FSSLA2. The FSSLA1 considers three input parameters: Reliability (Re), Availability (Av), Latency (La) and the output parameter is SLA. In FSSLA2, we consider Traffic Load (Tl) as a new parameter. From simulation results, we conclude that the considered parameters have different effects on the SLA. When Re and Av are increasing, the SLA parameter is increased but when La and Tl are increasing, the SLA parameter is decreased. When the Tl value is changed from 20% to 80%, the SLA is decreased by 16.62% when Re 10%, Av 90% and the La value is 1 ms. When the Re is increased from 10% to 90% and 50% to 90% and the Tl value is 50%, the Av is 50% and the La is 1 ms, the SLA is increased by 22.76% and 11.38%, respectively.
1.Introduction
By the advancement of wireless technology, the customer demands for services, have rapidly increased. There will be billions of additional devices with irregular traffic patterns and enormous data rates. With the emergence of the Internet of Things (IoT), these devices will create significant volumes of data for the Internet, increasing network congestion and lowering the Quality of Service (QoS). Therefore, the Fifth Generation (5G) network should be good and capable of meeting users requirements [7,11,14,29,31]. It also can be used to fulfill the demand of several industries, including medicine, automotive, education, media, manufacturing, and transportation.
Fig. 1.
The key challenges of 5G.
In comparison to 4G, the 5G network is expected to surpass 4G. The key challenges of 5G are illustrated in Fig. 1, which have been required to include better spectrum efficiency, reduced latency, low consumption, high data rate, capacity and throughput improvement. For example, peak data rates for 5G are likely to exceed 20 Gbps [13]. Furthermore, the 5G network will provide customers new experiences such as Ultra High Definition Television (UHDT) on the Internet [30], but also support a large number of IoT devices with long battery life and high data rates in high-density hotspot [12].
The 5G is developing by considering three different usage scenarios which have been identified as enhanced mobile broadband (eMBB), ultra-reliable & low latency communications (URLLC) and massive type communication (mMTC) [1,33,37]. The eMBB is related to human-essential and has greater accessibility to multi-media content and services by enhancing seamless Quality of Experience (QoE). The URLLC can efficiently reduce the latency and enhance reliability. The mMTC can accommodate a large number of connected devices while maintaining a long battery life. In order to give a nice experience for consumers, routing and switching technologies have also been changed, and 5G technology’s coverage area is shorter than 4G [10,12,14,19].
The traditional IP networks are complicated and difficult to maintain, therefore network administrators must identify and develop new approaches to improve network performance. The Software-defined Networking (SDN) is a new networking paradigm that decouples the data plane from the control plane in the network and facilitates (logical) network control by allowing users to program the network. As a result, the SDN can improve system administration and processing performance [22]. As an example, the mobile handover mechanism with SDN can be used for reducing the delay in handover processing and improve the QoS [19,23,27,36].
Network Slicing is a new technology that leverages SDN and Network Function Virtualization (NFV) to create various services over the same physical network to fulfill the customers’ different QoS requirements [38]. A slice is a group of network resources that have been chosen to fit the demands of the services. By slicing a physical network into numerous logical networks, it is possible to provide on-demand tailored dependable service in a network with limited resources. Because multiple slices with varied priority values can satisfy diverse traffic requirements, users in the 5G system will have a better QoS than users in the 4G system [17,21,31,38].
In our previous work [2–5], we presented a Fuzzy-based system for admission decision considering four input parameters: Quality of service (QoS), Slice Priority (SP), Service Level Agreement (SLA) and Slice Overloading Cost (SOC). The output parameter was Admission Decision (AD). In this paper, we present two models for SLA: FSSLA1 and FSSLA2. The FSSLA1 considers three input parameters: Reliability (Re), Availability (Av), Latency (La) and the output parameter is SLA. In FSSLA2, we consider Traffic Load (Tl) as a new parameter.
The rest of the paper is organized as follows. In Section 2 is presented an overview of SDN. In Section 3 is presented the network slicing enabling SDN technology. In Section 4, we present application of Fuzzy Logic for admission control. In Section 5, we describe the proposed Fuzzy-based scheme and its implementation. In Section 6, we explain the simulation results. Finally, conclusions and future work are presented in Section 7.
Fig. 2.
The comparison of traditional network and SDN.
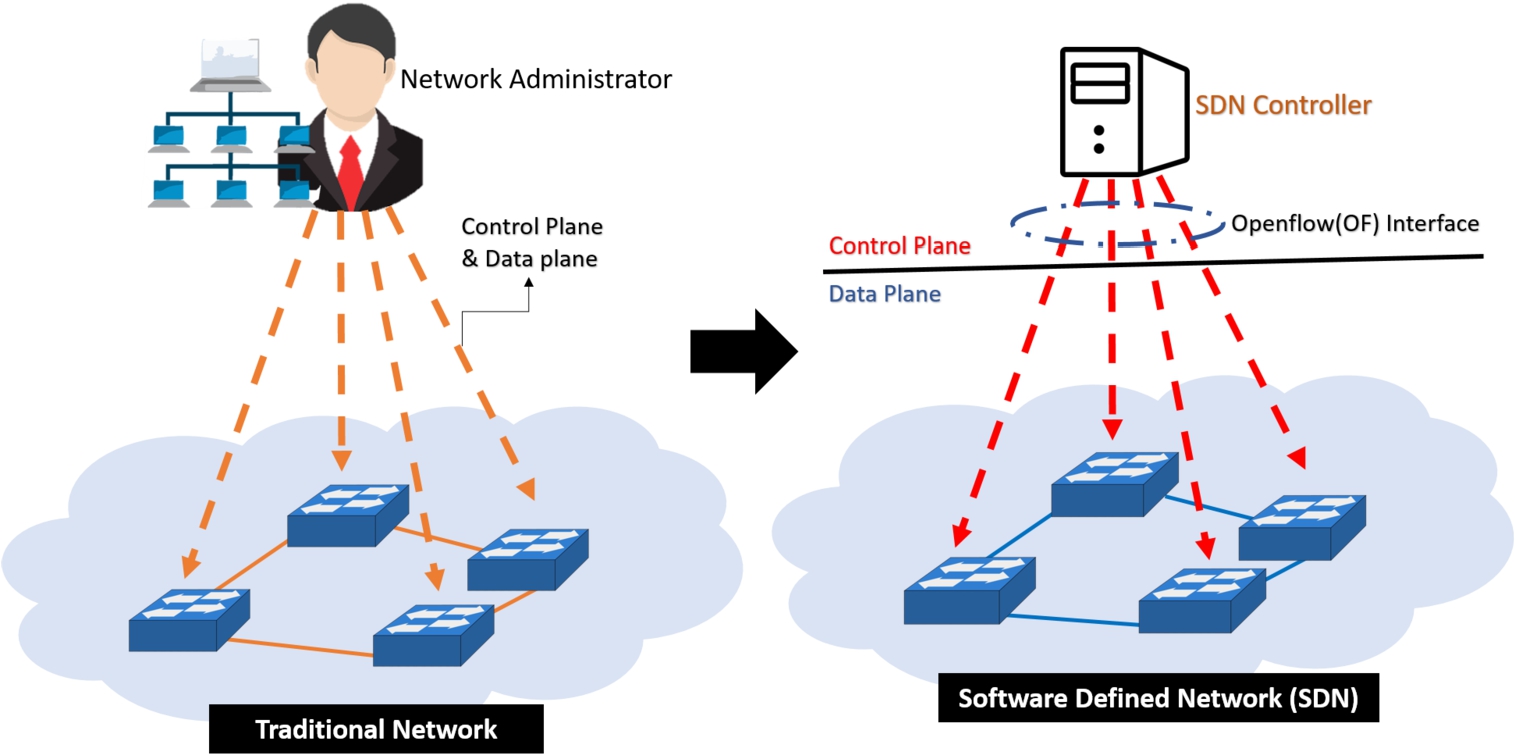
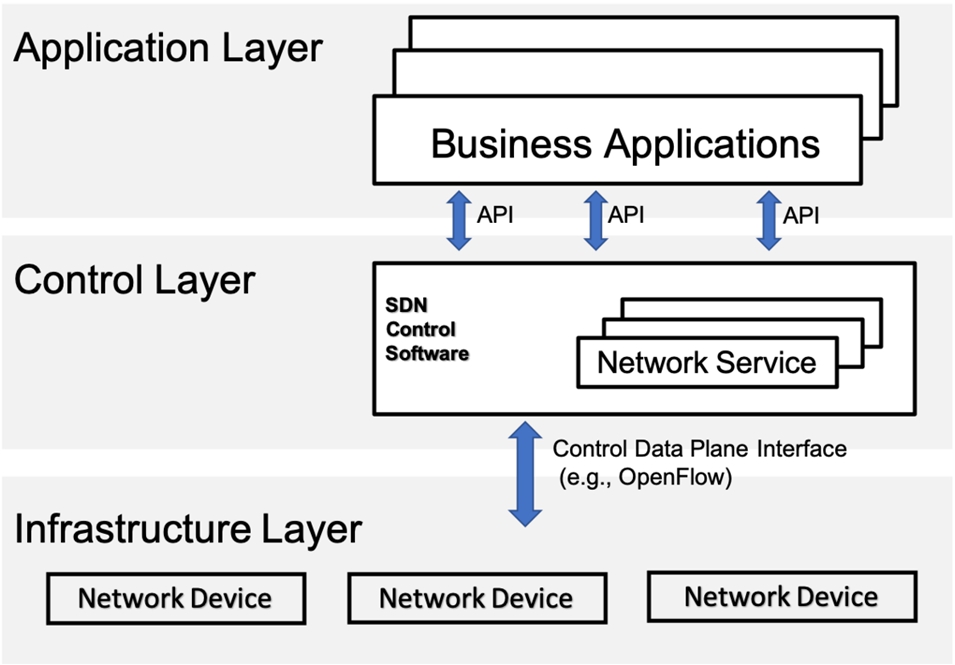
Fig. 3.
Structure of SDN.
2.Software-defined networks (SDNs)
The SDN is a new networking paradigm that decouples the data plane from control plane in the network and promotes (logical) centralization of network control that have ability to program the network. This separation can be flexible and centralized management with a global view of entire network. In Fig. 2 is shown the traditional network and SDN approaches. The traditional networks are hard to manage and control since they rely on physical infrastructure. It is difficult to configure the network according to predefined policies and to reconfigure it to respond to faults, load, and changes because the processes must be based on the setting of each device and making controlling and operation on each device. In contrast, SDN creates virtualized control plane with intelligent management decisions, when network administrators can control and reconfigure the overall network by managing on virtualized controller. Thus, the SDN is easy to manage and provide network software-based services from a centralized control plane. The SDN control plane is managed by SDN controller or cooperating group of SDN controllers. The SDN structure is shown in Fig. 3 [8,24,25,28].
Application Layer builds an abstracted view of the network by collecting information from the controller for decision-making purposes. The types of applications are related to network configuration and management, network monitoring, network troubleshooting, network policies and security.
Northbound Interfaces allow communication between the control layer and the application layer and can provide a lot of possibilities for networking programming. It will pass commands and information to the control layer and make the controller creates the best possible software network with suitable qualities of service and acceptable security.
Control Layer receives instructions or requirements from the Application Layer. It contains the controllers that control the data plane and forward the different types of rules and policies to the infrastructure layer through the Southbound interfaces.
Southbound Interfaces allow connection and interaction between the control plane and the data plane. The southbound interface is defined as protocols that allow the controller to create policies for the forwarding plane.
Infrastructure Layer receives orders from SDN controller and sends data among them. This layer represents the forwarding devices on the network such as routers, switches and load balancers.
The SDN can manage the network while enabling new services. In congestion traffic situation, the management system can be flexible, allowing users to easily control and adapt resources appropriately throughout the control plane. Mobility management is easier and quicker in forwarding across different wireless technologies (e.g.5G, 4G, Wifi and Wimax). Also, the handover procedure is simple and the delay can be decreased [34]. But, when the administrator wants to implement SDN protocol and SDN controller, the entire network infrastructure needs to be changed. If the SDN controller fails, the entire system also fails.
3.5G network slicing enabling SDN technology
The network slicing is a technique that divides a single virtualized infrastructure into several virtual end-to-end networks, referred to as “Slices”, that are configured into virtualized functions to adapt to the user’s demands. Each slice is conceptually distinct and has no impact on the other virtual logical networks [6,9,18].
Fig. 4.
ONF SDN network slicing architecture.
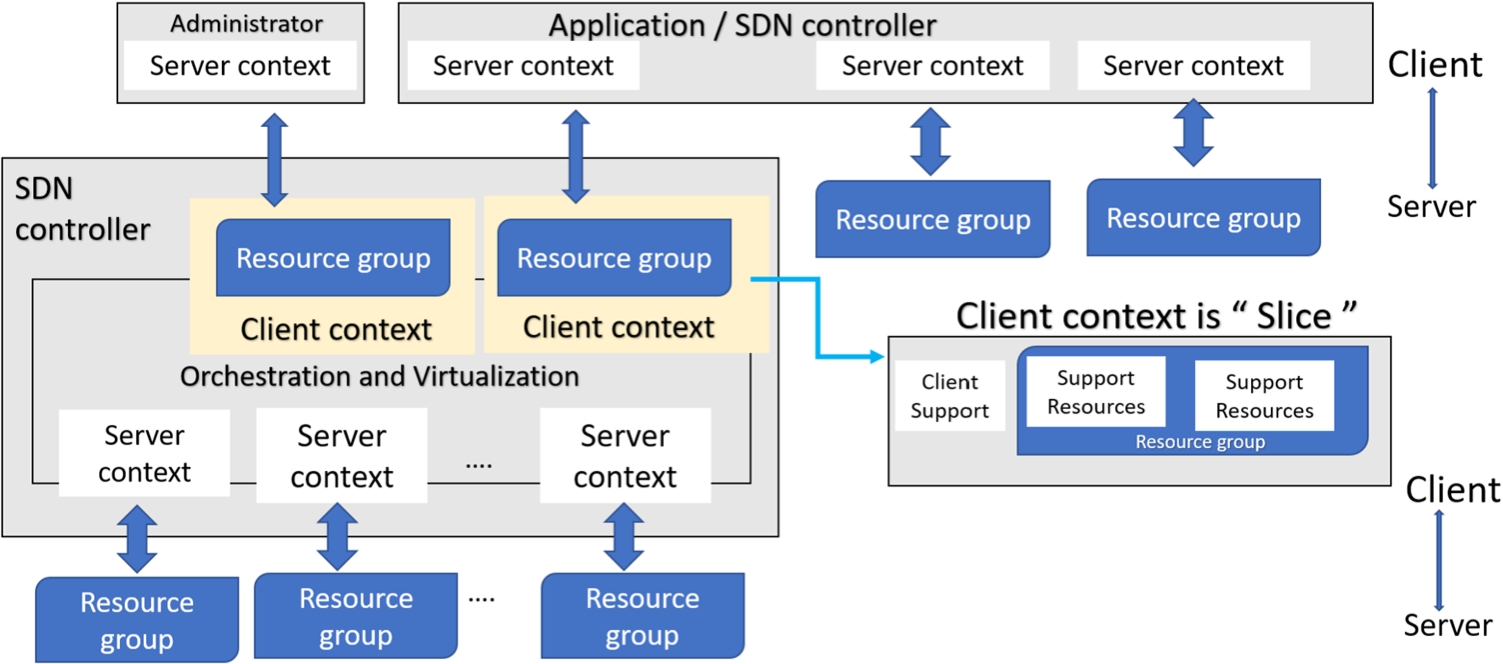
The SDN network slicing architecture is provided by the Open Network Foundation (ONF). In SDN network environment, the main components of SDN architecture are resources and control. In Fig. 4, the SDN controller dynamically manages network slice by using a set of policies and grouping slices that belong to the same context [32]. The ONF SDN network slicing architecture has the following components.
Client context: It has all information that the controller needs to communicate with a client. The components of client context are client support and virtual resources for responding to end user’s requests.
∗ Client support: It contains support information of client operation.
∗ Resource group: It contains the customized view of all resources that the controller offers to client based on service demands and facility.
Server context: It has all information that the controller needs to interact with a set of underlying resources.
Administrator: The administrator configures all controllers, servers and client context including installation of their associated policies.
Application/SDN controller: This controller can control the slice by using server context.
4.Outline of fuzzy logic
A Fuzzy Logic (FL) system is a nonlinear mapping of an input data vector into a scalar output, which is able to simultaneously handle numerical data and linguistic knowledge. The FL can deal with statements which may be true, false or intermediate truth-value. These statements are impossible to quantify using traditional mathematics. The FL system is used in many controlling applications such as aircraft control (Rockwell Corp.), Sendai subway operation (Hitachi), and TV picture adjustment (Sony) [16,26,35].
Fig. 5.
FLC structure.
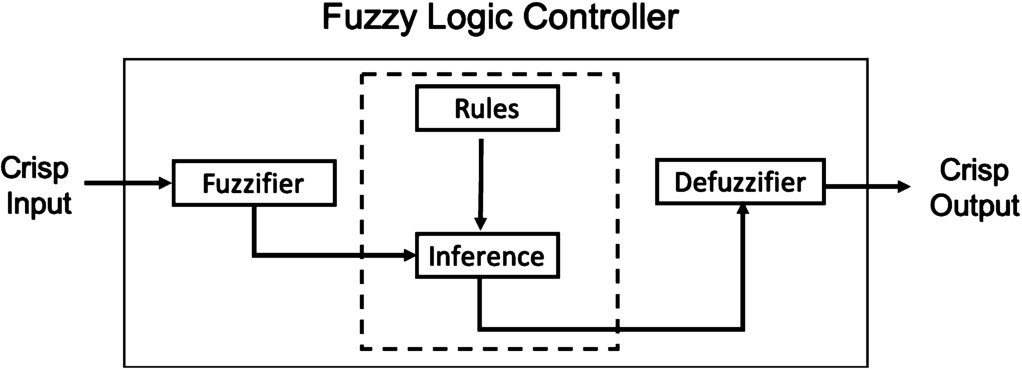
Fig. 6.
Operation of a fuzzy controller.
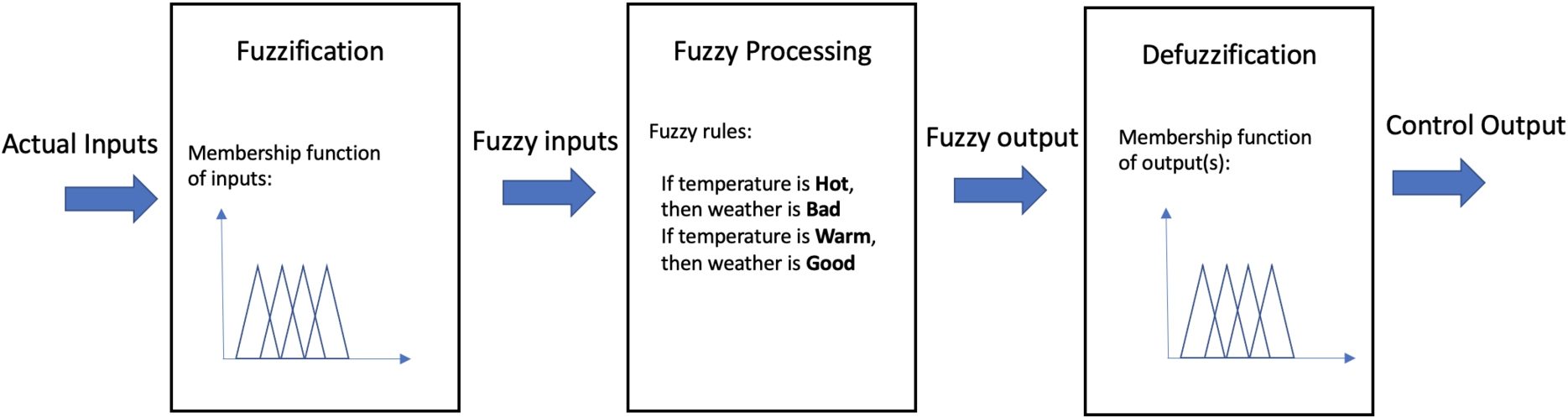
In Fig. 5 is shown Fuzzy Logic Controller (FLC) structure, which contains four components: fuzzifier, inference engine, fuzzy rule base and defuzzifier. In Fig. 6 is shown the operation of the fuzzy controller. In the first step, the Fuzzification fuzzified the actual inputs to obtain fuzzy inputs. Then, Fuzzy Processing will process fuzzy inputs according to the rules set and produces fuzzy outputs. Finally, the Defuzzification produces a crisp real value from fuzzified inputs for control output.
Fuzzifier is needed for combining the crisp values with rules which are linguistic variables and have fuzzy sets associated with them.
The Rules may be provided by on expert or can be extracted from numerical data. In engineering case, the rules are expressed as a collection of IF-THEN statements.
The Inference Engine infers fuzzy output by considering fuzzified input values and fuzzy rules.
The Defuzzifier maps output set into crisp numbers.
4.1.Linguistic variables
A concept that plays a central role in the application of FL is that of a linguistic variable. The linguistic variables may be viewed as a form of data compression. One linguistic variable may represent many numerical variables. It is suggestive to refer to this form of data compression as granulation.
The same effect can be achieved by conventional quantization, but in the case of quantization, the values are intervals, whereas in the case of granulation the values are overlapping fuzzy sets. The advantages of granulation over quantization are as follows:
it is more general;
it mimics the way in which humans interpret linguistic values;
the transition from one linguistic value to a contiguous linguistic value is gradual rather than abrupt, resulting in continuity and robustness.
For example, let Temperature (T) be interpreted as a linguistic variable. It can be decomposed into a set of Terms: T (Temperature) = {Freezing, Cold, Warm, Hot, Blazing}. Each term is characterised by fuzzy sets which can be interpreted, for instance, “freezing” as a temperature below 0°C, “Cold” as a temperature close to 10°C.
4.2.Fuzzy control rules
IF x is S THEN y is T is a standard formula for fuzzy control rules, where x and y are linguistic variables that are expressed by S and T, which are fuzzy sets. The control (input) variable is x, while the solution (output) variable is y. Fuzzy control rule is the name of this regulation. A conditional sentence is one that has the form “IF... THEN”. It is comprised of two parts: the antecedent “IF” and the consequent “THEN”.
Table 1
The canonical form for a fuzzy rule-based system
| Rule 1: | IF condition |
| Rule 2: | IF condition |
| ⋮ | ⋮ |
| Rule r: | IF condition |
In Table 1 are showing several simple canonical rules from decomposing and reducing any compound rule structure. These rules are based on natural language representations and models, which are represented based on fuzzy sets and FL. The fuzzy level of understanding and describing a complex system is expressed from the form of a set of restrictions on the output with the condition of the input (
4.3.Defuzzification methods
There are many defuzzification methods as follows:
The Centroid Method;
Tsukamoto’s Defuzzification Method;
The Center of Are (COA) Method;
The Mean of Maximum (MOM) Method;
Defuzzification when Output of Rules are Function of Their Inputs.
Fig. 7.
Proposed system overview.
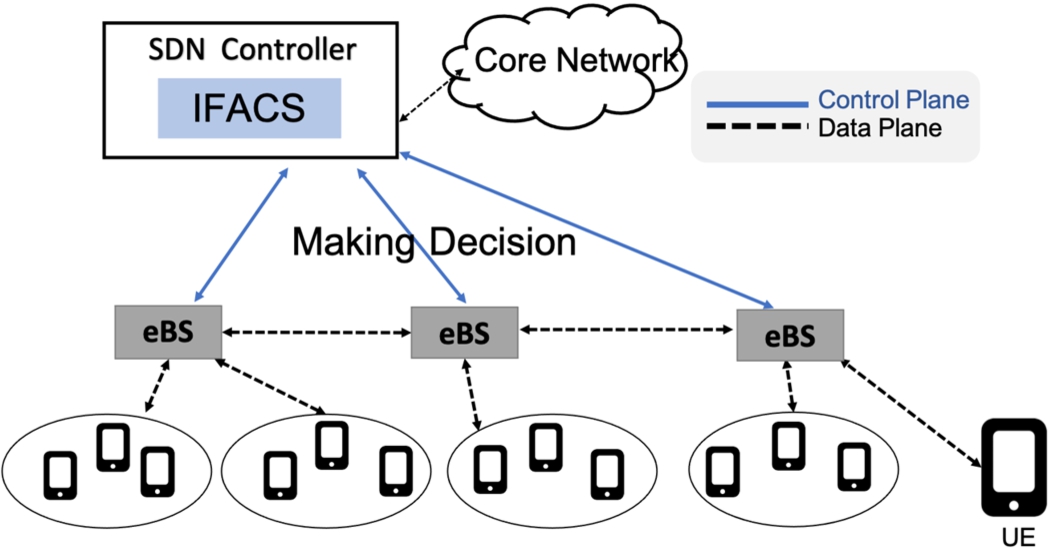
Fig. 8.
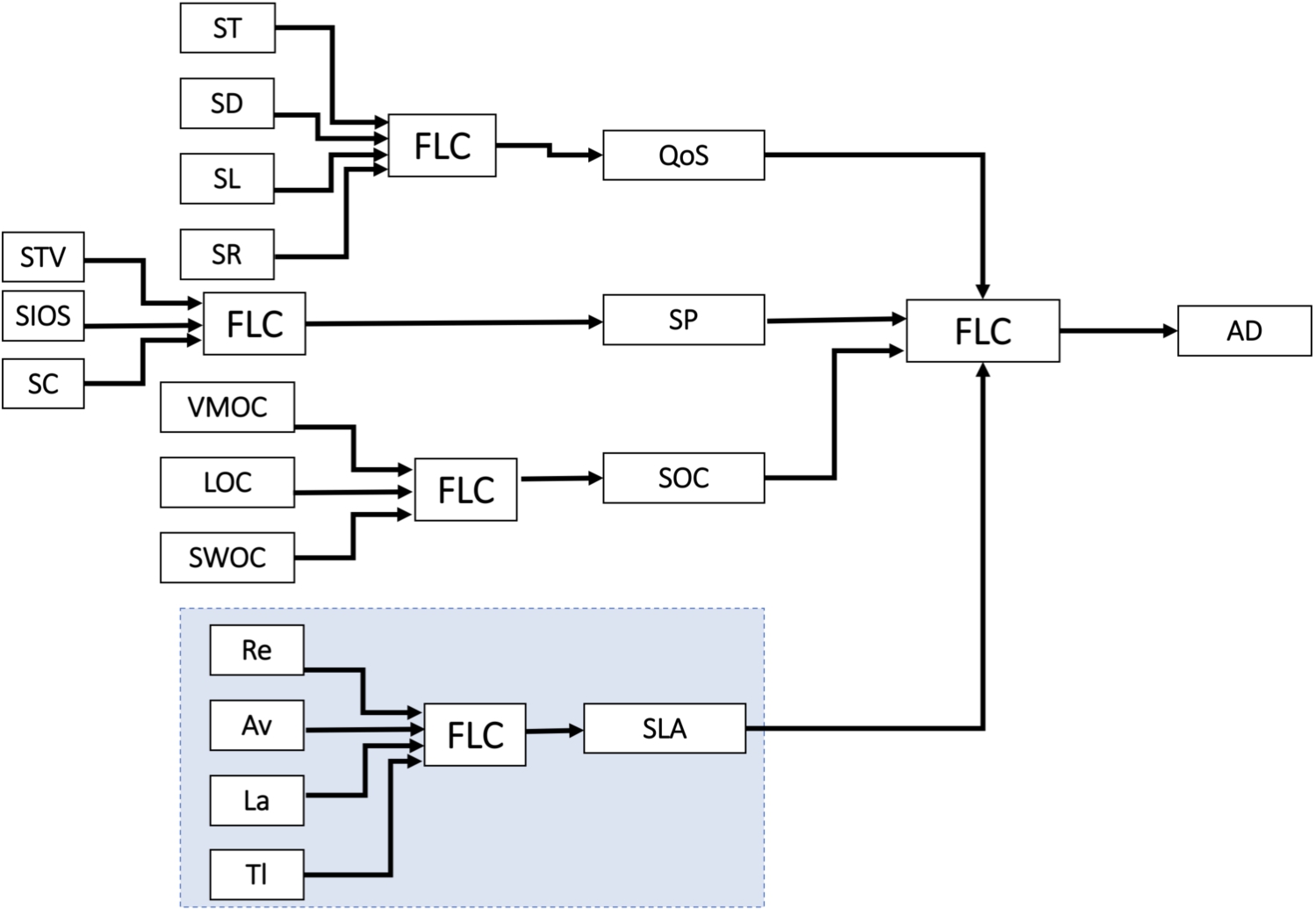
Proposed system structure.
5.Proposed Fuzzy-based scheme
In this work, we use FL to implement the proposed system. In Fig. 7, we show the overview of our proposed system. Each evolve Base Station (eBS) will receive controlling order from SDN controller and they can communicate and send data with User Equipment (UE). On the other hand, the SDN controller will collect all the data about network traffic status and controlling eBS by using the proposed Fuzzy-based system. The SDN controller will be a communicating bridge between eBS and 5G core network. The proposed system is called Integrated Fuzzy-based Admission Control System (IFACS) in 5G wireless networks. The structure of IFACS is shown in Fig. 8. For the implementation of our system, we consider four input parameters: Quality of Service (QoS), Slice Priority (SP), Slice Overloading Cost (SOC), Service Level Agreement (SLA) and the output parameter is Admission Decision (AD). We applied FL to evaluate QoS, SP, SOC and SLA. The QoS is considering four parameters: Slice Throughput (ST), Slice Delay (SD), Slice Loss (SL) and Slice Reliability (SR). The SP is considering three parameters: Slice Traffic Volume (STV), Slice Interference from Other Slices (SIOS) and Slice Connectivity (SC). The SOC is considering three parameters: Virtual Machine Overloading Cost (VMOC), Link Overloading Cost (LOC) and Switches Overloading Cost (SWOC).
In this paper, we propose a Fuzzy-based Scheme for SLA evaluation (FSSLA). The structure of FSSLA is shown in Fig. 8. We compare two models: FSSLA1 and FSSLA2. The FSSLA1 considers three input parameters: Reliability (Re), Availability (Av), Latency (La) and the output parameter is SLA. In FSSLA2, we consider Traffic Load (Tl) as a new parameter.
Reliability (Re): | The Re value is the required user reliability. When Re value is high, the SLA is high. |
Availability (Av): | The Av is the required user availability. When Av value is high, the SLA is high. |
Latency (La): | The La is the required user latency. When La value is high, the SLA is low. |
Traffic Load (Tl): | The Tl is the total traffic of users in a slice. When Tl value is high, the SLA is low. |
Service Level Agreement (SLA): | The SLA is described based on these four parameters. The user request is characterized by its required SLA. |
Fig. 9.
Membership functions.
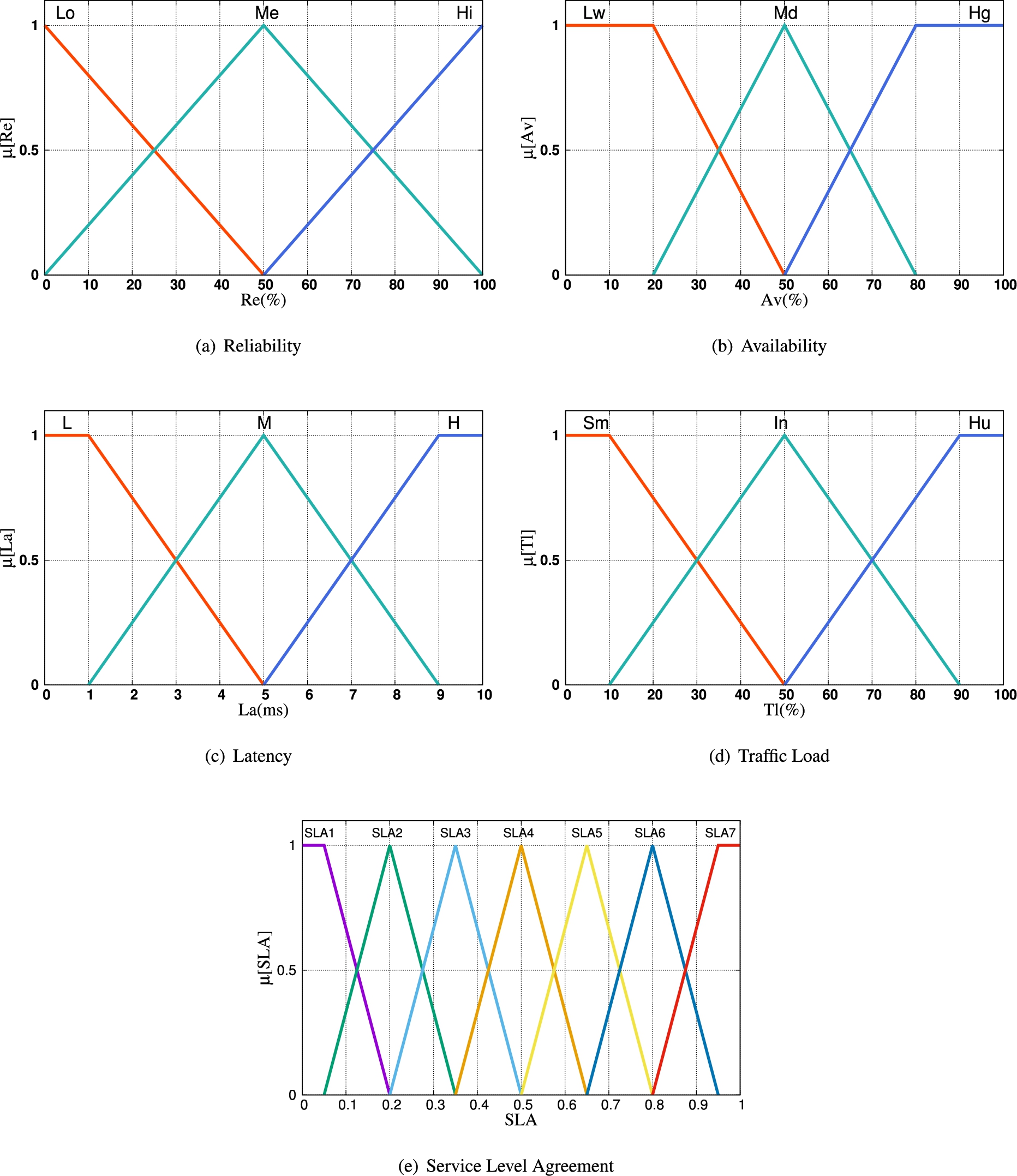
Fig. 10.
Triangular and trapezoidal membership functions.
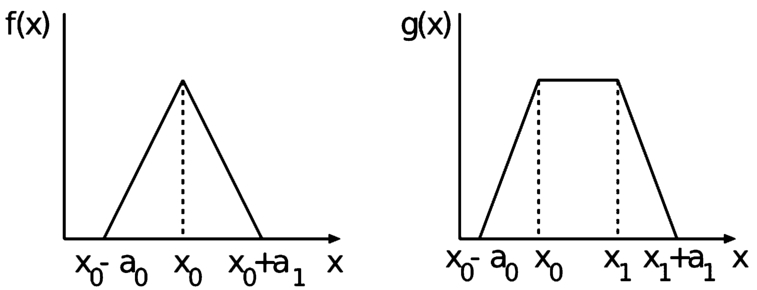
The membership functions are shown in Fig. 9. The proposed fuzzy system can be used for different applications. We consider the values of Reliability, Availability and Traffic Load from 0 to 100% in order to easily fuzzify them. In the case when we want to use the proposed system in a real scenario, we require from the applications the maximum value, which will be 100%. For the value of Latency, we consider the maximum value 10 ms based on the results shown in [20]. In this paper are shown the Latency values for different use cases: eMBB (5 ms to 10 ms), Massive IoT (10 ms) and Critical Communications (1 ms or 5 ms). We use triangular and trapezoidal membership functions as shown in Fig. 10 because they are more suitable for real-time operations. We explain the design of FLC in following.
We use three input parameters for FSSLA1 and four input parameters for FSSLA2:
Reliability (Re);
Availability (Av);
Latency (La);
Traffic Load (Tl).
The membership function for input parameters are defined as follows.
Table 2
Parameter and their term sets for FSSLA1 and FSSLA2
| Parameters | Term set |
| Reliability (Re) | Low (Lo), Medium (Me), High (Hi) |
| Availability (Av) | Low (Lw), Medium (Md), High (Hg) |
| Latency (La) | Low (L), Medium (M), High (H) |
| Traffic Load (Tl) | Small (Sm), Intermediate (In), Huge (Hu) |
| Service Level Agreement (SLA) | SLA1, SLA2, SLA3, SLA4, SLA5, SLA6, SLA7 |
Table 3
Fuzzy rule base for FSSLA1
| Rule | Re | Av | La | SLA |
| 1 | Lo | Lw | L | SLA3 |
| 2 | Lo | Lw | M | SLA2 |
| 3 | Lo | Lw | H | SLA1 |
| 4 | Lo | Md | L | SLA4 |
| 5 | Lo | Md | M | SLA3 |
| 6 | Lo | Md | H | SLA2 |
| 7 | Lo | Hg | L | SLA5 |
| 8 | Lo | Hg | M | SLA4 |
| 9 | Lo | Hg | H | SLA3 |
| 10 | Me | Lw | L | SLA4 |
| 11 | Me | Lw | M | SLA3 |
| 12 | Me | Lw | H | SLA2 |
| 13 | Me | Md | L | SLA5 |
| 14 | Me | Md | M | SLA4 |
| 15 | Me | Md | H | SLA3 |
| 16 | Me | Hg | L | SLA6 |
| 17 | Me | Hg | M | SLA5 |
| 18 | Me | Hg | H | SLA4 |
| 19 | Hi | Lw | L | SLA5 |
| 20 | Hi | Lw | M | SLA4 |
| 21 | Hi | Lw | H | SLA3 |
| 22 | Hi | Md | L | SLA6 |
| 23 | Hi | Md | M | SLA5 |
| 24 | Hi | Md | H | SLA4 |
| 25 | Hi | Hg | L | SLA7 |
| 26 | Hi | Hg | M | SLA6 |
| 27 | Hi | Hg | H | SLA5 |
Table 4
Fuzzy rule base for FSSLA2
| Rule | Re | Av | La | Tl | SLA | Rule | Re | Av | La | Tl | SLA |
| 1 | Lo | Lw | L | Sm | SLA4 | 41 | Me | Md | M | In | SLA4 |
| 2 | Lo | Lw | L | In | SLA3 | 42 | Me | Md | M | Hu | SLA3 |
| 3 | Lo | Lw | L | Hu | SLA2 | 43 | Me | Md | H | Sm | SLA4 |
| 4 | Lo | Lw | M | Sm | SLA3 | 44 | Me | Md | H | In | SLA4 |
| 5 | Lo | Lw | M | In | SLA2 | 45 | Me | Md | H | Hu | SLA2 |
| 6 | Lo | Lw | M | Hu | SLA1 | 46 | Me | Hg | L | Sm | SLA7 |
| 7 | Lo | Lw | H | Sm | SLA2 | 47 | Me | Hg | L | In | SLA6 |
| 8 | Lo | Lw | H | In | SLA1 | 48 | Me | Hg | L | Hu | SLA5 |
| 9 | Lo | Lw | H | Hu | SLA1 | 49 | Me | Hg | M | Sm | SLA6 |
| 10 | Lo | Md | L | Sm | SLA5 | 50 | Me | Hg | M | In | SLA5 |
| 11 | Lo | Md | L | In | SLA4 | 51 | Me | Hg | M | Hu | SLA4 |
| 12 | Lo | Md | L | Hu | SLA3 | 52 | Me | Hg | H | Sm | SLA5 |
| 13 | Lo | Md | M | Sm | SLA4 | 53 | Me | Hg | H | In | SLA4 |
| 14 | Lo | Md | M | In | SLA3 | 54 | Me | Hg | H | Hu | SLA3 |
| 15 | Lo | Md | M | Hu | SLA1 | 55 | Hi | Lw | L | Sm | SLA6 |
| 16 | Lo | Md | H | Sm | SLA3 | 56 | Hi | Lw | L | In | SLA5 |
| 17 | Lo | Md | H | In | SLA2 | 57 | Hi | Lw | L | Hu | SLA4 |
| 18 | Lo | Md | H | Hu | SLA1 | 58 | Hi | Lw | M | Sm | SLA5 |
| 19 | Lo | Hg | L | Sm | SLA6 | 59 | Hi | Lw | M | In | SLA4 |
| 20 | Lo | Hg | L | In | SLA5 | 60 | Hi | Lw | M | Hu | SLA3 |
| 21 | Lo | Hg | L | Hu | SLA4 | 61 | Hi | Lw | H | Sm | SLA4 |
| 22 | Lo | Hg | M | Sm | SLA5 | 62 | Hi | Lw | H | In | SLA3 |
| 23 | Lo | Hg | M | In | SLA4 | 63 | Hi | Lw | H | Hu | SLA2 |
| 24 | Lo | Hg | M | Hu | SLA3 | 64 | Hi | Md | L | Sm | SLA7 |
| 25 | Lo | Hg | H | Sm | SLA4 | 65 | Hi | Md | L | In | SLA6 |
| 26 | Lo | Hg | H | In | SLA3 | 66 | Hi | Md | L | Hu | SLA5 |
| 27 | Lo | Hg | H | Hu | SLA2 | 67 | Hi | Md | M | Sm | SLA6 |
| 28 | Me | Lw | L | Sm | SLA5 | 68 | Hi | Md | M | In | SLA5 |
| 29 | Me | Lw | L | In | SLA4 | 69 | Hi | Md | M | Hu | SLA4 |
| 30 | Me | Lw | L | Hu | SLA3 | 70 | Hi | Md | H | Sm | SLA5 |
| 31 | Me | Lw | M | Sm | SLA4 | 71 | Hi | Md | H | In | SLA4 |
| 32 | Me | Lw | M | In | SLA3 | 72 | Hi | Md | H | Hu | SLA3 |
| 33 | Me | Lw | M | Hu | SLA2 | 73 | Hi | Hg | L | Sm | SLA7 |
| 34 | Me | Lw | H | Sm | SLA3 | 74 | Hi | Hg | L | In | SLA7 |
| 35 | Me | Lw | H | In | SLA2 | 75 | Hi | Hg | L | Hu | SLA6 |
| 36 | Me | Lw | H | Hu | SLA1 | 76 | Hi | Hg | M | Sm | SLA7 |
| 37 | Me | Md | L | Sm | SLA6 | 77 | Hi | Hg | M | In | SLA6 |
| 38 | Me | Md | L | In | SLA5 | 78 | Hi | Hg | M | Hu | SLA5 |
| 39 | Me | Md | L | Hu | SLA4 | 79 | Hi | Hg | H | Sm | SLA6 |
| 40 | Me | Md | M | Sm | SLA5 | 80 | Hi | Hg | H | In | SLA5 |
| 81 | Hi | Hg | H | Hu | SLA4 |
The output linguistic parameter is Service Level Agreement (SLA).The term set for the output parameter SLA is defined as follows.
The membership functions for the output parameter SLA are defined as follows.
The Fuzzy Rule Base (FRB) for FSSLA1 and FSSLA2 is shown in Table 3 and Table 4, respectively. The FRB is formed by a fuzzy set of dimensions (
6.Simulation results
The simulation results are presented in this section. The simulations are run on a Linux Ubuntu OS computer with the following specifications: 8 GB RAM, i5 (3.2 GHz × 4) processor, and SSD (650 GB). We used our FuzzyC system that we had implemented for simulation. The FuzzyC simulation system is written in C and includes the Fuzzy library [15].
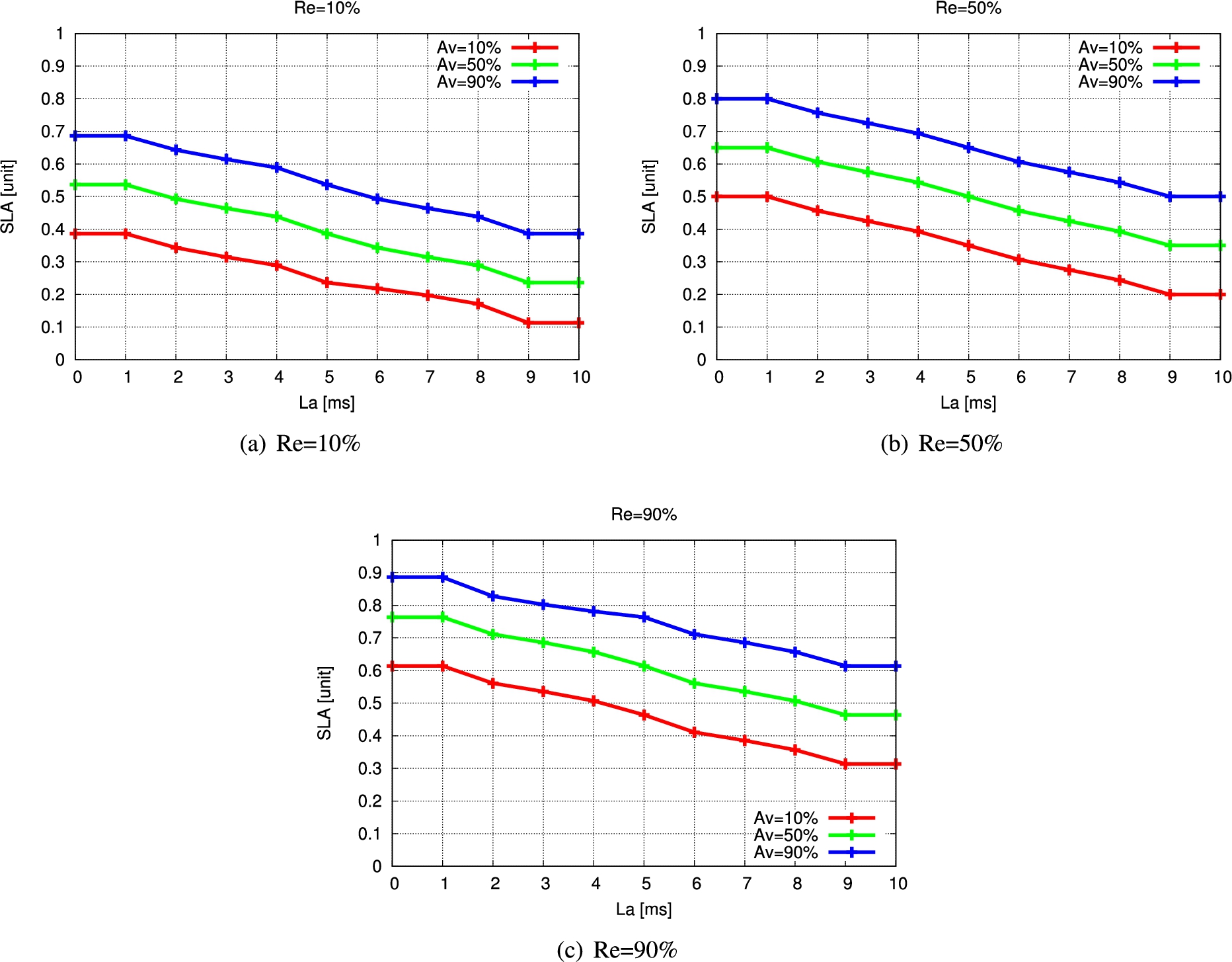
Figure 11(a), Fig. 11(b), and Fig. 11(c) illustrate the simulation results for FSSLA1. They represent the relationship between SLA and La. The Re and Av are considered as a constant parameters. We alter the Av value from 10% to 90%. We choose 10% for the Re value in Fig. 11(a). We can see that when La increases from 0 to 10 ms, the SLA decreases. When La is 5 ms, the SLA increases by 15% when Av increased from 10% to 50% and from 50% to 90%, respectively.
To understand how Re has impacted SLA, we compare Fig. 11(a) and Fig. 11(b). When La is 5 ms and Av is 50%, SLA is raised by 11.38% by increasing Re from 10% to 50%. When Av is 90%, all SLA values are greater than 0.5, as shown in Fig. 11(b). We raise the value of Re to 90% in Fig. 11(c). When comparing the results of Fig. 11(a) and Fig. 11(b), we can observe that the SLA values have grown significantly.
The simulation results for FSSLA2 are shown in Fig. 12, Fig. 13 and Fig. 14. They show the relation of SLA with Tl for different La values considering Re and Av as constant parameters.
Fig. 11.
Simulation results of FSSLA1.
The Re and Av values are 10% in Fig. 12(a). We can see that when Tl is increased, SLA is slightly reduced. When La is increased from 1 ms to 5 ms and 5 ms to 9 ms, the SLA is decreased by 15% and 11.84%, respectively, for Tl 30%. To see how Av has influenced SLA, we compare Fig. 12(a) and Fig. 12(b). In case when the Av is increased from 10% to 50%, the Tl value is 50% and the La is 1 ms, the SLA is increased by 15%. When the Tl value is changed from 20% to 80%, the SLA is decreased by 18.75% when the La value is 1 ms, as shown in Fig. 12(b). This is because when the system have a lot of traffic load, it will degrade the required SLA. In Fig. 12(c), when we changed the Av value to 90%, all SLA values are higher than Fig. 12(a) and Fig. 12(b) because the required user availability is higher and the SLA should be high for supporting the user requirement.
In Fig. 13, we have increased the value of Re to 50% and the SLA values are higher than in Fig. 12. The SLA is increasing by 11.38% when the Tl values is 50%, La value is 1 ms and Av value is 10%. When the Av increases from 10% to 50% and 90%, the SLA increases by 15%, respectively when the Tl value is 60% and the La value is 5 ms. When La values are 5 ms and 1 ms, all SLA values are greater than 0.5, as shown in Fig. 13(c). This means that users fulfill the SLA requirements.
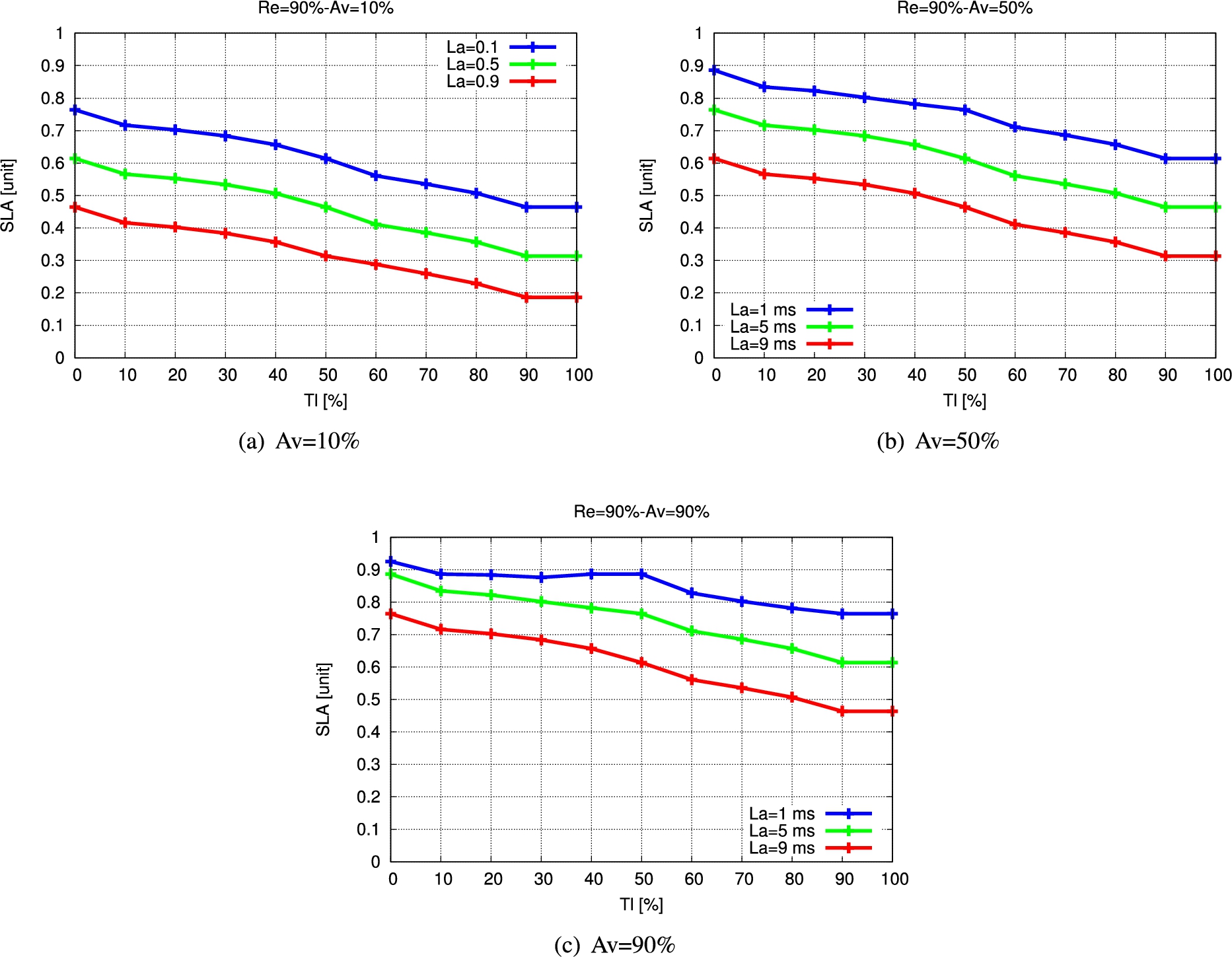
We have increased the value of Re to 90% in Fig. 14. In comparison to the results of Fig. 12 and Fig. 13, we can see that the SLA values have increased significantly. When the Re is increased from 10% to 90% and 50% to 90% and the Tl value is 50%, the Av is 50% and the La is 1 ms, the SLA is increased by 22.76% and 11.38%, respectively.
Fig. 12.
Simulation results for FSSLA2 (Re = 10%).
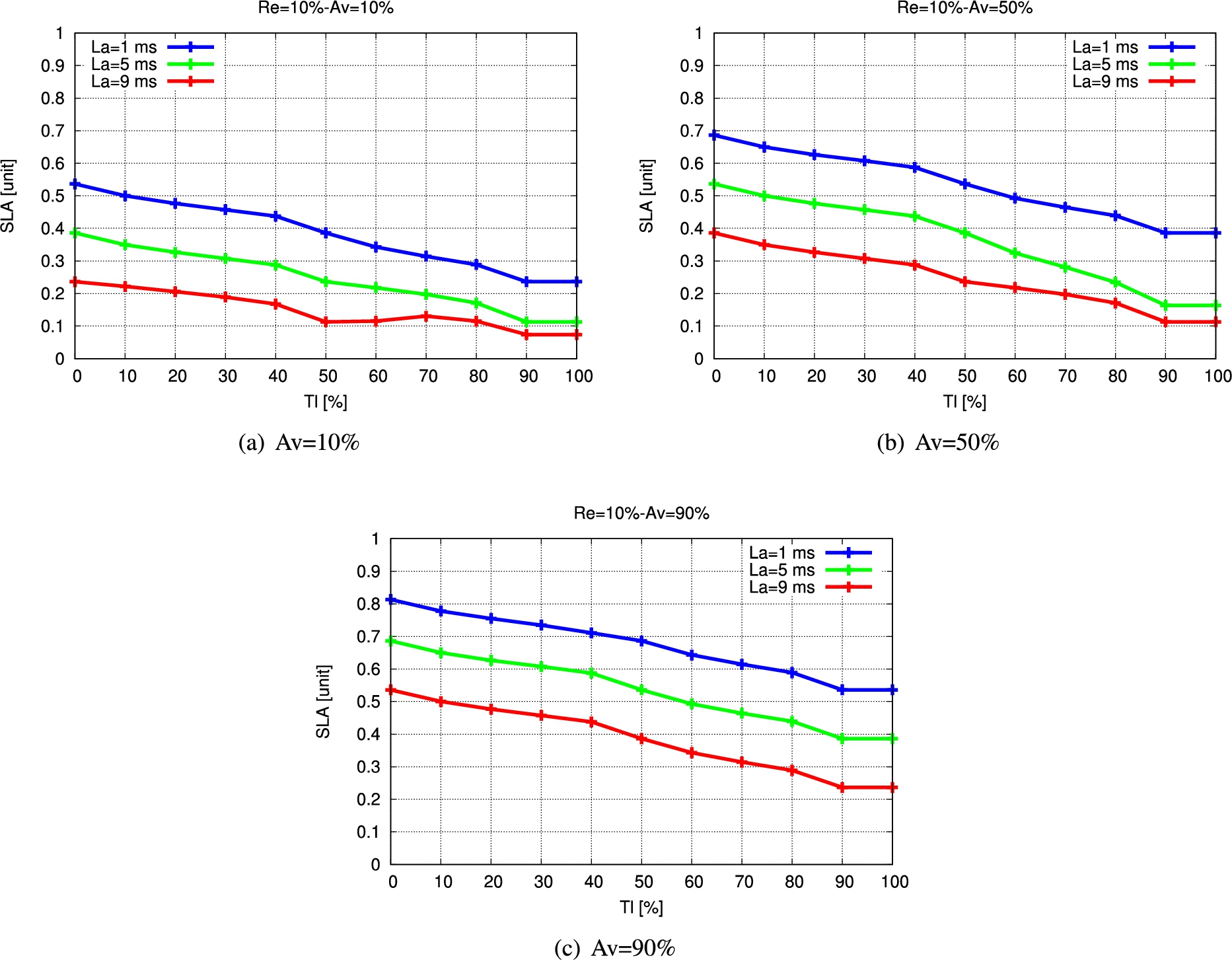
Fig. 13.
Simulation results for FSSLA2 (Re = 50%).
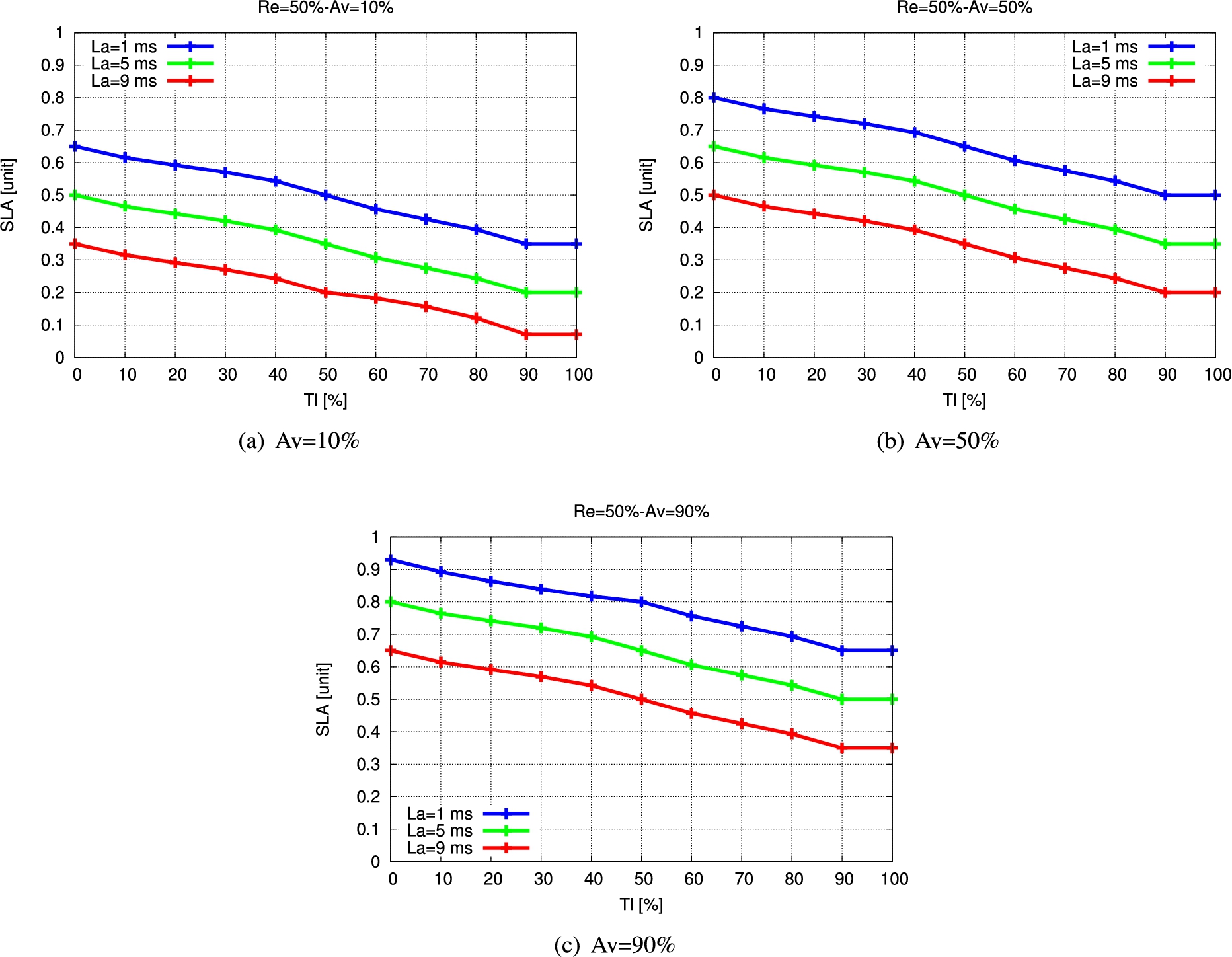
Fig. 14.
Simulation results for FSSLA2 (Re = 90%).
7.Conclusions and future work
In this paper, we proposed and implemented a Fuzzy-based scheme for user SLA. The admission control mechanism will find a set of slices that match the required SLA and attempt to connect a new user to one of the slices. As a result, in 5G wireless networks, the SLA parameter will be utilized as an input parameter for admission control. We evaluated the proposed system by simulations. We discovered that four parameters have varied effects on the SLA based on the simulation results. The SLA value increases as the Re and Av values increases, but when the La and Tl values increase, the SLA value decreases. When comparing FSSLA1 with FSSLA2, we find that FSSLA2 is more complex than FSSLA1, but it performs better for admission control since the Tl parameter is considered.
In the future, we will consider other parameters and make extensive simulations to evaluate the proposed system.
Conflict of interest
The authors have no conflict of interest to report.
References
[1] | G.A. Akpakwu, B.J. Silva, G.P. Hancke and A.M. Abu-Mahfouz, A survey on 5G networks for the Internet of things: Communication technologies and challenges, IEEE Access 6: ((2018) ), 3619–3647. doi:10.1109/ACCESS.2017.2779844. |
[2] | P. Ampririt, S. Ohara, E. Qafzezi, M. Ikeda, L. Barolli and M. Takizawa, Integration of software-defined network and fuzzy logic approaches for admission control in 5G wireless networks: A Fuzzy-based scheme for QoS evaluation, in: Advances on Broad-Band Wireless Computing, Communication and Applications, L. Barolli, M. Takizawa, T. Enokido, H.-C. Chen and K. Matsuo, eds, Springer International Publishing, Cham, (2021) , pp. 386–396. ISBN 978-3-030-61108-8. doi:10.1007/978-3-030-61108-8_38. |
[3] | P. Ampririt, S. Ohara, E. Qafzezi, M. Ikeda, L. Barolli and M. Takizawa, Effect of slice overloading cost on admission control for 5G wireless networks: A Fuzzy-based system and its performance evaluation, in: Advances in Internet, Data and Web Technologies, L. Barolli, J. Natwichai and T. Enokido, eds, Springer International Publishing, Cham, (2021) , pp. 24–35. ISBN 978-3-030-70639-5. doi:10.1007/978-3-030-70639-5_3. |
[4] | P. Ampririt, E. Qafzezi, K. Bylykbashi, M. Ikeda, K. Matsuo and L. Barolli, A Fuzzy-based system for user service level agreement in 5G wireless networks, in: Advances in Intelligent Networking and Collaborative Systems, L. Barolli, H.-C. Chen and H. Miwa, eds, Springer International Publishing, Cham, (2022) , pp. 96–106. ISBN 978-3-030-84910-8. doi:10.1007/978-3-030-84910-8_10. |
[5] | P. Ampririt, E. Qafzezi, K. Bylykbashi, M. Ikeda, K. Matsuo and L. Barolli, An intelligent system for admission control in 5G wireless networks considering fuzzy logic and SDNs: Effects of service level agreement on acceptance decision, in: Advances on P2P, Parallel, Grid, Cloud and Internet Computing, L. Barolli, ed., Springer International Publishing, Cham, (2022) , pp. 185–196. ISBN 978-3-030-89899-1. doi:10.1007/978-3-030-89899-1_19. |
[6] | N. An, Y. Kim, J. Park, D.-H. Kwon and H. Lim, Slice management for quality of service differentiation in wireless network slicing, Sensors 19: ((2019) ), 2745. doi:10.3390/s19122745. |
[7] | J.G. Andrews, S. Buzzi, W. Choi, S.V. Hanly, A. Lozano, A.C.K. Soong and J.C. Zhang, What will 5G be?, IEEE Journal on Selected Areas in Communications 32: (6) ((2014) ), 1065–1082. doi:10.1109/JSAC.2014.2328098. |
[8] | A.A. Barakabitze, A. Ahmad, R. Mijumbi and A. Hines, 5G network slicing using SDN and NFV: A survey of taxonomy, architectures and future challenges, Computer Networks 167: ((2020) ), 106–984. doi:10.1016/j.comnet.2019.106984. |
[9] | J. Chen, M. Tsai, L. Zhao, W. Chang, Y. Lin, Q. Zhou, Y. Lu, J. Tsai and Y. Cai, Realizing dynamic network slice resource management based on SDN networks, in: 2019 International Conference on Intelligent Computing and Its Emerging Applications (ICEA), (2019) , pp. 120–125. doi:10.1109/ICEA.2019.8858288. |
[10] | O.O. Erunkulu, A.M. Zungeru, C.K. Lebekwe, M. Mosalaosi and J.M. Chuma, 5G mobile communication applications: A survey and comparison of use cases, IEEE Access 9: ((2021) ), 97251–97295. doi:10.1109/ACCESS.2021.3093213. |
[11] | K.G. Eze, M.N. Sadiku and S.M. Musa, 5G wireless technology: A primer, International Journal of Scientific Engineering and Technology 7: (7) ((2018) ), 62–64. |
[12] | M. Giordani, M. Mezzavilla and M. Zorzi, Initial access in 5G mmWave cellular networks, IEEE Communications Magazine 54: (11) ((2016) ), 40–47. doi:10.1109/MCOM.2016.1600193CM. |
[13] | E. Hossain and M. Hasan, 5G cellular: Key enabling technologies and research challenges, IEEE Instrumentation Measurement Magazine 18: (3) ((2015) ), 11–21. doi:10.1109/MIM.2015.7108393. |
[14] | S. Hossain, 5G wireless communication systems, American Journal of Engineering Research (AJER) 2: (10) ((2013) ), 344–353. |
[15] | T. Inaba, S. Sakamoto, T. Oda, L. Barolli and M. Takizawa, A new FACS for cellular wireless networks considering QoS: A comparison study of FuzzyC with MATLAB, in: 2015 18th International Conference on Network-Based Information Systems, (2015) , pp. 338–344. doi:10.1109/NBiS.2015.52. |
[16] | J. Jantzen, Tutorial on fuzzy logic, Technical Report, Technical University of Denmark, Dept. of Automation, 1998. |
[17] | M. Jiang, M. Condoluci and T. Mahmoodi, Network slicing management prioritization in 5G mobile systems, in: European Wireless 2016; 22th European Wireless Conference, (2016) , pp. 1–6. |
[18] | M. Jiang, M. Condoluci and T. Mahmoodi, in: Network Slicing Management & Prioritization in 5G Mobile Systems, in: European Wireless 2016; 22th European Wireless Conference, VDE, (2016) , pp. 1–6. |
[19] | I.A. Kamil and S.O. Ogundoyin, Lightweight privacy-preserving power injection and communication over vehicular networks and 5G smart grid slice with provable security, Internet of Things 8: ((2019) ), 100–116. doi:10.1016/j.iot.2019.100116. |
[20] | A. Kammoun, N. Tabbane, G. Diaz and N. Achir, Admission control algorithm for network slicing management in SDN-NFV environment, in: 2018 6th International Conference on Multimedia Computing and Systems (ICMCS), (2018) , pp. 1–6. doi:10.1109/ICMCS.2018.8525945. |
[21] | Y. Kim, J. Park, D. Kwon and H. Lim, Buffer management of virtualized network slices for quality-of-service satisfaction, in: 2018 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), (2018) , pp. 1–4. doi:10.1109/NFV-SDN.2018.8725780. |
[22] | D. Kreutz, F.M.V. Ramos, P.E. Veríssimo, C.E. Rothenberg, S. Azodolmolky and S. Uhlig, Software-defined networking: A comprehensive survey, Proceedings of the IEEE 103: (1) ((2015) ), 14–76. doi:10.1109/JPROC.2014.2371999. |
[23] | J. Lee and Y. Yoo, Handover cell selection using user mobility information in a 5G SDN-based network, in: 2017 Ninth International Conference on Ubiquitous and Future Networks (ICUFN-2017), (2017) , pp. 697–702. doi:10.1109/ICUFN.2017.7993880. |
[24] | L.E. Li, Z.M. Mao and J. Rexford, Toward software-defined cellular networks, in: 2012 European Workshop on Software Defined Networking, (2012) , pp. 7–12. doi:10.1109/EWSDN.2012.28. |
[25] | T. Mahmoodi, 5G and software-defined networking (SDN), in: 5G Radio Technology Seminar. Exploring Technical Challenges in the Emerging 5G Ecosystem, (2015) , pp. 1–19. |
[26] | J.M. Mendel, Fuzzy logic systems for engineering: A tutorial, Proceedings of the IEEE 83: (3) ((1995) ), 345–377. doi:10.1109/5.364485. |
[27] | A. Moravejosharieh, K. Ahmadi and S. Ahmad, A fuzzy logic approach to increase quality of service in software defined networking, in: 2018 International Conference on Advances in Computing, Communication Control and Networking (ICACCCN-2018), (2018) , pp. 68–73, ISSN null. doi:10.1109/ICACCCN.2018.8748678. |
[28] | M. Mousa, A.M. Bahaa-Eldin and M. Sobh, Software defined networking concepts and challenges, in: 2016 11th International Conference on Computer Engineering & Systems (ICCES), IEEE, (2016) , pp. 79–90. doi:10.1109/ICCES.2016.7821979. |
[29] | J. Navarro-Ortiz, P. Romero-Diaz, S. Sendra, P. Ameigeiras, J.J. Ramos-Munoz and J.M. Lopez-Soler, A survey on 5G usage scenarios and traffic models, IEEE Communications Surveys Tutorials 22: (2) ((2020) ), 905–929. doi:10.1109/COMST.2020.2971781. |
[30] | J. Nightingale, P. Salva-Garcia, J.M.A. Calero and Q. Wang, 5G-QoE: QoE modelling for ultra-HD video streaming in 5G networks, IEEE Transactions on Broadcasting 64: (2) ((2018) ), 621–634. doi:10.1109/TBC.2018.2816786. |
[31] | N. Omnes, M. Bouillon, G. Fromentoux and O.L. Grand, A programmable and virtualized network IT infrastructure for the Internet of things: How can NFV SDN help for facing the upcoming challenges, in: 2015 18th International Conference on Intelligence in Next Generation Networks, (2015) , pp. 64–69. doi:10.1109/ICIN.2015.7073808. |
[32] | J. Ordonez-Lucena, P. Ameigeiras, D. Lopez, J.J. Ramos-Munoz, J. Lorca and J. Folgueira, Network slicing for 5G with SDN/NFV: Concepts, architectures, and challenges, IEEE Communications Magazine 55: (5) ((2017) ), 80–87. doi:10.1109/MCOM.2017.1600935. |
[33] | F. Palmieri, A reliability and latency-aware routing framework for 5G transport infrastructures, Computer Networks 179: ((2020) ), 107365. doi:10.1016/j.comnet.2020.107365. |
[34] | J. Rizkallah and N. Akkari, SDN-based vertical handover decision scheme for 5G networks, in: 2018 IEEE Middle East and North Africa Communications Conference (MENACOMM), (2018) , pp. 1–6. doi:10.1109/MENACOMM.2018.8371040. |
[35] | D.A.N. Wulandari, T. Prihatin, A. Prasetyo and N. Merlina, A comparison tsukamoto and mamdani methods in fuzzy inference system for determining nutritional toddlers, in: 2018 6th International Conference on Cyber and IT Service Management (CITSM), (2018) , pp. 1–7. |
[36] | D. Yao, X. Su, B. Liu and J. Zeng, A mobile handover mechanism based on fuzzy logic and MPTCP protocol under SDN architecture, in: 18th International Symposium on Communications and Information Technologies (ISCIT-2018), (2018) , pp. 141–146, ISSN null. doi:10.1109/ISCIT.2018.8587956. |
[37] | Y. Yu, Mobile edge computing towards 5G: Vision, recent progress, and open challenges, China Communications 13: (2) ((2016) ), 89–99. doi:10.1109/CC.2016.7405725. |
[38] | H. Zhang, N. Liu, X. Chu, K. Long, A. Aghvami and V.C.M. Leung, Network slicing based 5G and future mobile networks: Mobility, resource management, and challenges, IEEE Communications Magazine 55: (8) ((2017) ), 138–145. doi:10.1109/MCOM.2017.1600940. |




