Internet of Things for enabling smart environments: A technology-centric perspective
Abstract
The Internet of Things (IoT) is a computing paradigm whereby everyday life objects are augmented with computational and wireless communication capabilities, typically through the incorporation of resource-constrained devices including sensors and actuators, which enable their connection to the Internet. The IoT is seen as the key ingredient for the development of smart environments. Nevertheless, the current IoT ecosystem offers many alternative communication solutions with diverse performance characteristics. This situation presents a major challenge to identifying the most suitable IoT communication solution(s) for a particular smart environment. In this paper we consider the distinct requirements of key smart environments, namely the smart home, smart health, smart cities and smart factories, and relate them to current IoT communication solutions. Specifically, we describe the core characteristics of these smart environments and then proceed to provide a comprehensive survey of relevant IoT communication technologies and architectures. We conclude with our reflections on the crucial features of IoT solutions in this setting and a discussion of challenges that remain open for research.
1.Introduction
The Internet of Things (IoT) is a computing and communications paradigm whereby everyday life objects are connected to the Internet. Such connectivity, supported by the incorporation of resource-constrained devices including sensors and actuators, enables intelligent systems that obtain information from the physical world, process such information, and may perform actions on the physical world accordingly. Benefits of the IoT comprise efficient resource management, enhanced productivity, and increased quality-of-life for human populations [39]. The IoT is therefore a fundamental enabler of smart environments [24], such as smart homes, smart health, smart cities and smart factories, among others. Indeed, the trend towards smart-x promises a revolution for most kinds of human-related activities.
Advances in many technical areas are making the IoT and smart environments possible, including multiple communication solutions for IoT devices, which we categorize into two main families: i) Radio Frequency Identification (RFID), intended mainly for object and device identification, and ii) general-purpose Constrained-Node Network (CNN) technologies and architectures. The numerous and highly heterogeneous solutions available provide different features and performance trade-offs, a fact that makes identifying the most suitable IoT communication technologies and solutions for a particular smart environment challenging. While all smart environments collect, process and act upon information, different specific smart environments do so at different scales. Moreover, different vertical domains (e.g. smart home/health/city/factory) come with diverse requirements, and hence technology choices, which also influences the tactics of how and where data is processed and how to act upon the information within a specific context. Furthermore, different types of smart environments evolve at a different pace: Some vertical domains can evaluate and adopt new technologies much faster (e.g. smart home and smart health), while in others (e.g. smart factories and smart cities) changes cannot be adopted expediently due to the fact that such environments must deal with legacy systems. This requirement further complicates the choice of communication technologies and solution availability for particular smart environments.
In this paper, we identify emerging trends in IoT communication and compare different IoT technologies and solutions. We then collect lessons learnt from specific vertical domains to elicit best practices that are reusable across families of smart environments. In Section 2, we describe the main characteristics and services of smart home, smart health, smart cities, and smart factories. In Sections 3–5, we survey a wide range of IoT communication technologies and architectures, including RFID (Section 3), CNN technologies (Section 4) and CNN architectures (Section 5). In Section 6, we discuss crucial features of IoT solutions for supporting the highlighted smart environments, and we elaborate on the main remaining challenges. Finally, Section 7 concludes with a summary of the main insights of this work.
2.Smart environments
This Section provides an overview of the main features and services in key smart environments, including the smart home, smart health, smart cities and smart factories. These four vertical domains are chosen because of their distinct characteristics in size and complexity, such as personal- vs business- oriented, single-user vs many users, different “smartness” objectives, etc. Although clearly other types of smart environments exist, we focus on the aforementioned four domains as representative use cases.
2.1.Smart home
Fig. 1.
Main components in smart home systems.
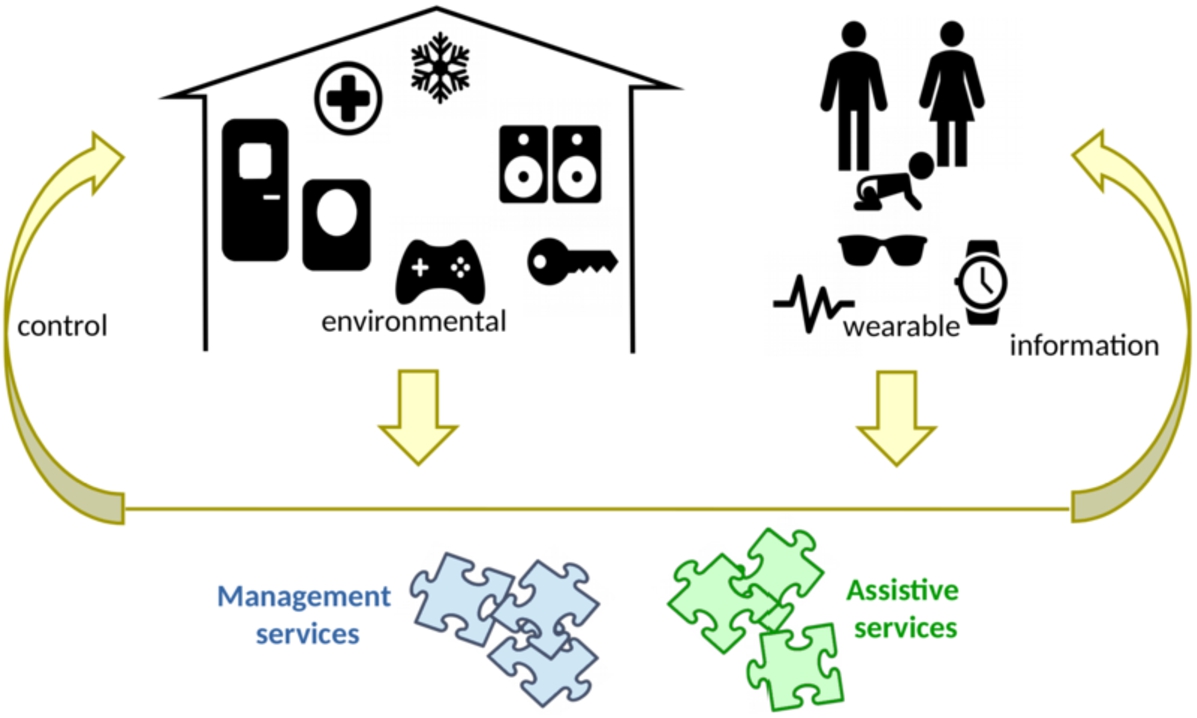
Homes are environments particularly suitable to host smart technologies for three main reasons: (i) modern homes already contain a large number of technological devices, even if not always interconnected or interoperable; (ii) they are controlled environments and their owners can (at least in principle) provide the suitable investments for the deployment of technological solutions and provide to their maintenance, and (iii) they can provide to the inhabitants a large number of useful services and applications.
Services of smart homes vary widely. We broadly classify them as assistive services and management services (Fig. 1). Assistive services in smart homes aim at providing direct support to the users in their interests [77] and in their daily actions and activities that take place in the home [15]. For example, if watching television or listening to music are particular user interests, the smart home can assist by scheduling sources of noise caused by machine automation (such as the activation of the washing machine) at different hours, or by setting appropriately the lights and the multimedia devices configuration, according to the users’ preferences. Assistive services may also be tailored to some special needs of the user, especially when the user is an elder or a disabled or just sick, like ambient assisted living [68] or e-health [18] services.
Further, management services are those that address specific functionalities of the smart home. Examples of such services can be those concerning the security and safety of inhabitants (for example the anti-intrusion alarms or the detection of gas leaks) [35] or those concerning energy efficiency of the home [65], such as those that control ventilation and solar panels for the energy production and those that control the appliances and lights to reduce energy consumption while satisfying the inhabitants’ needs.
Although individually different, smart home services are usually developed at the application level of context-aware systems, which, in turn, are built on top of common mechanisms and functions. In fact, at the foundation of such systems are home automation mechanisms, which provide the ability to monitor/control the building blocks of a home like windows, doors, electrical system, air conditioning system, energy production subsystem, alarm, appliances and so forth.
Furthermore, most advanced services also need information about the inhabitants that can be obtained by a combination of environmental and wearable sensors, possibly those embedded in the users’ personal devices such as smartphones for example. Such additional sensors are necessary to obtain a detailed context about the users that is crucial to make the smart home an intelligent environment at the service of the user. Examples of such information are the user position (by means of a localization system), the user physical condition (by means of wearable sensors) or the user activities (by means of combined wearable and environmental sensors).
However, this information, which is often high-level, cannot be obtained by a direct observation of raw data coming from sensors. Instead, it must be processed by suitable data fusion algorithms, usually based on signal processing, machine learning and/or data analysis algorithms.
From the perspective of the information and communication technology (ICT), support for the full range of these mechanisms and services requires the development of a complete and complex IoT infrastructure. Such infrastructure must span the full range from the sensor/state data acquisition, storage and fusion to the data presentation and control of the actuation mechanisms present in the home, and should also include the appropriate support for deployment, commissioning and maintenance.
Employing contemporary standards and technologies, basic functionalities for sensing, state acquisition and control can already be achieved with relative ease. In particular, at the level of home automation, several standards [38] already provide adequate support, which include accessing state or sensor information and binding this information to the control/actuation mechanisms. Similarly, both ZigBee [32] and Bluetooth [30] support the integration of wearable devices and, at an upper layer, M2M standards [3] including but not limited to MQTT and CoAP, provide the mechanisms necessary to integrate the smart home in cloud services over the Internet. On the other hand, the development of services and applications in smart homes reflecting use cases and business plans of rich application scenarios is usually supported by specialized platforms for example, see Section 2.2.3 for AAL [28].
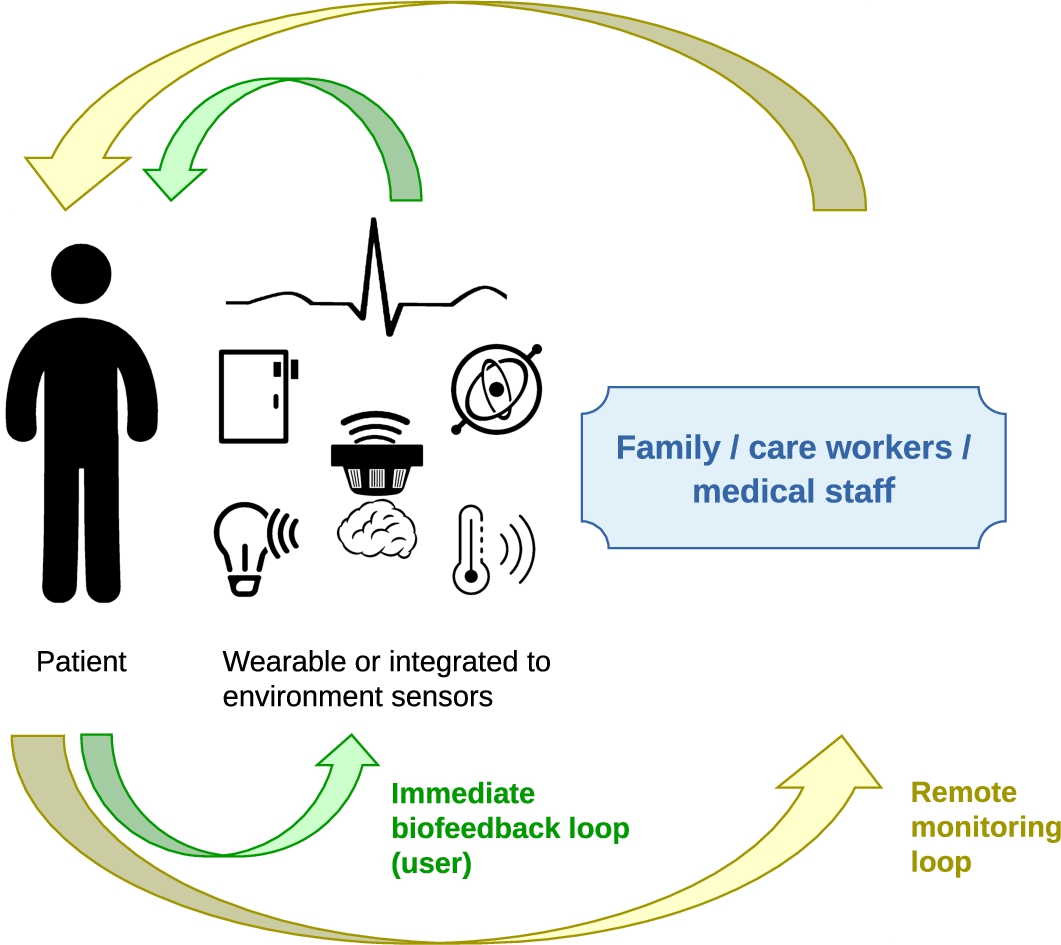
Fig. 2.
General description of IoT or smart environments for health.
Another aspect of IoT that has been confined so far to research, concerns the adaptation and personalization of services offered by smart homes. Adaptation and personalization consider the ability of a smart home to automatically tailor its services to the individual user’s needs. This is often achieved by building on generic services designed for a specific group of users such as children or the elderly, and then by adapting the behavior of the service to the habits of the user. This implies the ability to detect habits as well as to discover deviations from these habits while at the same time, to automatically reconfigure the business logic of the service or application. Such mechanisms usually require a strong convergence among sensors and activity recognition, anomaly detection and cognitive capabilities, especially in those cases in which at least part of these capabilities are integrated within the sensors themselves. Significant preliminary experiences with this approach which is often referred to as the Internet of Intelligent Things [4], has been obtained by EU projects RUBICON [56] and OPPORTUNITY [6].
2.2.Smart health
Over the last twenty years, due to significant reductions to the cost of sensors and improvements in both signal processing techniques and integration/quality of signal, applications of smart environments and Internet of Things to health have expanded rapidly. This Section relates some of the work in this domain with an overview description of enabling technologies.
2.2.1.General description of solutions
Enabling technologies and their application to healthcare are presented under the common scheme described in Fig. 2. A set of sensors, integrated to the environment of the person and/or worn by him/her will acquire some data continuously or periodically and process them, to be able to firstly give some information or some feedback to the person and secondly inform the medical staff, the family or some other authorized persons of the status. These devices can be used for medical monitoring in specific contexts for instance after surgery, or to enable the person to live longer, in better health and independently for instance in applications for the elderly or for people with disabilities [45].
2.2.2.Distress situation detection
Continuous monitoring of a person using physiological data or even using contextual/activity data, can provide information on the physical condition of the person and the ability to raise alerts in case of distress or other hazardous situations.
One key example due to its importance in developed countries, is detecting fall for elderly people living independent. In France for instance it is one of the most frequent causes of emergency calls and of medical intervention for the elderly at home. Solutions must be found to analyze it, detect it better and know which kind of persons have to be sent (medical or normal citizen) to help the person. Fall is a highly studied subject in the last years and one of the main uses of IoT and smart environments for health-related applications [53,67].
One of the most common ways to detect fall is using inertial sensors that are worn by the person. With the wider availability and the power offered by smartphones in recent years, it has become possible to use their Inertial Motion Unit to detect falls. For example, [52] that fuses the different sensors of the smartphone (IMU, GPS, etc.) to try to understand the context of the alert raised by the motion sensors-based algorithm and reduce false positives. Another way to achieve this is to add external sensors to the IMU, such as PIR sensors in the home, and fuse them with the IMU to check the activity of the person in the next minutes after the detection of the event [36]. In the last years, video cameras [73] have been more and more used in this context. Depth cameras can give more information and analyze more easily the moving vs. background objects [27]. They can be used to analyze the scene, detect the activities and this abnormal scenario of fall. Concerning 2D cameras, [26] gives the state-of-the-art of the subject and tries to analyze the pertinence of the different results and the real advances that have been made versus what remains to overcome. Finally, other kinds of solutions exist and for instance [60] presents a solution that is based on radar sensors that are integrated to the home. Fall remains a very difficult (considering all the kinds of falls that exist) and challenging.
Another kind of situation that could be detected is heart conditions and for instance atrial fibrillation [59]. It can be detected using the camera of a smartphone or even now with a smartwatch. This detection concerns one of the most common heart problems in the world and is a subject of research nowadays by means of using phones and watches. Situations such as relapse in depression can also be detected and analyzed [5]. Such system can permit to act as soon as possible to prevent the state of the person to escalate.
2.2.3.Ambient assisted living
As presented in the previous Section, smart homes are a huge challenge in the last years and have been a hot topic of research. Indeed, data from ambient assisted living can also be used to infer the behavior of the person and detect changes in it to find signs of a degradation of the health of the person as soon as possible. There are multiple challenges in this case including the correct segmentation of data in uncontrolled trials [85], an important multimodality using very different kind of data [89], how to adapt the models to the person that we have to monitor [21], the problem to infer behavior or high-level data from the activities that are recognized [21] or the efficiency and capacities of different kind of recognitions [19]. This activity recognition is then crucial in applications related to health in smart homes as it will be the basis to infer the well-being of the person and to link the results to well-known and use scales in geriatrics such as ADLs. The challenges are very difficult as the first problem is that it is very difficult to separate the activities that are performed, and secondly the realization of the activities not only depends on the person that does it but also on the environment in which it is done. That leads to very complex models to construct and to evaluate.
From these detections and recognition, applications are then two-fold. The first kind is to evaluate the status of the person that is monitored in the home for a certain kind of problem, such as cognitive impairment [2]. This evaluation allows to show the evolution of the problem of the person to determine when he/she is not any more able to live independently. The second kind of application is to help people performing these activities taking into account the specificity of their disease/impairment [46]. It can improve their conditions of living at home and their experiences.
2.2.4.Prevention/assistance to healthcare
The final goal of all the solutions of smart sensors and environments for health is to help prevent or assist the person that has to face a specific condition. Dependence is one of the huge cost in our healthcare systems and if it can be improved, it would reduce this part. A lot of work focuses on that considering different kinds of assistance. For people with a disability for instance, [44] proposes a system that will combine a web-app to allow the caregiver to give instruction to the environment and a smartphone to help the person in daily living. Such development has required expertise to design it as efficiently as possible so that it can be useful to the person. It generally includes co-conception with users.
One of the major concerns in health is monitoring and/or improving the condition of persons with chronic diseases or recurrent disorders. For instance, some smart devices and applications can help managing chronic diseases such as diabetes [47]. The goal of such applications, that relies generally on measurement devices and/or on smartphones and other connected devices is to help the person to manage the effect of the disease and control it or control the observance of medication. Solutions can also be integrated in objects daily used such as the bed [91]. In this application, the goal is to analyze the sleep conditions in order to detect and/or quantify changes in it and thus detect disorders. To this end, sensors and strain gauge are integrated to the bed. The long-term evolution of the uses of the person is important and relevant to the improvement or degradation of living conditions of the person. Other data can be acquired, such as heart rate, to be able to monitor in long terms the evolution of this data, and possibly in the future to raise alarms such as described before in the distress situations detection [78].
Fig. 3.
A subset of the most relevant domains in the smart city.
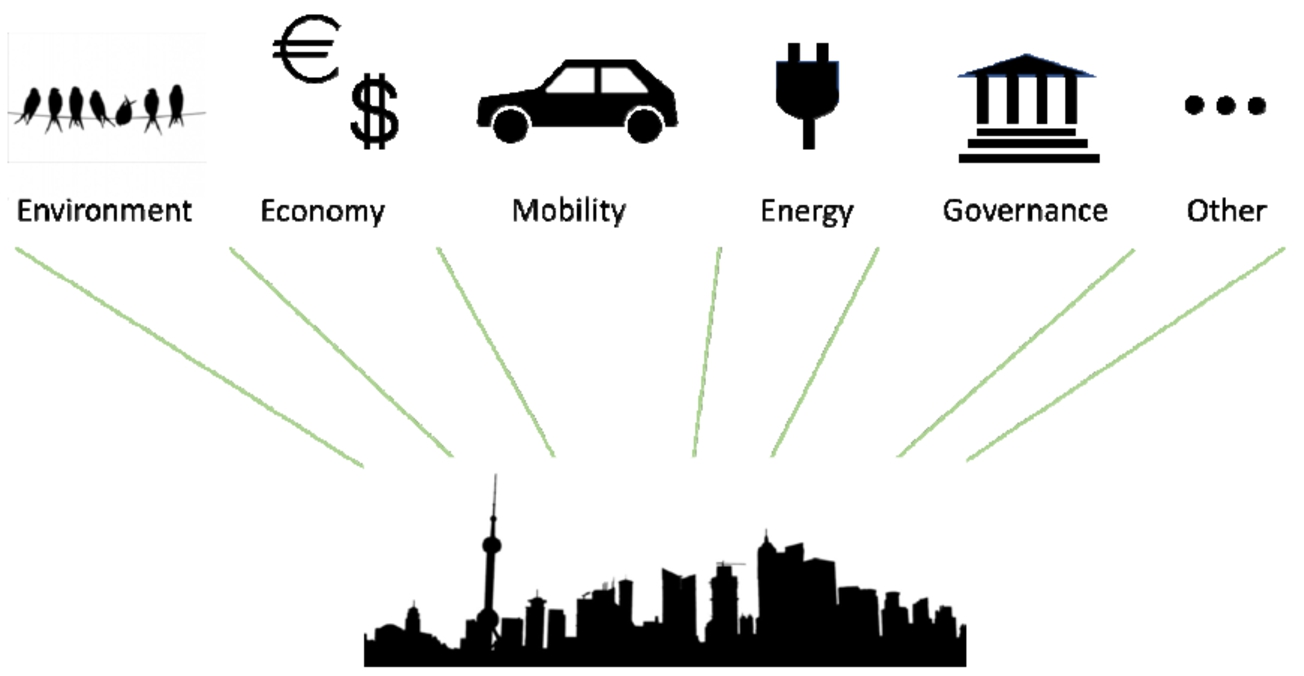
To conclude this Section, one of the important applications is the monitoring of and help offered to elderly people. In all developed countries, population is ageing fast due to improvements in medicine, and another fact is that the family is spreading all over countries and ageing people generally are lonelier than in the past. In addition to the works that monitor activities of daily living of the person, monitoring some characteristics of the living conditions of the person could be important. For instance, in [7] and [72], gait or time of transfers are measured along time, and their evolution is characterized. This evolution is another point of evaluating possible entrance in dependency. As a prevention, some works [12,31] propose to train the person with some specific exercises (link to posture, transfers or movements) to prevent fall or give benefit to the person.
Finally, in case of dependence, robots can be of help for the person to allow measurement and monitoring, and more importantly, to create a presence for the person and bring help in case of specific needs [70].
As seen in this Section, health applications are numerous and go from distress situation detection to long-term monitoring in smart environments. Such monitoring can be included in larger architectures. In the future, we could think that it can be included in smart city architectures. Smart cities are the subject of the next Section.
2.3.Smart city
Smart cities are one of the richest and most com-plex scenarios for smart environment (if not already the most complex) [86,87]. It crosses several domains including the environment, economy, mobility, energy, planning, governance among others (see Fig. 3) presenting a large number of associated challenges and involving multiple actors such as city administrators, operators, service providers and citizens, with possibly competing objectives.
It is thus clear that smart cities are not just a technological challenge, but they are the place in which the challenges to the technology are the most diverse and heterogeneous, and the technological solutions must confront themselves against many interests and needs.
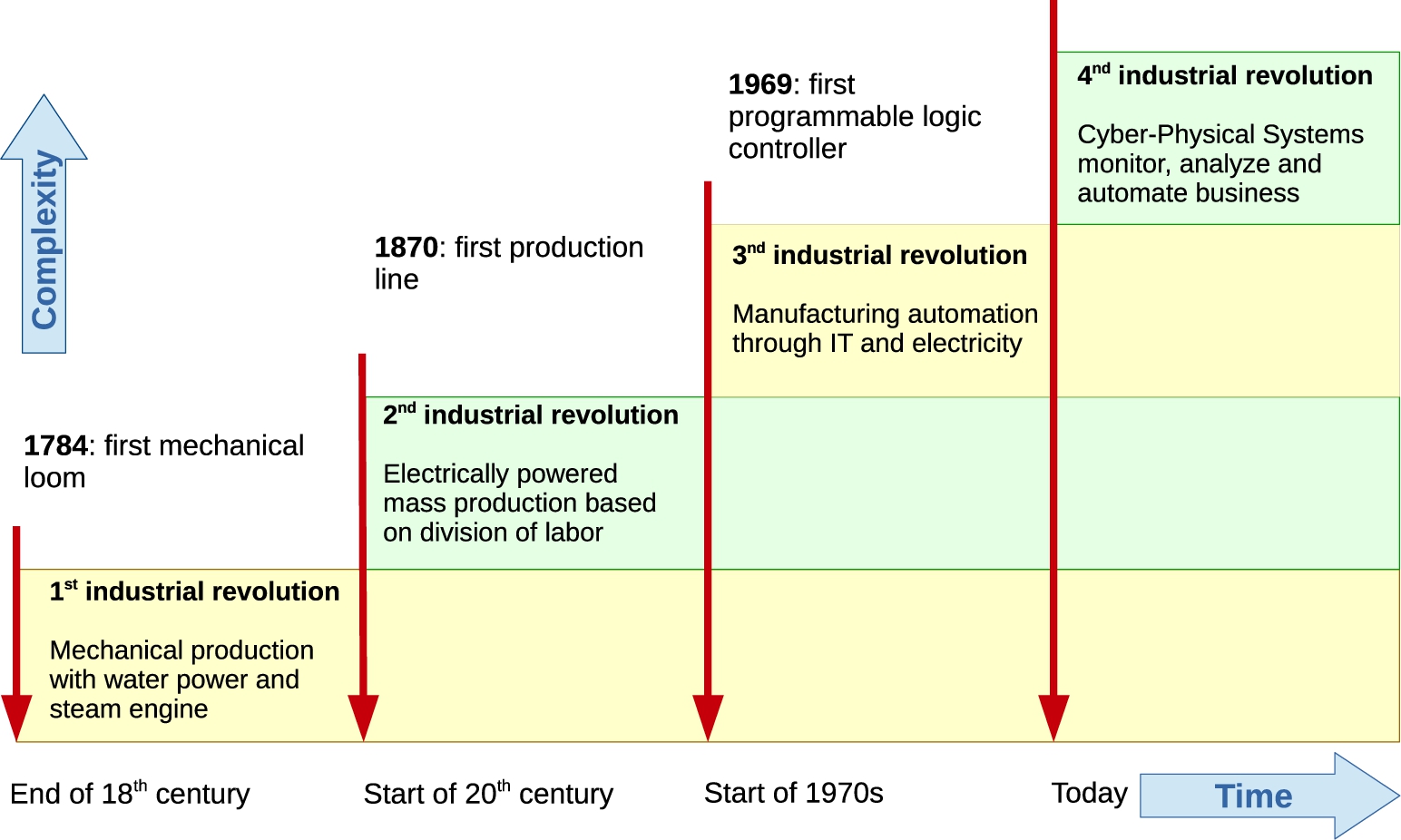
Fig. 4.
The 4 industrial revolutions leading to the smart factory of the future and cyber-physical production systems.
From an ICT perspective, its technologies are of-ten transversal to all domains and challenges, and they address a number of scenarios of smart cities spanning from e-tourism [88], e-culture [11], e-government [61], smart energy [63], smart mobility [96], e-health/wellbeing [25], just to mention a few.
The heterogeneity of technical problems and of available technologies [84], united to political issues [54], are barriers that may delay the development of smart cities. It is thus no surprise that the interoperability of technological solutions and standards are of utmost importance, especially in the field of the Internet of Things, which is widely recognized as a key technological enabler of smart cities [95]. Most recent trends, under this respect, are the introduction of novel participatory sensing paradigms that involve the citizens themselves in the (expensive) task of sensing data from the cities, by means mobile applications for personal smartphones [17].
In addition to reducing or indeed avoiding the costs due to the deployment and maintenance of capillary sensory apparatus in the city, such paradigms have also the great advantage of empowering users in the development of smart cities. However, the relative youth of these approaches makes them even farther from a standardization, and many different experimental platforms have been tested in several smart cities [16,43,57]. Furthermore, recent approaches to participatory sensing are also experiencing novel forms of network organization based on emerging edge computing [10].
2.4.Smart factory and industry 4.0
Industry 4.0 is an emerging business paradigm that is reaping the benefits of enabling technologies driving intelligent systems and environments [74]. While acquiring, processing and acting upon various kinds of relevant context information is common in application areas such as smart homes and offices, smart automated manufacturing systems can benefit from these capabilities as well. For example, smart manufacturing systems can make well-informed decisions to adapt and optimize their production processes at runtime or adapt to a customer’s personal preferences without any delay on the production process. The proliferation of smart enabling technologies has sparked a digital transformation in the manufacturing world. This paradigm shift is often referred to as the 4th Generation Industrial Revolution (Industry 4.0) [34,58] or the Factory of the Future (FoF) [50], as depicted in Fig. 4.
It envisions smart factories where the Internet of Things (IoT) and Cyber-Physical Systems (CPS)-enabled manufacturing [66] provide the foundations for creating smart products through smart processes and procedures. Large factories connect hundreds – if not thousands – of sensors and devices, not only within the plant, but also with other factories and the outside world. Smart products will plan, control and optimize their own production process with minimal human intervention by harnessing ongoing developments in sensor technology, machine-to-machine communication [90], big data analytics [69] and machine learning [71,75]. The purpose of this digital transformation is to enhance the transparency of the production process across the organizational boundaries of the manufacturing enterprise.
Enhanced access to data from the Industrial IoT (IIoT) [34] will support business applications on any device, any time, from any location. In turn, the data-intensive nature of smart production systems will enable timely, accurate and detailed log trails resulting in a real-time augmented view on many systems and activities in a way that was not previously possible. A consequence is that the production floor has become an inherently complex intelligent environment, as the digital and physical worlds are heavily intertwined.
Indeed, interconnected systems will be linked to cloud services for remote monitoring and data analytics to optimize production plans, enable proactive maintenance, and respond quicker to continuously changing customer requirements. The factory of the future will leverage data-accessing and data-processing services available on the Internet to support data-intensive business processes and time-critical applications, as depicted in Fig. 5.
Fig. 5.
Networked production and manufacturing.
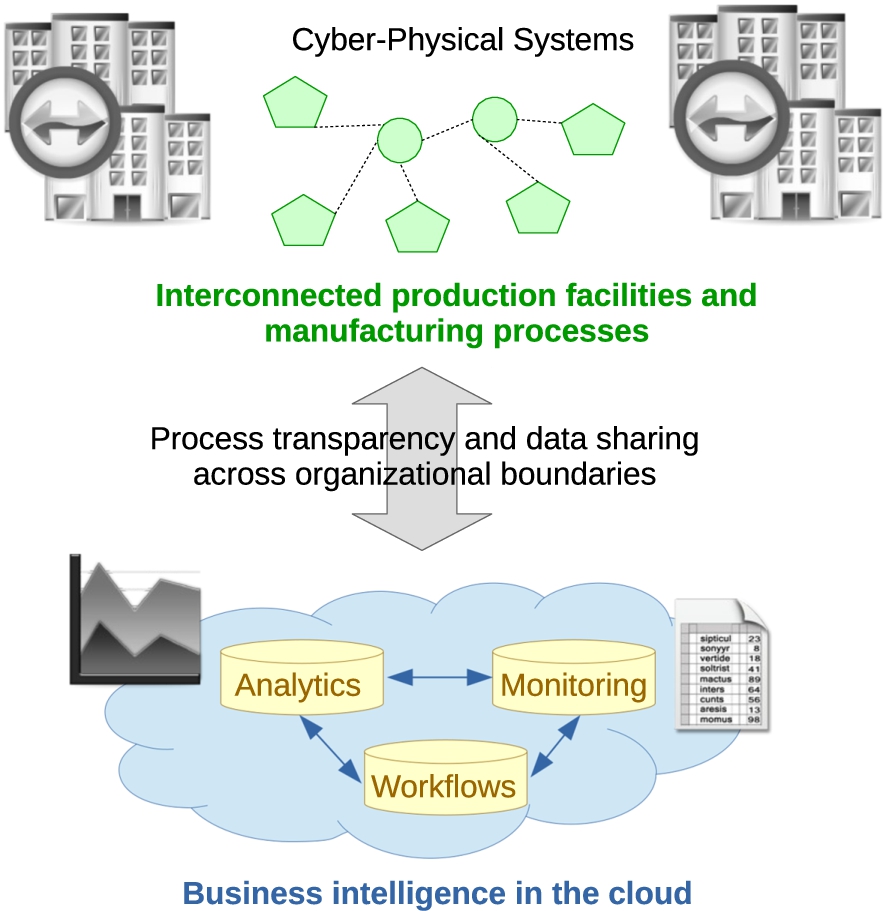
With networked production as a key feature of Industry 4.0, people, machines and business processes will interact with one another to enable personalized products through flexible, resource-efficient and cost-effective manufacturing.
3.Radio frequency identification
As it can be concluded from the previous Section, IoT communication solutions constitute a fundamental enabler of smart environments. This Section focuses on RFID, which is a family of solutions mainly intended to provide device identification.
A traditional RFID system consists of two elements namely a reader or interrogator which typically controls communication with several tags, low-cost devices that can be easily embedded into a variety of physical artefacts and assets. Contrary to other low-power wireless communication systems, RFID is an asymmetric system in that in most cases the interrogator not only controls all communication with the tags but also provides the energy source for the tags through the emission of its radio frequency signal [79,81]. This distinctive architecture enables the development of systems where a relatively small number of expensive components are combined with a very-large number of low-cost tags to optimize the overall cost of the system. For example, a metropolitan transit ticketing system such as the Oyster card in London or the Suica card in Tokyo, incorporate reade.rs in the thousands with millions of tags embedded in tickets and mobile devices.
The use of RFID in the IoT context introduces two additional elements that are necessary to enable large-scale open infrastructures: (i) universally unique identification (UUID) schemes that allow each entity connected to the IoT to be unambiguously identified through an alphanumeric handle, and (ii) networked services that allow the mapping of a handle to entity-related information and supporting meta-data.
Table 1
RFID technologies by frequency band
| RFID Name | Band | Frequencies in use |
| Low Frequency (125–134.2 kHz) | 125 kHz RFID 134 kHz RFID | |
| High Frequency (13.553–13.567 MHz) | 13.56 MHz RFID | |
| UHF | Ultra-High Frequency(433 MHz and 858–960 MHz) | 433 MHz RFID UHF RFID (including ETSI RFID at 865–868 and FCC RFID at 902–928) |
| Microwave | Microwave (2.4–2.454 GHz 5.725–5.875 GHz) | 2.4 GHz RFID 5.8 GHz RFID |
Table 2
RFID technologies by chip type
| Chip type | Description |
| Passive | Tag power source: RF energy transmitted by reader/integrator; Communication: by modulation of the reader/integrator signal |
| Semi-Passive | Tag power source: battery; Communication: by modulation of the reader/integrator signal |
| Active | Tag power source: battery; Communication: active transmission |
| Sensor Tag | Simple sensor integrated in the tag (temperature, pressure or humidity); Tag power source: battery or RF harvesting; Communication: passive or active transmission |
| Chipless | No chip but uses time-domain reflectometry (e.g. surface acoustic waves) |
Table 3
Main flavors of RFID technologies used in IoT systems
| Technology | Brand name | Typical frequency | Range | Bit rate and tag density | Typical applications | Organization responsible |
| ISO 14443 | NXP Mifare Sony FeLiCa | 13.56 MHz | Short | Low | Personal identification Payments and ticketing Access control and security | ISO/IEC |
| ISO 18000-63 | EPC Gen2 RAIN RFID | 858–960 MHz (depending on region) | Long | High | Asset tracking Logistics Retail/Consumer applications | ISO/IEC/EPCglobal |
| ISO 18000-7 EN 300 220–2007 | N/A | 433 MHz | Very Long | High or Very High | Real-time Location Tracking Industrial/Hardened | ISO/IEC/ETSI |
3.1.RFID technologies
RFID is the umbrella term in common use which covers a variety of distinct technologies using a wide range of frequencies, communication protocols, and device types. Moreover, RFID technologies have been standardized under many different organizations including international such as ISO, ITU and IEC as well as national such as DIN (Germany), JIS (Japan) and SINIAV (Brazil). The confusing landscape of RFID is further complicated by the common use of commercial brand names such as Mifare and RAIN RFID as alternatives to the difficult to use alphanumeric standard names.
To provide some structure and help navigate the range of RFID technologies a common approach is to refer to different technologies using the names of the corresponding frequency band as summarized in Table 1. Furthermore, often RFID technologies are characterized with reference to their tag chip technology, which also defines their communication characteristics, as summarized in Table 2.
Despite the great variety of RFID technologies and flavors on offer, the vast majority of applications developed in the context of the IoT reviewed in Section 2 above typically employ one of the three most common types summarized in Table 3. This table provides summary information that can be used to select the particular flavors that meet the requirements of a particular IoT application matching specific characteristics such as the number of co-located tags that must be supported (depending on the ability of the technology in terms of reading speed and its ability to avoid collisions), security provisions, tag capacity, range, tag packaging and form as well as the ability to easily integrate readers in bespoke system designs.
3.2.Identifier schemes
As noted earlier, for the development of open IoT systems, which typically incorporate a variety of stakeholders and must support scalable operation, RFID must support a common way to interpret identifiers retrieved from tags [81]. Moreover, standard identifier schemes are already in widespread use for a variety of material objects, locations and even digital artifacts so demanding that RFID within the IoT starts from a clean slate would not be feasible either from a financial or an organizational point of view. Electronic Product Codes (EPC) developed by SG-1 and EPCglobal, Object Identifiers (OID) according to the ISO/ITU standard, Ubiquitous IDs (uID) in wide use in Japan as well as a variety of other schemes commonly employed in RFID and barcode encodings, often in an industry-specific manner, are in current common use for the identification of billions of already tagged objects.
Although it is not possible to cover each one of these schemes in detail in this paper, we note that all schemes follow a similar pattern to structure their codes. Specifically, each code starts with a prefix which identifies the particular type of code that follows, for example within the EPC system, the prefix of 00110000 identifies the remainder of the codes as a Serialized Global Trade Item Number of length 96 bits (SGTIN-96). The remainder of the code is then typically organized in a hierarchical manner to enable code allocation delegation across regions or organizations. In the case of SGTIN-96 codes for example, the code will include the company prefix identifying the manufacturer of the particular product, the item reference identifying the product type and finally a serial number that is unique to the particular product item. Similar structures exist for OID (specified under Section 9834-8:2009 of ISO/IEC) and uID although of course identifier space management and regulation are carried out through their respective organizational custodians.
3.3.Identifier resolution systems
Notwithstanding the specific choice of identifier use, any IoT system that incorporates RFID-tagged entities must provide an automated way to discover information associated with a particular identifier as well as control access to this information in a manner that ensures secure operation and privacy protection. In the content of IoT RFID, this system capability is referred to as the Identifier Resolution Service(s).
Many of the current proposals for IRSs provide specifications for scheme-specific services: for example, EPCglobal [55] provides resolution services that cater only for EPC codes issued within their ecosystems. Ongoing work by ISO/IEC JTC 1/SC 6/WG 9 and ITU-T Q12/SG17 has developed an OID resolver specification known as X.oid-res or the SG17 ORS (OID Resolution Service). In contrast to that work, IoT applications require an open and inclusive approach. For example, the extensive experience and experimentation in this area conducted within the Internet Engineering Task Force (IETF) and specifically the work carried out on the HIP (RFC 5201) and LISP (RFC 6115) protocols and on scalable Internet-scale resolution systems [39] offers valuable lessons on how to enable IoT-scale IRS that can cater to all types of RFID irrespective of the specific UUID scheme employed. At the time of writing, there is no commonly accepted standard but certain developments point the way towards a usable solution [80].
4.CNN communication technologies
While RFID systems mainly aim at communicating the identification of a given object, CNNs serve more general purposes regarding interaction with the physical world. CNN devices are often tiny computers provided with sensing and/or acting capabilities, which however may exhibit computational constraints such as RAM in the order of
This Section introduces the main wireless or wired communication technologies used in the CNN space. Many such technologies typically provide only Physical layer (PHY) and Medium Access Control layer (MAC) functionality, although some of them are defined as part of a larger protocol stack. As shown in this Section, a wide range of CNN technologies is available. However, each technology may have specific characteristics and may be better suited for a limited set of environments and scenarios.
The set of technologies presented in this Section comprises IEEE 802.15.4, Bluetooth Low Energy (BLE), ITU-T G.9959, Digital Enhanced Cordless Telecommunications Ultra Low Energy (DECT-ULE), Near Field Communication (NFC), Wi-Fi, LoRaWAN, Sigfox, Narrowband IoT (NB-IoT), Power Line Communication (PLC) and Master-Slave/Token Passing (MS/TP). The main features of these technologies are summarized in Table 4.
Table 4
Main features of IoT technologies
| Technology | Medium | Frequency Band (MHz) | Range (m) | Bit rate (kbit/s) | Network topology | Responsible organization |
| IEEE 802.15.4 | Wireless | 868/915/2400 | 20/40/250 | Star and mesh | IEEE | |
| BLE | Wireless | 2400 | 1000 | Star and mesh | Bluetooth SIG | |
| ITU-T G.9959 | Wireless | 868/915 | 9.6/40/100 | Mesh | ITU-T | |
| DECT-ULE | Wireless | 1900 | 1152 | Star | ETSI | |
| NFC | Wireless | 13.56 | 106/212/424 | Point-to-point | NFC Forum | |
| IEEE 802.11ah | Wireless | 150–7800 | Star | IEEE | ||
| LoRaWAN | Wireless | 433/868/915 | 0.25–50 | Star | LoRaWAN Alliance | |
| Sigfox | Wireless | 868/902 | 0.1–0.6 | Star | Sigfox | |
| NB-IoT | Wireless | Several (licensed) | 60/30 (uplink/down.) | Star | 3GPP | |
| PLC | Wired | 500 (IEEE 1901.2) | Mesh | IEEE, ITU-T | ||
| MS/TP | Wired | Baseband | 115.2 | Multidrop bus | ANSI/ASHRAE |
4.1.IEEE 802.15.4
IEEE 802.15.4 is a family of wireless technologies intended to enable monitoring and control applications for Wireless Personal Area Network (WPAN). Publication of its first version in 2003 was a milestone, since for the first time, an open standard targeted low-rate communication, with a focus on simplicity and low energy consumption [9].
IEEE 802.15.4 was not designed for a specific application domain. Instead, it is intended as a generic technology, and it has become the basis of relevant protocol architectures, supporting IPv6, and also non-IP-based protocol solutions such as ZigBee (see Section 5). Nevertheless, IEEE 802.15.4 has been optimized for specific environments, such as the IEEE 802.15.4e Time Slotted Channel Hopping (TSCH) mode, designed to overcome impairments in industrial environments [93]. In fact, TSCH is also used in standard protocol stacks on top of IEEE 802.15.4 for industrial environments such as ISA 100.11a and WirelessHART.
4.2.BLE
BLE was released in 2010 as a low-energy variant of classic Bluetooth [37]. Since BLE can partially reuse Bluetooth hardware, a device that supports classic Bluetooth can also support BLE for low additional cost. Therefore, BLE can leverage its widespread presence in smartphones, which can be used to collect data from or send commands to surrounding sensors and actuators. The smartphone can also be used as a gateway for interaction between sensors, actuators, and the Internet. In addition, BLE has become dominant in the areas of wearables, tablets, and other consumer electronics devices [1].
4.3.ITU-T G.9959 (Z-Wave)
ITU-T G.9959 is an open standard that specifies the lower layers of the Z-Wave technology. Z-Wave is a wireless protocol stack that was born as a proprietary technology, which has been specifically designed for home automation [38].
4.4.DECT-ULE
DECT-ULE is a low-energy variant of DECT, which is the main technology used for voice and data communication for indoor cordless telephony [93]. Use of DECT-ULE has been proposed in order to enable communication between a gateway and sensors or actuators in the home, by exploiting the strong presence of DECT equipment.
4.5.NFC
NFC is a wireless technology that provides very short range (e.g.
4.6.IEEE 802.11
IEEE 802.11 is a massively successful Wireless Local Area Network (WLAN) family of standards, often referred to as Wi-Fi. While its design includes power-saving mechanisms, it has not been a clear choice for energy-constrained devices, given its implementation complexity and overall power consumption. In order to fill the gap of IEEE 802.11 for sensor/actuator applications, IEEE 802.11ah has been recently designed for low energy consumption, lower bit rate and increased range, enabling sensor data collection application areas such as smart grid [8].
4.7.LoRaWAN
LoRaWAN is an unlicensed band wireless technology that belongs in the emerging Low Power Wide Area Network (LPWAN) category. LoRaWAN uses LoRa technology at the physical layer, and it allows an increased communication range up to the order of 10 s of kms. Based on a star topology, whereby a gateway collects data from up to hundreds of thousands of devices such as sensors, it offers a low infrastructure cost, at the expense of severe message rate and bit rate limitations [29].
4.8.Sigfox
Sigfox is another flagship LPWAN wireless technology, therefore it offers long range and low infrastructure coverage for a massive amount of devices, at the expense of very reduced bit and message rates. This technology operates in unlicensed frequency bands, and it is managed by the company that is also called Sigfox. Like other LPWAN technologies, it is based on the star topology, and a communication range in the order of 10 s of kms is achievable [29].
4.9.NB-IoT
Narrowband IoT (NB-IoT) is another emerging technology that is often considered to be in the LPWAN category [92]. NB-IoT has been defined in the Release 13 specification by 3GPP, it is based on licensed spectrum, and it also offers support of a large number of devices per single base station, at low bit rates.
4.10.PLC
Power Line Communication (PLC) defines a family of technologies that leverage power grid infrastructure as a means for communication. While PLC is based on using a wired medium, it is subject to interference, therefore it is subject to impairments similar to those of wireless media. There exist low bit rate PLC variants such as IEEE 1901.2 or ITU-T G.9903, which are often used in smart home or related applications such as smart grid [42].
4.11.MS/TP
Master Slave/Token Passing (MS/TP) is a wired technology that belongs to the BACnet family of standards for building automation. Devices that use MS/TP are typically grid-powered. While the described features do not pose the same degree of limitations as other technologies overviewed in this Section, devices that use MS/TP are constrained, and the physical layer, based on RS-485 specification, offers low bit rates [62].
5.CNN protocol architectures
The previous Section provided an overview of the main communications technologies used in IoT applications. This Section presents the main protocol architectures, i.e. complete sets of communication protocols, from the PHY to the application layer in the IoT space. We first focus on IP-based architectures, and then we overview non-IP-based stacks.
5.1.IP-based architectures
In order to obtain the maximum benefit from sensors and actuators, they need to be connected to the Internet, which allows the highest degree of flexibility (i.e. making it possible to communicate with these devices remotely) and interoperability (i.e. Internet connectivity maximizes the number of devices that one device can talk to).
Running IP can be considered the most suitable method for many constrained devices to achieve Internet connectivity. IP is an open protocol, it was designed for interoperability, and it simplifies application development, since applications run on well-known services on top of IP, regardless of the underlying technology [39].
The least constrained devices (e.g. class 2 or greater [14]) are considered to be able to run a traditional IP-based protocol stack (e.g. using HTTP, TCP, and IP, on top of common network interfaces, see Fig. 6-left, especially when such devices are grid-powered.
Fig. 6.
IP-based protocol architectures, including typical application layer and transport layer protocols: Classic architecture (left) and IoT-specific architecture (right). RPL is only used for multihop topology IoT networks.
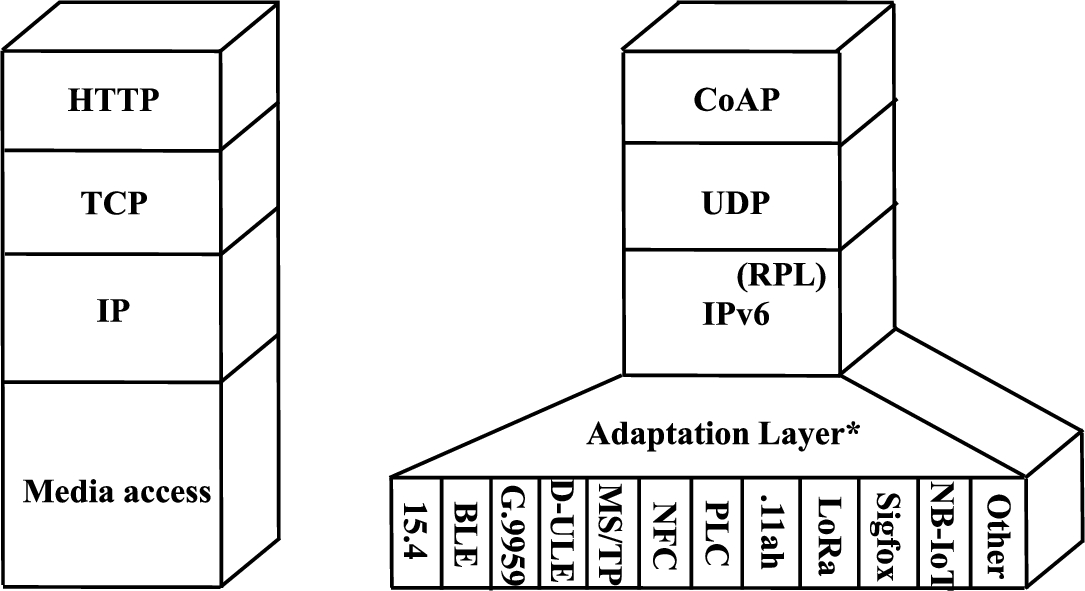
However, the most constrained devices, and/or those that are energy-constrained, cannot afford the more traditional protocol stack, due to lack of sufficient computational power and energy availability. For this reason, the IETF engaged in 2005 in a decade-long process to define adaptations, optimizations and new protocols for a first version of an IPv6-based lightweight protocol stack for constrained devices. IPv6 was assumed at the core of the stack, since IPv4 faces the problem of address exhaustion, and also because IPv6 is provided with tools for device self-configuration. The lightweight, IoT-specific protocol stack (see Fig. 6-right) comprises an adaptation layer below IPv6 [82], the IPv6 Routing Protocol for Low-power and lossy networks (RPL) [94], and the Constrained Application Protocol (CoAP) [83].
IPv6 over Low power WPAN (6LoWPAN) is an adaptation layer that was designed in order to support IPv6 over IEEE 802.15.4 networks. Among others, 6LoWPAN provides IPv6 (and UDP) header compression, packet fragmentation and reassembly (given the short IEEE 802.15.4 frame size), and an adaptation of the IPv6 Neighbor Discovery protocol for energy-constrained devices [82].
The 6LoWPAN work has been extended to several other technologies. For example, as of the writing, the IETF effort called 6Lo has adapted 6LoWPAN for interfaces such as BLE, DECT-ULE, ITU-T G.9959, MS/TP, and NFC [1]. On the other hand, the effort called IPv6 over Time Slotted Channel Hopping (6TiSCH) has enabled IPv6 support over IEEE 802.15.4e TSCH mode [93]. Finally, the IETF has recently targeted IPv6 support over LPWAN technologies, such as Sigfox, LoRaWAN and NB-IoT [64]. While this effort also provides header compression and fragmentation, the extremely severe communication constraints in some of the considered technologies, requires this adaptation layer to go significantly beyond 6LoWPAN-style adaptation.
At the network layer, for networks that follow a multihop topology (e.g. the mesh topology), a routing protocol is needed. RPL was designed for sensor data collection applications. In fact, RPL is optimized when all nodes in a network need to report data to a single destination, by minimizing routing table memory requirements and message overhead. However, RPL is not optimal for any-to-any operation and requires additional mechanisms in such case [22].
Finally, at the application layer, CoAP was designed to follow the Representational State Transfer (REST) principles, which are also used in the World Wide Web (WWW) [13]. CoAP can be viewed as a lightweight cousin of HTTP, as it allows the manipulation of resources identified by Uniform Resource Identifiers (URIs), and messages are self-contained, albeit with a lightweight binary header, and based (by default) on UDP.
5.2.Non-IP-based architectures
There exist also complete protocol architectures for sensor and/or actuator devices that are not based on IP. For example, ZigBee defined its own upper layer functionality on top of IEEE 802.15.4. BLE and Z-Wave are other non-IP-based complete protocol stacks. Internet connectivity for non-IP-based protocol stacks can be achieved by means of Protocol Translation Gateways (PTGs), which pose management issues and limit application development. Nevertheless, ZigBee, BLE and Z-Wave also support protocol stack variants that are based on IP.
6.Discussion
In this paper, we discussed selected smart environments of key relevance to research in Section 2; and, reviewed alternative IoT communication solutions fundamental to enabling such smart environments in Sections 3–5. In this Section, we reflect on different aspects of how smart environments are supported by underlying IoT communication solutions.
In the first part of this Section, we identify and reflect on crucial features of IoT solutions and then proceed to discuss the main challenges for the applications of these IoT solutions in smart environments.
6.1.IoT solutions features and smart environments
The following features of IoT solutions used in the selected smart environments are discussed first, specifically the type of sensors used, CNN topology, technology capabilities, and computing approach (see Table 5).
Table 5
Main features of IoT solutions in smart environments
| Smart environment | Type of sensors | CNN topology | Technologies | Computing approach |
| Smart home | Dedicated | Mesh and Star | IEEE 802.15.4 | Cloud |
| Bluetooth LE | ||||
| Wi-Fi | ||||
| ITU-T G.9959 | ||||
| DECT-ULE | ||||
| PLC | ||||
| Smartphone | N/A | Wi-Fi | ||
| Smart city | Dedicated | Star | LoRaWAN | Cloud and Fog |
| Sigfox | ||||
| NB-IoT | ||||
| Dedicated | Mesh | IEEE 802.15.4 | ||
| Smartphone | N/A | 4G, Wi-Fi | ||
| Smart factory | Dedicated | Mesh | IEEE 802.15.4 TSCH | Fog |
6.1.1.Type of sensors
A smart environment will typically be instrumented with dedicated sensors that measure physical parameters of interest. Such sensors may be statically located at points of interest within the target environment for example a home, a factory, a city, specific locations on or in the human body and so forth. However, the popularity of the smartphone as the main user device generates opportunities to exploit the information captured by smartphone sensors, even if these sensors have not been designed for the specific use case. However, this paradigm involves several challenges (detailed in Section 6.2).
In the smart factory, smartphones are not typically used to enrich the sensing capabilities of the environment, since dedicated systems focus on the parameters of interest while providing the robustness, reliability and deterministic behavior highly required in this context. On the other hand, smart homes may leverage presence of the smartphone (and the user) as an additional input to that offered by dedicated sensors deployed in the home.
In a smart manufacturing environment, analog and digital sensors are commonly used to monitor the status of Industry 4.0 automation applications, for predictive maintenance, or to diagnose production processes under the toughest operating conditions. That is why sensors must meet higher quality standards compared to sensors deployed in less harsh conditions such smart home environments. These sensors may need to be more resistant to dust, moisture, chemicals, vibrations, shocks or high temperatures in order to prevent them from failing or their performance from degradation.
6.1.2.CNN topology
In many smart environments, the CNN used follows a mesh network topology which is more complex than alternatives such as the star topology. In fact, a bespoke routing solution typically based on use of a dynamic routing protocol, is needed in this setting. Despite this requirement, the mesh topology is attractive because it offers two significant advantages. First, it allows overcoming the network range limitations of a star topology, especially when link range is reduced for example to just a few tens of meters. Secondly, it offers path diversity thus avoiding the single-point of failure issue of a star topology, which relies on the availability of a central device. This may help coping with link quality issues in wireless systems (e.g. due to multipath propagation, interference, etc.) or in noisy wired systems (e.g. PLC). Both smart homes and smart factories typically use mesh networks for wireless sensor systems. In smart cities, while IEEE 802.15.4 mesh networks have been deployed in some experiments, LPWAN technologies have recently gained high momentum. LPWAN technologies follow the star topology, and offer a high link range, therefore they allow city-wide coverage of devices such as sensors at a low infrastructure cost.
6.1.3.Technologies
Smart homes benefit from a larger variety of available technologies among all smart environments considered. Some of these technologies have been designed specifically for smart home scenarios (e.g. ITU-T G.9959) or leverage infrastructure typically available at a home (e.g. PLC and DECT-ULE). Nevertheless, general purpose technologies such as IEEE 802.15.4, Bluetooth LE or Wi-Fi are also commonly used in smart homes.
At the other end of the spectrum, CNN technologies used in smart factories are typically based on IEEE 802.15.4e TSCH, which appears to be dominant in this setting.
Smart cities employ both general-purpose CNN technologies (e.g. IEEE 802.15.4), technologies not specifically developed for CNNs (e.g. 4G or Wi-Fi), and moreover, have recently leveraged the emerging LPWAN technologies, such as LoRaWAN, Sigfox or NB-IoT.
Finally, smart health application scenarios benefit from the technologies used in the physical environment where smart health applications are carried out. Note that many smart health applications are home-centric, therefore leveraging smart home technologies. In other cases, smart health users exploit the connectivity means provided by the smartphone.
6.1.4.Computing approach
IoT applications require services and support for storing, managing and processing the data collected from devices such as sensors. There exist different trends in this regard, where Cloud computing and Fog computing appear to be the most relevant approaches. The former leverages remote platforms available via the Internet, whereas in the latter, processing and storage is carried out locally, near the IoT device. Fog computing is suitable when low latency is required, and/or as a scalable solution when the number of devices is very high.
In smart homes, Cloud computing is the main paradigm for collected data processing and storage, generally intended for smart home monitoring and non-critical control operations. In this type of applications, Cloud computing is suitable, since latency requirements are not strict. On the other hand, real-time interactions are also common in smart homes, often involving humans in the loop: for example, a user turns on a lightbulb by pressing a button on a remote control. In such case, direct interaction between the communicating devices is a good fit, and neither cloud nor Fog computing are strictly needed.
In smart cities, a combination of cloud and Fog computing provides a suitable approach. The latter allows low latency, while providing support for handling the data collected by the potentially high number of IoT devices in a city.
In smart factories, the production network connects a wide variety of sensors and actuators, for example, to monitor a variety of machine-health parameters, and to stream data via a gateway to business intelligence and administration systems within the smart factory – such as Enterprise Resource Planning (ERP) applications and Manufacturing Execution Systems (MES) – to manage the entire lifecycle of the product. To support these smart manufacturing application cases, data is frequently processed in real-time in a distributed manner on top of a fog (or real-time edge) computing analytics architecture for efficiency reasons. Indeed, with latency requirements in the range of milliseconds, timely data processing is key for industrial control and manufacturing applications. Rather than executing all data processing jobs in the cloud, by offloading to the fog layer i.e. closer to the production floor, a smart manufacturing company can minimize latency and operational expense. Cloud computing also has its place as well in Industry 4.0. The production network may provide connectivity and share data across the Internet to cloud services of other manufacturing enterprises and suppliers. The objective of this increased transparency is a seamless integration with supply chain and logistic networks and a more streamlined automated production environment.
6.2.Challenges
The following challenges for IoT solutions in smart environments are considered: interoperability and standardization, adaptation and personalization, and entity identification and virtualization.
6.2.1.Interoperability and standardization
The concept of IoT is strongly driven by the development of standards (either de facto or de jure) that address all layers from the physical to the application layer. Their majority have direct application in smart environments (see Section 4) and are still in continuous evolution. For example, in the context of smart factories, the networked production in Industry 4.0 requires interoperability between different machines. To address this concern, the OPC Unified Architecture (OPC UA) provides a secure, scalable and open platform for reliable machine-to-machine communication. OPC UA employs standard transport protocols and encodings to ensure connectivity between, for example, embedded controllers and high-end enterprise service environments [40]. It offers configuration capabilities for alarms and event notifications, and from a security perspective, it provides authentication capabilities for users, clients and servers to manage the integrity of their communication. Many industrial control and automation applications and production networks are typically time sensitive. To ensure a precise time distribution across manufacturing systems, many networks are adopting the IEEE Time Sensitive Networking (TSN) unified standard for this purpose [51]. In other contexts, such as smart homes, smart health or smart cities, the standardization process is often not as advanced as for the smart industry but still present and rich. However, while, on the one hand, the presence of standards certifies the maturity of the technology, on the other hand the large number of standards and the fact that they have often significant overlaps certifies that the area is lively and that the market is fast-developing and still looking for an equilibrium. From the point of view of the users, the richness of the offer in terms of solutions based on standards is certainly positive and it limits potential vendor locks-in, however, the fact that standards are often not easily interoperable may lead to standard locks-in. In a context of a fast-developing market in which standards may become easily obsolete, standards lock-in could be problematic and limiting for the further market development. For this reason, the interoperability of different IoT standards (for example by the definition of suitable gateways) may become, in perspective, a critical aspect.
6.2.2.Adaptation and personalization
A growing trend towards personalization, both in leisure and professional smart environments, triggers greater demands of transparency and interoperability. Sensor and actuator networks that operated well in isolation will face new connectivity and adaptation challenges for opening up IoT networks to different stakeholders, computing paradigms (mobile, fog, cloud), and technologies that will drive the personalization.
An important challenge is how to adapt the way the algorithms use the data processed to give the best possible experience to the user of the solution or to someone that will take information from the processing. In the previous Sections we showed that despite considerable effort being devoted to this problem several challenges remain to make sensors and actuators work together in ambient environments. Two features are important for new technologies to be accepted and used long-term: they have to provide useful and verified information and be relatively simple to install, understand and maintain.
In the examples that have been cited as applications above, smart environments (smart homes, smart city, smart manufactories) or smart health, these two points are crucial for the technology not to be abandoned. For well-being or health, devices are reputed to be abandoned quickly [23] as people are at the beginning motivated by the information that is brought, but this information is insufficient to motivate the use for a long time. For instance, if an activity tracking device is not able to detect the amount of activity that you do because the threshold defining it does not fit your use, it will have no use (for instance, an incorrect threshold for walk detection on the combination IMU/changes of heartrate in fitness applications). That is why such a device will “learn” in the first few days how the person behaves. Another example is for distress. The goal of several researches on that topic is for instance to build systems that will be able to monitor the activity of an elderly person at home to detect changes in his behavior and infer some possible health-related problems that should need warning the family or the medical staff or to detect distress situations such as fall. Analyzing the activity to detect changes of behavior (for instance in repartition of walk/stand/sit/lie down) needs having learnt the ones of the person in a first place, but also to be able to detect what is a change. For instance, for devices measuring heart rate and activity, does an episode of fever, that will increase the heart rate, have to be considered as relevant for the adaptation of the thresholds of detections of anomalies in the values? Incremental learning algorithms can allow to create models that will evolve with time, but an important question is when to adapt the model and when to warn? This very important question is the basis of all that kind of distress/health monitoring because we must not launch too much alarm, but we also must absolutely not miss an event.
The second important property is their relative simplicity to use, install and maintain a new technology. Installation and maintenance is primarily a technological and design problem. But for the easiness of use, the algorithms embedded will have a role to play. An important topic that we can discuss to ease user experience is the adaptation of the environment behavior to the user, so that it will not disturb his way of living. Some research projects are going through this problem (e.g. [48,49,76]), are on-going and are in their early stages. The idea is to use system traces and what are called implicit and explicit feedbacks from the user to adapt continuously the behavior of the system. These feedbacks are either a comment that the user does to the system saying that he does not like the action that has been done or are actions of the user that are in contradiction with the behavior of the system. Analyzing the way a person lives within the smart environment to detect such discrepancies in the data is still very costly but important for the experience of the user and the usability of the systems. If we want smart environments and ambient assisted living be more and more used and disseminated, these systems have to be simple and adapted to the person, not the contrary.
6.2.3.Entity identification and virtualization
IoT technologies bring together a variety of distinct elements and functionalities to construct integrated systems of increasing complexity consisting of numerous interacting complements. Entity identification is a core ingredient for managing this complexity and ensuring that assembly and commissioning of fully functional systems is successful as well as ensure trustworthy operating in the context of flexible and dynamic operations. In turn, this suggests the need for IoT universal identification as well as for supporting services to resolve entity codes and relate them to associated meta-data. Note that IoT entities may incorporate widely heterogenous types including physical objects, manufactured artefacts and devices, locations, humans and other living animals and plants, as well as the built environment and locations. Although attempts have been made to use communication identifiers for this purpose, there are many reasons that suggest that this is not a general solution including their typically limited scope with a specific communications context, multihoming and surrogacy relationships between entities and their communication interfaces as well as the well understood need for separation of entity identifier and IoT location attachment point.
Furthermore, entity identifiers offer a core ingredient for the development of effective ways to validate trust relationships between IoT entities and systems and control access to sensitive resources. Last but not least, entity identification is a core requirement towards object virtualization on the IoT which is considered a key development towards interoperability due its ability to track and synchronize across physical and digital resources.
7.Conclusions
Wireless networking is a core ingredient in a variety of IoT-enabled smart systems including homes, digital healthcare, smart factories and cities. Yet, choosing the right technology that best meets the requirements of a specific system can be a challenging task for the system architect due to the large diversity of options. In this paper, we have explored the advantages and limitations of different options with a view to provide guidance for the designer of smart systems in making an effective and efficient choice that best matches the goals of their work.
In conducting this survey, we recognise that low power wireless networking is in a state of flux as a consequence of the rapid development of innovative IoT solutions, which stretch the limits of current technologies. To this end, in this paper we have also explored areas of current and future development that investigate ways in which current technological limitations can be addressed. In particular, we have identified key research questions relating to interoperability and standardisation, adaptation and personalisation and entity virtualization that are expected to extend the functionality of current smart environments.
As a final reflection, we position our work against the other contributions in this thematic issue. We note that the exchange of data allowed by IoT technologies and systems is a starting point for creating smart environments powered by artificial and ambient intelligence [33]. The process of building smart environments may also leverage the inputs from other systems, such as computer vision ones [73]. This whole process requires considering the human aspect, since the human is in fact, either directly or indirectly, the main subject of smart environments [20]. However, designing smart environments involves grand societal challenges, from both technical and social points of view, that will require the efforts of the community in upcoming years [87].
Acknowledgements
Carles Gomez was funded in part by the European Regional Development Fund (ERDF) and the Spanish Government through project TEC2016-79988-P, AEI/FEDER, UE. Davy Preuveneers was supported by the H2020 project EXCELL (http://excell-project.eu/). This project has received funding from the European Union’s Horizon 2020 research and innovation programme under grant no. 691829.
References
[1] | S. Aguilar, R. Vidal and C. Gomez, Opportunistic sensor data collection with bluetooth low energy, Sensors 17: (1) ((2017) ), 159. doi:10.3390/s17010159. |
[2] | A. Akl, B. Chikhaoui, N. Mattek, J. Kaye, D. Austin and A. Mihailidis, Clustering home activity distributions for automatic detection of mild cognitive impairment in older adults 1, Journal of Ambient Intelligence and Smart Environments 8: (4) ((2016) ), 437–451. doi:10.3233/AIS-160385. |
[3] | A. Al-Fuqaha, M. Guizani, M. Mohammadi, M. Aledhari and M. Ayyash, Internet of Things: A survey on enabling technologies, protocols, and applications, IEEE Communications Surveys & Tutorials 17: (4) ((2015) ), 2347–2376. doi:10.1109/COMST.2015.2444095. |
[4] | G. Amato, D. Bacciu, M. Broxvall, S. Chessa, S. Coleman, M. Di Rocco, M. Dragone, C. Gallicchio, C. Gennaro, H. Lozano, H. McGinnity, A. Micheli, A.K. Ray, A. Renteria, A. Saffiotti, D. Swords, C. Vairo and P. Vance, Robotic ubiquitous cognitive ecology for smart homes, Journal of Intelligent & Robotic Systems 80: (1) ((2015) ), 57–81. doi:10.1007/s10846-015-0178-2. |
[5] | A.A. Aziz, M.C. Klein and J. Treur, An integrative ambient agent model for unipolar depression relapse prevention, Journal of Ambient Intelligence and Smart Environments 2: (1) ((2010) ), 5–20. |
[6] | D. Bacciu, S. Chessa, C. Gallicchio and A. Micheli, On the need of machine learning as a service for the Internet of Things, in: ACM International Conference Proceedings Series, ACM, (2017) . |
[7] | G. Baldewijns, V. Claes, G. Debard, M. Mertens, E. Devriendt, K. Milisen, J. Tournoy, T. Croonenborghs and B. Vanrumste, Automated in-home gait transfer time analysis using video cameras, Journal of Ambient Intelligence and Smart Environments 8: (3) ((2016) ), 273–286. doi:10.3233/AIS-160379. |
[8] | V. Baños-Gonzalez, M.S. Afaqui, E. Lopez-Aguilera and E. Garcia-Villegas, IEEE 802.11 ah: A technology to face the IoT challenge, Sensors 16: (11) ((2016) ), 1960. |
[9] | P. Baronti, P. Pillai, V.W. Chook, S. Chessa, A. Gotta and Y.F. Hu, Wireless sensor networks: A survey on the state of the art and the 802.15. 4 and ZigBee standards, Computer Communications 30: (7) ((2007) ), 1655–1695. doi:10.1016/j.comcom.2006.12.020. |
[10] | P. Bellavista, S. Chessa, L. Foschini, L. Gioia and M. Girolami, Human-enabled edge computing: Exploiting the crowd as a dynamic extension of mobile edge computing, IEEE Communications Magazine 56: (1) ((2018) ), 145–155. doi:10.1109/MCOM.2017.1700385. |
[11] | S. Bernardino, J. Freitas Santos and J. Cadima Ribeiro, The legacy of European capitals of culture to the “smartness” of cities: The case of Guimarães 2012, in: Journal of Convention & Event Tourism, Vol. 19: , Taylor & Francis, (2018) , pp. 138–166. |
[12] | G. Bleser, D. Steffen, M. Weber, G. Hendeby, D. Stricker, L. Fradet, F. Marin, N. Ville and F. Carré, A personalized exercise trainer for the elderly, Journal of Ambient Intelligence and Smart Environments 5: (6) ((2013) ), 547–562. |
[13] | C. Bormann, A.P. Castellani and Z. Shelby, CoAP: An application protocol for billions of tiny Internet nodes, IEEE Internet Computing 16: (2) ((2012) ), 62–67. doi:10.1109/MIC.2012.29. |
[14] | C. Bormann, M. Ersue, A. Keranen and C. Gomez, Terminology for Constrained-Node Networks. RFC 7228, Internet Draft (Work in Progress), Draft Name: draft-bormann-lwig-7228-bis-02. Retrieved from http://www.rfc-editor.org/info/rfc7228, 2017. |
[15] | V. Callaghan and H. Hagras, Preface, Thematic issue: Smart homes, Journal of Ambient Intelligence and Smart Environments 2: (1) ((2010) ), 207–209. doi:10.3233/AIS-2010-0078. |
[16] | G. Cardone, A. Cirri, A. Corradi and L. Foschini, The participact mobile crowd sensing living lab: The testbed for smart cities, IEEE Communications Magazine 52: (10) ((2014) ), 78–85. doi:10.1109/MCOM.2014.6917406. |
[17] | F. Castro-Jul, R.P. Díaz-Redondo and A. Fernández-Vilas, Collaboratively assessing urban alerts in ad hoc participatory sensing, Computer Networks 131: ((2018) ), 129–143. doi:10.1016/j.comnet.2017.12.008. |
[18] | A. Cesta, G. Cortellessa, F. Fracasso, A. Orlandini and M. Turno, User needs and preferences on AAL systems that support older adults and their carers, Journal of Ambient Intelligence and Smart Environments 10: (1) ((2018) ), 49–70. doi:10.3233/AIS-170471. |
[19] | P. Chahuara, A. Fleury, F. Portet and M. Vacher, On-line human activity recognition from audio and home automation sensors: Comparison of sequential and non-sequential models in realistic smart homes 1, Journal of Ambient Intelligence and Smart Environments 8: (4) ((2016) ), 399–422. doi:10.3233/AIS-160386. |
[20] | J. Chin, V. Callaghan and S. Ben Allouch, The Internet of Things: Reflections on the past, present and future from a user centered and smart environments perspective, Journal of Ambient Intelligence and Smart Environments 11: (1) ((2019) ). |
[21] | S.-L. Chua, S. Marsland and H. Guesgen, A supervised learning approach for behaviour recognition in smart homes, Journal of Ambient Intelligence and Smart Environments 8: (3) ((2016) ), 259–271. doi:10.3233/AIS-160378. |
[22] | T. Clausen, U. Herberg and M. Philipp, A critical evaluation of the IPv6 routing protocol for low power and lossy networks (RPL), in: Wireless and Mobile Computing, Networking and Communications (WiMob), 2011 IEEE 7th International Conference on, IEEE, (2011) , pp. 365–372. |
[23] | J. Clawson, J.A. Pater, A.D. Miller, E.D. Mynatt and L. Mamykina, No longer wearing: Investigating the abandonment of personal health-tracking technologies on craigslist, in: Proceedings of the 2015 ACM International Joint Conference on Pervasive and Ubiquitous Computing, ACM, (2015) , pp. 647–658. |
[24] | D.J. Cook and S.K. Das, How smart are our environments? An updated look at the state of the art, Pervasive and Mobile Computing 3: (2) ((2007) ), 53–73. doi:10.1016/j.pmcj.2006.12.001. |
[25] | D.J. Cook, G. Duncan, G. Sprint and R.L. Fritz, Using smart city technology to make healthcare smarter, Proceedings of the IEEE 106: (4) ((2018) ), 708–722. doi:10.1109/JPROC.2017.2787688. |
[26] | G. Debard, M. Mertens, M. Deschodt, E. Vlaeyen, E. Devriendt, E. Dejaeger, K. Milisen, J. Tournoy, T. Croonenborghs, T. Goedemé, T. Tuytelaars and B. Vanrumste, Camera-based fall detection using real-world versus simulated data: How far are we from the solution?, Journal of Ambient Intelligence and Smart Environments 8: (2) ((2016) ), 149–168. doi:10.3233/AIS-160369. |
[27] | A. Dubois and F. Charpillet, Measuring frailty and detecting falls for elderly home care using depth camera, Journal of Ambient Intelligence and Smart Environments 9: (4) ((2017) ), 469–481. doi:10.3233/AIS-170444. |
[28] | G. Fagerberg, A. Kung, R. Wichert, M.-R. Tazari, B. Jean-Bart, G. Bauer, G. Zimmermann, F. Furfari, F. Potortì, S. Chessa, M. Hellenschmidt, J. Gorman, J. Alexandersson, J. Bund, E. Carrasco, G. Epelde, M. Klima, E. Urdarneta, G. Vanderheiden and I. Zinnikus, Platforms for AAL applications, in: European Conference on Smart Sensing and Context, Springer, (2010) , pp. 177–201. doi:10.1007/978-3-642-16982-3_14. |
[29] | S. Farrell, LPWAN Overview. Internet Draft (Work in Progress), Draft Name: Draft-ietf-lpwan-overview-10, 2018. |
[30] | E. Ferro and F. Potorti, Bluetooth and Wi-Fi wireless protocols: A survey and a comparison, IEEE Wireless Communications 12: (1) ((2005) ), 12–26. doi:10.1109/MWC.2005.1404569. |
[31] | A. Fleury, Q. Mourcou, C. Franco, B. Diot, J. Demongeot and N. Vuillerme, Evaluation of a smartphone-based audio-biofeedback system for improving balance in older adults – A pilot study, in: Engineering in Medicine and Biology Society (EMBC), 2013 35th Annual International Conference of the IEEE, IEEE, (2013) , pp. 1198–1201. |
[32] | F. Furfari, M. Girolami, S. Lenzi and S. Chessa, A service-oriented zigbee gateway for smart environments, Journal of Ambient Intelligence and Smart Environments 6: (6) ((2014) ), 691–705. |
[33] | M. Gams, I. Yu-Hua Gu, A. Härmä, A. Muñoz and V. Tam, Artificial intelligence and ambient intelligence, Journal of Ambient Intelligence and Smart Environments 11: (1) ((2019) ). |
[34] | A. Gilchrist, Industry 4.0: The Industrial Internet of Things, Springer, (2016) . |
[35] | K. Gill, S.-H. Yang, F. Yao and X. Lu, A zigbee-based home automation system, IEEE Transactions on Consumer Electronics 55: (2) ((2009) ). |
[36] | H. Gjoreski, M. Gams and M. Luštrek, Context-based fall detection and activity recognition using inertial and location sensors, Journal of Ambient Intelligence and Smart Environments 6: (4) ((2014) ), 419–433. |
[37] | C. Gomez, J. Oller and J. Paradells, Overview and evaluation of bluetooth low energy: An emerging low-power wireless technology, Sensors 12: (9) ((2012) ), 11734–11753. doi:10.3390/s120911734. |
[38] | C. Gomez and J. Paradells, Wireless home automation networks: A survey of architectures and technologies, IEEE Communications Magazine 48: (6) ((2010) ). |
[39] | C. Gomez, J. Paradells, C. Bormann and J. Crowcroft, From 6LoWPAN to 6Lo: Expanding the universe of IPv6-supported technologies for the Internet of Things, IEEE Communications Magazine 55: (12) ((2017) ), 148–155. doi:10.1109/MCOM.2017.1600534. |
[40] | R. Henssen and M. Schleipen, Interoperability between OPC UA and AutomationML, Procedia CIRP 25: ((2014) ), 297–304. doi:10.1016/j.procir.2014.10.042. |
[41] | Y.G. Hong, Y.H. Choi, J.S. Youn, D.K. Kim and J.H. Choi, Transmission of IPv6 packets over near field communication. Internet Draft (Work in Progress), Draft Name: Draft-ietf-6lo-nfc-09, 2015. |
[42] | J. Hou, X. Tang and Y.-G. Hong, Transmission of IPv6 Packets over PLC Networks. Internet Draft (Work in Progress), Draft Name: draft-hou-6lo-plc-03, 2018. |
[43] | X. Hu, T.H. Chu, H.C. Chan and V.C. Leung, Vita: A crowdsensing-oriented mobile cyber-physical system, IEEE Transactions on Emerging Topics in Computing 1: (1) ((2013) ), 148–165. doi:10.1109/TETC.2013.2273359. |
[44] | R. Igual, I. Plaza, C. Medrano and M.A. Rubio, Personalizable smartphone-based system adapted to assist dependent people, Journal of Ambient Intelligence and Smart Environments 6: (6) ((2014) ), 569–593. |
[45] | S.R. Islam, D. Kwak, M.H. Kabir, M. Hossain and K.-S. Kwak, The Internet of Things for health care: A comprehensive survey, IEEE Access 3: ((2015) ), 678–708. doi:10.1109/ACCESS.2015.2437951. |
[46] | E. Jean-Baptiste, M. Russell, J. Howe and P. Rotshtein, Intelligent prompting system to assist stroke survivors, Journal of Ambient Intelligence and Smart Environments 9: (6) ((2017) ), 707–723. doi:10.3233/AIS-170461. |
[47] | Ö. Kafalı, S. Bromuri, M. Sindlar, T. van der Weide, E. Aguilar Pelaez, U. Schaechtle, B. Alves, D. Zufferey, E. Rodriguez-Villegas, M.I. Schumacher and K. Stathis, Commodity 12: A smart e-health environment for diabetes management, Journal of Ambient Intelligence and Smart Environments 5: (5) ((2013) ), 479–502. |
[48] | A.-B. Karami and A. Fleury, Using feedback in adaptive and user-dependent one-step decision making, in: 25th International Joint Conference on Artificial Intelligence (IJCAI-16) Workshop “Interactive Machine Learning”, AAAI Press/International Joint Conferences on Artificial Intelligence, (2016) , p. 5. |
[49] | A.B. Karami, A. Fleury, J. Boonaert and S. Lecoeuche, User in the loop: Adaptive smart homes exploiting user feedback – state of the art and future directions, Information 7: (2) ((2016) ), 35. doi:10.3390/info7020035. |
[50] | S. Karnouskos, A.W. Colombo, T. Bangemann, K. Manninen, R. Camp, M. Tilly, P. Stluka, F. Jammes, J. Delsing and J. Eliasson, A SOA-based architecture for empowering future collaborative cloud-based industrial automation, in: IECON 2012 – 38th Annual Conference on IEEE Industrial Electronics Society, IEEE, (2012) , pp. 5766–5772. |
[51] | S. Kehrer, O. Kleineberg and D. Heffernan, A comparison of fault-tolerance concepts for IEEE 802.1 Time Sensitive Networks (TSN), in: Emerging Technology and Factory Automation (ETFA), 2014, IEEE, (2014) , pp. 1–8. |
[52] | H. Kerdegari, S. Mokaram, K. Samsudin and A.R. Ramli, A pervasive neural network based fall detection system on smart phone, Journal of Ambient Intelligence and Smart Environments 7: (2) ((2015) ), 221–230. |
[53] | S.S. Khan and J. Hoey, Review of fall detection techniques: A data availability perspective, Medical Engineering and Physics 39: ((2017) ), 12–22. doi:10.1016/j.medengphy.2016.10.014. |
[54] | M. Krivỳ, Towards a critique of cybernetic urbanism: The smart city and the society of control, Planning Theory ((2016) ). doi:10.1177/1473095216645631. |
[55] | C. Kürschner, C. Condea, O. Kasten and F. Thiesse, Discovery service design in the epcglobal network, in: The Internet of Things, Springer, (2008) , pp. 19–34. doi:10.1007/978-3-540-78731-0_2. |
[56] | M. Kurz, G. Holzl, A. Ferscha, A. Calatroni, D. Roggen, G. Troster, H. Sagha, R. Chavarriaga, J. del R. Millan, D. Bannach, K. Kunze and P. Lukowicz, The opportunity framework and data processing ecosystem for opportunistic activity and context recognition, International Journal of Sensors Wireless Communications and Control 1: (2) ((2011) ), 102–125. doi:10.2174/2210327911101020102. |
[57] | J.K. Laurila, D. Gatica-Perez, I. Aad, O. Bornet, T.-M.-T. Do, O. Dousse, J. Eberle and M. Miettinen, The mobile data challenge: Big data for mobile computing research, in: Pervasive Computing. |
[58] | J. Lee, B. Bagheri and H.-A. Kao, A cyber-physical systems architecture for industry 4.0-based manufacturing systems, Manufacturing Letters 3: ((2015) ), 18–23. doi:10.1016/j.mfglet.2014.12.001. |
[59] | J. Lee, B.A. Reyes, D.D. McManus, O. Maitas and K.H. Chon, Atrial fibrillation detection using an iPhone 4S, IEEE Transactions on Biomedical Engineering 60: (1) ((2013) ), 203–206. doi:10.1109/TBME.2012.2208112. |
[60] | L. Liu, M. Popescu, M. Skubic, M. Rantz and P. Cuddihy, An automatic in-home fall detection system using Doppler radar signatures, Journal of Ambient Intelligence and Smart Environments 8: (4) ((2016) ), 453–466. doi:10.3233/AIS-160388. |
[61] | Z. Lv, X. Li, W. Wang, B. Zhang, J. Hu and S. Feng, Government affairs service platform for smart city, Future Generation Computer Systems 81: ((2018) ), 443–451. doi:10.1016/j.future.2017.08.047. |
[62] | J. Martocci, K. Lynn, C. Neilson and S. Donaldson, Transmission of IPv6 over Master-Slave/Token-Passing (MS/TP) Networks. RFC 8163, 2017. |
[63] | M. Masera, E.F. Bompard, F. Profumo and N. Hadjsaid, Smart (electricity) grids for smart cities: Assessing roles and societal impacts, Proceedings of the IEEE 106: (4) ((2018) ), 613–625. doi:10.1109/JPROC.2018.2812212. |
[64] | A. Minaburo, L. Toutain and C. Gomez, LPWAN Static Context Header Compression (SCHC) and fragmentation for IPv6 and UDP. Internet Engineering Task Force, Internet Draft, Draft Name: draft-ietf-lpwan-ipv6-static-context-hc-10, 2017. |
[65] | A. Monacchi, F. Versolatto, M. Herold, D. Egarter, A.M. Tonello and W. Elmenreich, An open solution to provide personalized feedback for building energy management, Journal of Ambient Intelligence and Smart Environments 9: (2) ((2017) ), 147–162. doi:10.3233/AIS-170422. |
[66] | L. Monostori, B. Kádár, T. Bauernhansl, S. Kondoh, S. Kumara, G. Reinhart, O. Sauer, G. Schuh, W. Sihn and K. Ueda, Cyber-physical systems in manufacturing, CIRP Annals 65: (2) ((2016) ), 621–641. doi:10.1016/j.cirp.2016.06.005. |
[67] | N. Noury, A. Fleury, P. Rumeau, A.K. Bourke, G.O. Laighin, V. Rialle and J.E. Lundy, Fall detection-principles and methods, in: Engineering in Medicine and Biology Society, 2007. EMBS 2007. 29th Annual International Conference of the IEEE, IEEE, (2007) , pp. 1663–1666. |
[68] | J. O’Donoghue, R. Wichert and M. Divitini, Thematic issue: Home-based Health and Wellness Measurement and Monitoring (Vol. 4). Journal of Ambient Intelligence and Smart Environments 2012. |
[69] | P. O’Donovan, K. Leahy, K. Bruton and D.T. O’Sullivan, Big data in manufacturing: A systematic mapping study, Journal of Big Data 2: (1) ((2015) ), 20. doi:10.1186/s40537-015-0028-x. |
[70] | N. Pavón-Pulido, J.A. López-Riquelme, J. Ferruz-Melero, M.Á. Vega-Rodríguez and A.J. Barrios-León, A service robot for monitoring elderly people in the context of ambient assisted living, Journal of Ambient Intelligence and Smart Environments 6: (6) ((2014) ), 595–621. |
[71] | R.A. Perez, J.T. Lilkendey and S.W. Koh, Machine learning for a dynamic manufacturing environment, ACM SIGICE Bulletin 19: (3) ((1994) ), 5–9. doi:10.1145/182063.182067. |
[72] | B. Pogorelc and M. Gams, Home-based health monitoring of the elderly through gait recognition, Journal of Ambient Intelligence and Smart Environments 4: (5) ((2012) ), 415–428. |
[73] | A. Prati, C. Shan and K. Wang, Sensors, vision and networks: From video surveillance to activity recognition and health monitoring, Journal of Ambient Intelligence and Smart Environments 11: (1) ((2019) ). |
[74] | D. Preuveneers and E. Ilie-Zudor, The intelligent industry of the future: A survey on emerging trends, research challenges and opportunities in Industry 4.0, Journal of Ambient Intelligence and Smart Environments 9: (3) ((2017) ), 287–298. doi:10.3233/AIS-170432. |
[75] | P. Priore, D. de la Fuente, J. Puente and J. Parreño, A comparison of machine-learning algorithms for dynamic scheduling of flexible manufacturing systems, Engineering Applications of Artificial Intelligence 19: (3) ((2006) ), 247–255. doi:10.1016/j.engappai.2005.09.009. |
[76] | P. Rashidi and D.J. Cook, Keeping the resident in the loop: Adapting the smart home to the user, IEEE Transactions on Systems, Man, and Cybernetics – Part A: Systems and Humans 39: (5) ((2009) ), 949–959. doi:10.1109/TSMCA.2009.2025137. |
[77] | B. Reiterer, C. Concolato, J. Lachner, J. Le Feuvre, J.-C. Moissinac, S. Lenzi, S. Chessa, E.F. Ferrá, J.J.G. Menaya and H. Hellwagner, User-centric universal multimedia access in home networks, The Visual Computer 24: (7–9) ((2008) ), 837–845. doi:10.1007/s00371-008-0265-5. |
[78] | L. Rosales, B.Y. Su, M. Skubic and K.C. Ho, Heart rate monitoring using hydraulic bed sensor ballistocardiogram, Journal of Ambient Intelligence and Smart Environments 9: (2) ((2017) ), 193–207. doi:10.3233/AIS-170423. |
[79] | G. Roussos, Networked RFID: Systems, Software and Services, Springer Science & Business Media, (2008) . |
[80] | G. Roussos and P. Chartier, Scalable id/locator resolution for the iot, in: Internet of Things (iThings/CPSCom), 2011 International Conference on and 4th International Conference on Cyber, Physical and Social Computing, IEEE, (2011) , pp. 58–66. |
[81] | S. Sarma, D. Brock and D. Engels, Radio frequency identification and the electronic product code, IEEE Micro 21: (6) ((2001) ), 50–54. doi:10.1109/40.977758. |
[82] | Z. Shelby and C. Bormann, 6LoWPAN: The Wireless Embedded Internet, Vol. 43: , John Wiley & Sons, (2011) . |
[83] | Z. Shelby, K. Hartke and C. Bormann, The constrained application protocol (CoAP). RFC 7252, 2014. |
[84] | B.N. Silva, M. Khan and K. Han, Towards sustainable smart cities: A review of trends, architectures, components, and open challenges in smart cities, Sustainable Cities and Society 38: ((2018) ), 697–713. doi:10.1016/j.scs.2018.01.053. |
[85] | E.-E. Steen, T. Frenken, M. Eichelberg, M. Frenken and A. Hein, Modeling individual healthy behavior using home automation sensor data: Results from a field trial, Journal of Ambient Intelligence and Smart Environments 5: (5) ((2013) ), 503–523. |
[86] | N. Streitz, Beyond ‘smart-only’ cities: Redefining the ‘smart-everything’ paradigm, Journal of Ambient Intelligence and Humanized Computing. ((2018) ). doi:10.1007/s12652-018-0824-1. |
[87] | N. Streitz, D. Charitos, M. Kaptein and M. Böhlen, Grand challenges for ambient intelligence and implications for design contexts and smart societies, Journal of Ambient Intelligence and Smart Environments 11: (1) ((2019) ). |
[88] | A.K. Tripathy, P.K. Tripathy, N.K. Ray and S.P. Mohanty, iTour: The future of smart tourism: An IoT framework for the independent mobility of tourists in smart cities, IEEE Consumer Electronics Magazine 7: (3) ((2018) ), 32–37. doi:10.1109/MCE.2018.2797758. |
[89] | R. Velik, A brain-inspired multimodal data mining approach for human activity recognition in elderly homes, Journal of Ambient Intelligence and Smart Environments 6: (4) ((2014) ), 447–468. |
[90] | P.K. Verma, R. Verma, A. Prakash, A. Agrawal, K. Naik, R. Tripathi, M. Alsabaan, T. Khalifa, T. Abdelkader and A. Abogharaf, Machine-to-machine (M2M) communications: A survey, Journal of Network and Computer Applications 66: ((2016) ), 83–105. doi:10.1016/j.jnca.2016.02.016. |
[91] | L. Walsh and S. McLoone, Non-contact under-mattress sleep monitoring, Journal of Ambient Intelligence and Smart Environments 6: (4) ((2014) ), 385–401. |
[92] | Y.-P.E. Wang, X. Lin, A. Adhikary, A. Grovlen, Y. Sui, Y. Blankenship, J. Bergman and H.S. Razaghi, A primer on 3GPP narrowband Internet of Things, IEEE Communications Magazine 55: (3) ((2017) ), 117–123. doi:10.1109/MCOM.2017.1600510CM. |
[93] | T. Watteyne, M. Palattella and L. Grieco, Using IEEE 802.15. 4e time-slotted channel hopping (TSCH) in the Internet of Things (IoT): Problem statement. RFC 7554, 2015. |
[94] | T. Winter, RFC 6550, 2012. |
[95] | A. Zanella, N. Bui, A. Castellani, L. Vangelista and M. Zorzi, Internet of Things for smart cities, IEEE Internet of Things Journal 1: (1) ((2014) ), 22–32. doi:10.1109/JIOT.2014.2306328. |
[96] | J. Zawieska and J. Pieriegud, Smart city as a tool for sustainable mobility and transport decarbonisation, Transport Policy 63: ((2018) ), 39–50. doi:10.1016/j.tranpol.2017.11.004. |




