Edge computing in IoT for smart healthcare
Abstract
The rapid advances in the Internet of Things (IoT) and the increment of its users have opened a door to put into service IoT in healthcare, known as the Internet of Medical Things (IoMT), which consists of cloud, fog, and edge computing. IoMT has shown to be a flexible framework to remove traditional healthcare limits through utilizing technology/techniques and innovative digital devices to monitor patients’ conditions and to address medical service problems such as inaccuracy and long response time. It also could be helpful within critical and unexpected circumstances like epidemic diseases. Fortunately, some methods, including Edge Computing, were introduced to improve the healthcare system, make it more effective and solve problems. In this work, a Systematic Literature Review (SLR) was used to study Edge Computing solutions in healthcare, evaluate efficient therapeutic approaches, and demonstrate key factors that have not been considered in previous studies.
Abbreviations
AoI | Age of Information |
API | Application Programming Interface |
AQ | Analytical Questions |
CH | Cluster Head |
CoAP | Constrained Application Protocol |
DNN | Deep Neural Network |
DoS | Denial-of-Service |
DTLS | Datagram Transport Layer Security |
ECC | Edge Cognitive Computing |
ECG | Electrocardiogram |
ED | Emergency Departments |
eHealth | electronic Health |
Fri-jam | Friendly jamming |
HMWWO | Hybrid Modified Water Wave Optimization |
HR | Heart Rate |
IoT | Internet of Things |
IoMT | Internet of Medical Things |
LDM | Left Data Mapping |
LOS | Length of Stay |
MEC | Mobile Edge Computing |
MQTT | Message Queue Telemetry Transport |
NB | Narrowband |
PRM | Pixel Repetition Method |
RPN | Resource Preservation Net |
RR | Respiratory Rate |
SDN | Software Defined Network |
SLR | Systematic Literature Review |
SpO2 | blood oxygen saturation |
WBAN | Wireless Body Area Network |
MF-GAM | Multi-stage Feature extraction Generative Adversarial Network |
1D-CNN | One-dimensional convolutional neural network |
MEC | Medical Edge Computing |
RNN | Recurrent Neural Network |
SGX | Software Guard Extension |
VR | Video Restoration |
ECG | Electrocardiogram |
TP | Trigonometric Projection |
DER | Detection Error Rate |
BSA | Battery Smoothing Algorithm |
QoS | Quality of Service |
PMR | Peak-to-Mean Ratio |
BSA | Battery Smoothing Algorithm |
1.Introduction
The Internet of Medical Things (IoMT) utilizes networks, sensors and applications to establish a connection between healthcare and information technology. Using these devices in healthcare has evolved as a result of modern technologies. Because of the emerging focus on IoT technology, it is now possible to use IoT-based platforms in medicine to improve clinical records and healthcare services. Moreover, some measurements could be analyzed within a few minutes, which would prove beneficial to medical staff in crisis like COVID-19 [7,79]. Traditional healthcare limitations are covered through the use of technology and new smart devices. World health is facing serious challenges as epidemic diseases like Covid-19 [47] spread throughout the globe. Population growth, living in densely populated cities, is a leading factor to a rise in disease, adversely affecting societies as well as countries’ healthcare systems. Healthcare platforms are not able to eliminate healthcare issues, and sometimes the problems of patients will not be resolved with treatment. However, it is true that technology is used in medicine to reduce healthcare costs and problems in many ways, and one of them is IoMT. In the healthcare sector, the IoMT revolutionized the way medical services were provided [23,58]. The IoMT system can eliminate needless medical visits by linking patients with their doctors and offering a secure network for medical professionals to view their medical data remotely, especially during epidemic. Moreover, new solutions to the combination of tag data and historical data from the devices to help detect abnormal daily activity patterns remotely developed [29]. Figure 1 shows an Edge computing-based solution to connect the patient to medical professionals. Consider the fact that medical-based Internet solutions would be ideal for patients with disabilities, in contrast to traditional services [57].
Fig. 1.
Edge computing-based patient treatment.
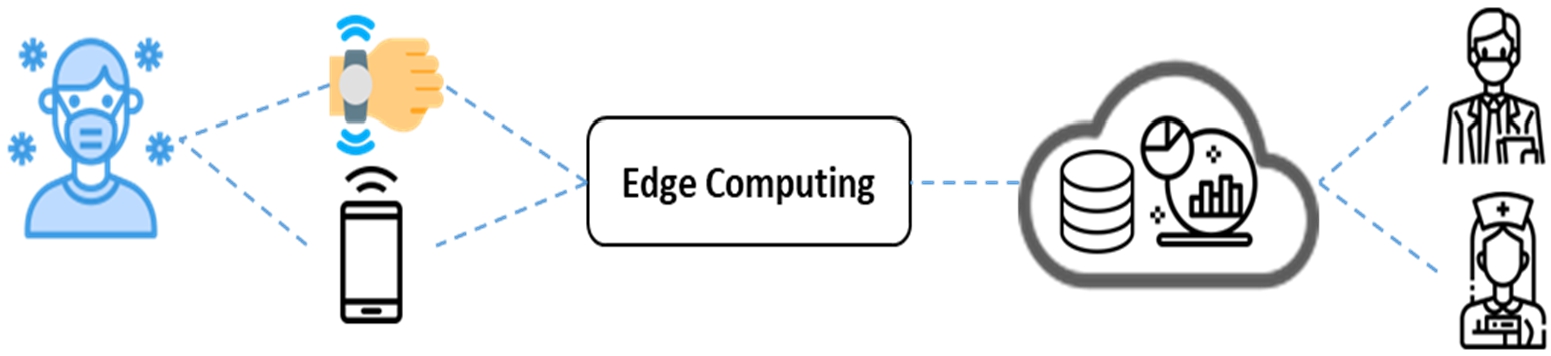
Fig. 2.
Three-tier layers of IoMT architecture.
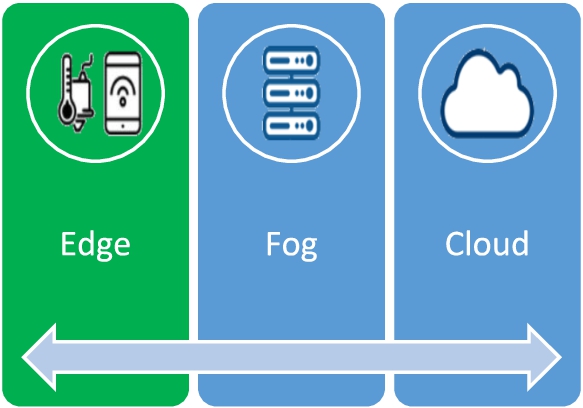
Each IoMT system’s architecture may contain cloud computing, fog computing, and edge computing. Figure 2 demonstrates each of these layers, with their specifications and resources. Despite their similarities, the three layers function differently and are different from each other. The Cloud computing layer might be a location for data processing as well as a data center where data is produced for future usage and analysis. Despite its location between the cloud and edge computing, the fog layer provides local networking, control, standardization capabilities, and data analysis. The fog layer is one of the most important layers of IoMT Architecture which has attracted attention of experts to solve different challenges. For instance, Quy et al. [62] proposed a common architectural framework based on fog computing for Internet of Health Things (Fog-IoHT) applications. The study covered solutions into three categories based on approach, including performance, security, and offloading. This paper describes the edge layer that performs computations nearby medical sensors and is located close to the network’s nodes. Medical treatment using edge computing-based healthcare systems contribute significantly to reduce healthcare costs in IoMT environments. There are also for modeling of IoT in Smart Healthcare some solutions developed. For instance, Ouchani et al. [51] aimed to improve smart healthcare by modeling IoT systems that address emergency services. They did this by developing a Healthcare Management System (HMS) using UML diagrams to initiate a modeling mechanism. There are also some other useful papers that need to be investigated. Bonfanti et al. [11] utilized formal methods to systematically model, design, develop, verify, and validate software-intensive medical systems.
1.1.Why edge computing
Increasing IoT-based solutions and widespread use of wireless networks has led to a proliferation of edge devices and data generated from the edge. Edge-related concepts refer to a distributed computing paradigm that deploys processing and storage resources at the production site of data as close as possible to the point of data creation. Edges are more than just hardware. It also includes software, services provided (Service is supplied by one party to another), and professional services (Special services to bootstrap commercial IoT products). In general, healthcare solutions with edge-based IoT deploy systems that use different types of smart sensors to implement diagnostic, sensitive, and preventive healthcare systems [3]. Shi et al. [72] defined edge computing as a technology that allows computation at the edge of the network on behalf of cloud services and upstream computing. By 2025, more than 75% of the new IT infrastructure will be available at the edge, up from less than 10% today [1]. Edge computing has the advantages of low latency and high responsiveness, making it an essential companion to cloud computing and opening up new possibilities for a variety of intelligent applications. It still confronts several potential issues, including remote configuration, a well-defined native application paradigm, and restricted node capacity [74]. Various hard challenges in cloud computing, such as processing complexity and increased latency, paved the way for accessible solutions and efficient ways. Edge and Fog computing have surpassed the traditional approach by allocating resources effectively and fairly, such as energy and battery life, in the IoT-based industrial applications [76,77]. For example, the study [32] presented an effective Edge Computing (EC) management system for IoT applications in smart cities to minimize service response times. The core structure of this system is a small database (referred to as an information map) that allows smart city edge computing servers to store edge service information. When mobile end-users migrate to the new edge server-managed overlay, EC service-related features exchange between edge servers. The simulation results revealed that the suggested approach is more efficient than the old method in terms of service response time and energy usage.
There is a discussion of motives in the area of application. They all have lucrative goals. It is to improve the quality of human life. Therefore, real-time, energy efficiency, security, cost, reliable information, and efficiency are important metrics in these applications and services. Reading some related surveys and review articles, you won’t find basic useful information about IoMT applications. This study’s core approach is edge computing in IoMT applications; the research chosen mostly covers patient monitoring, remote maternity, telemedicine, remote diagnostics, predictive maintenance, virtual home support, and fall detection.
Fig. 3.
Location-based IoMT devices and services.
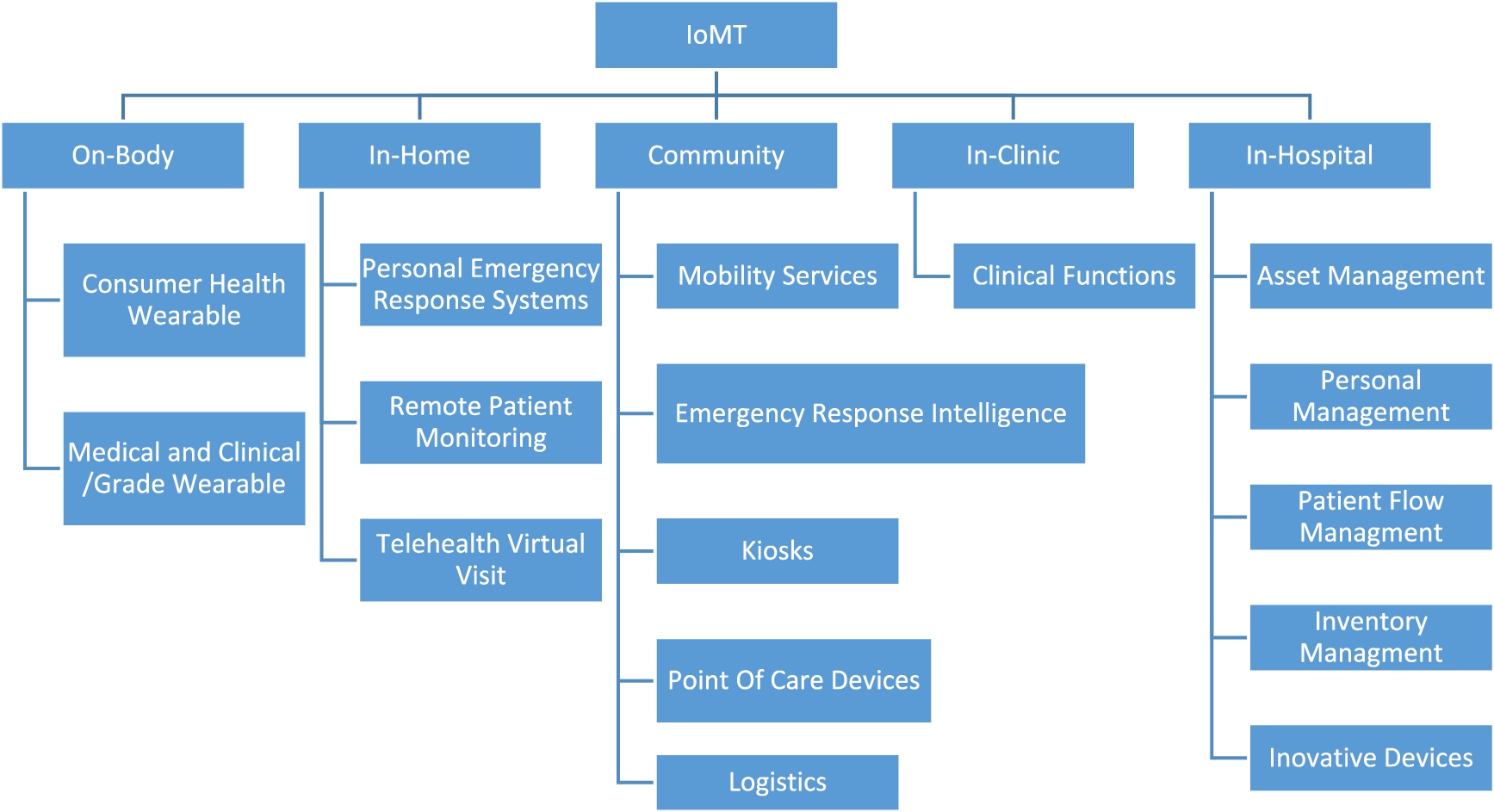
Figure 3 shows a diagram of a location-based intelligent health system based on new technology. In location-based Devices and services are categorized based on their environment including On-body, In-home, Portable, In-clinic, and In-hospital. On-body: These types of devices are attached to an individual’s body and gather medical data. On-body devices can be either consumer- or medical-grade. For instance, smartwatches are consumer-grade, on-body IoMT that collects health information such as heart rate and blood pressure. Consumer-grade smart devices can be utilized for wellness and health-metric tracking without medical supervision. Medical-grade, on-body IoMT is employed under the guidance of a physician. For example, ingestible sensors that obtain information from within the patient’s body. In-home: Devices are utilized or situated in or around a patient’s dwelling. For instance, personal emergency response systems make use of devices within the home that sends an alert to a hospital in the event of an emergency experienced by the patient. Community: These devices are spread out across a geographical region. They provide patients in remote locations without conventional medical facilities the ability to access healthcare and healthcare systems. In-clinic: devices employed for administrative or clinical purposes, such as examination platforms based in the cloud. In-hospital: Hospitals utilize internet connectivity to aid in patient care. Hospitals also employ IoMT devices for the management of assets and inventory. RFID tags affixed to medical equipment and supplies transmit updates to hospital personnel regarding the quantities they have on hand and their locations. Similar devices are also used to monitor the movement of patients through facilities.
The ideal and fundamental strategy of IoMT systems is to reduce traffic and reaction time at the network edge, and difficulties associated with heavy traffic may be considerably addressed by approaches such as data reduction and clustering. On the other hand, Edge computing manages millions of sensor nodes and medical devices because of the benefits of the IoT and control and manage large devices without human intervention to become an important solution during critical times like COVID-19. Instead of cloud computing with centralized processing, edge computing pushes data computation to close sensor nodes. By using this strategy, latency, response time, and energy consumption can all be reduced as well as low bandwidth requirements compared with cloud computing. Through an analysis of the research literature, this study seeks to map out the IoT features that are used in the medical field. A classification of the IoMT research area, including contributions according to the categories identified in the classification, was developed [56].
1.2.Some emerging technonolies in smart healthcare
Smart environments and Internet of Things in healthcare have become prevalent in recent years as sensor costs have decreased and signal processing techniques have improved [13]. Advances in wireless technologies such as 5G which is designed to improve network performance for greater bandwidth, reliability and lower latency. Moreover, the next generation, called the 6G network is considered a platform conducive to innovations in computing, artificial intelligence, connectivity, sensors, virtualization, and more. The 6G is designed to meet the requirements of higher global coverage, greater spectral efficiency, and a reduced carbon footprint, emphasizing sustainability, equity, trust, and security through unprecedented architectural evolutions and technology. Thus, edge computing-based solutions can gain more benefits from these reliable networks and services. The study [61] focused on identifying a complete picture of changes in architectures, technologies, and challenges that will shape the 6G network. Due to these advances in communication and computation technologies, some technologies such as Digital Twin (DT), Metaverse, and Blockchain have been introduced. DT is a comprehensive solution connecting the physical and digital spaces. It allows the construction of a virtual representation of physical objects. DT technology has been applied in a series of areas across multiple levels to monitor, control, and optimize physical objects.
IoT has recently been researched in the context of the Metaverse in order to give users with immersive cyber-virtual experiences in mixed-reality environments [38,61]. The collaborative healthcare is one of these applications. Li et al. [38] extensively evaluated four pillar technologies that allow augmented reality (AR) and virtual reality (VR) in the IoT-inspired Metaverse, namely responsible artificial intelligence (AI), high-speed data connectivity, cost-effective mobile edge computing (MEC), and digital twins. Furthermore, their study discusses the unresolved concerns in the IoT-inspired Metaverse that must be addressed in order to realize the eventual merger of the physical and cyber worlds.
1.3.Contribution and motivation of the study
Identifying the types of applications of IoMT by creating a technical taxonomy
Explain the presented study by expressing its superiority over other similar studies with a closer look at Edge Computing
Discussing and illustrating the main challenges of the IoMT applications
Identifying the types of solutions to try to overcome IoMT challenges
Investigation of important parameters in IoMT and its contribution to studies
Displaying the importance of IoMT in times of epidemic diseases
Showing a clear path and understanding of the research challenges for future study
Edge computing is a rapidly growing field that has the potential to unlock the full potential of IoT by reducing connectivity costs, bringing faster response times, reducing network congestion, and improving reliability. These benefits make edge computing an attractive subject for research. Researchers are interested in exploring various aspects of edge computing in the IoT environment.
The remaining section of this study provides an overview of related surveys in Section 2. Section 3 provides information about the research selection technique. Section 4 categorizes and summarizes the different approaches to applications in IoMT. Taking a deeper look at IoMT applications in Section 5 that have not been thoroughly analyzed. The article is then concluded in Section 6.
2.Related surveys
An overview of related IoMT-based applications is presented in this section. Quy et al. [62] present a comparison of cloud computing, edge computing, and fog computing and present a fog-based architecture for the Internet of Health Things (Fog-IoHT) applications. Fog computing and IoT Healthcare applications are also discussed in the article, along with challenges and opportunities.
An article published by Ray et al. [64] examined edge computing technologies for the Internet of things. The important aspect of the article is categorizing industrial edge-IoT computing and analyzing various parameters involved in it. A discussion of each of the taxonomical components in detail has been done. It covers a wide range of industrial software, analytics, edge-IoT ecosystem, edge-IoT cloud platform, etc. The second section presented two practical use cases, such as Waggle and Array of Things, that have recently used the edge-IoT paradigm together to solve urban smart living problems. The third part of study is a novel edge-IoT-based e-healthcare architecture called EH-IoT, and a demo test-bed was developed. In general, the article examines the issues expressed in a discrete manner also there is no clear state of its usability, and no method for comparison is mentioned.
Using a mapping survey, Behmanesh [10] examined the Internet of things in medicine. This article summarizes the IoT applications in medicine and examines the technical aspects of the Internet of Things-based platform. The advantages of CoAP (Constrained Application Protocol) over MQTT (Message Queue Telemetry Transport), storage and computational challenges, operating systems for low-power IoT devices, new technologies such as BLE (Bluetooth Low Energy), NFC (Near-field communication), Zigbee 6LoWPAN (a standards-based wireless technology), 5G/B5G, programming languages, and microcontrollers were among the gaps discussed. This study illustrates some of the technical aspects of several studies articles, which highlight some of the gaps that could adversely affect the use of IoT-based applications within the medical field.
A survey on edge computing and the Internet of things was presented by Yu et al. [84]. Edge computing has been discussed and classified into different groups, and the performance of each of these groups has been evaluated in terms of parameters, including latency, bandwidth occupation, energy consumption, and overhead. In comparison to well-known cloud-based solutions, edge computing is advantageous in reducing transmission latency, reducing response time, and simplifying computation on nodes that takes into account security issues, availability, integrity, and confidentiality. In analyzing studies for integrating edge computing and IoT, it can be seen that this type of system lets users have some smart applications that run with low power and real-time response. Even so, managing resources, maintaining security and privacy, and communicating have been highlighted as challenges. For an in-depth examination of privacy-preserving within the IoT, Yaraziz et al. [83] deliberated on its orientations and encountered challenges.
By using cutting-edge deep learning algorithms, Amin et al. [8] investigated a type of edge intelligence that specializes in categorizing health data with the detection and counting of vital signs. Also included is a comprehensive study of the use of artificial intelligence-based techniques for classified and predictive functions in edge intelligence. In this study, several drawbacks such as data quality, data availability, and real-time processing were clarified in a situation where prevention and timely detection of symptoms are the main concerns. Useful research recommendations are identified in this study that improves edge computing services for healthcare to offer a higher quality of life to patients. Nevertheless, this investigation presents a good evaluation and discussion, which clarifies several artificial intelligence techniques and ML and DL techniques such as AI-driven Data Analytics-based Spectrum Allocation (ADASA). However, it does not discuss the approaches from the exactly edge-based application point of view.
A study conducted by Hartmann et al. [28] investigated edge computing challenges in smart healthcare systems. It includes architecture and IoT-based systems, security and latency issues, and security awareness. It provides an overview and cloud, cloudlet, and edge-based models, architectures, and functions to open up a new avenue of research and provide more insight into the pros and cons of these solutions. Edge computing is an interesting solution to address the problem of low latency processing for IoT devices as the main objective of this study.
A detailed survey was carried out by Kumhar et al. [34] to investigate the significance of SDN and edge computing in the field of health care. The combination of Edge Computing and SDN appears to be a promising structure for use in IoT applications. This combination has some challenges and without solving those issues such as Resource allocation, scalability, heterogeneity, availability, security, and privacy the implementation will encounter with difficulties. This study illustrates some of the technical aspects of limited studies articles, which highlight some of the issues that could adversely affect the use of SDN-based applications in Edge computing.
In order to minimize service response times for IoT applications in smart cities, Quy et al. [61] presented an effective Edge Computing (EC) management system. The server of the system stores edge service information in a small database. EC services-related features are shared between edge servers when mobile end users migrate to the new overlay managed by edge servers.
2.1.Analysis of reviewed survey papers
Table 1 presents related studies demonstrating the major subject of IoMT applications as part of a summary of relevant works and research for better understanding of IoMT applications. The main contexts of papers include network parameters management, AI in edge computing, the Industrial aspect of IoT, and protocols/techniques.
Table 1
Related studies in IoMT applications
| Reference | Main Topic | Key Factor | Limitations | Publication Year |
| Yu et al. [84] | Edge computing for IoT | Comparing Edge/Cloud Solutions | Inconsistency of content | 2018 |
| Amin et al. [8] | Cutting-edge AI-based classification | Brief overview of AI in Edge | Contains content outside of Edge | 2020 |
| Ray et al. [64] | Classification of industrial edge-IoT | Categorizing industrial, Healthcare edge-IoT | Evaluation in discrete manner | 2019 |
| Hartmann et al. [28] | Challenges of edge computing in healthcare | Highlighting low latency processing | Without comparing solutions | 2019 |
| Behmanesh [10] | IoT applications in medicine | Focus of protocols and technologies | Describe some solutions | 2020 |
| Kumhar et al. [34] | Edge Computing in SDN-Enabled IoT | The importance of SDN and Edge Computing | Mostly focus on latency | 2022 |
| Quy et al. [62] | Fog computing for IoMT | Comparing Edge/Fog/Cloud Solutions | Mostly focused on Fog | 2021 |
| Quy et al. [61] | Edge computing for smart cities | The importance of Edge on smart cities | Content outside of smart healthcare | 2023 |
2.2.Aim of doing presented study
According to a comprehensive study on Edge Computing, no study has clearly addressed this issue. Studies have not shown why they have not exactly addressed Edge Computing despite the wide range of solutions proposed in the literature. For example, Ray et al. [64] examines three branches of the Edge category in the areas of smart city, industry, and healthcare without going into detail. It also does not specifically focus on the role of IoT in healthcare. Behmanesh et al. [10] also goes on to describe some of the technologies such as wearable, cloud, wireless communication, microcontrollers, operating systems and etc used in IoMT. Amin et al. [8] also describes approaches based on artificial intelligence in Edge. It gave a short summary of how AI and IoT are commonly used in Smart Healthcare. Hartmann et al. [28] provides an overview of the Cloud, Cloudlet, and Edge-based models and focuses more on low-latency processing in IoT devices. Kumhar et al. [34] present a review of the importance of SDN and edge computing, with a particular emphasis on different IoT applications that have specific latency needs.
In this study, the authors cover important indicators that are essential and critical in smart health care, as well as describe in detail the shortcomings that are not expressed in related methods. This study focuses on the role of Edge Computing in healthcare by putting the spotlight on factors such as computational complexity, energy efficiency, Real-Time, security, and privacy.
Based on literature reviews, the following comparisons are provided:
Hardly to determine what would be an optimal approach to healthcare from the studies
Lack of a clear approach for combating the spread of infectious illnesses like COVID-19
Real-time data access has become common in healthcare; several papers have merely addressed it in passing
3.Research selection method
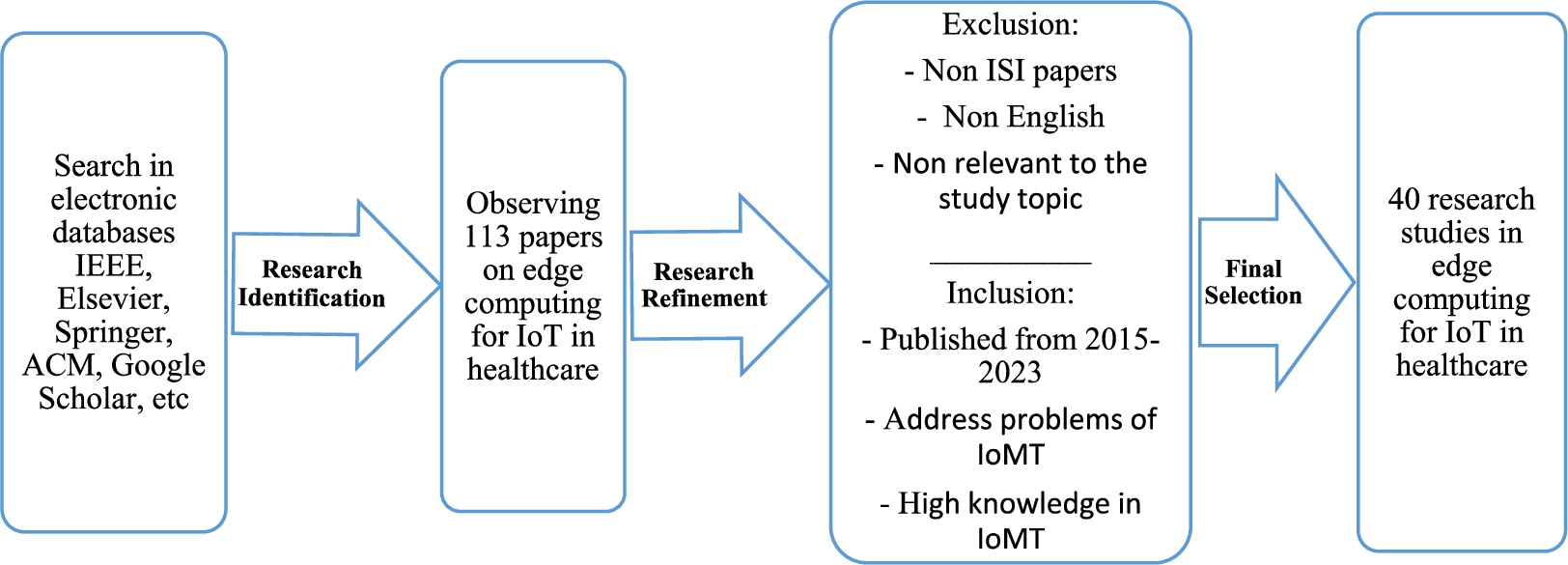
A systematic literature review (SLR) method was used to examine IoMT and edge computing applications. The main objective of this research is to show how healthcare IT systems, solutions, protocols, and technological advancements can effectively address healthcare challenges. Figure 4 illustrates the research methodology for this SLR-based study.
Fig. 4.
The criteria for selection and the chart on evaluating research findings.
Following are the analytical questions (AQ) on which this SLR paper offers clear responses:
(1) What are the primary reasons for selecting an Edge-based application as a robust healthcare solution?
(2) What kind of maintenance and upgrade process will be used in Edge-based Healthcare?
(3) What methods may be used to alleviate issues in Edge-based healthcare?
(4) What are the major IoMT Edge-based domains?
(5) Which main contexts are considered for Edge computing applications?
(6) In IoT-based healthcare, what security/privacy has been used?
(7) What technologies have had an impact on the evolution of this field?
(8) What schemes have been taken to make remote monitoring healthcare sustainable?
(9) What are the significant gaps and open questions for future research directions?
The articles considered were published from 2015 to 2023
The research focuses on IoMT applications
In the field of IoMT, high-quality articles
Research papers to address IoMT-related issues
The papers do not include any novel or important ideas
Articles, conferences, and technical reports that have not been accepted for publication in reputable journals
Articles are written in a language other than English
The research papers that were published before 2015
Papers that are unrelated to the research subject
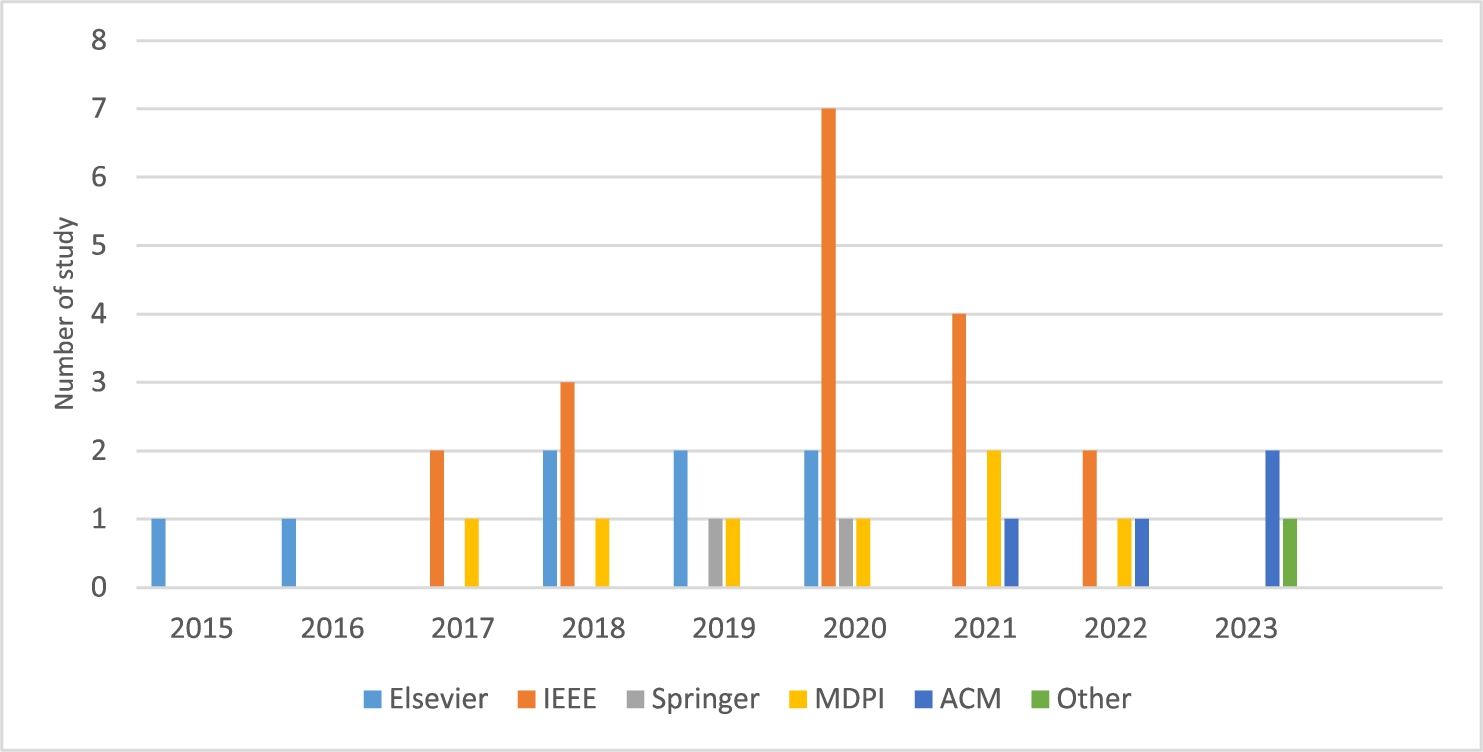
Fig. 5.
Publishers’ research papers distribution.
4.Edge-based IoMT applications
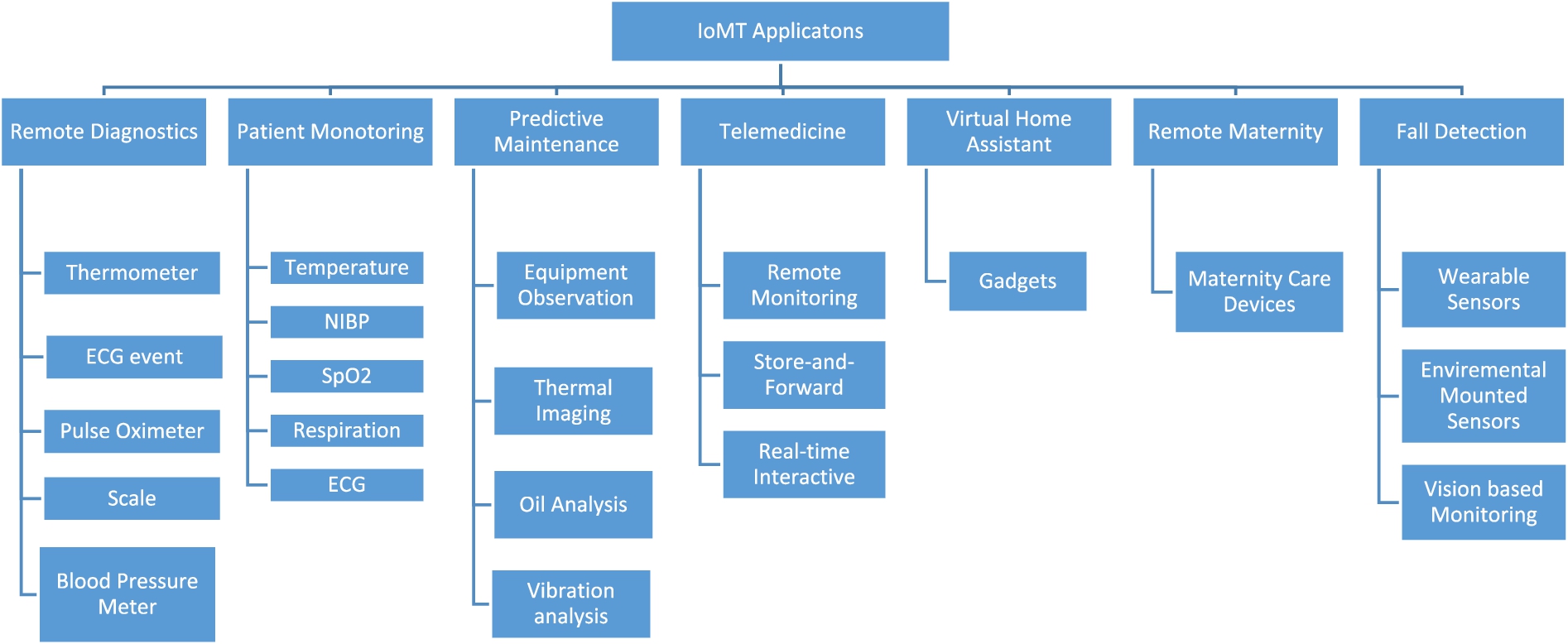
This section demonstrates how to apply the SLR method to a technical assessment of literature research in the IoMT discipline. Patient monitoring (ex: personalized healthcare system with monitoring vital signs of patient [59]), remote diagnostics, predictive maintenance, telemedicine, virtual home assistants, remote maternity care, and fall detection are examples of IoMT uses in healthcare, as illustrated in Fig. 6. According to several research, each one offers a viable solution for overcoming some of the challenges associated with supporting IoMT applications in one or more domains. In general, various obstacles were faced in each study topic, making the IoMT a unique way for solving problems and improving healthcare quality among other technologies. As a result, a number of desirable properties, such as security, increased dependability, and gradual adaptation (step by step adaption to the IoMT), make IoMT beneficial in eHealth and medical services. IoMT, like other systems, have issues at any application level. Heart rate (HR), respiration rate (RR), SpO2 (blood oxygen saturation), temperature, and other indicators, for example, might be troublesome in a remote healthcare system. The systematic mapping process [56] was used to extract data from selected research papers. The study’s contribution to clustering and categorizing the map has been examined after finding the ideas, keywords and assessing them. The following context presents IoMT applications with categories that include Blockchain, AI (Artificial Intelligence), 5G, and general aspects. The next section of this paper includes the study of IoMT applications. Moreover, the authors compared various solutions in terms of case studies, major fields, advantages, and drawbacks.
Fig. 6.
The taxonomy of IoMT based applications and services.
4.1.BlockChain applications
Nguyen et al. [48] developed an integrated Mobile Edge Computing (MEC) and blockchain architecture in a distributed health network for data offloading and data sharing called BEdgeHealth. First, mobile devices can send their health data to a nearby MEC server to achieve efficient computing with privacy awareness. The MEC server is a coordinator that provides low-latency computation services in order to manage a group of mobile devices within the hospital. MEC enables decentralized user access verification at the network edge without relying on any central authority by including a smart contract-based authentication mechanism that provides authentication reliability and reduces network latency. Second, an integrated data sharing system that uses blockchain and interplanetary file systems to enable data exchanges between healthcare users. Generally, the proposed offloading scheme has demonstrated a significant advantage over the other baseline methods regarding reduced time latency, decreased energy consumption, and higher memory utilization. This approach also reveals a high level of system security.
The work in Ejaz et al. [24] suggested an easy-to-use, secure, and reliable remote monitoring and care service for senior citizens at their homes called Health-BlockEdge. Under the study, it is recommended that edge computing and blockchain technology be used to solve some of the major requirements for smart remote healthcare systems, including long operating times, resilience to network problems, low cost, security, and trust in highly dynamic network conditions. Health-BlockEdge brings processing and computational operations close to the users and digital devices in order to make real-time data analysis and decisions and to optimize resource usage. In addition, adding a blockchain to the proposed healthcare use case enables a number of highly relevant characteristics for its implementation, such as trusted data sharing, secure monitoring or tracking of various processes and their phases, and keeping patient records in electronic form. The analytical comparison demonstrated that blockchain and edge computing together could be used to support decentralized trust, control over the network, real-time access and computational capacity in the healthcare aspect while maintaining a high level of system performance and resource efficiency.
Dai et al. [18] presented a secure solution for dealing with COVID-19 utilizing blockchain technology. The author used blockchain technology and IoMT in this study to address the security and privacy of IoMT systems. To evaluate the proposed strategy, five factors include medical data provenance, tracing the pandemic origin, smart hospitals, quadrating and social distance, and remote healthcare and telemedicine are used. In a nutshell, IoMT-based systems can easily provide authentication and access control on both the edge computing and blockchain layers thanks to integration. The proposed technique might be a way to deal with COVID-19 illness while maintaining security in the IoMT environment. The recommended technique, on the other hand, requires greater explanation in order to provide a clear response to new medical concerns.
Gao et al. [25] were the first to propose a new framework for remote medical diagnosis and monitoring with edge computing and blockchain. In order to ensure the confidentiality of the data analysis process, SGX (Software Guard Extension) technology is implemented in the edge computing environment. IoMT devices and cloud service providers are authenticated through the blockchain, and credentials for IoMT data can be managed via access policies. In this approach blockchain is responsible for digesting IoMT data and managing the access strategy. Some modern Intel central processing units (CPUs) include a security-related set of instruction codes called Intel Software Guard Extensions (SGX). These technologies allow programs running at either the user or operating system level to define private portions of memory, called enclaves, whose contents can’t be read or saved by the process outside the enclave, including processes running at the higher privilege level [2]. SGX technology is enabled on the edge server to ensure that IoMT data can be safely and securely processed. Thus, the framework comprises a blockchain consortium network, an IoMT environment, trusted edge computing layers, and cloud service layers. Due to the analysis of this method, the following parameters, including authenticity, confidentiality, and integrity ensured. Moreover, data confidentiality is guaranteed by cryptographic algorithms and hardware-based SGX technology.
Sharma et al. [70] introduced a privacy-preserving Distributed Application (DA) that uses blockchain technology to create and manage healthcare certificates. The DA acts as an intermediary between the blockchain network and entities such as healthcare centers, verifiers, and authorities to produce and issue medical documents. It employs several smart contracts for user registration, certificate generation and verification, attack prevention, and user access. The scheme’s performance was evaluated through experiments using the Etherscan tool to measure operation cost, latency, and processing time. The results showed that the proposed method is more efficient in terms of latency, throughput, and response time compared to existing techniques. However, the transaction and execution costs increase with the number of medical certificates as the number of blocks in the blockchain structure increases.
Makina et al. [41] designed a system that combines edge computing, blockchain technology, and the InterPlanetary File System (IPFS) to provide data confidentiality, integrity, fine-grained access control, and real-time data processing. Blockchain technology is used to ensure that data is accurate and traceable. Smart contracts provide fine-grained access control while IPFS provides distributed file storage and eliminates the risk of a single point of failure. An edge layer is also integrated to process eHealth emergency data from IoT devices in real time. This ensures that medical data is processed throughout its entire lifecycle.
4.2.AI (artificial intelligence) applications
Kong et al. [33] introduced an edge computing-based mask identification framework (ECMask) with deep learning to support public health precautions and ensure real-time performance on low-power camera devices on the bus. An identification system has been developed to identify the mask-wearing state in real-time from the bus driver tracking video. ECMask consists of three main phases: video restoration (VR), face recognition, and mask identification to prevent COVID-19 infection and provide real-time public health prevention reminders. Monitoring data is sent to high-performance devices for additional model training and then to edge devices for real-time testing. In the real-time image analysis part, image blur detection using the Laplace operator can be performed to determine whether VR is necessary, thereby reducing the huge computational cost related to VR. Real-time video data are then sent to subsequent models for recognition and identification results. These results will be returned to the administrator for display. Generally, based on the dataset for monitoring the real bus, the results illustrate that VR can improve detection accuracy. This method shows excellent performance in terms of output time efficiency of overall video analysis.
Manogaran et al. [42] used a bayesian deep network system on edge computing to recognize and analyze human body activities in an IoT environment. It’s a multi-access physical monitoring system based on smart logs. In this study, smart log-based techniques on multimedia technology were developed to address inefficiencies in the healthcare business. The system attempted to analyse data provided by IoT sensors and combining multimedia technology with edge computing to track human behavior and employing agile learning for lifetime analysis. As a result of simulation and comparison with other similar methods, this method are more efficient in terms of residual error, latency, and energy consumption than other approaches. The suggested technique would be more accurate and efficient. However, there are certain disadvantages to this strategy. Putting computation and analysis near sensors brings a big process and operation close to the sensors, which requires more energy than data sent to the cloud or processed via fog computing. On the other hand, close gadgets require more energy to function over an extended period of time.
ETS-DNN (“Effective Training Scheme for Deep Neural Network- Deep Neural Network”) is a training schema provided by Pustokhina et al. [60] for the Deep Neural Network model driven by edge computing in the IoMT system. A healthcare monitoring system that operates in real time has unquestionably become a prerequisite in medical therapy. As a result, the proposed approach to diagnose acquired data was used to make timely judgments after detecting patients’ conditions in edge computing. The ETS-DNN model employed a HMWWO (Hybrid Modified Water Wave Optimization) technique to adjust the parameters of the DNN structure, and finally, an SM classification layer was added to the model for classification. As a consequence, the ETS-DNN method generates a patient data report and transmits it to a cloud server for further analysis by medical personnel. The investigation results demonstrate that the proposed technique performed well in terms of low latency metrics compared to other methods.
Md. Z. Uddin in [80] proposed a human activity prediction system in a smart healthcare environment using Recurrent Neural Network (RNN). For predicting human activities, gathered data from multiple wearable healthcare sensors that include twelve different human activities are trained by RNN deep learning technique. RNN technique has been elected in this system to model time-sequential information. When compared to other approaches such as Hidden Markov Models (HMM- a statistical model that assumes a Markov process as the system being modeled) and Deep Belief Networks (DBN- in DBNs, multiple layers of latent variables (“hidden units”) are arranged in layers, but units within layers do not have connections between them.). Despite the capabilities of those approaches, this method still outperforms them in terms of prediction rate. That means this shows the proposed method could be the more efficient multimodal system for real-time analyzing and activity prediction in the smart health care environment.
Rahman et al. [63] proposed a framework for tacking COVID-19 by developing a deep learning technique in IoMT environment to detect and identify known types of COVID-19 symptoms. The edge nodes have been major points of the system to run deep learning algorithms to process sensed and detected data. Using the edge-GPU (Graphics Processing Unit) architecture could provide user data privacy, security, and low latency in data computing. One of the advantages of this approach could be fast detection, remote detection, low cost, and efficiency in tackling coronavirus disease. On the other side, the weakness is that the emergence of a new type of COVID-19 requires changes to the system, which will lead to uncertainty in its performance.
Shen et al. [71] use multiple Deep Reinforcement Learning (DRL) agents deployed on IoT devices to guide computation offloading decisions. Besides, Federated Learning (FL) is utilized to train DRL agents in a distributed fashion, aiming to make DRL-based decision-making practical and further decrease the transmission cost between IoT devices and Edge Nodes. This approach has several benefits including energy efficiency, speed, and the preservation of privacy. However, it also has some drawbacks. For instance, FL-based DRL training may not perform well during training and may take longer to converge. FL-based DRL training may not be as effective as centralized training.
Jourdan et al. [31] developed a framework for IoT devices that uses machine learning to accurately recognize user activity for personal healthcare monitoring while minimizing the risk of re-identification from biometric patterns. They created a protection mechanism that processes raw signals on the user’s smartphone to select relevant features for activity recognition and normalize features that could lead to re-identification. Only a set of features that are not linked to the user’s identity is uploaded to the application server. This allows the server to accurately recognize user activity while reducing the risk of re-identification.
In edge computing-based IoHT networks, Ali et al. [4] proposed energy-efficient multisensor adaptive sampling and aggregation (EMASA). At the edge gateway, EMASA uses machine learning to provide fast and accurate decisions about the patient’s condition, reducing the amount of data transmitted by the sensors, conserving their energy, and reducing the amount of data transmitted by the sensors.
4.3.5G-based applications
Zhang et al. [87] proposed a real-time healthcare system based on MEC (Mobile Edge Computing) and AI (Artificial Intelligent) techniques to monitor patient health status and automatic disease diagnosis. This system is based on the integration of multiple techniques such as 5G, machine learning, MEC, and biomedical devices to the real-time prediction and monitoring of human life characteristics and health conditions. 1D-CNN (one-dimensional convolutional neural network) model used as a machine learning approach to predict and diagnose human disease. So, the 1D-CNN model has been used on the MEC layer to provide real-time heart disease detection. This proposed system could reduce medical responsibility to improve the quality of services. This real-time healthcare system consists of three layers: IoT for gathering produced data, the MEC layer in the middle of a system for data processing, and the cloud layer for storing data and future evaluation. Generally, this work could provide high accuracy of prediction and reduce the cost of health care. The system’s drawback, on the other side, its efficacy has not been assessed using any other approach.
Sodhro et al. [75] proposes the window-based Rate Control Algorithm (w-RCA) to optimize the medical quality of service (m-QoS) in mobile edge computing-based healthcare. By considering the network parameters, for instance, peak-to-mean ratio (PMR), standard deviation (Std. dev), delay, and jitter during 8 min medical video stream named “Navigation to the Uterine Horn, transection of the horn and re-anastomosis” transmission over 5 G networks, the method provide suitable approach. The method highlights three things that include a window-based rate control algorithm for the medical video applications such as Tele-surgery over 5G networks, a mobile edge computing-based 5G framework for QoS optimization, and establishing a tradeoff between client buffer size, window size, and network metrics. Proposed w-RCA is an offline server-side algorithm where the frame rate is controlled by the overlapping of N video frames, and the size of the W window. Because of voluminous medical health data collection from the mobile edge clouds such as Tele-medical news casts video transmission, the server is not able to smooth the complete stream. The w-RCA is periodically applied while the video is transmitted in a new smoothing window each time. For w-RCA development, a method is applied in which a video source creates one data frame per unit of time. The performance of the proposed w-RCA is evaluated and compared with the conventional Battery Smoothing Algorithm (BSA) and Baseline by using a MPEG-4 encoder for optimizing m-QoS at the source or the server-side. The experimental results demonstrate that the w-RCA outperforms the BSA and Baseline by optimizing QoS in remote healthcare applications i.e., Telesurgery. Besides, it is observed and analyzed that w-RCA produces better and more effective results at a small buffer and window sizes, unlike BSA and Baseline by adopting a large buffer size during QoS optimization. The study’s weakness is that a large server buffer is required for the strategy’s performance in big IoT-based systems, as well as increasing client-side playback delays. Furthermore, the major difficulty with these sorts of systems is latency. The time delay not only causes a lengthy process but also causes substantial functional inaccuracy, which can endanger safety and make delivering appropriate service difficult.
Ning et al. [50] developed a distributed GT (Game-Theoretic) strategy for mobile edge computing monitoring. The author employed a decentralized GT strategy with MEC (Mobile Edge Computing) and 5G technologies in the IoMT context to reduce system-wide expenses. Because of the interconnectedness of contemporary life and the lack of time, in-home health monitoring is one of the primary concerns that require more attention. The suggested system is separated into intra-WBANs (Wireless Body Networks) and beyond-WBANs subnetworks. A GT-based formula has been proposed in WBAN for allocating network resources. A distributed non-cooperative game method for minimizing system cost has been emphasized for beyond-WBAN. In summary, the recommended method may reduce system-wide costs and safeguard privacy by employing an efficient strategy that has been studied, and its performance is superior to that of other systems, but the loss of time sensitivity offsets this advantage.
4.4.General aspect applications
To increase the lifespan of IoMT-based networks, Han et al. [27] proposed a clustering approach. Selecting a node as Cluster Head (CH) is one of the essential tasks in the suggested technique, and it plays a significant part in this study. Energy, latency, distance, capacity, and packet queue are among the characteristics used to choose a node as CH. The advantages of this model are that it is more efficient and gives a longer network lifetime than prior models stated in the study. This technique seeks to limit data transit between nodes by designating some nodes as cluster head and requiring other nodes to deliver data to them.
This strategy, on the other side, has substantial drawbacks; the position of CHs in respect to each other and the position of cluster heads in connection to the Sink (Base Station) is crucial. In this technique, a system seeks to collect a list of nodes around the base station and then computes the distance between them to produce a list of nodes from which to choose CH. Nonetheless, the remaining energy of cluster head nodes in close proximity to the base station would dissipate with time, resulting in a network gap between the sink (base station) and normal nodes. Another problem of concern is that local optimization has a detrimental influence on coverage networks; in wide area networks, the position of the cluster head in clusters is matters in preventing network fragmentation, but still, this matter has not been clarified and remains unsolved. Overall, utilizing this strategy to increase network lifespan has certain drawbacks. One of the concerns that this technique raises is how, given the aforementioned approach, it can achieve general optimization and coverage by picking particular nodes as CHs?
Muhammad et al. [46] provided a method for assessing and treating vocal disorders. This method uses smart sensors to collect customers’ voices, then transmits the data to edge computing for initial processing before sending it to the cloud for further processing. The suggested method’s strong suit might be its ability to detect and classify vocal disorders, as well as its accuracy in detecting customers’ voices. The use of data transformation in real time and computing at the edge also allows efficient, near-real-time execution at the network’s edge to enhance network performance, which has the potential to benefit this technology greatly.
The suggested approach, on the other hand, has various limitations, including the need for extra resources to gather data from nodes and send it to the cloud; due to the nature of speech data, no attempt has been made to reduce data in order to enhance network performance. Furthermore, no methodology has been introduced to make safe data transmission in the technique provided. In general, the suggested approach appears to be a viable option for achieving high detection and classification precision.
A real-time QRS detection and R point recognition method was proposed by Chen et al. [14] that maintained high accuracy at low computational complexity. In a trigonometric projection (TP), the R peak is an anchor point to determine displacement value. For rhythm classification, QRS detection is a prerequisite for detecting the heartbeat, so the high QRS detection method is the most significant element of ECG analysis for remote ECG (electrocardiogram) monitoring applications. The new generation of wearable electrocardiogram (ECG) systems requires the use of signal processing with low power consumption. This transmission of data and recording of signals allows users to detect dangerous rhythms and abnormal rhythms. The fiducial point for QRS is determined as a function of crests and troughs of the transformed signal. Based on four QRS waveform templates, the R point can be identified, and preliminary classification of the heart rhythm is also possible. Due to the MIT-BIH arrhythmia benchmark, the approach’s low computational complexity. Implementing the real-time application on a mobile phone or embedded system is also achievable. Testing the proposed approach using the MIT-BIH arrhythmia benchmark demonstrates that it is more accurate than existing methods in terms of sensitivity (Se), positive prediction (+P), and DER (Detection Error Rate).
HealthEdge is a platform suggested by Wang et al. [82] to measure healthy human behavior using edge computing in smart homes. This work introduced a mechanism for deciding whether to transmit data using edge computing in the IoMT environment. Resource management has been a major concern in these systems due to energy constraints. As a result, a variety of techniques for solving issues have been developed. HealthEdge executes and processes jobs on local or remote devices using a range of processing algorithms and task scheduling to reduce processing time and response times as much as possible. The advantages of this technique might include avoiding further data translation, maintaining efficient network activity, and shortening data response time. This study, on the other hand, seeks to recognize tasks and decide whether or not to process them on remote devices. Consequently, one of the benefits of this method is that it minimizes energy consumption when moving data while increasing network throughput. This strategy has a number of drawbacks, including various factors. The real-time reaction has been a goal in IoMT systems because it has the potential to transform gaming. It is something that each method should pay close attention to. However, it is not addressed in this strategy for various reasons. It indicates that assessing the status of patients with certain disorders should be a top concern. In other words, the human priority of body measuring is different, and this approach should be adjusted to account for these challenges in the proper location and at the appropriate time. Task scheduling and determining the process of a work based on its importance is a wonderful technique to increase system efficiency and, indirectly, reduce energy consumption.
Another study, such as one by Chen et al. [15], showed ECC-based (“Edge Cognitive Computing”) healthcare systems in the smart healthcare environment, an edge cognitive computer system that analyzes, monitors, and optimizes computing resources. The ECC technique provided a healthcare system with resource recognition by assessing the user’s physical health cognition, allowing it to distribute resources to better resource management. By assessing the user’s health state and management, this strategy might solve network resource deployment challenges. In an emergency, the supplied approach provides a superior mechanism. In addition to these advantages, the proposed technique has certain disadvantages, such as the system’s inability to deal with atypical and unstructured data and the need for human interaction in order to reach an acceptable final judgment in a more challenging and changing environment.
Satija et al. [68] developed an IoT-based system called ECG-SQA for continuous heart health monitoring. It has three modules: ECG analysis and transmission, signal sensing, and quality assessment. The goal is to evaluate ECG signal quality in real-time under different conditions. The evaluation method has three steps: detecting flat-line signals, establishing baseline wander, and detecting high-frequency noise. ECG-SQA is superior to other methods based on morphological features and RR intervals (The time between two R-waves on an ECG is called the RR interval. It is influenced by the sinus node’s intrinsic properties and the autonomic nervous system. The reciprocal of the RR interval is the heart rate) and reduces battery consumption by transmitting only acceptable signals and putting the device to sleep for unacceptable signals.
P2P-based deep neural networks were proposed by Chung et al. [16] as a model for edge computing health to process health big data. Multiple edge nodes and the edge node modules are deployed at locations where health data are produced to construct the model then directly connect to the deep neural network model. A modularized deep neural network is constructed at the edge nodes to implement a parallel big data processing system. A single server is provided to gather the results of a neural network model. This server collects user evaluation results. With this approach, the response time delay is improved. So, edge computing systems also can function effectively within a poor network environment without having time delay or connection problems.
A. Lakhan presented a lightweight secure efficient offloading scheduling (LSEOS) metaheuristic approach for workflow healthcare applications in [36]. Layers for IoT (i.e., IoMT) workflow applications, administration, and resources are proposed in the prototype system. In terms of delay and security validation, the LSEOS has been shown to outperform all other available methods for offloading and scheduling process applications. The program was the workflow at the time of application design and is comprised of three processor jobs in the system, namely, local, fog, and cloud tasks. Local tasks on mobile devices must be executed with the least amount of delay and time while exchanging data with the system’s edge node tasks. This study also takes into account distinct workflow requirements such as mobile, delay-sensitive, and delay-tolerant (A type of network design that solves the problem of interrupted network connections.), as well as heterogeneous computing nodes in the system such as mobile devices, edge nodes, and cloud computing. The adaptive deadlines (determination of deadline for each round), sorting, and scheduling with neighborhood search strategies comprise the metaheuristic LSEOS. In general, the goal of LSEOS is to execute workflow applications on other nodes while minimizing system latency and security risk.
A. Lakhan in [35], proposes a dynamic application-partitioning workload task-scheduling-secure (DAPWTS) algorithm framework comprised of many schemes such as the min-cut algorithm, searching nodes, energy-enabled scheduling, failure scheduling, and security schemes. This solution creates the secure-min-cut algorithm, which tries to transfer data between nodes in a safe manner during system application partitioning. After partitioning the apps, the node-search algorithm searches for the best way to run them within their deadlines. The energy and failure schemes maintain the nodes’ energy consumption and the system’s failure. The Dynamic Application-Partitioning Workload Task-Scheduling Secure (DAPWTS) framework comprises many stages to handle the simultaneous application partitioning and task-scheduling issues, such as the secure min-cut, and task-sequencing phase, task-scheduling phase, and failure-aware scheduling phase. DAPWTS beats existing baseline techniques in terms of energy consumption, deadline, and application failure in the system, according to simulation data. The secure min-cut technique is used to minimize node energy consumption and divide the application across local and edge nodes.
Dong et al. [22] developed a healthcare mechanism based on edge computing that was divided into two sub-networks: intra-WBANs and beyond-WBANs (Wireless Body Area Network). In intra-WBAN, resource allocation was represented using a bargaining game, and Nash bargaining solution was utilized to compute the Pareto optimal point. The primary purpose of this study is to lower total expenses by merging medical urgency, the AoI (Age of Information – A performance metric that measures how up-to-date the information is from the point of view of the receiver), and energy dissipation. The system-wide cost of this approach is more efficient as a result of simulation and comparing it to other ways in terms of different clients. Furthermore, over time, the average number of time slots in the Source Destination Pair Matching Algorithm (SDMA) technique [21] is greater than the suggested approach due to the growing number of clients. Moreover, the offered method’s convergence rate is lower than SDMA’s. On the other hand, when the data size of packages grows larger, the system-wide cost of transit decreases, making SDMA inefficient. In summary, the suggested technique outperforms previous methods in terms of efficiency, and the system-wide cost is intended to be as low as possible.
A fuzzy logic-based clustering schema was designed by Sellam et al. [69] for edge computing in the Internet of Things. Energy consumption has been a major concern in remote healthcare systems due to the complexity of edge computing. This article demonstrated an effective scheme for reducing energy usage using a clustering approach known as FC-IoMT (Fuzzy Logic IoMT) to address these issues. Cluster head selection in FC-IoMT is based on the following parameters: node energy, distance, latency, capacity, and queue. Several measurements have been conducted in comparison to other ways, demonstrating that this approach is more energy-efficient than others, which is the advantage of the suggested schema.
However, there are certain disadvantages to this technique, such as the importance of the location of CHs to each other and the position of cluster heads to the sink (base station), which is not specified in the method. Furthermore, network coverage has been a source of contention in scientific literature since network size directly influences network lifetime and energy consumption.
A precise and efficient edge computing-based algorithm for remote healthcare systems in the Internet of things by Zhang et al. [86] was introduced. CT images are used as patient data for multi-stage feature extraction known as MF-GAM (Multi-stage Feature Extraction Generative Adversarial Network). Thus, MF-GAM can ensure the reconstruction of the image texture and edges. For performing 3d reconstruction, the denoised images generated from the MF-GAM are applied. Besides that, the RGT-MC algorithm has been introduced with regional growth that improves and accelerates renovation accuracy. In general, this method could be improving system accuracy and efficiency and patient treatment in places with few facilities by saving money costs.
Using medical images, Pareh et al. [53] established a novel safe and efficient platform based on “Left Data Mapping (LDM)”, “RC4 encryption”, “Pixel Repetition Method (PRM)”, and checksum computation. This work developed a strategy for mapping bit rates to an equal size of the shifted sequence in order to prevent a deteriorating scenario and increase security. A new checksum computing technique is offered for temper detection in any 2x2 block. A fragile watermark has also been used for early tamper detection. In a nutshell, one of the major benefits of this technology is that it brings dual security by concealing data transformations in medical images, which might be a secure way to give patient data in high-tech healthcare services. However, there are several disadvantages to this approach, including the fact that it requires a lot of calculation from the system, and in large-scale and complex networks where response time is a critical metric, sophisticated computation has a detrimental impact on the performance of the system.
Moosavi et al. [45] introduced an end-to-end security schema in an IoT-based medical environment to solve security challenges during data transfer. To offer a safe framework in IoT, this study used three schemas: secure end-user authentication and authorization using secure end-to-end communication on session resumption, DTLS (Datagram Transport Layer Security) handshake certificate, and robust mobility via smart gateways. [21] mentions one of this study’s significant contributions. This tree layer system was created utilizing the Datagram Transport Layer Security handshake between clients and gateways, as well as the session resumption approach. Due to the review and assessment of the suggested framework, it has been determined that this research is more efficient in terms of communication latency and overhead, and that when compared to systematic key-based Datagram Transport Layer Security in terms of memory requirements, it uses less memory. In general, this research might lead to more secure and energy-efficient data transfer. The system’s weakness is its inability to assess the approach at the low level (device layer) as a consequence of a large number of sensor devices incorporated into it.
Sigwele et al. [73] developed a strategy for linking disparate healthcare systems. In an IoT setting, a conceptual semantic framework can work together to create an integrated system that can address security concerns. An intelligent edge semantic gateway with a restful API (Application Programming Interface) might connect to and interact with this study. In this concept, the semantic smart gateway acted as a bottleneck between smart sensors and external systems. Each sensor communicates with the semantic smart gateway via a unique protocol. This IoT-based healthcare method is composed of three layers: a cloud layer, a fog layer, and a smart sensor layer, all of which are accessible through API. In general, this calibration framework aims to gather and represent data from many sources, generate knowledge, transmit information, and acquire data from other healthcare applications. As per the backdrop of the study, creating an integrated system via transferring information from multiple systems was examined; however, executing these solutions is inconceivable. Some negative points, including the complexity of management, network high traffic, non-standard IoT applications and infrastructures, and security challenges while transferring data among different applications, should be overcome.
Li et al. [39] used a friendly jamming (Fri-jam – Fri-jam is a simple approach that requires no more energy and has no processing capacity to classify security) strategy to secure patients’ acquired data via medical sensors from eavesdroppers to increase data security. To safeguard data, a three-layer design consisting of a data collecting (sensor layer), data management, and server is often recommended. The Fri-jam system is thought to have an impact on the data acquired by sensors in order to offer security. The proposed technique will considerably protect medical data from being eavesdropped on, according to a simulation that demonstrates Fri-jam-based systems can also be more secure. This method, on the other hand, would not be able to ensure data everywhere. When an eavesdropper attempts to enter the system from an appropriate place and acquire medical data, it has certain fundamental security restrictions. If the system tries to transfer the same data again, it may lose its confidentiality.
An intelligent, energy-efficient, and secure framework by Saba et al. [66] was provided. This framework relies on the Kruskal algorithm to reduce communication overhead and provide a low-cost routing mechanism to boost energy efficiency. Kruskal’s algorithm locates an edge-weighted undirected graph with the shortest spanning tree. The Kruskal algorithm also finds a minimum spanning tree if the graph is connected [17]. To protect data against malicious data, a cipher block chaining method is used to transport obtained data from the sink node to the medical centers (Hospitals). A private-public key-based digital authentication is given for data validation and integrity. This intelligent approach is energy efficient and functions with less energy, delay, and in a secure environment than prior efforts, thanks to simulation and statistical analysis. This design outperforms others in terms of packet loss rate, throughput, end-to-end latency, energy consumption, and connection breaches. More advanced computing, on the other hand, adds to the system computing process since a complicated schema is used to increase system throughput.
To improve medical data security, Moosavi et al. [44] established a system that utilizes smart gateways in the Internet of things healthcare. Smart gateways are important in this study because they handle client authentication and authorization between medical sensors and distant servers. The fundamental IP security method connecting both entries is the certificate-based DTLS (“Datagram Transport Layer Security”) handshake protocol. In comparison to previous ways, the proposed solution is more resistant to DoS (denial-of-service) assaults, has lower communication overhead, and has lower communication latency. This can aid in the deployment of scalable and dependable end-to-end security in smart healthcare applications. The study’s weak point is that it does not assess the strategy’s performance in wide IoT-based systems, and its evaluation is vague.
Li et al. [37] used SDN-based (Software Defined Network) edge computing to create a secure architecture for IoMT edge layer. Edge servers authenticated IoT devices using a lightweight authentication schema in this framework. SDN controller collaborates with edge servers for load balancing, resource management, and network optimization. Furthermore, the SDN controller plays a key role in delivering critical data in real-time, which aids in better network resource usage. When compared to previous approaches that have been tested with simulation data, the suggested method may have higher performance in terms of average (response time, latency), control overhead, packet delivery ratio, and throughput.
The proposed technique, on the other hand, has significant disadvantages: with these solutions, a large number of nodes (sensors) are available to collect data from the patient. As a result, securing a substantial number of these digital devices may be difficult, and authentication techniques should be scalable enough to accommodate a massive number of networked devices when introducing additional ones with no configuration or setup. Another disadvantage is that while building an authentication schema for an IoMT application, heterogeneous devices must be addressed. These concerns, however, have not been addressed and are unclear.
Zhang et al. [85] investigated a way for presenting an NB-IoT-based (Narrowband IoT) system in smart medical centers with a method for connecting intelligent things. The development of an infusion monitoring device to monitor the drop rate and amount of residual medications in intravenous infusion is the most important aspect of this approach. Because of the benefits of wearable devices, the Internet of Things (IoT) allows intelligent gadgets to be used in a variety of industries, including healthcare. Some activities, such as monitoring the drop rate and volume of remaining pharmaceuticals in medical centers (hospitals) for patient treatment, are recognized to be more difficult and need more time and precision. However, while creating a monitoring terminal, it employs encryption for data protection. The advantages listed above make it easier to link all smart objects in the healthcare aspect. For infusion monitoring, the suggested system employed an infrared signal modulation scheme to help count drops more precisely and determine the remaining drug volume by overcoming mild, undesirable noise. It has been codified a flaw detection technique and a learning algorithm. One of the suggested system’s disadvantages is that it does not allow a high data rate, which will make data transfer difficult during periods of traffic congestion.
Oueida et al. [52] presented an edge-computing architecture for managing medical resources in the smart health sector. In this study, an RPN (Resource Preservation Net) technique is utilized with cloud and edge computing in ED (Emergency Department) applications, and a Petri net is used to describe processes and protocols. RPN is a strategy for modeling and optimizing the LOS (length of stay), resource allocation rate, and waiting time for treatment and system benefit. RPN’s primary goal is to minimize wait times and LOS during visits, so saving time and avoid congestion. The system’s security is enhanced by a petri net-based security module.
Sardar et al. [67] proposed a secure face recognition system for IoT-enabled healthcare systems. In this system, each registered individual is identified by their face biometric using strong template protection schemes. To safeguard biometric information, a three-step template protection technique is proposed: Cancelable Biometrics, BioCrypto-Circuit, and BioCrypto-Protection. The system’s performance is evaluated in terms of the correct recognition rate and equal error rate. The method’s performance is compared to state-of-the-art methods for each database used, demonstrating the system’s efficiency.
Archana et al. [9] developed a remote health monitoring system that utilizes IoT and Edge computing. The system measures and processes various vital signs, including pulse rate, oxygen levels, and body temperature, using both cloud and edge technology. It is designed to continuously monitor a patient’s health and vital parameters. The primary objective of the system is to leverage edge computing technology to address the limitations of cloud architecture.
4.5.Evaluations of the presented applications
Table 2 categorizes research based on its applicability to smart healthcare systems. Energy consumption, security, healthcare expenditures, health monitoring, analysis, and diagnostics are all part of the major setting. Moreover, the methods’ pros and cons are briefly outlined for use in future examination in subsequent sections. In terms of response time, accuracy, cost, energy usage, security, and throughput, Table 3 lists the assessment elements for each technique. The majority of research presented energy efficiency and security solutions, as seen by this graph.
Table 2
Classification of recent research in the area of IoMT
| Ref. | Main context | Advantage | Limitations | New finding |
| Manogaran [42] | A method for analyzing human bodily activity | Efficient in energy consumption, residual error delay | Putting computation in the vicinity of sensors | Framework |
| Han [27] | A clustering model | More efficient, long time network | Local optimization, network fragmentation | Algorithm |
| Li [37] | A secure framework in edge computing | Lightweight authentication, the quick, average response time, average delay | Authentication problem in large scale network | Framework |
| Pustokhina [60] | A deep neural network model training scheme | Low latency metric performance | Complex computing | AI-Model |
| Saba [66] | Secure, energy-efficient framework | Improve system throughput, secure and energy-efficient | Complex computing | Framework |
| Muhammad [46] | A method for voice disorder assessment | Real-time transmission and accrue | Compress and security difficulties | Architecture |
| Ning [50] | Decentralized GT solutions for monitoring | Minimizing system wide-cost | losing of time-sensitivity | Framework |
| Zhang [85] | Connected intelligent gadgets in smart hospitals | Low-cost, data encryption and efficient power consumption | Not considering high data-rate | Prototype |
| Dong [22] | Edge computing-based smart healthcare | Improving system wide-cost and energy dissipation | Coverage | Framework |
| Moosavi [45] | A Secure end-to-end framework | End-to-end security, energy-efficient | Not considering scalability | Framework |
| Sigwele [73] | A platform for connecting various healthcare systems | Easy-to-use and secure | It’s tough to build without considering throughput | Platform |
| Chen [14] | A real-time QRS detection | Accurate, Real-time, Low power consumption, Low computational complexity | Not considering cost | Prototype |
| Satija [68] | Signal quality-aware electrocardiogram health monitoring system | Real-time an automated and efficient power consumption | Not considering scalability | Prototype |
| Chung [16] | P2P-based deep neural network | Improve response time, efficiency on the poor networks | Depending on the server | Algorithm |
| Oueida [52] | Resource management in smart healthcare | Reduce waiting time and LOS, secure | Not considering cost | Architecture |
| Chen [15] | Monitor, analyze, optimize the computing resources | Network resource deployment | Unstructured data has not been mentioned | Prototype |
| Wang [82] | Task scheduling in the smart home for human health monitoring | Decrease response time, improve system throughput, reduce energy consumption | Some procedures have long wait times, and it is difficult to map autonomous tasks to resources | Platform |
| Sellam [69] | A fuzzy logic-based clustering scheme | Energy efficient | Not considering scalability | Algorithm |
| Li [64] | Keeping patient information safe from eavesdroppers | Secure, efficient, low complexity | Information security and confidentiality are not guaranteed | Framework |
| Dai [18] | Block-Chain based secure solution | Improving security and privacy, smartly analyze | Low reliable | Framework |
| Pareh [53] | Secure and authenticated framework | Improving Security | Complex computing | Prototype |
| Moosavi [44] | A Secure and Efficient Authentication and Authorization Architecture | Improving Security | Not considering large-scale network | Framework |
Table 2
(Continued)
| Ref. | Main context | Advantage | Limitations | New finding |
| Rahman [63] | Edge computing framework for tackling Covid-19 | Security, Low-latency, Privacy | Not considering cost, different symptoms – large scale difficulties | Framework |
| Zhang [86] | Edge computing-based 3D reconstruction method | Reduce cost, improve efficiency, precision, accuracy, and reduce response time | Not mentioned implementation possibility | Algorithm |
| Zhang [87] | Remote monitoring system by 5G | Improving patient treatment and reducing the cost of healthcare | Not considering large scale network | Prototype |
| Md. Z. Uddin. [80] | Human activity prediction by recurrent neural network | Improving computational speed, performance, and accurate | Throughput and security difficulties | Framework |
| Gao [25] | Blockchain and SGX-based Edge-Computing | Providing authenticity, confidentiality, and integrity | Higher throughput depends on the higher hardware configuration | Framework |
| Kong [33] | Real-Time Mask Identification Framework | Reduce cost, improve accuracy and real-time response | Complex computing | Framework |
| Nguyen [48] | A Decentralized Architecture using blockchain | Reduced time latency, decreased energy consumption, and higher memory utilization | Not considering real-time response and are complex | Architecture |
| Ejaz [24] | Blockchain-based edge computing framework for reliable low-latency smart healthcare | Decentralized trust, real-time access, resource efficiency | Complex computing, increasing power consumption and network usage, operational cost | Framework |
| Sodhro [75] | A framework for Tele-sergery over 5G network | QOS optimization | Delay in client side and latency | Algorithm |
| Lakhan [36] | A lightweight secure metaheuristic method | Improve security, minimize latency | Processing time, Needs multiple edge server to overcome processing | Architecture |
| Lakhan [35] | Task-scheduling secure framework | Improve security, energy consumption and deadline | Operational space shortage | Algorithm |
| Shen et al. [71] | Computation Offloading | Improve privacy, energy efficiency and speed | Longer time to converge | AI-model |
| Jourdan et al. [31] | Efficiently recognize the user activity | Improve privacy, reducing cost | Depending on the server | Framework |
| Sharma et al. [70] | Privacy-preserving Distributed Application | Managing healthcare certificates | Increasing execution costs | Framework |
| Makina et al. [41] | Combines edge computing and blockchain | Real time response | Complex computing | Prototype |
| Archana et al. [9] | Utilizing IoT and Edge computing | Reducing the cost of healthcare | Not considering scalability | Framework |
| Sardar et al. [67] | Secure face recognition system | Improve security | Complex computing | Framework |
| Ali et al. [4] | Efficient patient monitorin | Improve energy, accuracy, transmission | Not considering large scale network | Platform |
Table 3
Comparison of the existing evaluation factors in studies
| Ref. | Accuracy | Security/privacy | Energy Consumption | Real-time | Cost | Throughput |
| Wang [82] | * | * | ||||
| Sigwele [73] | * | * | * | * | * | |
| Chung [16] | * | |||||
| Satija [68] | * | * | ||||
| Pareh [53] | * | * | ||||
| Ning [50] | * | * | ||||
| Li [37] | * | |||||
| Muhammad [46] | * | * | ||||
| Dong [22] | * | * | ||||
| Moosavi [45] | * | * | ||||
| Han [27] | * | * | ||||
| Manogaran [42] | * | * | ||||
| Zhang [85] | * | * | * | * | ||
| Pustokhina [60] | * | * | ||||
| Chen [14] | * | * | * | |||
| Oueida [52] | * | * | * | |||
| Li [37] | * | * | * | * | ||
| Chen [15] | * | * | * | |||
| Sellam [69] | * | * | * | |||
| Saba [66] | * | * | * | |||
| Dai [18] | * | |||||
| Moosavi [44] | * | |||||
| Kong [33] | * | * | * | |||
| Zhang [86] | * | * | * | * | ||
| Ejaz [24] | * | * | * | |||
| Md. Z. Uddin [80] | * | * | * | |||
| Gao [25] | * | * | * | |||
| Rahman [63] | * | * | * | |||
| Nguyen [48] | * | * | * | |||
| Zhang [87] | * | * | ||||
| Sodhro [75] | * | * | ||||
| Lakhan [36] | * | * | ||||
| Lakhan [35] | * | * | ||||
| Shen et al. [71] | * | * | ||||
| Jourdan et al. [31] | * | * | * | |||
| Sharma et al. [70] | * | * | * | |||
| Makina et al. [41] | * | * | * | |||
| Archana et al. [9] | * | * | ||||
| Sardar et al. [67] | * | |||||
| Ali et al. [4] | * | * | * |
4.6.Insights
Literature review shows that energy, security and privacy as the highest frequency factors for most solutions. Thus, one of the key aspects of IoMT solutions is energy efficiency that mentioned in most literary works. The Internet of Things is a direction for the development of various technologies and topics that tries to achieve a sustainable intelligent world in which the energy consumption of the intelligent objects of the IoT should be reduced. Many techniques such as fuzzy logic, task scheduling, block-chain, etc. enable efficient IoMT. Therefore, all the mentioned technologies can face different challenges. Sometimes, one of the ways to reduce these problems is to use them as a combined method.
Furthermore, security and privacy has been the next important aspect of IoMT applications. IoT applications generate enormous amounts of data, and there is always the risk of data leakage and security issues that mentioned applications covered these problems and proposed state of the art of security algorithms. According to the review and classification of articles [2,18,24,25,41,48,70], blockchain technology is used to increase and provide system security and privacy in data transfer. In short, blockchain can act as a distributed ledger that has digitally signed data and is auditable; any changes made therein can be traced back to the original data, which ensures security. This shows that blockchain technology is more reliable in securing data. By combining smart contracts and blockchain technology, it will be possible to design secure identification, authentication, and authorization methods in order to make an efficient electronic health record access control process [78]. Through a smart contract-based authentication mechanism, the method in [48] allows decentralized network edge user access verification without relying on centralized authorities, providing authentication reliability and decreasing network latency. Moreover, other applications use different types of security and privacy. For instance, Game Theory and Edge-GPU have been used for privacy in articles [37,63].
5.Discussion and comparison
This section examines an analysis of several IoMT-based application studies. As a corollary, the following context is used to answer the analytical questions raised in Section 3.
(1) What are the primary reasons for selecting an Edge-based application as a robust healthcare solution?
According to our study on literature research shows that by using a smart digital solution, services and treatment are improved, and innovative techniques are more accurate and require a relatively short time compared to alternatives. Moreover, the existence of several limitations to the traditional cloud computing paradigm, including potential backhaul network congestion and network delays, opened the door to migrating services to near the data production point. Thus, these weaknesses of the cloud were the main reason for selecting edge computing as the reliable solution. Edge computing allows data to be handled more effectively since processing is done in parallel across several edge nodes. Also, because data is calculated at the edge, there is no need to suffer delay from a round trip across the local network, to the cloud, and back. Edge computing is well suited for low-latency applications. It also lets users contact medical personnel and physicians electronically without physically visiting, lowering the expense of each visit; another benefit is the availability of mobile applications that allow patients to save time by swiftly checking their health status.
(2) What kind of maintenance and upgrade process will be used in Edge-based Healthcare?
The maintenance process involves restarting the operating system of the IoT device, updating the firmware or software of an application, and resetting configurations. Many edge devices and apps are distributed around the healthcare environment – or are managed by other parties – continual maintenance and updates may be difficult. Ultimately, the ideal would be to enable software-driven upgrades to be sent automatically across all of these devices, but the reality these days is that a corporation may be connected to thousands of devices from various manufacturers and built on various protocols. As a result, the requirement for proper approaches to solving this difficulty might be advantageous. The strategy by Dong et al. [22] attempts to alleviate these issues.
(3) What methods may be used to alleviate issues in Edge-based healthcare?
Healthcare is one of the most delicate and risky ecosystems in the Internet of Things, demanding the use of high-standard solutions to handle medical faults. Despite this, a review of the available literature and a survey of publications show that strategies with speed, high accuracy, low cost, and security can significantly help technology-based type of application. The noveler methods to alleviate issues in Edge-based healthcare are to adopt edge intelligent technology along with AI. These methods include (Manogaran et al. [42] (bayesian deep network system), Pustokhina et al. [60] (Deep Neural Network model), Md. Z. Uddin [80] Recurrent Neural Network (RNN), etc). Blockchain methods [2,18,24,25,41,48,70].
(4) What are the major IoMT Edge-based domains?
IoT-based healthcare solutions are getting started in the realm of smart healthcare. It is used to leverage technology and smart digital devices to enhance healthcare quality while cutting treatment costs and times and increasing efficiency. The following domains at the Edge layer have sparked the interest of researchers and corporations, according to literary studies. To demonstrate domains, Fig. 7 provides a proportion chart of the literature articles. Patient monitoring ([9,31,50,68,82,87]), resource utilization ([15,52]), collaborative healthcare systems ([73,85]), smart technology-based hospitals ([69]), disease detection/diagnosis ([14]) and general aspects are among these topics. Among these domains, some solutions took more attention. For instance, remote monitoring and care service for senior citizens at their homes, remote medical diagnosis and monitoring, recognition and analysis of the human body/behavior, fall detection, AI-based monitor patient health status, and automatic disease diagnosis.
Fig. 7.
Percentage of studies in IoMT applications.
(5) Which main contexts are considered for Edge computing applications?
Figure 8 shows the primary context-based chart, which shows that owing to the diversity of publications by the main context, energy efficiency has the highest frequency, with 22 studies and security/privacy with 20 studies. Furthermore, several studies were presented in more than one context due to fields provided in the study schema.
(6) In IoT-based healthcare, what security/privacy has been used?
Fig. 8.
The number of studies by the main context.
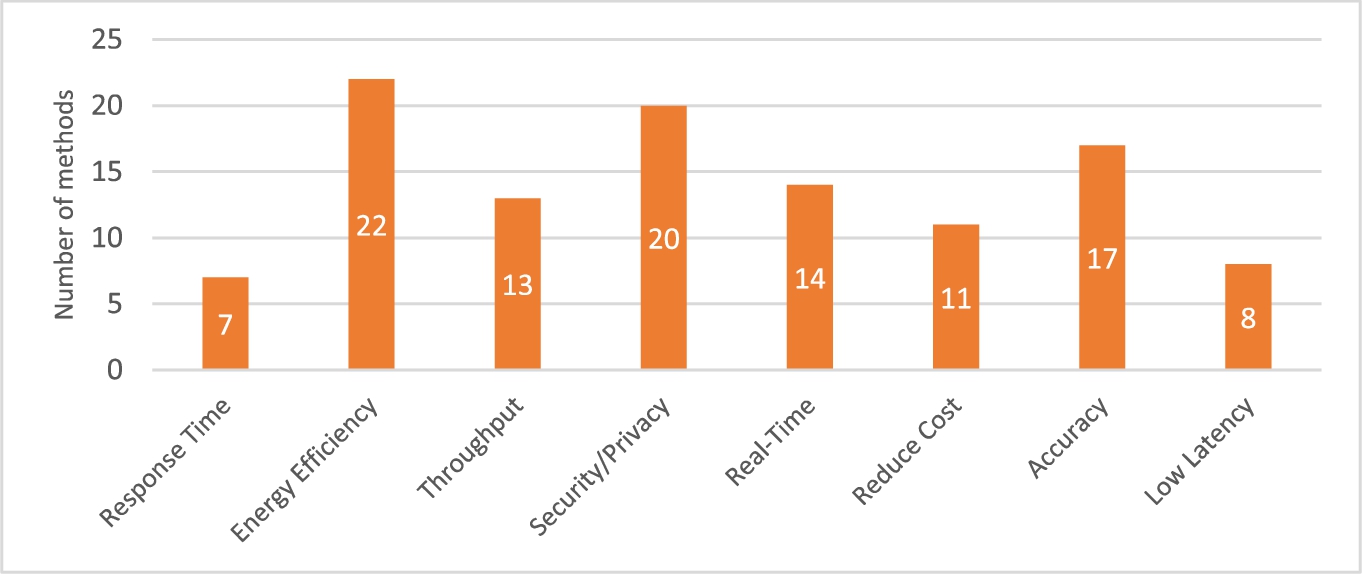
Fig. 9.
Studies in IoMT applications by the technology.
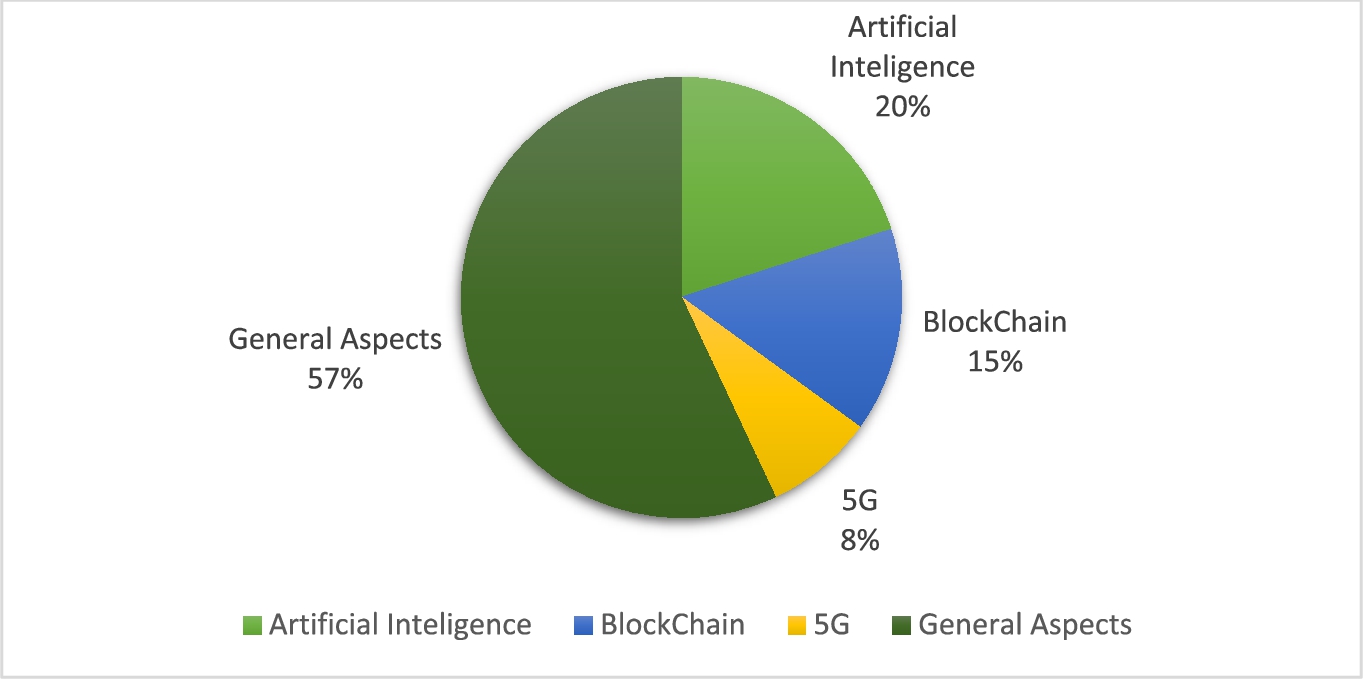
On the wider picture, healthcare information is more profitable, patients’ data may face numerous significant difficulties to cyber-attacks due to insufficient security. In a nutshell, the key difficulty for cheap computational-based devices is security. Lightweight cryptography approaches, Fri-Jam schema, Blockchain, authentication by role, and authentication by edge servers employing lightweight authentication schema have all been established in recent years. In addition, users have the power to edit, erase, or transfer their data and refuse any data collection or processing that they do not consent to. These kinds of strong security actions stop unwanted entry, change, or exposure of user data. As a result, security is a serious concern that affects IoMT over patient data. Additionally, by default, the data from IoT devices in smart healthcare systems are made available to doctors, caregivers, and authorized parties.
(7) What technologies have had an impact on the evolution of this field?
According to technical studies, smart healthcare, which uses mobile and smart technologies to improve treatment, is becoming more widespread than in the past. Figure 9 provides a pie chart of the distribution of literature articles by technology. Artificial intelligence (pattern recognition such as voice and video recognition, monitor human health status and etc), additive manufacturing, computers, 5G, big data, multimedia, and communication are examples of exponential technologies (exponential technology describes technologies that improve rapidly, with their power or speed doubling yearly and their cost halving.). Digital mobile devices are another technology that has been related to making healthcare more efficient, accrued, and less costly. Moreover, among these technologies, AI (Artificial Intelligence) might be a viable approach to some issues in edge computing caused by the vast amount of data generated when networking. It can be pointed out that newer solutions tend to use artificial intelligence more in solving problems (for example, see Section 2 of Section 4). Moreover, due to the importance and attractiveness of smarter methods, Hua et al. [30] highlight the related challenges of Artificial Intelligence and Edge Computing. It has been discussed especially from the perspective of machine learning. Furthermore, Blockchain (manage healthcare certificates, privacy awareness, integrity of systems and etc) has been more suitable to address some difficulties of edge computing (Eg. [25]). So, it has the potential to alter the future of wearable digital sensors /devices (pulse rate, oxygen levels, and body temperature) utilized in IoMT applications [20,55].
(8) What schemes have been taken to make remote monitoring healthcare sustainable?
In terms of power outages at home, the function of the IoMT schema depends on the type of application and the availability of backup power sources. Based on the solutions, if a wearable device is used to monitor a patient’s oxygen level, heart rate, blood pressure, or body temperature, the client may require a battery-powered device that may store data locally and transfer it later when power is restored [55]. In addition, these types of devices will alert you if they detect any unusual changes that may indicate disease or infection. When clients use telemedicine to consult with their doctor online, they may require an additional communication channel, such as a cellphone or a mobile app that works offline [31]. Clients who use a smart hospital system to regulate their medical equipment, medicine, or security may require a dependable backup generator to prevent any disruption or damage to their health or safety [73]. Moreover, when equipment fail or needs calibration/validation and client training, it is the responsibility of the healthcare provider to handle concerns and ensure that the devices they employ are correctly configured/maintained at the client’s house. However, depending on the circumstances, the device’s manufacturer may be held liable for problems. Depending on the kind and function of the solution, notification, reaction, and alarm methods may be used in applications. For instance, in case of an emergency or a change in the patient’s health, certain techniques may need to alert the patient, the doctor, or the caregiver. Some applications require instantaneous or recurring responses to the data they receive or gather. In order to prevent excessive or erroneous warnings that can lead to unnecessary stress or confusion, certain solutions have been created with alarm thresholds or anomaly detection algorithms.
5.1.Open issues
In this part, obstacles and issues have been discussed in order to propose future study paths and to solve the following question indicated (question 9) in Section 3.
(9) What are the significant gaps and open questions for future research directions?
Security Medical data, in terms of IoMT, might be a lucrative resource for directing attackers to data theft. Because many aspects and levels of IoMT have insufficient security, applications may encounter issues like unauthorized access, wireless signal blocking, and DoS (denial-of-service) attacks. As a result, it isn’t easy to adopt unless security concerns are addressed. Of course, some methods to improve security and privacy have been proposed and presented, which were discussed in detail in Section 4. Some presented methods, such as utilizing encryption to protect data before transmitting it to the cloud or edge nodes. Blockchain is being used to authenticate IoMT devices and cloud service providers, as well as to offer an access policy management method for IoMT data. As is generally known, medical-based information has greater security and privacy vulnerabilities than other systems [5,12,54]. If this system is to be used in a big area, particular attention to information and equipment security is required. Furthermore, due to concerns for security and privacy, it is possible for data to be owned by National Health Service and controlled/supported by a company. However, IoT data ownership is a complex issue. As a rule of thumb, whoever holds title to the data-producing platform, likely owns the data. Moreover, most concerns and issues are addressable by the owner of the system and they are responsible to clients. The security concerns and obstacles are outlined by Luqman et al. [40] and Ghubaish et al. [26].
Cost IoT-based smart healthcare application establishes a communication between clinicians and patients, allowing them to communicate remotely reducing the expense of physical visits. To solve cost-related difficulties, however, various elements must be addressed. In general, it strives to lower total healthcare expenses, although implementation costs, which include smart hardware devices, software programs, data storage, and maintenance, play a big part in IoMT healthcare systems. According to research reports, it is estimated that by 2030, 125 billion devices will be connected to the Internet [6]. The growth of data is expected to put unprecedented pressure on the current internet infrastructure and the centralized (Cloud) data centers (DCs). This can also be stated in the form of a cost issue. Besides the importance of redesigning/improving data communication and processing across the Internet, one key ramification of these developments is an increase in the cost of both Cloud and Edge DCs. The successful exploitation of these approaches will lead to significant cost savings [49].
Energy consumption In the IoMT-based system, several sensors/devices including wearable, environmental mounted, thermometer, blood pressure sensors, etc are placed to collect data relating to medical treatment. As a corollary, the essential challenge in IoMT is to minimize the energy consumption of devices and sensors. Because energy plays such a large role in these systems, the energy usage of smart devices and communications should be decreased. It is obvious that using battery-powered equipment that can automatically transition to battery mode when the power goes off. Furthermore, providers should protect and manage their IoMT devices by analyzing their risk, implementing regulations, and monitoring their activity to avoid excessive energy usage. Many issues such as anomaly detection, overuse of the system, etc. should be considered. Therefore, presenting proper models including anomaly detection systems, and securitization for different parts of IoT systems will assist in addressing these types of challenges in energy consumption. The study [43] specially discussed the use of edge computing in IoT and analyzed its effect on the energy consumption of IoT devices.
Interoperability Several industries and manufacturers make medical equipment with different standards, such as blood pressure tester devices. Thus, without a defined set of rules to create a protocol and guidelines, IoMT-based applications will confront disparate standards. The standardization of IoMT devices is critical for achieving time savings and efficient solutions. To address interoperability concerns, Rubi et al. [65] developed an Internet of Medical Things (IoMT) platform for pervasive healthcare that ensures interoperability, detection process quality, and scalability in an M2M-based architecture and provides functionalities for data processing, knowledge extraction, and common healthcare services.
Flexible Home hospitalization systems are linked to hospitals and clinics using IoMT-based systems. However, many hospitals lack network infrastructure to incorporate IoMT-based systems, necessitating special attention in order to overcome implementation challenges. A discussion, solution and challenges regarding interconnected hospitals that use edge computing to prioritize the convenience of patients is presented in [19].
Real-time response The use of IoMT-based technologies to enhance healthcare treatment is growing, yet real-time interventions in crucial cases remain difficult. Furthermore, real-time data is closely related to analysis and decision-making in some treatments. Consequently, lowering response time is one of the most critical matters in IoMT, particularly in crucial situations. This sort of system is more commonly used. The study [81] utilized and discussed real-time statistics from IoMT devices to detect problems and provide remedies in a short period of time.
5.2.Comparison of solutions
Studies show that [4,17,48,69,71,73,86] methods are more efficient in terms of energy consumption, [24,31,52,63,66] methods are better in terms of security and privacy, and methods [4,42,68,82] in terms of real-time are better than other methods respectively. It is obvious that the selected methods are less than the stated methods. The reason is that methods have been selected with the least impact on other indicators related to health care. On one side, there is no agreement on standard evaluation measures for assessing the effectiveness of techniques. Many studies have developed their own cost metrics. Real-world infrastructure has characteristics such as large size, geographic distribution, and diverse edge computing nodes, making it difficult to find solutions in such situations. Despite the common use of simulations to evaluate applications, current simulation frameworks have significant limitations in their ability to represent mobility, scalability, complexity, and the specific needs of edge computing scenarios.
6.Conclusion
This article demonstrates a review of Edge Computing papers that thoroughly analyzes the literary works. A method based on SLR was presented to understand current studies by exploring high-quality papers published from 2015 to 2023 in the field of Edge Computing. The results of many investigations have been analyzed and progress reports have been presented. A careful evaluation of the existing research demonstrates that increasingly IoMT-based healthcare has drawn greater attention. Research papers indicate the following domains are of particular interest to researchers. These domains include collaboration healthcare systems, resource utilization, patient monitoring, smart hospitals (Monitoring the drop rate, BEdgeHealth solution), disease detection/diagnoses, and general fields. According to literature studies edge computing shortens the distance between data communication nodes. It brings computation closer to end-users in order to reduce the distance that data must travel. It also minimizes the quantity of traffic passing through the healthcare network, allowing systems to preserve bandwidth or use it for other reasons. The fewer data that be sent to the cloud, the lower the expenses, energy consumption, latency, and ability to give a real-time approach. The statistical analysis of different IoMT-based applications shows some achievements have been achieved include:
Quick monitoring/diagnoses patient health state
Utilization of various sensors such as wearable, environmental sensors
Link exponential technologies in IoMT to make healthcare more efficient
Utilization of IoMT in the various domain of healthcare
And some challenges remained
Reliable security/privacy approach as an important challenge of IoMT
Requirement of high-standard solutions to boost medical deficiencies
To overcome the challenges listed above in Edge Computing, new and optimum approaches such as artificial intelligence and machine learning can be of tremendous assistance.
The reality is that intelligent healthcare is a relatively young IoT-based system that faces several hurdles and unresolved concerns that must be tackled, particularly in challenging conditions like COVID-19. In addition to the security and privacy challenges raised, one of these issues is energy consumption, and improving energy efficiency has the most frequency among solutions. The authors have identified some open issues and future directions in their research and also provided the suitable response to guide future research in this area.
Funding
Not applicable.
Conflicts of interest/competing interests
The authors are not affiliated with any organization having a direct or indirect financial interest in the subject dealt with in the manuscript.
Availability of data and materials
Not applicable.
Authors’ contributions
Mahdi Safaei Yaraziz wrote the first draft of the manuscript, and all authors commented on earlier versions of the manuscript. The final manuscript was read and approved by all authors.
Ethics approval
All authors hereby ensure that the following contents of the manuscript are accurate:
This material is the original work of the authors, never published elsewhere.
This article is not currently being considered for publication elsewhere.
This article truly and fully reflects the author’s own research and analysis.
This article duly acknowledges the significant contributions of co-authors and lead researchers.
All sources used are properly disclosed (accurate citations).
All authors have personally and actively participated in important work on the preparation of articles and are responsible to society for the content of their articles.
Consent to participate
Informed consent was obtained from all individual participants included in the study.
Consent for publication
Participants’ informed consent to publish their data and photos.
References
[1] | https://www.gartner.com/smarterwithgartner/what-edge-computing-means-for-infrastructure-and-operations-leaders (accessed 20 May 2023). |
[2] | https://www.intel.com/content/www/us/en/developer/articles/technical/properly-detecting-intel-software-guard-extensions-in-your-applications.html, (accessed 16 Sep 2022). |
[3] | A.O. Akmandor and N.K. Jha, Smart health care: An edge-side computing perspective, IEEE Consumer Electronics Magazine 7: ((2018) ), 29–37. doi:10.1109/MCE.2017.2746096. |
[4] | K. Ali, A.D. Abd and H. Hassan, Energy-efficient multisensor adaptive sampling and aggregation for patient monitoring in edge computing based IoHT networks, Journal of Ambient Intelligence and Smart Environments ((2023) ). doi:10.3233/AIS-220610. |
[5] | T. Alsboui, H. Al-Aqrabi, R. Hill and S. Iram, An approach to privacy-preserving distributed intelligence for the Internet of Things, in: Proceedings of the 7th International Conference on Internet of Things, Big Data and Security – IoTBDS, SciTePress, (2022) , pp. 174–182. doi:10.5220/0011056400003194. |
[6] | T. Alsboui, Y. Qin, R. Hill and H. Al-Aqrabi, Enabling distributed intelligence for the Internet of Things with IOTA and mobile agents, Computing ((2020) ). doi:10.1007/s00607-020-00806-9. |
[7] | A.H.M. Aman, W.H. Hassan, S. Sameen, Z.S. Attarbashi, M. Alizadeh and L.A. Latiff, IoMT amid COVID-19 pandemic: Application, architecture, technology, and security, Network and Computer Applications ((2020) ). doi:10.1016/j.jnca.2020.102886. |
[8] | S.U. Amin and M.S. Hossain, Edge intelligence and Internet of things in healthcare: A survey, IEEE Access, IEEE 9: ((2020) ), 45–59. doi:10.1109/ACCESS.2020.3045115. |
[9] | R. Archana, C. Vaishnavi, D.S. Priyanka, S. Gunaki, S.R. Swamy and P.B. Honnavalli, Remote health monitoring using IoT and edge computing, in: IEEE, 2022 International Conference on IoT and Blockchain Technology (ICIBT), (2022) , pp. 1–6. doi:10.1109/ICIBT52874.2022.9807710. |
[10] | A. Behmanesh, N. Sayfouri and F. Sadoughi, Technological features of Internet of Things in medicine: A systematic mapping study, Wireless Communications and Mobile Computing 2020: ((2020) ). doi:10.1155/2020/9238614. |
[11] | S. Bonfanti, A. Gargantini and A. Mashkoor, A systematic literature review of the use of formal methods in medical software systems, Software: Evolution and Process Journal ((2018) ). doi:10.1002/smr.1943. |
[12] | S.A. Butt, T. Jamal, M.A. Azad, A. Ali and N.S. Safa, A Multivariant Secure Framework for Smart Mobile Health Application, Transactions on Emerging Telecommunications Technologies, Wiley, (2019) . doi:10.1002/ett.3684. |
[13] | G. Carlesa, C. Stefanob, F. Anthonyc, R. Georged and P. Davye, Internet of Things for enabling smart environments: A technology-centric perspective, Journal of Ambient Intelligence and Smart Environments ((2019) ), 23–43. doi:10.3233/AIS-180509. |
[14] | C.L. Chen and C.T. Chuang, A QRS detection and R point recognition method for wearable single-lead ECG devices, Sensors ((2017) ). doi:10.3390/s17091969. |
[15] | M. Chen, W. Li, Y. Hao, Y. Qian and I. Humar, Edge cognitive computing based smart healthcare system, Future Generation Computer Systems 86: ((2018) ), 403–411. doi:10.1016/j.future.2018.03.054. |
[16] | K. Chung and H. Yoo, Edge Computing Health Model Using P2P-Based Deep Neural Networks, Peer-to-Peer Networking and Applications, Springer, (2019) . doi:10.1007/s12083-019-00738-y. |
[17] | T.H. Cormen, C.E. Leiserson, R.L. Rivest and C. Stein, Introduction to Algorithms, 3rd edn, MIT Press, (2009) . |
[18] | H.N. Dai, M. Imran and N.N. Haider, Blockchain-Enabled Internet of Medical Things to Combat COVID-19, IEEE, Interent of Things Magazine, (2020) . doi:10.1109/IOTM.0001.2000087. |
[19] | S. Debdas, C.K. Panigrahi, P. Kundu, S. Kundu and R. Jha, IoT application in interconnected hospitals, in: Machine Learning for Healthcare Applications, (2021) , pp. 225–247. doi:10.1002/9781119792611.ch15. |
[20] | S. Deng, H. Zhao, W. Fang, J. Yin, S. Dustdar and A. Zomaya, Edge intelligence: The confluence of edge computing and artificial intelligence, IEEE Internet of Things 7: ((2020) ), 7457–7469. doi:10.1109/JIOT.2020.2984887. |
[21] | B. Di, L. Song and Y. Li, Sub-channel assignment, power allocation, and user scheduling for non-orthogonal multiple access networks, IEEE Transactions on Wireless Communications 15: ((2016) ), 7686–7698. doi:10.1109/TWC.2016.2606100. |
[22] | P. Dong, Z. Ning, M.S. Obaidat, X. Jiang, Y. Gue, X. Hu, B. Hu and B. Sadoun, Edge Computing Based Healthcare Systems: Enabling Decentralized Health Monitoring in Internet of Medical Things, IEEE Network, (2020) . doi:10.1109/MNET.011.1900636. |
[23] | T. Dutta, S. Pramanik and P. Kumar, Chapter 2 – IoT for Healthcare Industries: A Tale of Revolution, Healthcare Paradigms in the Internet of Things Ecosystem, Elsevier, (2021) . doi:10.1016/B978-0-12-819664-9.00002-8. |
[24] | M. Ejaz, T. Kumar, I. Kovacevic, M. Ylianttila and E. Harjula, Health-BlockEdge: Blockchain-edge framework for reliable low-latency digital healthcare applications, Sensors ((2021) ). doi:10.3390/s21072502. |
[25] | Y. Gao, H. Lin, Y. Chen and Y. Liu, Blockchain and SGX-enabled edge-computing-empowered secure IoMT data analysis, IEEE Internet of Things Journal 8: ((2021) ), 15785–15795. doi:10.1109/JIOT.2021.3052604. |
[26] | A. Ghubaish, T. Salman, M. Zolanvari, D. Unal, A.K. Al-ali and R. Jain, Recent advances in the Internet of Medical Things (IoMT) systems security, IEEE Internet of Things ((2020) ). doi:10.1109/JIOT.2020.3045653. |
[27] | T. Han, L. Zhang, S. Pirbhulal, W. Wu, V. Hugo and D. Albuquerque, A novel cluster head selection technique for edge-computing based IoMT systems, Computer Networks 158: ((2019) ), 241–261. doi:10.1016/j.comnet.2019.04.021. |
[28] | M. Hartmann, U.S. Hashmi and A. Imran, Edge computing in smart health care systems: Review, challenges, and research directions, Wiley, ((2019) ), pp. 1–25. doi:10.1002/ett.3710. |
[29] | L. Hsin-Chang, C. Ming-Jen and H. Jung-Tang, An IoT-based smart healthcare system using location-based mesh network and big data analytics, Journal of Ambient Intelligence and Smart Environments 14: (6) ((2022) ), 483–509. doi:10.3233/AIS-220162. |
[30] | H. Hua, Y. Li, T. Wang, N. Dong, W. Li and J. Cao, Edge Computing with Artificial Intelligence: A Machine Learning Perspective, ACM Computing Surveys, (2023) . doi:10.1145/3555802. |
[31] | T. Jourdan, A. Boutet, A. Bahi and C. Frindel, Privacy-preserving IoT framework for activity recognition in personal healthcare monitoring, ACM Transactions on Computing for Healthcare 2: (1) ((2021) ), 3. doi:10.1145/3416947. |
[32] | Q.V. Khanh, V.H. Nguyen, Q.N. Minh, A.D. Van, N.L. Anh and A. Chehri, An Efficient Edge Computing Management Mechanism for Sustainable Smart Cities, Sustainable Computing: Informatics and Systems, Elsevier, (2023) . doi:10.1016/j.suscom.2023.100867. |
[33] | X. Kong, K. Wang, S. Wang, X. Wang, X. Jiang, Y. Guo, G. Shen, X. Chen and Q. Ni, Real-time mask identification for COVID-19: An edge-computing-based deep learning framework, IEEE INTERNET OF THINGS, IEEE 8: ((2021) ), 15929–15938. doi:10.1109/JIOT.2021.3051844. |
[34] | M. Kumhar and J.B. Bhatia, Edge computing in SDN-enabled IoTBased healthcare frameworks: Challenges and future research directions, International Journal of Reliable and Quality E-Healthcare ((2022) ), 1–15. doi:10.4018/IJRQEH.308804. |
[35] | A. Lakhan, J. Li, T.M. Groenli, A.H. Sodhro, N.A. Zardari, A.S. Imran, O. Thinnukool and P. Khuwuthyakorn, Dynamic application partitioning and task-scheduling secure schemes for biosensor HealthcareWorkload in mobile edge cloud, Electronics Journal ((2021) ). doi:10.3390/electronics10222797. |
[36] | A. Lakhan, A.H. Sodhro, A. Majumdar, P. Khuwuthyakorn and O. Thinnukool, A lightweight secure adaptive approach for Internet-of-medical-things healthcare applications in edge-cloud-based networks, Sensors ((2022) ). doi:10.3390/s22062379. |
[37] | J. Li, J. Cai, F. Khan, A.U. Rehman, V. Balasubramaniam, J. Sun and P. Venu, A secured framework for SDN-based edge computing in IoT-enabled healthcare system, IEEE Access 8: ((2020) ), 135479–135490. doi:10.1109/ACCESS.2020.3011503. |
[38] | K. Li, Y. Cui, W. Li, T. Lv, X. Yuan, S. Li, W. Ni, M. Simsek and F. Dressler, When Internet of Things meets metaverse: Convergence of physical and cyber worlds, IEEE Internet of Things Journal 10: (5) ((2023) ), 4148–4173. doi:10.1109/JIOT.2022.3232845. |
[39] | X. Li, H.N. Dai, Q. Wang, M. Imran, D. Li and M.A. Imran, Securing Internet of Medical Things with friendly-jamming schemes, Computer Communications 160: ((2020) ), 431–442. doi:10.1016/j.comcom.2020.06.026. |
[40] | M. Luqman and A.R. Faridi, An Overview on Security Issues in Internet of Things, IEEE, 4th International Conference on Computing Communication and Automation (ICCCA), (2018) . doi:10.1016/j.procs.2018.10.439. |
[41] | H. Makina, A.B. Letaifa and A. Rachedi, Leveraging edge computing, blockchain and IPFS for addressing eHealth records challenges, in: IEEE, 15th International Conference on Security of Information and Networks (SIN), (2022) , pp. 1–4. doi:10.1109/SIN56466.2022.9970495. |
[42] | G. Manogaran, P.M. Shakeel, H. Fouad, Y. Nam, S. Baskar, N. Chilamkurti and R. Sundarasekar, Wearable IoT smart-log patch: An edge computing-based Bayesian deep learning network system for multi access physical monitoring system, Sensors ((2019) ), 1–18. doi:10.3390/s19133030. |
[43] | J. Mocnej, M. Miškuf, P. Papcun and I. Zolotova, Impact of Edge Computing Paradigm on Energy Consumption in IoT, IFAC-PapersOnLine, Elsevier, (2018) . doi:10.1016/j.ifacol.2018.07.147. |
[44] | S.R. Moosavi, T.N. Gia, A.M. Rahmani, E. Nigussie, S. Virtanen, J. Isoaho and H. Tenhunen, SEA: A secure and efficient authentication and authorization architecture for IoT-based healthcare using smart gateways, Elsevier 52: ((2015) ), 452–459. doi:10.1016/j.procs.2015.05.013. |
[45] | S.R. Moosavi, T.N. Gia, A.M. Rahmani, E. Nigussie, S. Virtanen, J. Isoaho and H. Tenhunen, End-to-end security scheme for mobility enabled healthcare Internet of Things, Elsevier 64: ((2016) ), 108–124. doi:10.1016/j.future.2016.02.020. |
[46] | G. Muhammad, M.F. Alhamid, M. Alsulaiman and B. Gupta, Edge computing with cloud for voice disorder assessment and treatment, IEEE Communications Magazine ((2018) ). doi:10.1109/MCOM.2018.1700790. |
[47] | M. Nasajpour, S. Pouriyeh, R.M. Parizi, M. Dorodchi, M. Valero and H.R. Arabnia, Internet of Things for current COVID-19 and future pandemics: An exploratory study, Healthcare Informatics 4: ((2020) ), 325–364. doi:10.1007/s41666-020-00080-6. |
[48] | D.C. Nguyen, P.N. Pathirana, M. Ding and A. Seneviratne, BEdgeHealth: A decentralized architecture for edge-based IoMT networks using blockchain, IEEE Internet of Things, IEEE 8: ((2021) ), 11743–11757. doi:10.1109/JIOT.2021.3058953. |
[49] | P. Nikolaou, Y. Sazeides, A. Lampropulos, D. Guilhot, A. Bartoli, G. Papadimitriou, A. Chatzidimitriou, D. Gizopoulos, K. Tovletoglou, L. Mukhanov, G. Karakonstantis, M. Kleanthous and A. Prat, Total Cost of Ownership Perspective of Cloud vs Edge Deployments of IoT Applications, Computing at the EDGE, Springer, (2022) . doi:10.1007/978-3-030-74536-3_6. |
[50] | Z. Ning, P. Dong, X. Wang, X. Hu, L. Guo, B. Hu, Y. Guo, T. Qiu and R.Y.K. Kwok, Mobile edge computing enabled 5G health monitoring for Internet of Medical Things: A decentralized game theoretic approach, IEEE Journal on Selected Areas in Communications ((2020) ). doi:10.1109/JSAC.2020.3020645. |
[51] | S. Ouchani and M. Krichen, Ensuring the Correctness and Well Modeling of Intelligent Healthcare Management Systems, International Conference on Smart Homes and Health Telematics, Springer, (2020) . doi:10.1007/978-3-030-51517-1_33. |
[52] | S. Oueida, Y. Kotb, M. Aloqaily, Y. Jararweh and T. Baker, An edge computing based smart healthcare framework for resource management, Sensors ((2018) ). doi:10.3390/s18124307. |
[53] | S.A. Pareh, J.A. Kaw, P. Bellavista, N.A. Loan, G.M. Bhat, K. Muhammad and A. Victor, Efficient Security and Authentication for Edge- Based, Internet of Medical Things, IEEE, (2020) . doi:10.1109/JIOT.2020.3038009. |
[54] | H.K. Patil and R. Seshadri, in: Big Data Security and Privacy Issues in Healthcare, IEEE, 2014 IEEE International Congress on Big Data, (2014) , pp. 2379–7703. doi:10.1109/BigData.Congress.2014.112. |
[55] | A. Pazienza, G. Mallardi, C. Fasciano and F. Vitulano, Articial Intelligence on Edge Computing: A Healthcare Scenario in Ambient Assisted Living, (2020) . |
[56] | K. Petersen, R. Feldt, S.H. Mujtaba and M. Mattsson, Systematic mapping studies in software engineering ((2008) ). |
[57] | S. Pirbhulal, W. Wu, S.C. Mukhopadhyay and G. Li, Adaptive Energy Optimization Algorithm for Internet of Medical Things, IEEE, (2018) . doi:10.1109/ICSensT.2018.8603601. |
[58] | B. Pradhan, S. Bhattacharyya and K. Pal, IoT-Based Applications in Healthcare Devices, Medical Internet of Things (IoT) Devices, Hindawi, (2021) . doi:10.1155/2021/6632599. |
[59] | A. Pravin Renold and K.V. Ranjith Kumar, Design of Internet of Things enabled personalized healthcare device for vital signs monitoring, Journal of Ambient Intelligence and Smart Environments ((2022) ). doi:10.3233/AIS-220098. |
[60] | I.V. Pustokhina, D.A. Pustokhin, D. Gupta, A. Khanna, K. Shankar and G.H. Nguyen, An effective training scheme for deep neural network in edge computing enabled Internet of Medical Things (IoMT) systems, IEEE Access 8: ((2020) ), 107112–107123. doi:10.1109/ACCESS.2020.3000322. |
[61] | V.K. Quy, A. Chehri, N.M. Quy, N.D. Han and N.T. Ban, Innovative trends in the 6G era: A comprehensive survey of architecture, applications, technologies, and challenges, IEEE Access 11: ((2023) ), 39824–39844. doi:10.1109/ACCESS.2023.3269297. |
[62] | V.K. Quy, N.V. Hau, D.V. Anh and L.A. Ngoc, Smart Healthcare IoT Applications Based on Fog Computing: Architecture, Applications and Challenges, Complex & Intelligent Systems, Springer, (2021) . doi:10.1007/s40747-021-00582-9. |
[63] | Md.A. Rahman and M.S. Hossain, An Internet of Medical Things-enabled edge computing framework for tackling COVID-19, IEEE Internet of Things ((2021) ). doi:10.1109/JIOT.2021.3051080. |
[64] | P.P. Ray, D. Dash and D. De, Edge computing for Internet of Things: A survey, e-healthcare case study and future direction, Network and Computer Applications 140: ((2019) ), 1–22. doi:10.1016/j.jnca.2019.05.005. |
[65] | J.N.S. Rubí and P.R.L. Gondim, IoMT platform for pervasive healthcare data aggregation, processing, and sharing based on OneM2M and OpenEHR, Sensors ((2019) ). doi:10.3390/s19194283. |
[66] | T. Saba, K. Haseeb, I. Ahmed and A. Rehman, Secure and energy-efficient framework using Internet of Medical Things for e-healthcare, Infection and Public Health 13: ((2020) ), 1567–1575. doi:10.1016/j.jiph.2020.06.027. |
[67] | A. Sardar, S. Umer, R.K. Rout, S. Wang and M. Tanveer, A secure face recognition for IoT-enabled healthcare system, ACM Trans. Sen. Netw. ((2023) ). doi:10.1145/3534122. |
[68] | U. Satija, B. Ramkumar and M.S. Manikanadan, Real-time signal quality-aware ECG telemetry system for IoT-based health care monitoring, IEEE Internet of Things Journal 4: ((2017) ), 815–823. doi:10.1109/JIOT.2017.2670022. |
[69] | V. Sellam, N. Kannan and H.A. Basha, An Effective Fuzzy Logic Based Clustering Scheme for Edge-Computing Based Internet of Medical Things Systems, Springer, (2020) . doi:10.1007/978-3-030-55833-8_6. |
[70] | P. Sharma, S. Namasudra, N. Chilamkurti, B. Kim and R.G. Crespo, Blockchain-based privacy preservation for IoT-enabled healthcare system, ACM Trans. Sensor Netw. ((2023) ). doi:10.1145/3577926. |
[71] | S. Shen, Y. Han, X. Wang and Y. Wang, Computation offloading with multiple agents in edge-computing–supported IoT, ACM Transactions on Sensor Networks ((2022) ). doi:10.1145/3372025. |
[72] | W. Shi, J. Cao, Q. Zhang, Y. Li and L. Xu, Edge computing: Vision and challenges, IEEE Internet of Things Journal 3: ((2016) ), 637–646. doi:10.1109/JIOT.2016.2579198. |
[73] | T. Sigwele, Y.F. Hu, M. Ali, J. Hou, M. Susanto and H. Fitriawan, An Intelligent Edge Computing Based Semantic Gateway for Healthcare Systems Interoperability and Collaboration, IEEE, (2018) . doi:10.1109/FiCloud.2018.00060. |
[74] | M. Simic, I. Prokic, J. Dedeic, G. Sladic and B. Milosavljevic, Towards edge computing as a service: Dynamic formation of the micro data-centers, IEEE Access, IEEE 9: ((2021) ), 114468–114484. doi:10.1109/ACCESS.2021.3104475. |
[75] | A.H. Sodhro, Z. Lue, A.K. Sangaiah and S.W. Baik, Mobile edge computing based QoS optimization in medical healthcare applications, Information Management ((2018) ). doi:10.1016/j.ijinfomgt.2018.08.004. |
[76] | A.H. Sodhro, S. Pirbhulal and V.H.C.d. Albuquerque, Artificial intelligence-driven mechanism for edge computing-based industrial applications, IEEE Transactions on Industrial Informatics ((2019) ). doi:10.1109/TII.2019.2902878. |
[77] | N. Sohrabi Safa, C. Maple, M. Haghparast, T. Watson and M. Dianati, An Opportunistic Resource Management Model to Overcome Resource-Constraint in the Internet of Things, Wiley, New York, (2018) . doi:10.1002/cpe.5014. |
[78] | M. Sookhak, M.R. Jabbarpour, N. Sohrabi Safa and F. Richard Yu, Blockchain and smart contract for access control in healthcare: A survey, issues and challenges, and open issues, Journal of Network and Computer Applications ((2021) ). doi:10.1016/j.jnca.2020.102950. |
[79] | S. Swayamsiddha and C. Mohanty, in: Application of Cognitive Internet of Medical Things for COVID-19 Pandemic, Elsevier, Diabetes & Metabolic Syndrome: Clinical Research & Reviews, Vol. 14: , (2020) , pp. 911–915. doi:10.1016/j.dsx.2020.06.014. |
[80] | M.Z. Uddin, A wearable sensor-based activity prediction system to facilitate edge computing in smart healthcare system, J. Parallel Distrib. Comput, Elsevier 123: ((2019) ), 46–53. doi:10.1016/j.jpdc.2018.08.010. |
[81] | S.A. Wagan, J. Koo, I.F. Siddiqui, M. Attique, D.R. Shin and N.M.F. Qureshi, Internet of medical things and trending converged technologies: A comprehensive review on real-time applications, Journal of King Saud ((2022) ). doi:10.1016/j.jksuci.2022.09.005. |
[82] | H. Wang, J. Gong, Y. Zhuang, H. Shen and J. Lach, HealthEdge: Task Scheduling for Edge Computing with Health Emergency and Human Behavior Consideration in Smart Homes, 2017 International Conference on Networking, Architecture, and Storage (NAS), IEEE, (2017) . doi:10.1109/NAS.2017.8026861. |
[83] | M.S. Yaraziz, A. Jalili, M. Gheisari and Y. Liu, Recent trends towards privacy-preservation in Internet of Things, its challenges and future directions, in: IET Circuits, Devices & Systems, (2022) . doi:10.1049/cds2.12138. |
[84] | W. Yu, F. Liang, X. He, W.G. Hatcher, C.H. Lu, J. Lin and X. Yang, A survey on the edge computing for the Internet of Things, IEEE access 6: ((2018) ), 6900–6919. doi:10.1109/ACCESS.2017.2778504. |
[85] | H. Zhang, J. Li, B. Wen, Y. Xun and J. Liu, Connecting intelligent things in smart hospitals using NB-IoT, IEEE Internet of Things 5: ((2018) ), 1550–1560. doi:10.1109/JIOT.2018.2792423. |
[86] | J. Zhang, D. Li, Q. Hua, X. Qi, Z. Wen and S.H. Myint, 3D remote healthcare for noisy CT images in the Internet of Things using edge computing, IEEEAccess, IEEE 9: ((2021) ), 15170–15180. doi:10.1109/ACCESS.2021.3052469. |
[87] | Y. Zhang, G. Chen, H. Du, X. Yuan, M. Kadoch and M. Cheriet, Real-Time Remote Health Monitoring System Driven by 5G MEC-IoT, (2020) . doi:10.3390/electronics9111753. |



