Biogeography-Based Krill Herd algorithm for energy efficient clustering in wireless sensor networks for structural health monitoring application
Abstract
Civil buildings are prone to various kinds of damages. The detection of damages caused in a building at an early stage is essential in order to save the invaluable human life and significant belongings. Wireless sensor networks (WSN) help to detect damages caused to a building by sensing different factors, which affect civil structures. Energy efficiency of sensor nodes and network congestion are quite common issues in wireless sensor networks that affect the network performance. In this research work, the formation of energy efficient clusters mitigates congestion by considering the buffer occupancy level and fairness index of flows to improve the network lifetime. The proposed method uses Biogeography-Based Krill Herd (BBKH) algorithm for cluster head selection. BBKH based congestion mitigation outperforms other classical evolutionary optimizations and swarm intelligence algorithms like Genetic Algorithm, Particle Swarm Optimization (PSO) and Symbiotic Organisms Search (SOS). Compared with PSO, the network throughput has increased by 26.18% using BBKH. The network lifetime has increased by 42.11% using the proposed BBKH, compared to PSO. The extended lifetime of the network helps damage detection in civil structures for extensive periods.
1.Introduction
Structural Health Monitoring (SHM) is a technique used to inspect the physical condition and detect the damage at the earliest stage of the civil, mechanical and aerospace structures. The damage-detection methods are either visual [43] or experimental methods such as acoustic or ultrasonic methods, magnet field methods, radiographs and eddy-current methods [5]. These techniques require a priori knowledge about the vicinity of the damage and require the portion of the structure to be readily accessible for inspection. These techniques are useful to detect damage on or near the surface of the structure. It is very tedious and time-consuming to inspect very complex and long structures, like bridges that run for several kilometers. The above drawbacks have motivated researchers to develop methods that examine changes in the global dynamic characteristics of the structure. SHM is an emerging tool that provides civil engineers in keeping a check on the damage or wear and tear caused to the structure. Damage detection, determined by changes in the dynamic properties or response of structures, is a subject that has received considerable attention in the recent technical literature. Inspection of the buildings is essential so that the damage can be we identified and maintenance is performed before it gets unrepairable. WSN is deployed in the appropriate location of buildings where damages are possible and help in the inspection. The sensor nodes sense the condition of the building and send the data to the Base Station (BS) or sink node for further processing. The sensor nodes are battery powered. Therefore, the energy utilization by the sensors must be efficient, to prolong the battery lifetime.
Fig. 1.
Damages caused to buildings.

There are different factors that cause damages to civil structures. Some of them are due to Erosion, Natural Calamities like an earthquake, flooding etc. Violence, Fire, and lack of maintenance. The damage is usually in the form of major and minor cracks. Major cracks could be structural cracks that cause immense damage to the structure. Figure 1 gives some the damages caused to buildings.
To identify the presence of a crack in the concrete, an accelerometer is used [22,36]. Fiber optic sensors embedded within concrete identifies cracks. By this method, the small opening of the crack has been identified [21,38]. The parameters like vibration, temperature, load, the amount of moisture content, etc. measured help to detect damages. High moisture content can promote its deterioration. In general, most chemical and physical corrosion process occur due to the high moisture content that leads to the damage of the buildings [25]. Figure 2 gives temperature sensors and Fig. 2 gives a corrosion monitoring sensor.
Fig. 2.
Temperature sensor. Corrosion monitoring sensor.
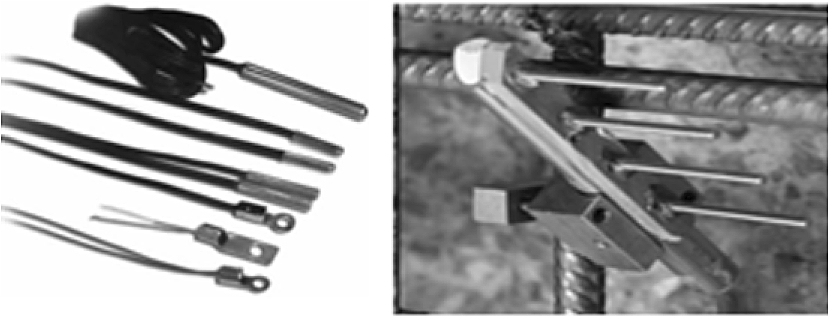
Traditional structural monitoring systems, namely, wired systems, which had shown many disadvantages like installation and maintenance, are slowly being replaced by wireless smart sensors to overcome the above-mentioned cons. WSN is deployed at critical locations of the building to sense the analog information, digitize and send them to a central monitoring system. Such an approach has solved most of the problems connected with wired systems, but has thrown new problems intrinsic to a wireless system like power, as the sensor units are battery powered. In literature, many approaches have been proposed to improve the energy efficiency of the WSNs. In the proposed work, a two-tier network architecture is used for data gathering. BS receives the data from CH and makes the required decision. While the data are transmitted to the BS, congestion is possible. Congestion occurs when the offered load exceeds the available link capacity. Congestion is one of the major problems which reduces network performance. The proposed method helps in the formation of energy efficient clusters and controls congestion occurrence. As a result, the network lifetime is improved.
Congestion leads to packet loss. If packets are lost, all the data sensed by the sensor nodes will not reach the BS, which does not help to know the severity level of the structural damage accurately. The categorization of cracks in the structural element column is proposed in [31]. The authors have categorized the cracks occurring in the column into the fine, medium or severe crack, using fuzzy cognitive maps (FCM).
This paper is structured in the following way: Section 2 briefs about the related works. Section 3 discusses the problem definition. Section 4 details about the building monitoring system. Section 5 gives the details about the proposed methodology and Section 6 gives the simulation environment. Section 7 concludes results and discussion. Finally, Section 8 concludes the paper.
2.Related work
Considerable research efforts were made in the past few years in developing clustering mechanisms for deploying sensor nodes in WSNs. The first well-known clustering protocol developed by Heinzelman et al. [11] is Low Energy Adaptive Clustering hierarchy with Deterministic CH Selection (LEACH). In this method, the CHs are selected using optimal probability. The protocol works on periodically randomized rotations of the CH within the cluster range between zero and one. If the random number is less than the pre-determined threshold value, the node becomes a CH for the current round. The main drawback of this method is a predefined number of clusters.
A new distributed type-2 fuzzy based self-configurable clustering (SCCH) mechanism is proposed [15]. In the case of failure of elected CH, another backup cluster head (BCH) takes the role of new CH in order to monitor the area. SCCH uses a fuzzy system and local information to select CH that is more eligible compared with others, and the remaining less eligible nodes act as BCH. Therefore, in the case of CH failure, the Cluster Members (CM) can replace the BCH with the permanent CH failure. The initial overhead incurred in selecting the CH using the fuzzy logic system is more.
Power-Efficient Gathering in Sensor Information Systems (PEGASIS) [24], Threshold Sensitive Energy Efficient Network (TEEN) [26] and Hybrid Energy-Efficient Distributed clustering (HEED) [45] are protocols that follow hierarchical clustering in a homogeneous network. All the above listed hierarchical clustering saves the transmission distance for sensor nodes, but the set of CHs still suffers from long transmissions. Energy Efficient Two Levels Distributed Clustering (EE-TLDC) [19] has proposed a scheme in which the number of CHs that transmit to BS has reduced in order to reduce the transmission cost. In this, the primary level of CH selection is by probability and the secondary level of CH selection is from these primary CHs based on distance from BS.
Li Qing et al. [29] have proposed a distributed energy-efficient clustering algorithm (DEEC) for heterogeneous WSN. By this method, CHs selection is by probability based on the ratio between the residual energy of each node and the average energy of the network. The nodes with high residual energy will have always chances to be the CH. The number of live nodes becomes almost zero around 4000 rounds compared to LEACH, SEP, LEACH-E protocols [29] where many nodes are alive even after 4000 rounds.
In an approach, called energy-driven adaptive clustering hierarchy (EDACH) [20], data transfer to the BS is by CH. A proxy acts as CH, in the case of low energy of existing CH. The drawback is if there are more CHs, they will consume more energy for aggregating the data and has to transmit the data to the longer distance. Adding to this is another disadvantage that, if the area to be sensed requires only less number of nodes, then it is waste to deploy a number of sensor nodes from distances longer from BS.
In an approach [30] Micro-electromechanical systems (MEMS) are used for the collection of multiple features by using several clustering algorithms, such as Fuzzy logic, by considering the residual energy of the nodes and the clusterheads degree.
Many research contributions made in the past for cluster formation used soft computing methods [2,4,6,7,9,10,12,32,33,35,47]. Sajid Hussain et al. [14] proposed a genetic algorithm based approach to determine the CHs. Ying Liang et al. [23] utilized PSO for clustering. They proposed a hybrid algorithm using PSO and LEACH that showed better results compared to LEACH. Saeed Mehrjoo et al. [27] proposed a clustering method using GA and ABC. This method uses GA to select CH and uses an ABC algorithm for cluster member selection. The authors claim that the proposed method improves the network lifetime compared with LEACH [11].
In Genetic Algorithm-based Energy-Efficient Adaptive clustering hierarchy Protocol (GAEEP) [1] the operation has many rounds, each round has a setup phase to form clusters and in the steady state phase, the sensed data are transferred to CH. The protocol, although shows better results compared with LEACH, the two phases in each round consumes more time and delays the entire process.
Clustering based on improving discrete particle swarm optimization [13] solves clustering inequality problem. In this method, the fitness function uses only the communication distance. The PSO inertia coefficient is variable to distinguish between particles. This method in comparison with LEACH shows better results, but the total residual energy of nodes and lifetime are not considered.
PSO-MV protocol [46] based on PSO method balances the energy of nodes. This method selects 2 nodes as CH, one is main cluster heads (MCH) and another as vice cluster head(VCH). The MCH is responsible for data collecting and transmission and VCH are responsible for inter-cluster communications or intra-cluster communications to BS. The drawback of this algorithm is in the optimum selection of a number of clusters.
In literature, many works concentrated on congestion control in WSN. Congestion control for Multiclass Traffic (COMUT) [17] is a framework that consists of a distributed and scalable congestion control mechanism. The network has different clusters, each of which monitors congestion within its local scope. A sentinel governs each cluster. These sentinel roles assigned to sensors help to proactively monitor the system and collect the event rates that used to infer the combined level of congestion. The sentinel estimates the local traffic and if the value exceeds the threshold, congestion has occurred and COMUT uses the AIMD policy to regulate congestion. The disadvantages of COMUT are when sentinel failure occurs, it directly affects the working of COMUT and the sensor failures that may be in the cluster member or the sentinel will affect the routing protocol layer of WSN.
Cluster-Based Congestion Control Protocol (CBCC) [18] consists of clusters and supporting mechanisms for congestion control in WSN. Nodes perform local computations of estimated traffic load. CH processes the estimated information and a collective cluster level load estimate is transmitted to the CHs towards the source clusters. This allows source nodes to regulate their sending rate based on the congestion level in the traffic path. This protocol supports multiple flows.
In a method proposed by [16], energy-aware smart homes are built by fixing sensor devices in power outlets and pillars. The entire system operates with Web technologies. The demonstration results have given the solution to energy awareness, energy conservation, etc.
Soft computing techniques help for congestion control. Sai Prakash et al. [28] proposed a firefly-inspired tree formation in wireless sensor networks. In this cluster-based energy aware technique, the responsibility of cluster head is distributed among nodes to distribute the energy drain factor. The results obtained have shown improvement in the network lifetime and minimizes the partitioning problem.
Sun, Yi et al. [44] proposed a clustering scheme for the network, which employs Firefly Algorithm. The clustering of the network is considered on the basis of parameters considered together, which includes energy and distance and a reach-back technique is employed for clustering of the sensor network.
In the existing papers, concentration towards maximization of network lifetime was less. Motivated by this drawback the proposed method has the following objectives: i) to improve the network lifetime ii) to reduce congestion. Congestion mitigation can reduce packet loss, which is a major issue in achieving maximum network utilization.
3.Problem formulation
Assume a network with a set of sensor nodes
To send and receive data packets, energy is consumed by the nodes. CH will consume comparatively more energy to aggregate the data packets collected. If CH is more distant from the BS it will consume more energy for transmitting the data from CH to BS. Routing of packets from CH to BS must be optimized so as to improve the energy efficiency of the nodes. Also, when packets are routed, congestion will occur. Due to congestion, packet loss will occur. If packets are lost, it is to be retransmitted, which will further reduce the energy of nodes and increases delay. So, mitigation of congestion is essential in order to improve the network performance. In this research paper, using soft computing techniques, the solution for an optimal CH selection with congestion mitigation is provided. The proposed method uses a meta-heuristic search algorithm called as Biogeography-Based Krill Herd (BBKH) [41] for selection of CHs and congestion mitigation. Better results have been obtained compared with classical optimization techniques like Genetic Algorithm (GA), Particle Swarm Optimization (PSO) and Symbiotic Organisms (SOS).
4.Building health monitoring system
A building health monitoring system (BMS) is discussed in this section. Cluster heads are selected using BBKH. The physical parameters which are identified as crack inducing factors are measured using sensors and instruments. Sensors are used to measure certain physical parameters like temperature, corrosion, etc. The thickness of the cover is measured by using the instrument, namely, cover meter. If the measured value of the parameter has reached the threshold limit, it is transmitted to the CH and the rate of monitoring is increased. If the measured value has not reached the threshold value the monitoring is continued by the sensor nodes. The data are aggregated by averaging and sent to remote monitoring system. The received data are analyzed and the damage condition is reported in different formats, such as predictive analysis, visual reports, etc. BMS are given in Fig. 3.
Fig. 3.
Buliding Monitoring System.
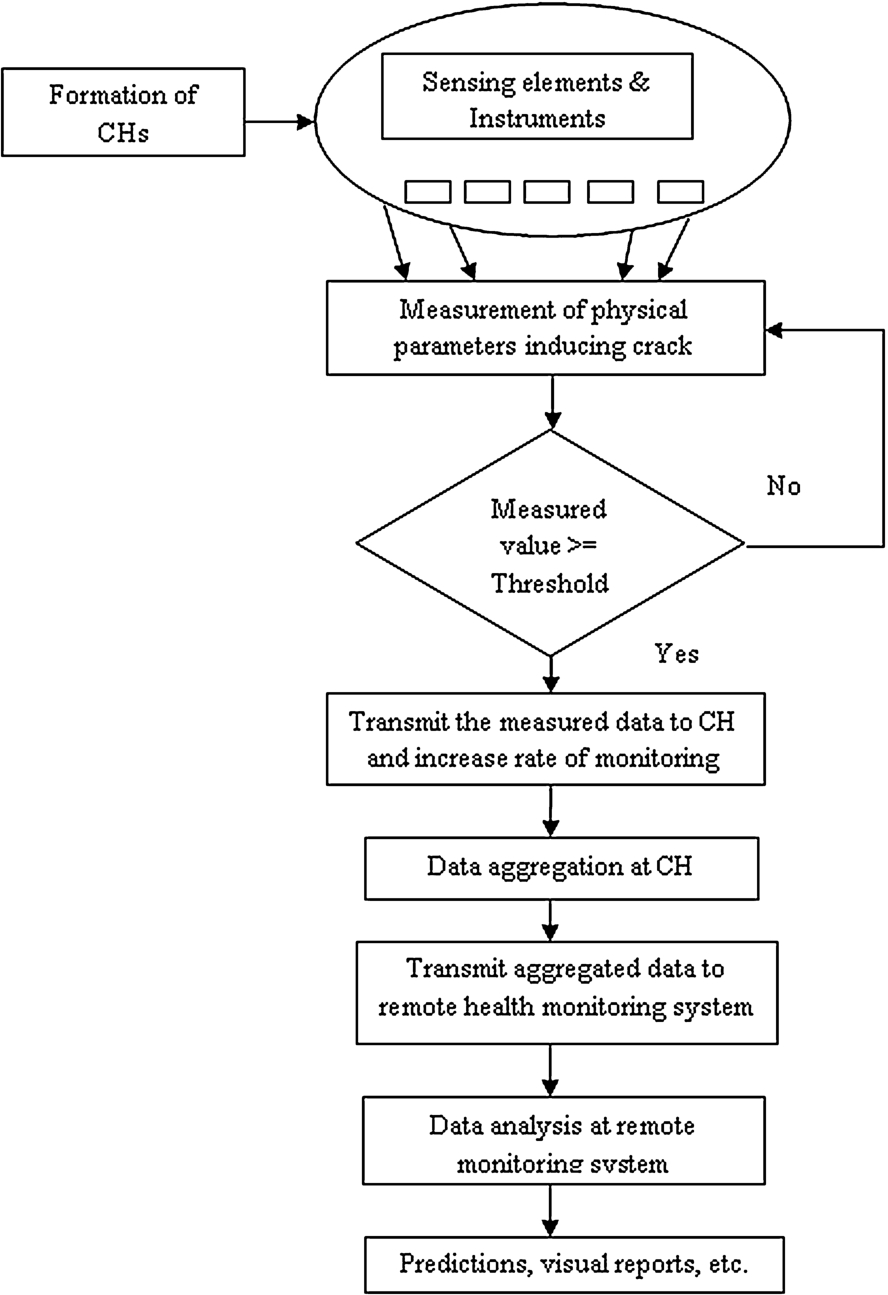
5.Proposed BBKH based CH selection
Initially, all the sensor nodes are alive. The proposed method runs for many rounds. In each round, the CHs keep on changing and selection of CH is by BBKH. Calculate the energy consumed by the all the nodes at the end of each round. Repeat the given steps until the stopping condition of i) Maximum number of rounds or ii) All nodes are dead. In the proposed work, the first stopping condition is used.
5.1.Biogeography-Based Krill Herd algorithm
Krill Herd (KH) is a novel search algorithm developed by Gandomi and Alavi [8] in the year 2012. KH algorithm is a meta-heuristic algorithm that is inspired by the bio-based swarm intelligence algorithm. The algorithm models the herding behavior of the Krill swarms. The least distance from the food and the highest density of the swarm form the objective function of the krill individuals. KH algorithm has few control variables to adjust, in comparison with other algorithms. Sometimes, KH algorithm may not escape local optima and fails global search completely, leading to an unsatisfactory solution. Biography-Based Optimization (BBO) is a novel optimizer [34] based on biogeography theory. BBO gives the globally best solution and is insensitive to parameters. KH is improved by combining a migration operator used in BBO algorithm, namely, krill migration (KM) operator. The combination of KH and KM operator forms BBKH. The addition of KM operator helps to regulate the new solution generated by KH. Initially, KH is used to cut down the search space and give a candidate solution set. Subsequently, the KM operator exploits the search space and gives global best optimal solution. The position of each the Krill using KH algorithm is affected by three actions [39,40], namely, (i) Movement affected by other krill, (ii) Foraging action and (iii) Random diffusion.
The objective function of the krill individuals is found using the above-listed actions and the best krill and its position are determined over the iterations until the optimization criteria are reached.
In KH, the time-dependent location of the krill in the two horizontal spatial dimensions
The new position of KH from time t to
5.2.Symbiotic Organisms Search (SOS)
SOS is an algorithm selected for comparison with BBKH. SOS is a simple and powerful Meta heuristic algorithm [3]. The algorithm simulates symbiotic interaction strategies that organisms use to survive in the ecosystem. Similar to KH, SOS also require fewer algorithm-specific parameters. Many species in nature depend on each other for their survival and this relationship means Symbiosis. The most common symbiotic relations are mutualism, commensalism, and parasitism. Mutualism denotes a relationship in which both species benefit each other. Commensalism is a relationship between two species in which, one benefits and the other is unaffected by other. In parasitism relationship, one benefits and the other is harmed. SOS is used to search for the fittest organism based on the relationship between two paired organisms.
SOS starts its iteration with an initial population, which is selected randomly which is the search space. The fitness value of each organism is calculated. Each organism interacts with the other organism randomly through all the three phases, namely mutualism, commensalism, and parasitism. In mutualism phase, two organisms, namely
In Commensalism phase, two organisms
The third phase is Parasitism phase; two organisms
5.3.Fitness function
The proposed BBKH helps to find the best CH with the help of fitness function that is calculated as discussed below. The fitness function helps to select CHs in order to form clusters. It is a multi-objective function with two objectives. The first objective is to improve energy efficiency by considering the distance between nodes. As distance The second objective is to reduce network congestion with mitigating buffer occupancy. The first objective helps to select CH based on the distances, energy level and the ratio of the distance from the node to CH and CH to BS. The second objective has two values to be minimized. The first is the fairness index, which is the average throughput of flows in the network and the second value is node buffer occupancy level. The fairness index must be maximized i.e. throughput of each flow must be more and buffer occupancy must be minimized. If buffer occupancy is more, packet drop occurs, which increases the packet retransmission, reducing the energy efficiency and network performance. The buffer occupancy level must be maintained as low as possible so that the buffer never gets fully occupied avoiding packet drops. The Eq. (11) gives the fitness equation.
Consider Eq. (12) for CH selection.
Energy consumption is directly proportional to the square of the distance, for distance
Fairness Index [18] is given by Eq. (14).
Each algorithm undergoes an iterative process to find the best solution for each round of the network. On each iteration, the fitness is calculated as per Eq. (1) and the best solution is the one with lowest fitness value. The solution consists of the optimal set of CHs which reduces the energy consumption and improves the overall throughput of the flows considered and also minimizes the buffer occupancy. The process repeats until the termination condition, which is the considered as a maximum number of rounds is reached.
6.Simulation environment
The proposed method is simulated using MATLAB. As the network is wireless, the network parameters considered in the simulation are given in Table 1. The energy model considered in the proposed work is the same as considered by LEACH protocol [11].
Table 1
Simulation parameters
| Parameter | Value |
| No. of nodes | 100 |
| Sensing region | |
| Energy dissipated | 50 nanoJoules/bit |
| Energy for data aggregation | 5 nanoJoules/bit |
| Initial energy | 200 Joules |
Initially, the sensor nodes are deployed randomly in the sensing region. In each round, CH is selected based on the heuristic search algorithm, namely BBKH, SOS, GA, and PSO. The individuals with the best fitness value become the CH. The solution must be fulfilling the following constraints i) It should be non-zero real numbers ii) It should be within the range of a number of nodes considered, i.e. 100 nodes iii) The entries must be unique and iv) the nodes which are selected as CHs must be an alive. Along with this, the transmission rate of the network is constrained between the preset maximum and minimum values. At the end of each round, the energy consumed by sensor nodes and CH is calculated. The new energy values after energy loss due to data transfer are considered for CH selection in the next round. In each round, the energy level of nodes reduces and after certain rounds the nodes become dead one by one. All necessary parameters such as the number of alive nodes, the packet transferred, energy consumed, the number of cluster heads, buffer occupancy are logged for each round.
7.Results and discussion
The proposed method of BBKH is used for CH selection. BBKH is compared with GA, PSO, and SOS. Different parameters which have an impact on network lifetime are considered for comparison. Using GA, initially a random population is created ant the fitness value if found. Based on the fitness value, the best individuals are selected and the crossover and mutation are performed. The resulting solution gives the best solution with a set of CH and rate of data transmission. PSO is initialized with a random particle group and finds the best solution by means of updating generations. In each generation, the particle moves towards the best solution by updating the velocity and location. Finally, at the end of the maximum number of generations, we have the best solution, which gives the set of CH and the rate of data transmission.
Fig. 4.
Number of Alive nodes.
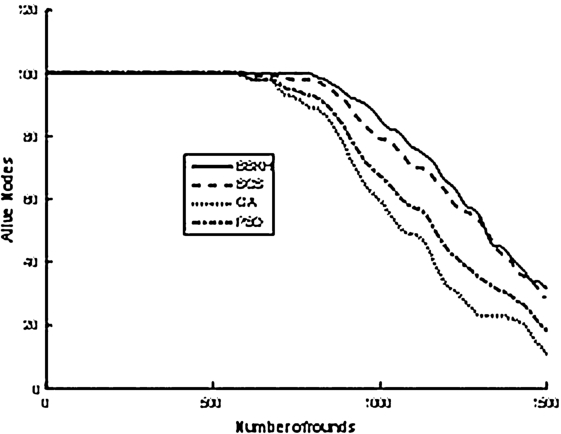
In Fig. 4 the number of alive nodes while running different algorithms are compared for a different number of rounds. As it is apparent from the Fig. 3, the proposed algorithm of BBKH based CH selection presents a significantly better network lifetime than other algorithms. Congestion is mitigated by BBKH by lowering the buffer occupancy level. When the buffer level is kept lower, packet drops are avoided. This, in turn, reduces the retransmissions of dropped packets and the energy consumption due to retransmission. As the power consumption is reduced, nodes are alive for many rounds as given the Fig. 4. The performance of GA in comparison with the other algorithms considered is very poor.
Fig. 5.
Total energy consumption.
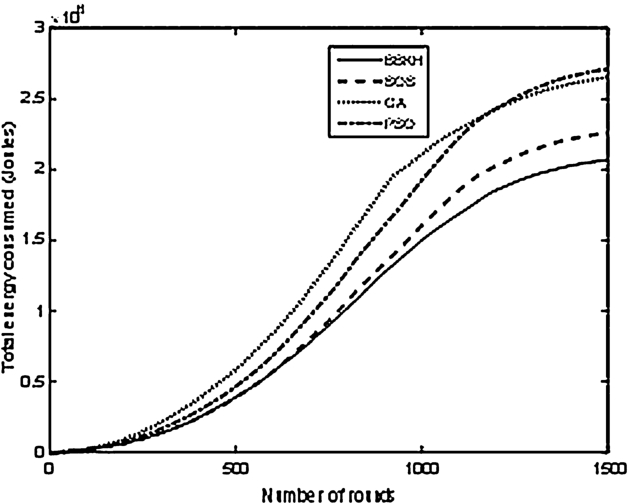
Figure 5 reveals the comparison of total energy consumption throughout the simulation of 1500 rounds. It is clear from the Fig. 5 that the lowest energy consumption is manifested by BBKH algorithm, due to congestion mitigation. While congestion is mitigated, packet drops, retransmissions due to packet drops and energy consumption due to retransmission are reduced. SOS consumes nearly 20% more energy than BBKH. Initially, GA consumes more energy than PSO, but in later stages, PSO consumes more energy than GA. SOS is able to maintain a close range with BBKH initially, but after 1000 rounds the energy consumption by SOS is comparatively more. This additional energy consumption is the reason why BBKH has its first node death at a much later round than SOS.
Fig. 6.
Total packets delivered.
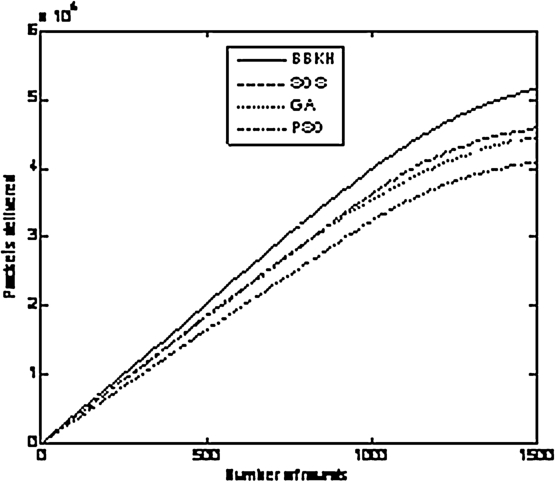
Figure 6 depicts the total number of packets delivered by the BS. BBKH sends a number of packets and PSO performs worst. Both SOS and GA are in the same range until 1000 rounds, after which GA performance is comparatively less.
Fig. 7.
Buffer Occupancy.
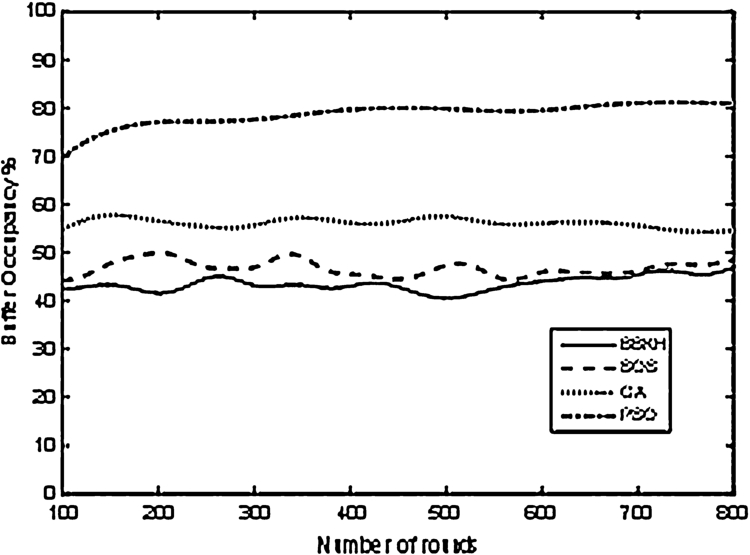
Figure 7 gives the buffer occupancy position of various algorithms. BBKH is able to maintain less buffer occupancy level among all other algorithms, which is closely followed by SOS. The less buffer occupancy level reveals that the queued up packets are delivered without any packet drop due to buffer occupancy. Lower buffer occupancy also facilitates less end to end delay of packets in the network. As PSO and GA show buffer occupancy more packets will be dropped and the packets delivered will be less as shown in Fig. 6. When more packets are dropped, retransmission of packets takes place, which in turn increases the energy consumed, which is inferred from Fig. 5 where energy consumed by PSO and GA are more.
Fig. 8.
Packet Delivery Ratio.
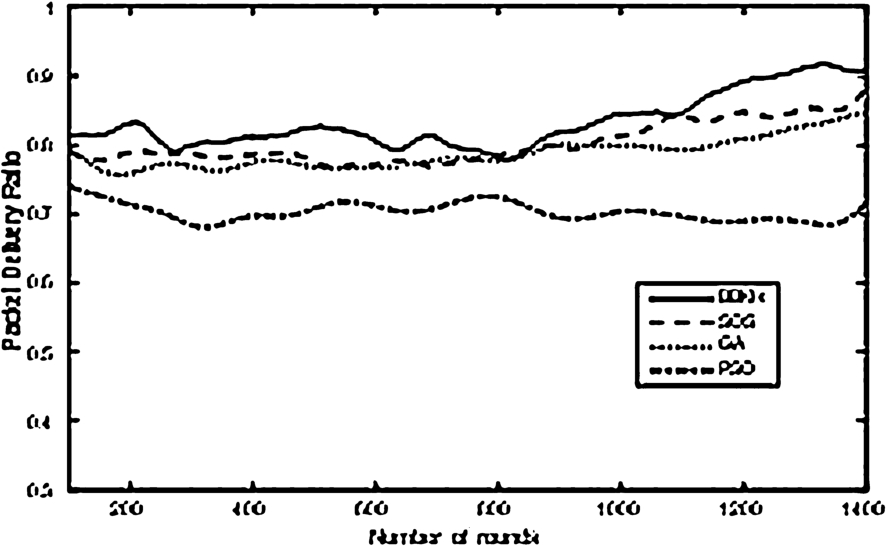
Finally, in Fig. 8 the packet delivery ratio (PDR) is given for all the algorithms throughout the period of simulation. BBKH has the highest PDR which is followed by SOS. Higher PDR is attributed to lower buffer occupancy, which mitigates packet loss. Since PSO has a buffer occupancy, it shows lower PDR. If the PDR is lower, it causes the packet to be retransmitted, which increases the energy spent per packet, also increasing the delay in the network.
The algorithms are tested for objective function solving capability at the first round of the network, where the node energy levels are same. The node locations are also maintained same for all the four algorithms. The convergence graph of Fig. 9 shows the objective function value for different algorithms for the same number of iterations. It is clear from the Fig. 9 that BBKH solved the round with a better solution compared with other algorithms.
Fig. 9.
Convergence graph.
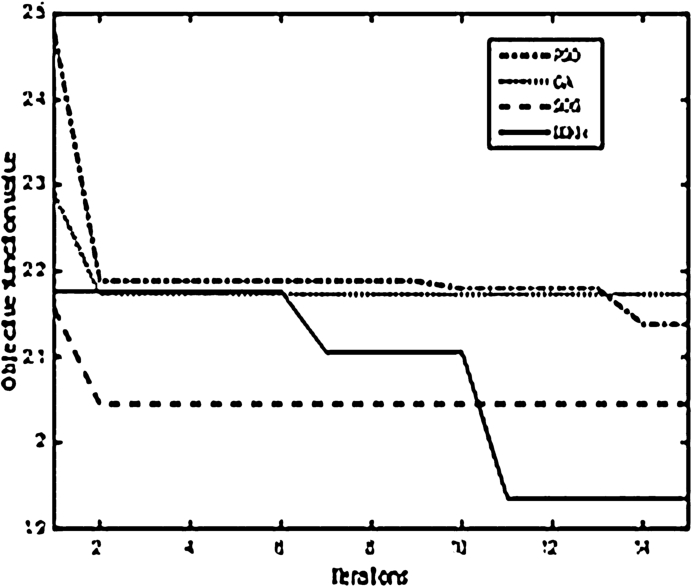
Overall, BBKH shows superior capabilities in solving the problem which is a complex, nonlinear, multi-objective problem. SOS and GA are other alternate algorithms which can be used to solve this problem. They can be improved by suitable modification/hybridization. PSO in spite of its fast convergence, solved the energy consumption objective better than the congestion mitigation, deteriorating the overall performance.
8.Conclusions
An Energy Efficient Clustering with Congestion Control in WSN using BBKH is proposed for SHM. Monitoring of buildings periodically and correctly helps in initiating the maintenance. The proposed method of BBKH based CH selection improves the lifetime of the network by 42.11% in comparison with PSO. This increase in the lifetime has revealed the efficient energy utilization of the sensor nodes by using the proposed method of BBKH based CH selection. The congestion has been reduced by considering the buffer occupancy. When the buffer occupancy is less, all the packets are delivered to BS without any packets being dropped. With BBKH, the network lifetime is improved, which helps in prolonging the lifetime of the network. With the improved lifetime, the buildings can be monitored for a longer duration for finding any damages caused to it and also reduces the need for inspection and maintenance. The proposed solution is applicable to other wireless sensor network applications, particularly where the resources are constrained and network utilization is vital.
References
[1] | M. Abo-Zahhad, S.M. Ahmed, N. Sabor and S. Sasaki, A new energy-efficient adaptive clustering protocol based on genetic algorithm for improving the lifetime and the stable period of wireless sensor networks, International Journal of Energy, Information and Communications 5: (3) ((2014) ), 47–72. doi:10.14257/ijeic.2014.5.3.05. |
[2] | M. AlRashidi and M. El-Hawary, A survey of particle swarm optimization applications in electric power systems, IEEE Transactions on Evolutionary Computation 13: (4) ((2009) ), 913–918. doi:10.1109/TEVC.2006.880326. |
[3] | M.-Y. Cheng and D. Prayogo, Symbiotic organisms search: A new metaheuristic optimization algorithm, Computers and Structures 139: ((2014) ), 98–112. doi:10.1016/j.compstruc.2014.03.007. |
[4] | Y. Del Valle, G. Venayagamoorthy, S. Mohagheghi, J.-C. Hernandez and R. Harley, Particle swarm optimization: Basic concepts, variants and applications in power systems, IEEE Transactions on Evolutionary Computation 12: (2) ((2008) ), 171–195. doi:10.1109/TEVC.2007.896686. |
[5] | J.E. Doherty, Nondestructive evaluation, in: Handbook on Experimental Mechanics, A.S. Kobayashi, ed., Society for Experimental Mechanics, Prentice-Hall, Englewood Cliffs, N.J., (1987) , Chapter 12. |
[6] | R.C. Eberhart and J. Kennedy, A new optimizer using particle swarm theory, in: Proceedings of the Sixth International Symposium on Micro Machine and Human Science, Nagoya, Japan, IEEE Service Center, Piscataway, NJ, (1995) , pp. 39–43. doi:10.1109/MHS.1995.494215. |
[7] | S.M. Elseuofi, Quality of service using PSO algorithm, International Journal of Computer Science & Information Technology (IJCSIT) 4: (1) ((2012) . |
[8] | A.H. Gandomi and A.H. Alavi, Krill herd: A new bio-inspired optimization algorithm, Commun. Nonlinear Sci. Numer. Simulat. 17: (12) ((2012) ), 4831–4845. doi:10.1016/j.cnsns.2012.05.010. |
[9] | D.E. Goldberg, Genetic Algorithms in Search, Optimization, and Machine Learning, Addison-Wesley Professional, (1989) . |
[10] | V. Gudise and G. Venayagamoorthy, Evolving digital circuits using particle swarm, in: Proceedings of the International Joint Conference on Neural Networks, Vol. 1: , (2003) , pp. 468–472. |
[11] | W.R. Heinzelman, A. Chandrakasan and H. Balakrishnan, Energy-efficient communication protocol for wireless micro-sensor networks, in: Proceedings of the 33rd Hawaii International Conference on System Science, Maui, Hawaii, (2000) . |
[12] | J.H. Holland, Adaptation in Natural and Artificial Systems, University of Michigan Press, Ann Arbor, MI, USA, (1975) . |
[13] | J. Hou, X. Fan, W. Wang, J. Jie and Y. Wang, Clustering strategy of wireless sensor networks based on improved discrete particle swarm optimization, in: 6th Int. Conference on Natural Computation (ICNC), Vol. 7: , (2010) , pp. 3866–3870. |
[14] | S. Hussain, O. Islam and A. Wasey Matin, Genetic algorithm for energy efficient clusters in wireless sensor networks, in: Proceedings of the 4th International Conference on Information Technology, IEEE Computer Society, (2007) . |
[15] | D. Izadi, J. Abawajy and S. Ghanavati, An alternative clustering scheme in WSN, IEEE Sensors Journal 15: (7) ((2015) ), 4148–4155. |
[16] | A. Kamilaris, A. Pitsillides and M. Yiallouros, Building energy aware smart homes using web technolgies, Journal of Ambient Intelligence and Smart Environments 5: (2) ((2013) ), 161–186. |
[17] | K. Karenos, V. Kalogeraki and S.V. Krishnamurthy, Cluster-based congestion control for sensor networks, ACM Trans. on Sensor Networks V: ((2007) ), 1–31. |
[18] | S. Karunakaran and P. Thangaraj, Cluster-based congestion control for sensor networks, ACM Transactions on Sensor Networks 4: (1) ((2008) ). |
[19] | M. Kaur, A. Jain and A.K. Goel, Energy efficient two level distributed clustering scheme to prolong stability period of Wireless Sensor Network, in: International Conference on Advances in Computing, Communications and Informatics (ICACCI), (2014) . |
[20] | K.T. Kim and H.Y. Youn, Energy-driven adaptive clustering hierarchy (EDACH) for wireless sensor networks, LNCS 3823: ((2005) ), 1098–1107, EUC Workshops, 2005. |
[21] | C.K.Y. Leung, N. Elvin, N. Olson, T.F. Morse and Y.-F. He, A Novel Distributed Optical Crack Sensor for Concrete Structures, Vol. 65: , Elsevier Sci. Ltd, (2000) , pp. 133–148. |
[22] | Y. Li, Y.-F. Duan and Y.-Q. Xiang, Automatic recognition and real-time alarming of earthquake induced vibration of a tied arch bridge, IEEE ((2011) ), 3866–3869. |
[23] | Y. Liang and H. Yu PSO-Based Energy Efficient Gathering in Sensor Networks, Springer-Verlag, Berlin Heidelberg, (2005) . |
[24] | S. Lindsey and C.S. Raghavendra, PEGASIS: Power efficient gathering in sensor information systems, in: Proc. of the IEEE Aerospace Conference, Vol. 3: , Big Sky, Montana, (2002) , pp. 1125–1130. |
[25] | M. Maksimovic, G.M. Stojanovic, M. Radovanovic, M. Malesev, V. Radonjanin, G. Radosavljevic and W. Smetana, Application of a LTCC sensor for measuring moisture content of building materials, Construction and Building Materials 26: ((2012) ), 327–333. |
[26] | A. Manjeshwar and D.P. Agrawal, TEEN: A routing protocol for enhanced efficiency in wireless sensor networks, in: 1st Int. Workshop on Parallel and Distributed Computing Issues in Wireless Networks and Mobile Computing, Vol. 3: , (2001) . |
[27] | S. Mehrjoo, H. Aghaee and H. Karimi, A novel hybrid GA-ABC based energy efficient clustering in Wireless Sensor Network, Canadian Journal on Multimedia and Wireless Networks 2: (2) ((2011) ). |
[28] | S. Prakash, S.K.L.V. Rami Reddy and S. Kondapalli, Firefly inspired energy aware cluster based tree formation in WSN, in: 2nd International Conference on Information and Communication Technology (ICoICT), Bandung, 28–30 May, (2014) , pp. 356–360. |
[29] | L. Qing, Q. Zhu and M. Wang, Design of a distributed energy-efficient clustering algorithm for heterogeneous wireless sensor networks, Elsevier, Computer Comm. 29: ((2006) ), 2230–2237. doi:10.1016/j.comcom.2006.02.017. |
[30] | R.A. Ramadan, Clustering based fuzzy logic for multimodal sensor networks: A preprocessing to decision fusion, Journal of Ambient Intelligence and Smart Environments 2: (3) ((2010) ), 271–286. |
[31] | V. Senniappan, J. Subramanian, E.I. Papageorugiou and S. Mohan, Application of fuzzy cognitive maps for crack categorization in columns of reinforced concrete structures, Neural Computing & Application, in press. doi:10.1007/s00521-016-2313-9. |
[32] | H. Shen, Y. Zhu, T. Liu and L. Jin, Particle swarm optimization in solving vehicle routing problem, in: Proceedings of the Second International Conference on Intelligent Computation Technology and Automation, Vol. 1: , (2009) , pp. 287–291. |
[33] | Y. Shi and R.C. Eberhart, A modified particle swarm optimizer, in: Proceedings of the 1998 IEEE International Conference on Evolutionary Computation, IEEE Press, Piscataway, NJ, (1998) , pp. 69–73. |
[34] | D. Simon, Biogeography-based optimization, IEEE Transactions Evol. Computing. 12: (6) ((2008) ), 702–713. doi:10.1109/TEVC.2008.919004. |
[35] | N.G. Singh and M. Joshi, Optimization of location and number of sensors for structural health monitoring using genetic algorithm, Materials Forum 33: ((2009) ). |
[36] | Y.-l.Tang, Y. Luo, L.-f. Huang, J. Guo and Y. Lei, Wireless sensor network for on-line structural health monitoring, in: The 7th Int. Conference on Computer Science & Education (ICCSE 2012), Melbourne, Australia, July 14–17, (2012) . |
[37] | N.H. Vaidya, P. Bahl and S. Gupta, Distributed fair scheduling in a wireless LAN, in: Proc. 6th Annual Int. Conf. on Mobile Computing & Networking, (2000) , pp. 167–178. |
[38] | T. Wan and C.K.Y. Leung, Fibre optic sensor for the monitoring of mixed mode cracks in structures, Sensors and Actuators A: Physical 135: ((2007) ), 370–380. |
[39] | G. Wang, L. Guo, A.H. Gandomi et al., Levy-flight krill herd algorithm, Math. Probl. Eng. 2013: ((2013) ), 1–14. |
[40] | G.Wang, L. Guo, H. Wang, H. Duan, L. Liu and J. Li, Incorporating mutation scheme into krill herd algorithm for global numerical optimization, Neural Comput. Appl. 24: (3–4) ((2012) ), 853–871. |
[41] | G.G. Wang, A.H. Gandomi and A.H. Alavi, An effective krill herd algorithm with migration operator in biogeography-based optimization, Applied Mathematical Modelling 38: ((2014) ), 2454–2462. doi:10.1016/j.apm.2013.10.052. |
[42] | M.-Y. Wang, J. Ding, W.-P. Chen and W.-Q. Guan, SEARCH: A stochastic election approach for heterogeneous wireless sensor networks, IEEE Comm. Letters 19: (3) ((2015) ). |
[43] | K.R. White, J. Minor and K.N. Derucher, Bridge Maintenance, Inspection and Evaluation, Marcel Dekker, New York, (1992) . |
[44] | S. Yi, Q. Jiang and K. Zhang, A clustering scheme for reachback firefly synchronicity in wireless sensor networks, in: 3rd IEEE Int. Conference on Network Infrastructure and Digital Content (IC-NIDC), Beijing, 21–23 September, (2012) , pp. 27–31. |
[45] | O. Younis and S. Fahmy, HEED: A hybrid energy efficient, distributed clustering approach for ad hoc sensor networks, IEEE Trans. on Mobile Computing 3: (4) ((2004) ), 366–379. doi:10.1109/TMC.2004.41. |
[46] | H. Yua and W. Xiaohuia, PSO-based energy-balanced double cluster-heads clustering routing for wireless sensor networks, Procedia Engineering 15: ((2011) ), 3073–3077. doi:10.1016/j.proeng.2011.08.576. |
[47] | G. Yuan-Liang and X. Wen-Bo, Study on automatic test generation of digital circuits using particle swarm optimization, in: Proceedings of the Tenth International Symposium on Distributed Computing and Applications to Business, Engineering and Science, (2011) , pp. 324–328. |




