Collaborating to implement SeamlessAccess: A library’s perspective
Abstract
In the past two years an ever-increasing number of publishers have implemented SeamlessAccess resulting in a better user experience and increased usage. However, to ensure more users benefit from federated authentication and seamless access more collaborations among publishers, libraries, and SeamlessAccess are needed. This brief paper will include a library perspective on the challenges to implementing federated access, the benefits that federated access brings to libraries and to their end-users in their research experience, and a brief walk-through of the SeamlessAccess experience that demonstrates how it enhances federated access.
1.Challenges to implementing federated access
One challenge that libraries face when implementing federated access [1] is that many librarians do not want to adopt this change because of their familiarity with proxy-based access. Although not exclusive to federated access, it is not unusual to find that a significant portion of a librarian technologist’s work is in change management as a result of trying to calm perceptions and fears regarding how a new technology or platform implementation will change existing workflows and procedures [2].
Specific to federated access, most librarians that are still using IP-based access [3] (typically through EZproxy [4] think that they do not have the personnel, expertise, or money to undertake moving to federated access. Most libraries are in a state of contraction post-COVID in spaces, resources, and personnel, and there were significant reductions in force during COVID of personnel who will not be rehired. Early retirements were also incentivized and overall, our library ranks are thinning [5].
Another challenge is the perception among librarians that very few libraries outside of those at R1 institutions have the in-house expertise and technical expertise necessary to manage a migration to federated access. This is no longer the case since EBSCO began partnering with OpenAthens [6] to make the implementation process for OpenAthens consistently easier and faster. The migration time has greatly decreased from many months to as few as three months, which was the case at Coastal Carolina University.
From a financial perspective, EZproxy was famously a one-time purchase of $325 for many years until OCLC purchased it from Chris Zagar. Even with consistent increases it is still priced at approximately $700–$800 for a locally-installed instance. On the other hand, OpenAthens typically costs several thousands of dollars annually depending on an institution’s full-time enrollment number.
To complicate matters, librarians frequently have poor or even non-existent relationships with their campus or organizational Information Technology (IT) department. As opposed to partners in the organization, librarians are many times seen as just another department that IT has to support. Not only does this serve as an impediment to the library for implementing new technologies but creates missed opportunities for communication and collaboration. It is vitally important for the library to have a good working relationship with their campus IT department so that they can serve as advocates for user privacy and the library user experience as well as for the overall needs of the library.
2.Benefits of federated access
Federated identity and access management utilizes a more reliable, robust, SAML [7]-based infrastructure that helps put libraries in control of privacy because the institution decides what, if any, user data (attributes) are shared with a vendor. Also, when compared to EZproxy, ongoing maintenance of this environment is much simpler since the specific information necessary to establish a trusted connection lives in a federation accessed by identity provider and service provider alike.
Federated access also provides support for researchers who might be affiliated with numerous institutions or research organizations, and has proven to improve the campus response to security incidents which limits the site-wide disruption caused from abuse by individuals. This is a result of it being much easier to ascertain a specific compromised user account, whereas with IP filtering the vendor many times shuts down access to the entire IP range until the specific compromised user account can be identified.
Lastly, and especially important to librarians, federated access also offers a far better user experience that provides authentication at the point of need. IP authentication is very counterintuitive to the current user experience because it forces researchers to start from, or at some point return to, the institutional portal before they can access the online content to which they are entitled. This is directly contradictory to the way discovery works; it degrades the overall user experience and needlessly complicates access to scholarly resources.
To briefly expound on the concept of authentication at the point of need, recent findings from Coastal Carolina University’s (CCU) migration from EZproxy to OpenAthens last August are telling. All resource links were re-encoded in CCU’s A-Z lists and discovery platform and went live with OpenAthens on August 16, 2021. However, the cloud-based infrastructure was in place and functional on July 22, 2021 and the OpenAthens usage dashboard began recording inbound traffic and successfully authenticated sessions on July 22. Overall, there were 1512 successfully authenticated sessions in the time period between July 22 and August 16, and Fig. 1 shows as many as 137 sessions in a day.
Fig. 1.
OpenAthens pre-launch usage.
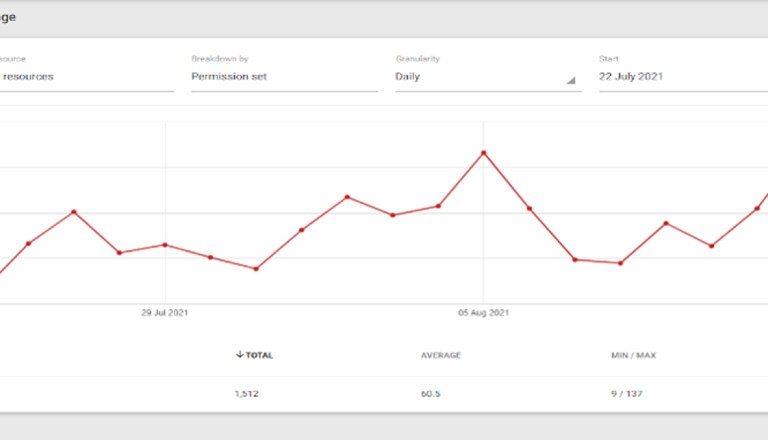
Since all outbound links from the library’s portal were still using EZproxy, there was at first confusion regarding how this was occurring. It was finally determined that users were accessing resources via the Wayfinder service on each vendor’s platform after having started their journey from the open web, typically from Google Scholar. Researchers were able to intuitively log in with no help or intervention from library staff and no reports of access issues were received during this time.
3.User experience
Because the overall user authentication experience is currently inconsistent, confusing, and replete with jargon, SeamlessAccess seeks to implement a standard for digital authentication based on a single sign on through the user’s home institution. Regardless of where the end user begins their research they will encounter consistent imagery, language, and login placement, along with a standardized Identity Provider Discovery flow. Once authenticated using their preferred sign in credentials, the end user will not be required to sign in again across all SeamlessAccess-enabled sites.
Federated access with the SeamlessAccess service enabled offers a far better user experience than IP authentication because it provides authentication at the point of need. In this use case scenario, the user begins their research on the open web and has located a journal article that resides on the ACS platform. The blue SeamlessAccess button shown in Fig. 2 labeled with Access Through Your Institution is a consistent call to action for the user.
Fig. 2.
SeamlessAccess button.
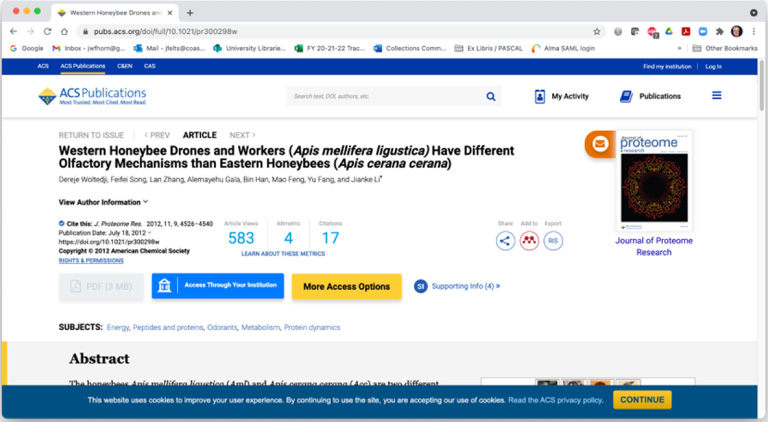
After clicking the access button, the user is directed to the SeamlessAccess directory service which allows the user to select the institution to which they would like to be affiliated (Fig. 3).
Fig. 3.
SeamlessAccess directory service.
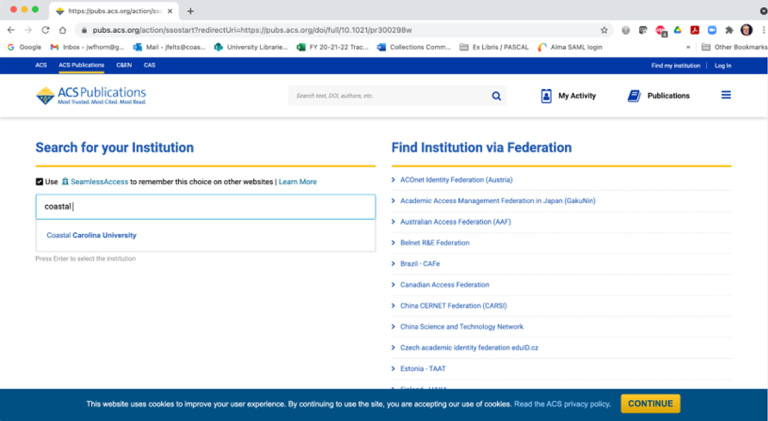
Figure 4 indicates that the user has successfully authenticated and the affiliation they selected has been applied (Fig. 5).
Fig. 4.
Authentication and affiliation.
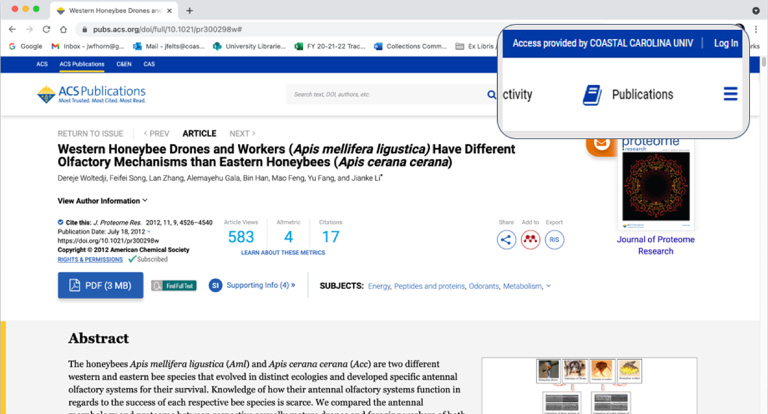
When leaving a vendor’s website to view information behind a paywall on a different vendor’s site, there is no longer the need to go through the cumbersome authentication process yet again since the SeamlessAccess persistence service has stored this information in the user’s local browser storage. Figure 6 shows that the user simply clicks on the SeamlessAccess button, which transparently sends them through their local authentication to verify that they are allowed access to this resource before redirecting them to vendor’s platform.
Fig. 5.
SeamlessAccess persistence service (from ACS to ScienceDirect).
Fig. 6.
SeamlessAccess persistence service (from ScienceDirect to Nature).
The user experience is consistent anywhere that the SeamlessAccess service has been enabled. For more information regarding how Federated Authentication works visit the SeamlessAccess Learning Center for an overview intended for a non-technical audience [8].
About the author
John W. Felts is currently the Head of Information Technology and Collections at Coastal Carolina University in Conway, SC, U.S.A. He has worked in academic library technology for over thirty years and is a former patent holder and co-founder of Journal Finder, the first OpenURL Resolver and knowledge base to go into production in the United States.
He is a member of the SeamlessAccess Outreach Committee and the Scholarly Network Security Initiative (SNSI) University Relations Group. E-mail: [email protected].
References
[1] | See: https://scholarlykitchen.sspnet.org/2020/09/29/guest-post-why-federated-access-matters-one-librarys-pandemic-story, accessed September 19, 2023. |
[2] | O. Adebayo, M. Opeoluwa Fagbohun, U. Chinyere Esse and N.M. Nwokeoma, , Change management in the academic library: transition from print to digital collections, [cited 2023 April 11]. Available from: https://www.igi-global.com/gateway/chapter/188021, accessed September 19, 2023. |
[3] | See: https://ask.springshare.com/libguides/faq/1066, accessed September 19, 2023. |
[4] | See: https://en.wikipedia.org/wiki/EXproxy, accessed September 19, 2023. |
[5] | NISO. SeamlessAccess learning center, [cited 2023 April 13]. Available from: https://seamlessaccess.org/learning-center/, accessed September 19, 2023. |
[6] | See: https://openathens.net, accessed September 19, 2023. |
[7] | See: https://www.cloudflare.com/learning/access-management/what-is-saml/, accessed September 19, 2023. |
[8] | NISO. SeamlessAccess learning center, [cited 2023 April 13]. Available from: https://seamlessaccess.org/learning-center/, accessed September 19, 2023. |




