Privacy-preserving policy evaluation in multi-party access control
Abstract
Recent years have seen an increasing popularity of online collaborative systems like social networks and web-based collaboration platforms. Collaborative systems typically offer their users a digital environment in which they can work together and share resources and information. These resources and information might be sensitive and, thus, they should be protected from unauthorized accesses. Multi-party access control is emerging as a new paradigm for the protection of co-owned and co-managed resources, where the policies of all users involved in the management of a resource should be accounted for collaborative decision making. Existing approaches, however, only focus on the jointly protection of resources and do not address the protection of the individual user policies themselves, whose disclosure might leak sensitive information. In this work, we propose a privacy-preserving mechanism for the evaluation of multi-party access control policies, which preserves the confidentiality of user policies while remaining capable of making collaborative decisions. To this end, we design secure computation protocols for the evaluation of policies in protected form against an access query and realize such protocols using two privacy-preserving techniques, namely Homomorphic Encryption and Secure Functional Evaluation. We show the practical feasibility of our mechanism in terms of computation and communication costs through an experimental evaluation.
1.Introduction
The widespread availability of the Internet has led to a significant growth in the use of online collaborative systems and platforms. Such systems generally offer their users the means for digital interactions and for the jointly creation and management of co-owned resources. These resources, however, can be sensitive and, thus, they should be protected from unauthorized usages by considering the access requirements of all co-owners. Multi-party access control is emerging with the aim of enabling collaborative governance of co-owned resources [45], thus overcoming the limitations of traditional access control models, which are based on the assumption that resources are governed by a single entity. Several approaches to multi-party access control have been proposed in the last years [14,18,35,48]. These approaches provide a means for collaborative decision making by reconciling the conflicts that can arise from the evaluation of the policies provided by the entities involved in the management of co-owned resources.
However, existing multi-party access control models do not account for the protection of the policies themselves, whose disclosure can leak sensitive information as well [34,54,60]. For instance:
Collaborative commercial agreements often contain partners’ policies specifying with who and under what conditions co-owned resources and assets can be shared. While each partner expects its policies to be enforced [14], the policies might contain confidential information about a company’s business and commercial relations and, thus, their disclosure can provide insights on the company’s business strategies, which can be used by competitors (possibly in the coalition) to “evaluate sales coverage, modify compensation plans, renegotiate terms and conditions, adjust compliance policies, build advanced segmentation categories and uncover hidden supply chain risk” [20].
Contents uploaded by a user on her/his profile (or others’ profile) in an online social network might refer to multiple users, e.g., a photo shared in Facebook in which several users are tagged. The collaborative management of the contents requires the social network to consider the privacy preferences (specifying who is permitted to access the co-owned contents) of individual users. The disclosure of the users’ privacy preferences might reveal the users’ interpersonal relationship and reduce the users’ willingness in sharing new contents [51].
In critical-missions, e.g. in the military and counter-intelligence domain, international cooperation is becoming a key factor to ensure the success of the mission. In this context, intelligence is often collected from heterogeneous sources and fused to enable situation awareness and, thus, take the proper actions to handle potential threats. Information sources, however, can be under the control of different authorities. Due to the high sensitivity of data, each authority might want to enforce specific constraints on the access and usage of its data. For fused data, this implies that possibly conflicting access requirements from different parties should be accounted for. While there exist solutions that allow the collaborative specification of access control policies for fuse data [5,15], these solutions typically require the parties’ individual policies to be disclosed in clear. However, the policies themselves might contain classified information and, hence, their disclosure can raise security concerns.
The aforementioned scenarios highlight the need of protecting not only the resources but also the security policies employed for their protection as the disclosure of those policies might leak sensitive information about the entities that contributed to their definition. Therefore, collaborative systems should be equipped with an access control mechanism that preserves the confidentiality of individual user policies while remaining capable of making collaborative access decisions. In this light, we assume a multi-owner-single-user setting where multiple entities are responsible for the security of co-owned resources; specifically, each co-owners defines policies stating their access constraints for the co-owned resources and these policies are combined into a single global policy (hereafter, called multi-party policy) for collaborative access decision making. The evaluation of the multi-party policy against an access request should not leak information about the policies defined by the single co-owners.
To address this issue, in previous work [51] we proposed a privacy-preserving multi-party access control framework, in which users provide their policies in private form and policy evaluation is performed over private inputs. In particular, we designed secure computation protocols for the evaluation of multi-party policies that preserve the confidentiality of the user policies forming the multi-party access control policies. However, the framework in [51] only allows the evaluation of policies expressed in a simple identity-based access control model and uses a three-valued decision set (permit, deny, and not-applicable) that is not able to capture the complexity of existing access control standards like XACML [44].
This paper extends our previous work to enable the secure evaluation of multi-party access control policies expressed in standardized Attribute-Based Access Control (ABAC) policy languages like XACML while protecting the confidentiality of user policies. Compared to the policies considered in our previous work, ABAC policies comprise a target that determines their applicability. The target of a policy essentially consists of a set of conditions defined over subject, resource, action and environment attributes that must be met for the policy to apply to a given query. In addition, standardized ABAC policy languages like XACML often rely on multi-valued decision sets that extend the three-valued decision set by accounting for situations for which the access control mechanism cannot make a definitive decision due, for instance, to missing attributes [38].11 The privacy-preserving evaluation of such complex ABAC policies requires the definition of new protocols for target evaluation22 and for the evaluation of composite policies. The design of such protocols, however, is not trivial and requires addressing a number of challenges to ensure their practical feasibility and prevent information leakages. The main challenge lies in identifying a suitable policy representation as secure computation protocols defined on a direct encoding of complex ABAC policies are inefficient due to the complex operations that this encoding requires performing over private input. Therefore, we investigated policy representations that enable the design of efficient secure computation protocols for target and policy evaluation. In particular, we adopted a Boolean encoding of ABAC policies, which by relying on AND, OR and negation operators provides an efficient structure for secure target and policy evaluation [51]. In addition, this Boolean encoding allows us to devise mechanisms to mask the size of multi-valued decisions, which if not protected, might leak information about the underlying user policies.
We investigate the realization of the proposed protocols using two alternative privacy preserving techniques, named Homomorphic Encryption (HE) [46] and Secure Functional Evaluation (SFE) [13]. Homomorphic Encryption and Secure Functional Evaluation are two well-known and established privacy-preserving techniques, which provide the cryptographic building blocks necessary for the realization of the proposed protocols. However, these techniques are usually computationally expensive [17,39] and, thus, they might be not practical in the real-world systems, hindering their use for the development of a multi-party access control framework. To this end, we have investigated optimizations for the realization of the proposed protocols in Homomorphic Encryption and Secure Functional Evaluation and evaluated their computation and communication costs through an experimental evaluation. The results show that the SFE-based protocols outperform the HE-based protocols both in terms of both computation and communication costs and provide a basis for the effective realization of privacy-preserving mechanisms for multi-party access control. We also discuss the security of the implementation of the proposed protocols in the presence of a semi-honest adversary, which guarantees that the policy evaluation does not leak any unintended information.
The contribution of this work can be summarized as follows:
We design secure computation protocols that enable the secure evaluation of multi-party access control policies expressed in standardized ABAC policy languages like XACML while protecting the confidentiality of user policies. Based on a Boolean encoding of complex ABAC policies, we propose efficient secure computation protocols for target and policy evaluation. We also propose a new approach to hide the size of multi-valued decisions resulting from the evaluation of such policy, thus preventing the leakage of information about the individual user policies.
We realize the proposed protocols using two well-known and largely used privacy-preserving techniques, namely Homomorphic Encryption and Secure Functional Evaluation and investigate further optimizations of the protocols based on the employed privacy-preserving techniques to reduce the computation and communication costs of the implementation.
We demonstrate the security of our framework for the privacy-preserving evaluation of multi-party access control policies as well as of the underlying secure computation protocols and their composition.
We demonstrate the practical feasibility of the proposed framework in terms of computational and communication costs through an experimental evaluation. Our experiments show that the evaluation of multi-party access control policies using SFE-based protocols considerably outperforms the use of HE-based protocols. In particular, evaluating large policies (of size 50) against queries consisting of 10 attributes using SFE-based protocols requires less than 2 seconds, thus showing their practical feasibility for the evaluation of multi-party access control policies.
The remainder of the paper is structured as follows. The next section introduces the background knowledge used in this work. Section 3 provides an overview of our framework for privacy-preserving multi-party access control. Section 4 presents our secure computation protocols for the evaluation of multi-party access control policies and Section 5 provides their implementation in Homomorphic Encryption and Secure Function Evaluation. Section 6 discusses the security of the proposed protocols. An experimental evaluation of their computation and communication costs is presented in Section 7. Finally, Section 8 discusses related work and Section 9 concludes the paper.
2.Preliminaries
This section introduces the policy language used for the specification of user and multi-party access control policies. We also present the building blocks used for the design and implementation of secure computation protocols for policy evaluation in two privacy-preserving techniques, namely Homomorphic Encryption and Secure Function Evaluation.
2.1.Policy specification and evaluation
For the specification of user and multi-party access control policies, we rely on an attribute-based access control (ABAC) policy language inspired by PTaCL [10,37], which provides an abstraction of the XACML policy language [44]. We first present an extension of the PTaCL syntax, which comprises two languages, one for targets, which is used to specify the applicability of a policy to a query, and another for policies, which is used to specify how policies are combined. Then, we present the semantics of target and policy evaluation.
ABAC Syntax: Let
To determine the applicability of a policy to a query, we employ a target language, denoted by
Table 1
Operators on decision set
| 1 | 1 | 0 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 |
| 1 | 0 | 0 | 1 | 0 | 0 | 0 | 1 | 1 | 1 | 1 |
| 1 | ⊥ | 0 | 1 | ⊥ | ⊥ | 1 | 1 | ⊥ | 1 | 1 |
| 0 | 1 | 1 | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 0 |
| 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 0 | ⊥ | 1 | 0 | 0 | ⊥ | 0 | ⊥ | ⊥ | 0 | 0 |
| ⊥ | 1 | ⊥ | 0 | ⊥ | ⊥ | 1 | 1 | ⊥ | 1 | 1 |
| ⊥ | 0 | ⊥ | 0 | 0 | ⊥ | 0 | ⊥ | ⊥ | 0 | 0 |
| ⊥ | ⊥ | ⊥ | 0 | ⊥ | ⊥ | ⊥ | ⊥ | ⊥ | ⊥ | ⊥ |
PTaCL also provides a policy language
ABAC Semantics: Given the set of policies
To evaluate a query against a policy, we first need to determine whether the policy is applicable to the given query. Given a query, a target evaluates to a single value in
A policy is evaluated to decisions within
2.2.Homomorphic encryption
Homomorphic Encryption (HE) is a family of cryptographic schemes that enable computation over encrypted data. HE allows performing an operation on ciphertexts, such that the resulting ciphertext would decrypt to the same value that would have been obtained by performing the operation on the corresponding plaintexts. In this work, we employ an additively homomorphic cryptosystem, e.g. the Paillier cryptosystem [46], which preserves the result of the addition of two ciphertexts.
Let
In additive homomorphic cryptosystem, addition and scalar multiplication operations are performed over ciphertexts, without the need to decrypt them. However, performing more complex operations in additive homomorphic cryptosystem requires designing two-party interactive protocols. Next, we introduce secure two-party computation protocols, which serve as building blocks for the construction of our HE-based protocols encoding policy evaluation.
Secure Equality Protocol: Secure equality is used to determine the equality of two ciphertexts [41]. Given two ciphertexts
2.3.Secure function evaluation
Despite allowing computations in the ciphertext domain, homomorphic encryption is usually expensive in terms of computation cost. Secure function evaluation (SFE) is an alternative to homomorphic encryption that enables several parties to compute a function on their private inputs without revealing any information apart from the result of the function. In this work, we implement secure function evaluation in two-party setting using the ABY framework [13]. ABY provides the constructions for Arithmetic circuits [4], Boolean circuits [22], and Yao’s garbled circuits [57]. For our work, we only use Boolean circuits since they provide efficient constructions for nonlinear functions.
Given two parties
For this work, we adopt seven Boolean gates from the ABY framework as building blocks for the design of our SFE-based policy evaluation protocols. For more details on the mechanism and implementation of Boolean circuits, we refer the reader to [13]. Next, we present these gates.
Inverse Gate: The inverse gate is used to compute the negation of a secret shared input in modulus
3.A framework for privacy-preserving multi-party access control
This section presents our framework for privacy-preserving multi-party access control. First, we present the model for multi-party access control adopted in this work and then we present the architecture of our framework and the underlying security assumptions.
3.1.Multi-party policy model
Collaborative systems usually provide their users with an environment in which they can interact and jointly contribute to the creation and management of shared resources. To protect those resources, each user can specify access requirements stating who is authorized to access them and under which circumstances. The access requirements provided by different users, however, can be in conflict. Therefore, a collaborative system should resolve these conflicting requirements in order to determine whether access to co-owned resources should be granted.
Traditional access control models are centered on a single-owner governance model (i.e., they assume that resources are controlled by single entities) and, thus, they are not suitable for collaborative systems [11,24]. To this end, recent years have seen the emergence of several models for multi-party access control [45]. These models enable collaborative access decision making by providing a means to reconcile the conflicts arising from the evaluation of the access requirements provided by users involved in the protection of co-owned resources.
In this work, we adopt the data governance model proposed in [35] as the underlying multi-party access control model. This model provides a general framework to explicitly reason on the level of authority that users have over co-owned resources based on their relations with the resource [12] and to build a multi-party access control policy based on their authorization requirements. Specifically, it captures the relations that users have with a co-owned resource and, based on these relations, determines suitable strategies to resolve possible policy conflicts, thus accounting for the level of authority that users have on co-owned resources. These policy conflict resolution strategies can be realized using the operators presented in Table 1. Compared to other models for multi-party access control (see [45] for a survey), the model in [35] allows a more fine-grained governance of co-owned resources by allowing the adoption of arbitrary conflict resolution strategies.
As an illustration of the application of this model, consider the following example, which is based on one of the scenarios presented in the introduction. In particular, consider the case where two car companies (
The classification model, however, can be used to reconstruct potentially privacy-sensitive training data [33]. Therefore, each partner in the joint venture might specify access control policies determining who is authorized to access the model and under which conditions based on their own business constraints. Below, we present some hypothetical policies, denoted by
These policies can specify conflicting access constraints. For instance,
The multi-party policies considered in this work can be evaluated using existing access control mechanisms. However, such mechanisms require the policies to be provided in plaintext in order to be evaluated. Making these policies available to other partners (or third parties) might reveal confidential information about a company’s business strategies and commercial relationships with other companies, which the company might want to keep confidential (e.g., by knowing
3.2.Architecture
To enable the evaluation of multi-party policies while protecting the confidentiality of user policies, we design an access control framework that supports policy evaluation over protected input. An overview of the proposed framework for privacy-preserving multi-party access control is presented in Fig. 1. The framework is general and can be realized using various privacy-preserving techniques. To avoid confusion, hereafter, we denote the protected version of a message m regardless of the specific privacy-preserving technique used for its realization as
The proposed framework comprises four main entities:
Data holders (
 ) share their resources and data along with encrypted privacy policies determining to whom access is granted.
) share their resources and data along with encrypted privacy policies determining to whom access is granted.Access requester (
 ) requests access to the shared resource.
) requests access to the shared resource.Data Server (DS) stores the data holders’ resources and is responsible for their protection. Specifically, the Data Server evaluates the encrypted data holders’ policies to determine whether access to their resources should be granted.
Semi Trusted Party (STP) is a semi-honest entity that assists Data Server in the secure evaluation of data holders’ policies.
Fig. 1.
Architecture.
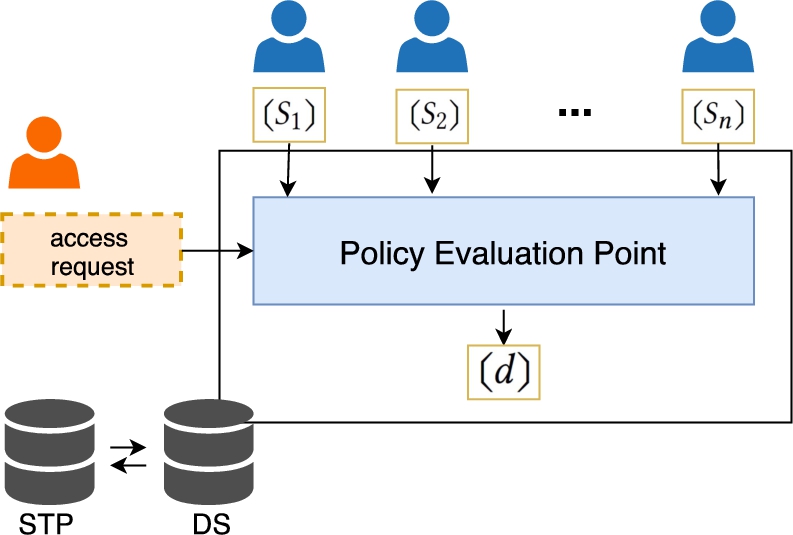
Data holders provide their policies in a private form (represented by
Upon receiving an access request, the Data Server’s policy evaluation point evaluates the request against the multi-party policy, which comprises the user policies, under privacy preservation with the assistance of the STP. To enable policy evaluation under privacy preservation, we propose secure computation protocols to determine the applicability of policies to the access request and to compute the combining operators in Table 1 over private inputs (cf. Section 4). These protocols can be used as building blocks for the secure evaluation of arbitrary multi-party policies expressed using those operators.
Once the multi-party policy has been evaluated, the policy evaluation point returns the access decision in private form,
We have realized the framework using two alternative privacy preserving techniques, namely Homomorphic Encryption (HE) and Secure Functional Evaluation (SFE). The underlying privacy-preserving technique dictates the ‘private form’ in which policies are provided and the computations to be performed in order to obtain the access decision in plaintext. In HE, the STP generates public (
In SFE, data holders create two secret shares of their policies and provide one share to the Data Server and the other share to the STP. After policy evaluation, the Data Server derives the access decision in plaintext from the decision in private form by recombining the secret share obtained by evaluating the multi-party policy with the one obtained by the STP (cf. Section 2.3).
3.3.Security assumptions
We assume a semi-honest security model where all participants are assumed to be honest-but-curious [21]. This model implies that all entities follow the protocol specification properly, but they are interested in obtaining more information from their input, intermediary messages and output. Specifically, they keep track of the messages exchanged and try to learn as much information as possible from them. This assumption guarantees that computations do not leak any unintended information. It is worth noting that while the semi-honest adversary model is more restrictive compared to the malicious model, it is a well-accepted adversary model with many applications in real-world scenarios, e.g., to protect sensitive information against passive insider attacks by administrators or government agencies, or when it is assured that the parties are trusted to not actively misbehave [13]. In this light, the semi-honest adversary model can be applied in the context of privacy preserving multi-party access control as the involved parties are typically engaged in a collaboration, implying that there exists a certain level of trust among them (see, e.g., the scenarios in the introduction). We also remark that the semi-honest adversary model enables an efficient implementation of the secure computation protocols performing considerably faster than the malicious setting, while offering a sufficient level of security [47]. This is specifically a desirable property for applications like the evaluation of security policies in private forms where (collaborative) access decisions should be made in a short amount of time.
With respect to the semi-honest security assumption, our goal is to design protocols that provide security against honest-but-curious non-colluding Data Server and STP. The non-colluding two-server setting is typically employed to reduce the workload on the client side. Without the employment of a semi trusted party, all computations have to be performed between the client and Data Server. This, however, is not desirable because it requires the data holders to have enough computational resources and to be online during computations. Note that the definition of protocols aiming to prevent the Data Server and STP from colluding is orthogonal to the scope of this work and here we consider them as two servers with independent interest who do not wish to or cannot collude [30]. The assumption of non-colluding Data Server and STP can be achieved through physical means (e.g., with the use of ballot boxes [32]) or by adding additional security verification on trusted communication channels (e.g., with the use of mediator model [1]). Moreover, several approaches have been proposed to verify the faithfulness of servers in secure two-party computation. For instance, it has been shown that multi-party computation protocols secure against semi-honest adversaries can be transformed to zero-knowledge proofs [23,28].
Nonetheless, we assume that a semi-honest adversary can compromise any subset of data holders (where at least two data holders are honest), the access requester and at most one of the STP and Data Server (i.e., if one is controlled by the adversary, the other behaves honestly66). This security definition assumes that such an adversary can only learn the policies of the data holders it has compromised and the final output but nothing else about the policies of the honest data holders [36]. We require that at least two data holders are honest because colluding data holders can learn the policy evaluation of the other data holders by comparing the final decision with the evaluation of their policies due to the definition of the used policy combining operators (see also Section 6). Imposing that at least two data holders are honest allows us to focus on flaws in the design of the protocols rather than on leakages that are inevitable.
We also assume that all parties communicate over an authenticated channel. This assumption aims to prevent attacks coming from outside the framework.
4.Protocol design
For the realization of a practical mechanism capable of evaluating policies in protected form, we need efficient secure computation protocols. In this section, we investigate the design of such protocols. We first introduce a suitable representation of targets and policies, and then we present secure computation protocols for their evaluation. These protocols serve as building blocks and can be used to evaluate arbitrary multi-party policies. In the next section, we describe the implementation of these building block protocols based on two alternative privacy-preserving techniques, namely Homomorphic Encryption and Secure Functional Evaluation.
4.1.Data structures
This section presents the data structures used for the specification of policies in private form and the representation of the decision space to enable the design of efficient protocols for secure policy evaluation.
Policy Specification: Privacy-preserving technologies like Homomorphic Encryption and Secure Function Evaluation only operate on integer numbers. To this end, we encode every attribute (
This work aims at a privacy-preserving mechanism that allows the evaluation of multi-party access control policies while protecting the confidentiality of the user policies forming the multi-party policy. In this light, we aim to protect the constraints in the target, which determine the applicability of policies, along with atomic policies (i.e., policies consisting of the permit and deny decisions) whereas combining operators are not protected. An atomic target
Note that, in this work, queries are not considered sensitive and, thus, they are received in plaintext. However, in order to be able to evaluate a policy against a query, the attributes and attribute values in the query should be mapped to integer numbers following the same encoding of attributes and attribute values used for the policy.
Decision Space: In this work, we adopt a policy language that is grounded on a three-valued logic and use
For the design of efficient secure computation protocols able to evaluate a policy in protected form against a query, we need suitable representation of the decision space encoding the results of policy evaluation. Inspired by previous work [37,56], we adopt a Boolean representation of the decision space and three-valued operators in Table 1. Given a policy p, we represent the decision space of p as a triple
In order to encode the target and policy evaluation functions and three-valued logic operators in Table 1 into triples of propositional formulas, we adopt and extend the rules proposed in [37]. These rules can be employed to compute a triple of propositional formulas
Table 2
Transformation rules for targets
| Target | |||
| 0 | |||
Table 3
Transformation rules for policies
| Policy | |||
| 1 | 1 | 0 | 0 |
| 0 | 0 | 1 | 0 |
| 0 | |||
This encoding of the target and policy evaluation functions allows the definition of protocols implementing the ¬, ∧, and ∨ operators, which can efficiently be implemented using inverse, AND and OR gates in SFE and negation, maximum and minimum protocols in HE (see Section 5). Moreover, this encoding allows masking the number of elements forming a decision d by using a fix-size representation for all decisions.
4.2.Target evaluation
To enable the secure evaluation of targets in protected form against a query, we design secure computation protocols implementing the rules presented in Table 2 over protected input. We first propose generic secure computation protocols for the evaluation of atomic targets (the first row of Table 2). As it can be observed in the table, two operations are needed for such an evaluation: i) an operation to determine whether the attribute in the target is present in the query (
Secure membership protocol. Secure membership is used to determine whether an encrypted value belongs to a set of encrypted values [19]. Given a ciphertext
Secure matching protocol. To determine whether a policy is applicable to a query we need to verify if the attribute name-value pairs forming the query satisfy the constraints in its target. To this end, we first define the secure value-matching protocol to determine whether a protected value satisfies the constraint defined in an atomic target under privacy preservation and, then, we show how this protocol can be used to determine whether there exists an attribute name-value pair in the query that satisfies the target.
Recall that our goal is to protect the confidentiality of user policies. Accordingly, the constraints establishing the applicability of these policies should be protected and, thus, we assume that not only the attribute name and value but also the predicate in an atomic target is in protected form. Given an atomic target in protected form
The value-matching protocol verifies whether a given attribute value satisfies the constraint defined in the target. Determining whether a policy is applicable to a given request requires extending this verification by checking if there exists an attribute name-value pair in the query that satisfies the target of the policy. To this end, we define the secure matching protocol (Algorithm 1). Given an atomic target in protected form
Algorithm 1:
matching: secure matching protocol
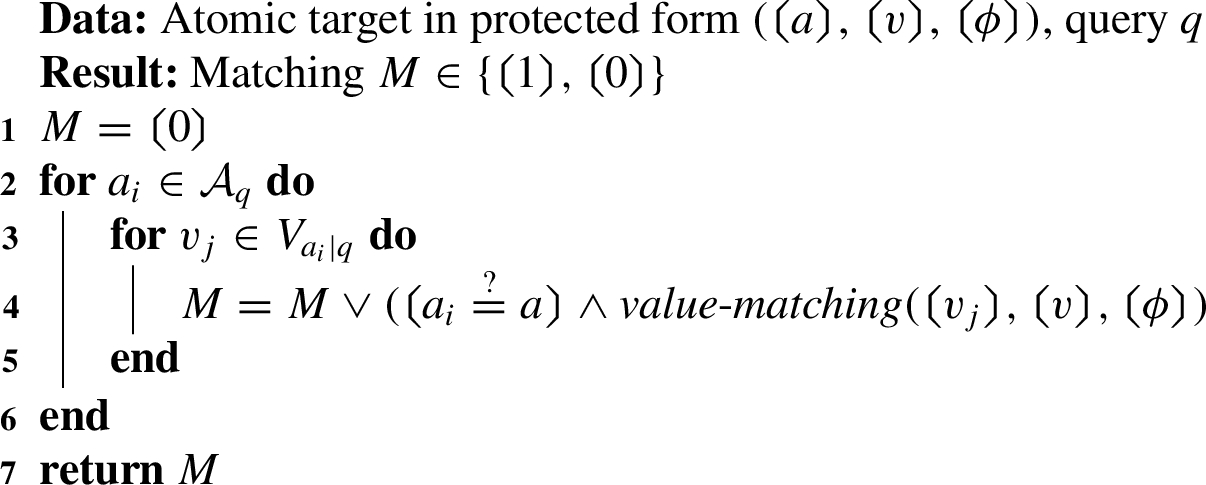
Target evaluation protocol. We have now the machinery to define the protocol for secure target evaluation. Given a target in protected form
Atomic target: Given an atomic target in protected form
4.3.Policy evaluation
The secure evaluation of a policy against a given query requires secure computation protocols implementing the formulas given in Table 3. Here, we provide the design of a generic protocol for policy evaluation under privacy preservation and then we discuss in Section 5 how it can be realized in Homomorphic Encryption and Secure Function Evaluation.
Given a policy in protected form
Decision policy: Given a policy comprising the permit or deny decision in protected form (
5.Protocol implementation
In this section, we describe the realization of the protocols for secure policy evaluation presented in Section 4 using two well-known privacy-preserving techniques, namely (additively) Homomorphic Encryption (HE) and Secure Functional Evaluation (SFE).
5.1.SFE-based protocols
To realize the protocols presented in Section 4 using Secure Functional Evaluation (SFE), we employ the building blocks presented in Section 2.3, i.e. inverse, AND, OR, subtraction, multiplication, equality, and comparison gates. We first observe that the protocols for the evaluation of composite targets (Table 2) and policies (Table 3) are built over operators ¬, ∧ and ∨, which can be implemented in SFE using the inverse, AND and OR gates, respectively. Therefore, in this section, we only detail how the secure membership and matching protocols can be realized in terms of SFE gates.
Secure membership protocol. Given a secret shared input
Secure matching protocol. To verify the applicability of a secret shared policy to a query, we realize the value-matching protocol presented in Section 4 using Secure Function Evaluation. Given a secret shared target
5.2.HE-based protocols
As an alternative to Secure Function Evaluation, we realize the protocols for secure policy evaluation using (additively) Homomorphic Encryption (HE). Specifically, we implement the generic protocols presented in Section 4 using the five cryptographic building blocks presented in Section 2.2, i.e., addition, subtraction, multiplication, equality and comparison. As shown in Tables 2 and 3, the protocols for secure policy evaluation rely on operators ¬, ∧ and ∨. To this end, we first discuss how the secure computation of these operators can be realized in HE. Then, we present the implementation of the secure membership and matching protocols.
Secure HE-based computation of operators ¬, ∧ and ∨. For the realization of the secure membership and matching protocols as well as for the realization of the protocols for secure evaluation of composite targets and policies, we need building block protocols implementing operators ¬, ∧ and ∨.
It is worth noting that operators ¬, ∧ and ∨ defined over Boolean logic are a reduction of the negation (¬), strong conjunction (
Operator ¬: Given an encrypted value
Operator ∧: This operator can be realized using the secure multiplication protocol. Given two ciphertexts
Operator ∨: Differently from operator ∧, none of the building blocks presented in Section 5.2 implements operator ∨. This operator can be realized through a protocol that computes the minimum between two values under encryption. Given two ciphertexts
Secure membership protocol. Given an encrypted value
Secure matching protocol. The protocols presented above can be used to implement the secure matching protocol in HE. Specifically, given an encrypted target
It is worth noting that the secure minimum protocol uses homomorphic subtraction and the multiplication protocol to ensure that the outcome is in the range
Specifically, given an encrypted target
Algorithm 2:
matchingH: secure HE-based matching protocol
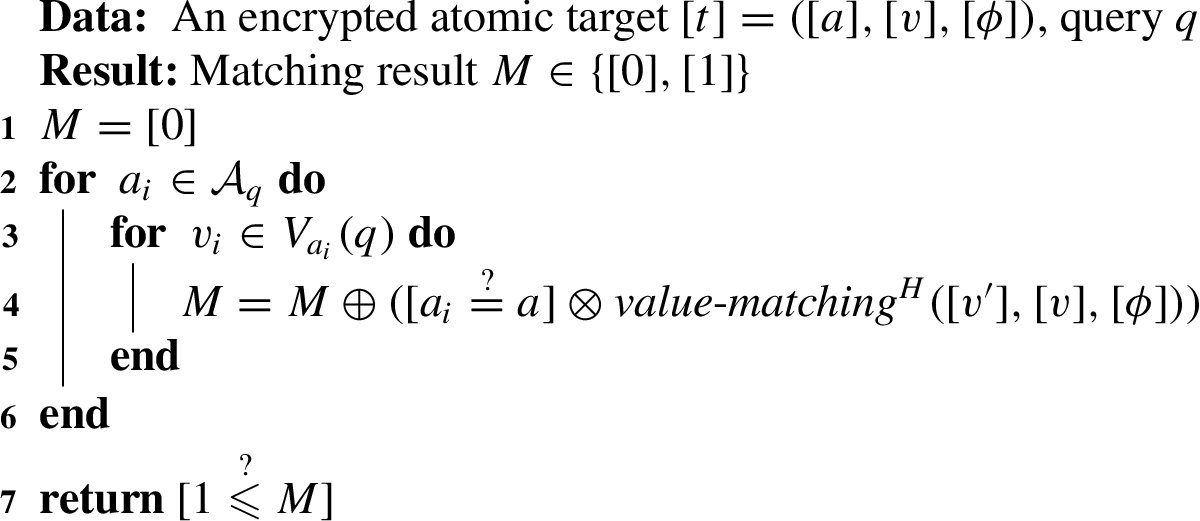
Then, instead of returning the result of the matching (i.e., M) directly as in Algorithm 1, the secure matching protocol for HE (Algorithm 2) applies the secure comparison protocol (line 7). Intuitively, if at least one of the query’s values satisfies the constrain specified in the target, M is greater than 0, and consequently the protocol (
5.3.Complexity analysis
To gain insights on the computational complexity of the proposed framework, we first analyze the complexity of the protocols for privacy-preserving target and policy evaluation presented in Section 4 in terms of the building block protocols, i.e., ¬, ∧, ∨, −, ×,
5.3.1.Protocol complexity
This section presents an analysis of the complexity of the proposed protocols for target and policy evaluation on private inputs in terms of the building block protocols used for their definition. Before presenting such an analysis, we assess the complexity of the secure membership, value-matching and matching protocols, which have been introduced to support target and policy evaluation on private inputs.
Membership protocol: The membership protocol employs the
Value-matching protocol: The value-matching protocol uses two times the ¬ protocol, four times the ∧ protocol, four times ∨ protocol, seven times the
Matching protocol: The matching protocol (Algorithm 1) employs the value-matching, ∧, ∨ and
Now we have the machinery to study the complexity of our protocols for secure target/policy evaluation. The analysis is performed per case based on the grammar of
Atomic target: Based on the encoding presented in Section 4.2, the secure evaluation of atomic targets in protected form
Composite target: The evaluation of a composite target in protected form
Decision policy: The secure evaluation of a decision policy
Targeted policy: The secure evaluation of a targeted policy
Composite policy: The evaluation of a composite policy in private form
As discussed above, targeted and composite policies are complex policy statements, whose elements can be in turn targeted and composite policies. Therefore, assessing their actual complexity requires unfolding their definition in terms of atomic targets, decision policies and targeted policies. Given an arbitrary policy
Table 4 summarizes the complexity of the main protocols in terms of the complexity of building block protocols. It is worth noting that the actual complexity depends on the specific privacy-preserving technique used for the implementation of the protocols. In next section, we discuss the complexity of the realization of the protocols in Secure Functional Evaluation and Homomorphic Encryption.
Table 4
Protocol complexity in terms of the number of building block protocols; k and m are respectively the number of distinct attributes and attribute-values in the query to be evaluated; n,
| Building block protocols | |||||||
| Membership | – | – | – | k | 1 | – | |
| Value-matching | 2 | 4 | 4 | – | – | 7 | 2 |
| Matching (Algorithm 1) | – | – | |||||
| Atomic target ( | |||||||
| Composite target ( | |||||||
| Decision policy ( | – | – | – | – | – | 2 | – |
| Arbitrary policy ( | |||||||
5.3.2.Complexity of the protocol realization in SFE and HE
This section analyzes the complexity of the realization of the proposed protocols in Secure Functional Evaluation and Homomorphic Encryption.
SFE-based protocols: in SFE, the ¬, ∧, ∨, −, ×,
HE-based protocols: in HE, only some of the building blocks used for the definition of the protocols in Section 4 can be directly mapped to the HE building blocks. In particular, the −, ×,
Similarly to what observed for the SFE encoding, some HE building block protocols are heavier than others in terms of computation and communication costs [16,41,42]. In particular, the addition and subtraction protocols are light in additively homomorphic cryptosystems such as the Paillier cryptosystem [46], while the multiplication, equality, and comparison protocols are considerably heavy protocols in those cryptosystems. For instance, it has been shown that the computation and communication costs of multiplication protocol are 200 times more than those of the addition protocol [16].
Based on these observations, we redesigned three building block protocols (i.e., ¬, ∧, ∨) proposed in [51] by replacing the use of heavy protocols with lighter protocols (cf. Section 5.2).99 Next we present a comparison between the complexity of the ¬, ∧, and ∨ protocols proposed in [51] (represented by Eq. (1), (2), and (3)) –
We have also optimized the HE implementation of the matching protocol (Algorithm 2) to reduce the instances of the multiplication protocol to be executed compared to Algorithm 1. By comparing Algorithm 1 and Algorithm 2, it can be observed that the application of the multiplication and subtraction protocols has been reduced m times each (recall that m is the number of attribute values in the query), which in addition to the complexity reduction resulting from using the optimized versions of the ¬, ∧, and ∨ protocols, significantly reduces the complexity of the matching protocol.
Table 5 summarizes the complexity of HE-based protocols in both general and optimized forms in terms of the number of HE-based building block protocols.1010 It can be observed that, for instance, in atomic target evaluation the application of the comparison (multiplication) protocol has been reduced from
Table 5
The complexity of HE-based protocols in terms of the number of HE building block protocols in generic and optimized form; k and m are respectively the number of distinct attributes and attribute-values appeared in query q; n,
| HE-based building block protocols | |||||
| Negation | 1 | ||||
| Optimized Negation | 1 | ||||
| Min | 1 | 2 | 2 | ||
| Optimized min | 1 | ||||
| Max | 1 | 2 | 2 | ||
| Optimized max | 1 | 1 | 1 | ||
| Value-matching | 8 | 16 | 9 | 18 | |
| Optimized Value-matching | 4 | 6 | 8 | 7 | 2 |
| Matching | |||||
| Optimized matching | |||||
| Atomic target | |||||
| Optimized atomic target | |||||
| Composite target | |||||
| Optimized composite target | |||||
| Arbitrary policy | |||||
| Optimized arbitrary policy | |||||
6.Security analysis
This section provides a security analysis of our framework for privacy-preserving multi-party access control (Section 3.2) and of the underlying secure computation protocols (Section 5).
6.1.Protocol security analysis
The proposed privacy preserving protocols were designed based on Homomorphic Encryption and Secure Function Evaluation. We chose Paillier’s cryptosystem for the implementation of HE-based protocols. The security of the Paillier cryptosystem is based on computational difficulty of solving decisional composite residuosity assumption [46]. We employed three HE-based building blocks to shape our complex protocols, namely secure equality [41], secure comparison [42] and secure multiplication protocols [16]. These building blocks have been proven to be secure in the presence of semi-honest adversaries. We refer readers to corresponding papers for the details of the security analysis for each building block.
For policy evaluation in Secure Function Evaluation, we employed the Boolean circuits provided by the ABY framework [22]. The use of these circuits provides information theoretic security against semi-honest adversaries and malicious adversaries in the existence of honest majority. We refer readers to [13,22] for the details of secure implementation and security proofs.
In the design of our protocols, we use a combination of the building blocks that are proven secure. According to the universally composable security theorem of Canetti [7], a protocol that is obtained by arbitrary combination of secure subprotocols guarantees security. Therefore, we can conclude that the protocols presented in Section 5 as well as their combination are secure since they are composed from subprotocols proven to be secure.
6.2.Framework security analysis
Our framework is designed to be secure against the semi-honest adversary model. The two parties involved in our setting, i.e. the STP and Data Server, are semi-honest non-colluding parties who try to obtain additional information from the execution of the protocols. The data holders provide the protected data properly (i.e., encrypted data for HE-based protocols and secret shared data for SFE-based protocols) to the intended parties.
Given that our protocols based on HE and SFE are secure, in the following we discuss the security of our whole framework with respect to the interactions between participants.
The access requester can observe whether access is granted or not. From this, she can learn the final decision but not the evaluation of the data holders’ policies. It is worth noting that, by testing all possible queries, an attacker can only reconstruct the overall multi-party policy, but she would not be able to reconstruct the individual user policies.
The STP learns neither the data holders’ policies nor the final decision. In the HE setting, the STP generates the public and private keys and sends the public key to the data holders and Data Server. Moreover, this entity interacts with the Data Server to evaluate the policies. As discussed above, the building blocks we use in the design of operators are secure and, thus, the semi-honest STP is not able to learn the data holders’ individual policies. Moreover, the STP receives the encrypted final decision, which it decrypts using the private key. However, because of the noise added by the Data Server to the encrypted message (see Section 3.2), the STP is not able to infer the final decision.1111 On the other hand, in the SFE setting, the STP only receives one secret share of the data holders’ policies. Therefore, neither the data holders’ policies nor the result of policy evaluation are revealed to the STP.
The Data Server does not learn the data holders’ policies. The Data Server receives the policies of each data holder in private form (encrypted in HE-based protocols and secure shared in SFE-based protocols). In the HE setting, since it does not have the private key, it is not able to learn the data holders’ policies. On the other hand, in the SFE setting, the Data Server only receives secret shares of the data holders’ policies. After policy evaluation, the Data Server learns the final decision, but not each individual policy. The Data Server evaluates the multi-party policy through communication with the STP, which has been proven secure. The final decision, which the Data Server derives with the help of the STP, is not considered as a secret information for the Data Server since this entity is responsible for its enforcement.
Data Server and requester collusion: in the SFE setting, neither the Data Server nor the requester has access to the other share of the data holders’ policies. Thus, even if they collude, they are not able to learn the intermediate decisions and data holders’ policies. Similarly, in the HE setting, neither the Data Server nor the requester has the private key. Therefore, they cannot decrypt the messages to obtain the policies of the data holders. Both the Data Server and the requester have access to the final decision; thus, neither of these entities learns new information.
STP and requester collusion: the security in the SFE setting can be demonstrated similarly to the case where the Data Server and requester collude as the STP and requester together only possess one share of the data holders’ policies. In the HE setting, the Data Server adds random noise to the encrypted data before transferring them to the STP. Thus, even if the STP and the requester have the private key (which is generated by the STP), they cannot obtain any unintended information. It is worth noting that the collusion of the STP and requester might reveal the final decision to the STP. Yet, from the final decision the STP and requester cannot reconstruct the individual policies of the data holders.
Data Server and data holders collusion: some data holders might collude with the Data Server to learn the policies of the other data holders, where at least two data holders are honest (cf. Section 3.3). However, the colluding data holders and the Data Server together only have one share of the data of the non-colluding data holders in the SFE setting and do not have the private key of the other data holders in the HE setting. Thus, they cannot derive any unintended information from intermediary messages. Nonetheless, by colluding, the Data Server and data holders might infer the overall evaluation of the honest data holders’ policies (from the final decision known by the Data Server), but they are not able to reconstruct the individual policies of honest parties. This is because at least two data holders are assumed to be honest and, in most cases, knowing the overall evaluation of their policies is not enough to learn the individual policies (see later for a discussion).
STP and data holders collusion: since the Data Server adds random noises to messages in the HE setting and the STP does not possess the share of the data of the honest data holders in the SFE setting, even if the STP and the data holders collude, they cannot understand the inputs of honest data holders.
7.Experiments
We have implemented the protocols presented in Section 5 in
To assess the practical feasibility of our mechanism for privacy-preserving multi-party access control, we performed three sets of experiments: 1) the first set of experiments is used to evaluate the impact of protected atomic target evaluation against the queries of different sizes; 2) the next set of experiments studies the scalability of implementing the combining operators over private inputs; 3) the last set of experiments investigates the impact of protected complex policies’ evaluation, where the number of atomic targets forming a complex policy varies. In all experiments, we used computation time (in ms) to measure computation cost and bandwidth usage (in bytes) to measure communication cost.
In a practical scenario, the two parties running the experiments (in both HE and SFE setting) would be remote parties communicating through an Internet connection. For the experiments such a connection was simulated with the use of local sockets. This does not matter for the communication costs as the data that is sent in a local network is equal to the data usage of a remote connection. The experiments were performed on a virtual single machine running Ubuntu 19.04 LTS with 64-bit microprocessor and 5 GB of RAM, with Intel Core i5-7200U CPU, 2.5 GHz.
7.1.Atomic target evaluation
The evaluation of an atomic target has a significant impact on policy evaluation as it serves as a building block for the evaluation of any target (cf. Table 2). As shown in Section 5.3, the secure evaluation of atomic targets depends on the query size (i.e., the number of attributes and attribute name-value pairs constituting the query). In the first set of experiments we assess their impact in terms of computation and communication costs by evaluating atomic targets against queries of different size for both HE-based protocols and SFE-based protocols.
Setting. For the experiments, we generated a set of 10 attributes
Fig. 2.
Computation time (in seconds) for the secure evaluation of protected atomic target against queries of different sizes. Y-axis is in log scale.
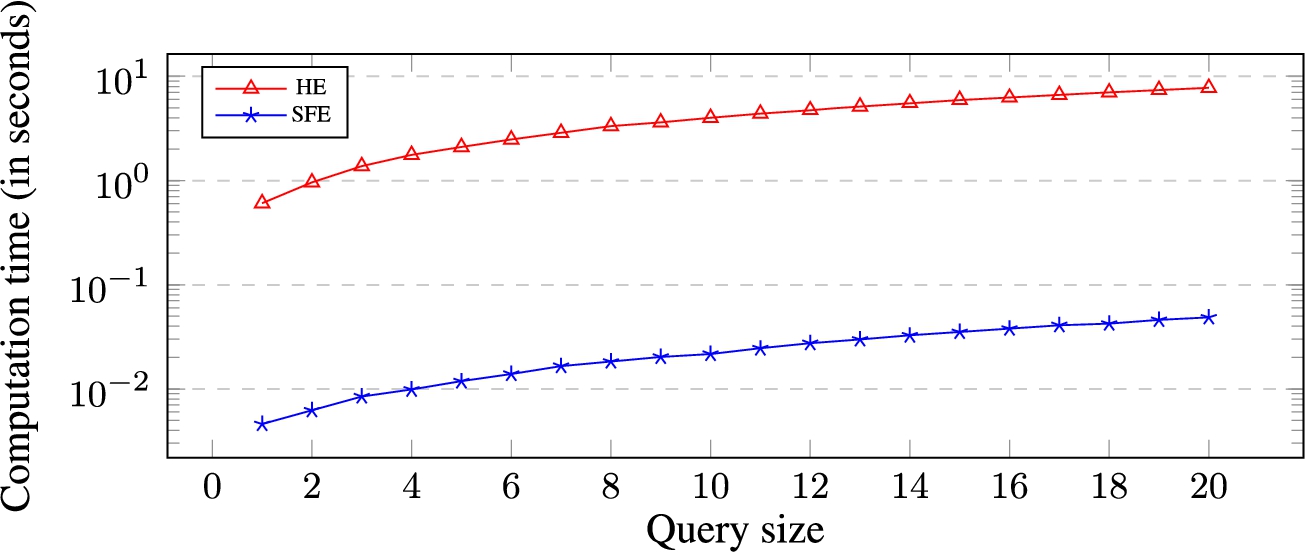
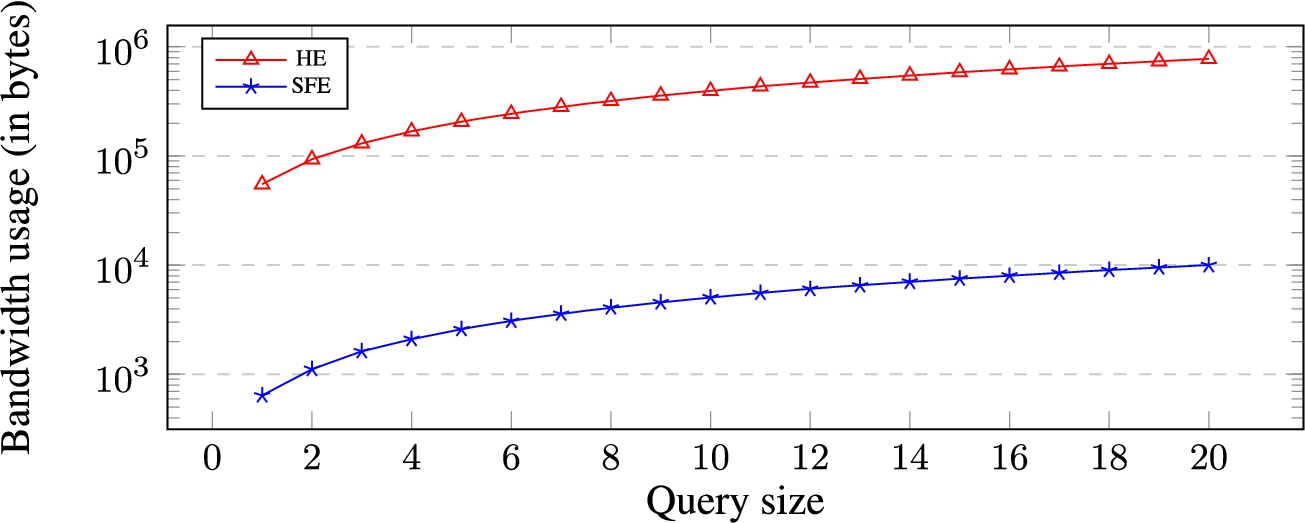
Results. Figures 2 and 3 show respectively the average computation time and bandwidth usage (in log scale) for the secure evaluation of protected atomic target against queries of different sizes (from 1 to 20) over 50 rounds of the experiments. The results show that the SFE-based protocols outperform the HE-based ones in terms of both computation and communication costs. In particular, the evaluation of an atomic target against a query of size 20 required 4.84 ms (9998 bytes) using SFE-based protocols and 779 ms (776171 bytes) using HE-based protocols. Moreover, we can observe that both computation and communication costs of atomic target evaluation are linear in the query size.
Fig. 3.
Bandwidth usage (in bytes) for the secure evaluation of protected atomic target against queries of different sizes. Y-axis is in log scale.
7.2.Combining operators
This set of experiments aims to assess the computation and communication costs required by the protocols for the secure computation of the combining operators presented in Table 1. This provides an indication of the resources required by the combining operators in Boolean encoding (Table 3) when implemented using Homomorphic Encryption and Secure Function Evaluation.
Settings. For the experiments, we have created two policies for each operator in Table 1, one for each privacy-preserving approach (HE and SFE). Each policy consists of one or two policy depending on the number of arguments required by the operator. For each operator, we repeated the experiments 50 times.
Results. Table 6 reports the average computation time and bandwidth usage for the protocols implementing the combining operators in Table 1 over 50 runs.
As it can be observed, the SFE-based protocols outperform the HE-based protocols both in terms of computation and communication costs. On average, the computation and communication costs of HE-based protocols are approximately 8000 and 32 times worse than SFE-based ones, respectively. It is worth noting that binary operators exhibit a similar computation and communication costs in binary operators (for both HE and SFE protocols). This is because these protocols comprise an equal number of ∧, ∨, and ¬ operators (cf. Table 3). On the other hand, the negation protocol is slightly cheaper in Homomorphic Encryption as it only requires swapping values rather than operating on logic formulas.
7.3.Composite policies
To gain more insights on the feasibility of our mechanism for privacy preserving multi-party access control, we performed experiments to assess the scalability of policy evaluation on private input in more complex scenarios.
Table 6
Computation time (in ms) and communication bandwidth (in bytes) for single operator
| Time (ms) | Bandwidth (bytes) | |||
| HE | SFE | HE | SFE | |
| ¬ | 0 | 0.09 | 0 | 51 |
| ∼ | 213 | 0.09 | 768 | 65 |
| ⊔ | 880 | 0.1008 | 3842 | 121 |
| ⊓ | 873 | 0.1032 | 3841 | 121 |
| 873 | 0.1159 | 3842 | 121 | |
| 882 | 0.1068 | 3842 | 121 | |
| △ | 882 | 0.0929 | 3841 | 121 |
| ▽ | 873 | 0.1072 | 3842 | 121 |
| ⊳ | 827 | 0.1041 | 3842 | 121 |
Settings. For this set of experiments, we generate random policies by varying the policy size. As target evaluation is more computationally and communicationally expensive compared to the evaluation of combining operators,1313 we regard the size of a policy as the number of atomic targets constituting the policy. We varied the policy size from 1 to 50, while we fixed the query size to 10.
Fig. 4.
Computation time (in seconds) for the secure evaluation of protected composite policies against queries of size 10. Y-axis is in log scale.
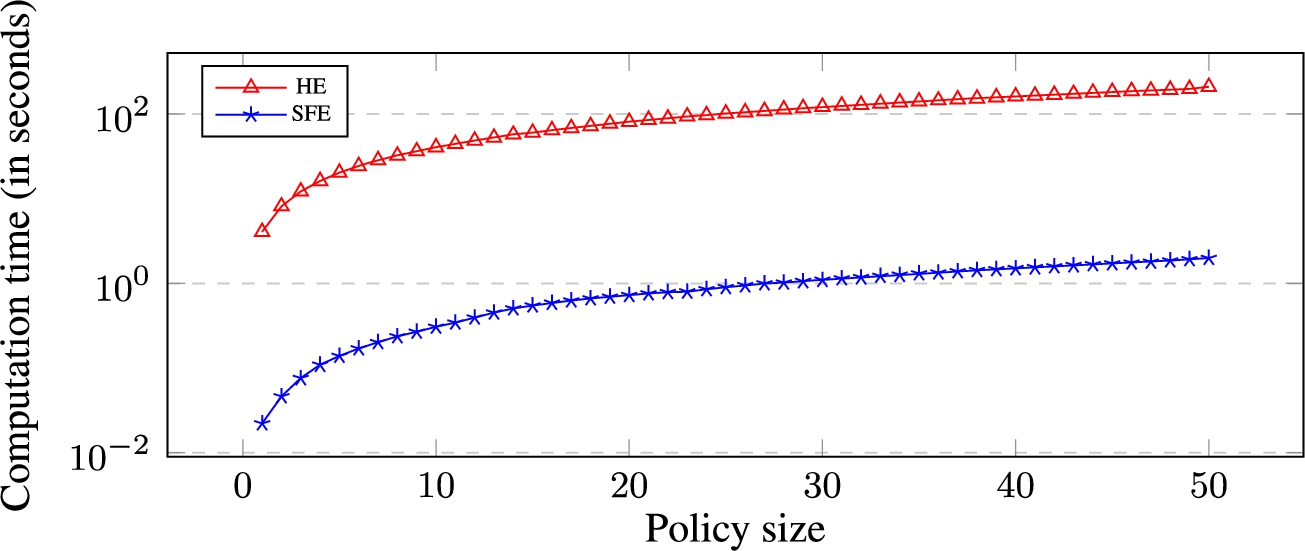
Fig. 5.
Bandwidth usage (in bytes) for the secure evaluation of protected composite policies against queries of size 10. Y-axis is in log scale.
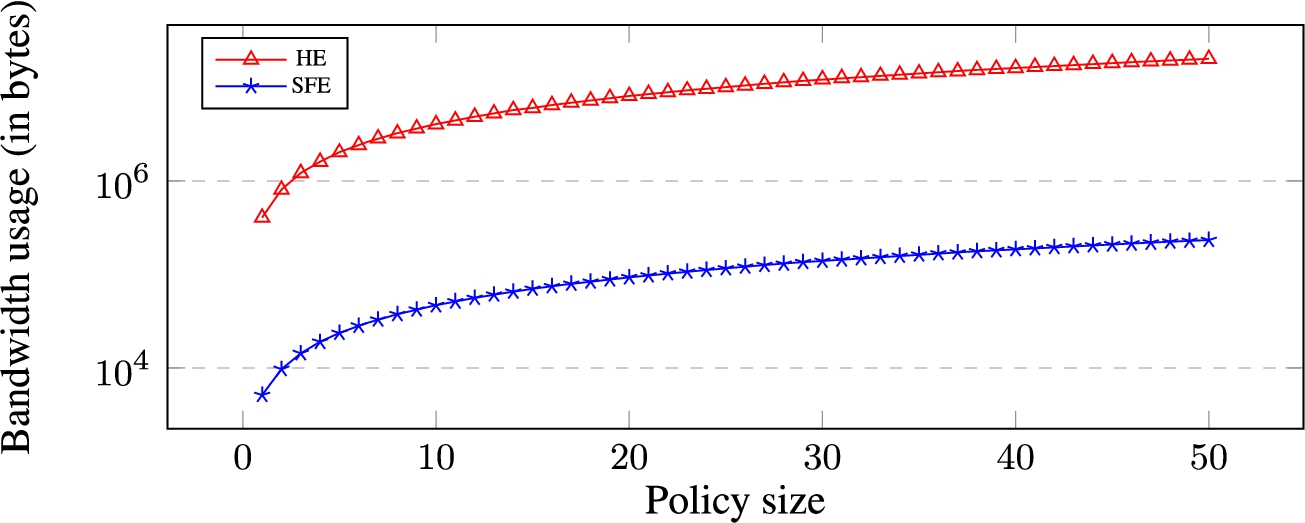
Results. Figures 4 and 5 report the average computation time and bandwidth usage (in log scale) for each policy size. This result confirms that SFE-based protocols outperform HE-based protocols in terms of both time and bandwidth usage. On average, the computation time required for the evaluation of policies of size 1 to 10 in HE is 13 times worse than the computation time required by SFE-protocols. This ratio increases to 105 when we compare the time required for evaluating the policy of size 50 in HE and SFE. Moreover, the bandwidth usage for the evaluation of policy of size 50 is 86 times worse when implemented in HE compared to SFE.
This difference between HE-based and SFE-based protocols arises for two reasons. The first reason is that HE-based protocols, beside needing to perform encryption and decryption at the end of each communication, also require implementing heavier multiplication operation for the implementation of ∧ and ∨ operators. These operations require modular exponentiations, which is computationally and communicationally heavy. On the other hand, operations in SFE are simpler, encompassing low-level circuit operations such as such as AND, OR and inverse check. The second reason is related to the size of messages used in HE and SFE. In HE, all operations are performed on 2048 bits ciphertexts. On the other hand, in SFE, a much smaller bit message size is used.
From these experiments, we conclude that the implementation of policy evaluation protocols using Homomorphic Encryption has some limitations in terms of computation and communication costs. On the other hand, Secure Functional Evaluation provides a viable solution for the realization of the proposed protocols for privacy-preserving policy evaluation in multi-party access control.
8.Related work
In recent years, multi-party access control has received increasing attention [45]. This interest has resulted in several access control solutions for the protection of jointly-owned and jointly-managed resources, either through co-owners’ negotiation [18] or automatic built-in interface [27]. Approaches for collaborative decision making and conflict resolution have been largely investigated through the application of game theory [49], computational mechanisms [52], social-friend circle model [59], and veto voting [53]. These approaches, however, do not consider users’ policies as sensitive information by themselves.
The confidentiality of policies has typically been addressed in trust negotiation [34,60]. The aim of trust negotiation is to establish mutual trust between parties that do not have a pre-existing relationship through an exchange of (extensional) policies, represented by digital credentials. Disclosure of credentials, in turn, is regulated by policies specifying which credentials must be received before the requested credentials can be disclosed. Similarly, Trivellato et al. [54] propose a goal evaluation algorithm for trust management that detects termination in a completely distributed way without the need of disclosing the policies of parties, thereby preserving their confidentiality. In this work, we pursue a different direction and assume that parties disclose their policies in private form. These policies are then evaluated in privacy-preserving way using secure computation protocols.
A large body of research has investigated the use of cryptographic techniques for the enforcement of access control policy. Identity-based Encryption (IBE) reconsiders the concept of public-key cryptography, in which a message is encrypted for a specific receiver using its public-key, by allowing the public-key to be an arbitrary string [50], e.g., the receiver’s email address. Attribute-Based Encryption (ABE) go one step further by modeling an identity as a set of attributes [25], thus supporting the enforcement of ABAC policies. ABE schemes can be classified into two main classes: Key-Policy ABE (KP-ABE) [2], in which the access control policy is encoded into the user’s private-key and the ciphertext is computed with respect to a set of attributes, and Ciphertext-Policy ABE (CP-ABE) [6], in which the user’s private-key is associated with a set of attributes and the access control policy is specified in the ciphertext. Our solution is closer to CP-ABE where the access control policy is closer to the resource to be protected. While CP-ABE schemes originally focus on the protection of the plaintext (i.e., ciphertexts reveal no information about the underlying plaintext) and rely on a single authority, a number of schemes have been proposed to extend CP-ABE to protect policy confidentiality and to deal with collaborative systems. Policy confidentiality can be protected using anonymous ABE schemes [31,43,62] where the access control policy is hidden and the decryptor cannot obtain more information about the policy associated with the encrypted data besides the fact that it can decrypt the data. On the other hand, multi-authority ABE schemes [8,9] have emerged to account for that more than one entity could be responsible for managing the attributes (e.g., one managing driver licenses and one managing voter registration). However, these schemes target a different type of collaborative systems, in which resources are governed by a single entity and delegation is used to enable decentralized authorization across administrative domains; contrarily, our solution focuses on the evaluation of multi-party access control policies which integrate possibly conflicting access constraints from multiple parties. To the best of our knowledge, no CP-ABE schemes support the collaborative specification of access control policies for co-owned resources. Moreover, CP-ABE and, in general, ABE schemes have restrictions in the types of ABAC policies that can be enforced (i.e., only equality constraints are supported), while our solution supports the specification of a larger range of access constraints (cf. Section 4) and, given its compositional nature, can be extended to support additional types of access constraints.
An application of cryptographic-based techniques to multi-party access control can be found in [26], which proposes a collaborative access control model based on threshold-based secret sharing. Data holders upload their co-owned resources encrypted and disclose secret shares of the decryption key to trusted friends, who are responsible to partially enforce the collective policy. A user can only decrypt a resource if she collects ‘enough’ shares of the key. This work, however, mainly focuses on the protection of resources, whereas the confidentiality of users’ policies is not addressed. Moreover, compared to our work that supports the definition of arbitrary strategies to combine users’ policies, this approach only allows a simple strategy based on the number of shares of the decryption key that the user should have.
For secure policy evaluation, we rely on previous work on secure multiparty computation. The basic concepts for secure multiparty computation were first introduced by Yao [57]. Since, several approaches for the secure evaluation of a function have been developed, e.g. based on combinatorial circuits [22] or one-dimensional look up tables [40]. These approaches tend to be impractical due to the high computation/communication costs. Homomorphic Encryption and Secure Functional Evaluation have shown a promising result in terms of communication and computation costs in the context of multi-party access control [51]. However, differently from [51], the secure computation protocols proposed in this work allow the evaluation of policies expressed in ABAC and have been implemented using a Boolean encoding of the decision space, which provides a more efficient implementation compared to the use of a three-valued encoding.
There are a few attempts in the literature implementing logical operations over protected inputs, e.g. privacy-preserving min computation in mobile sensing data [61] or privacy-preserving Max/Min query protocol for two-tiered sensor network [58]. However, this body of work fail to address the secure implementation of the complete set of operations required in this study (Tables 2 and 3).
9.Conclusions and future work
In this work, we proposed a framework for the secure evaluation of multi-party access control policies expressed in ABAC, which preserves the confidentiality of individual user policies forming the multi-party policy. In particular, we designed secure computation protocols for the evaluation of multi-party policies based on a Boolean encoding of the decision space and able to account for the evaluation of complex targets. We realized such protocols using two privacy-preserving approaches, namely Homomorphic Encryption and Secure Functional Evaluation. An experimental evaluation of the proposed protocols shows that the SFE-based protocols outperform the HE-based ones in terms of both computation time and bandwidth usage and provide an effective foundation for the realization of privacy-preserving mechanisms for multi-party access control.
As future work, we aim to extend our approach to support the evaluation of multi-party policies in which the operators used for combining atomic targets and policies are also protected. This should minimize the risks that an attacker can learn some information on the underlying user policies.
Notes
1 In this work, we use a seven-valued set
2 In our previous work [51], the applicability of policies to a given query was simply computed using the private set intersection protocol to check if the requester belongs to the set of authorized users while a target of an ABAC policy can comprise equality, inequality and inclusion conditions.
3 The PTaCL target language only supports the equality predicate.
4 Note that the encryption of two equal messages with the same public-key typically results in two different ciphertexts. In many cryptosystems like the Paillier cryptosystem, this is guaranteed by the fact that the encryption function is probabilistic.
5 Here the inclusion (∈) constraint is used as a shorthand to check if the country of the requesting company is one of the EU countries. It is trivial to observe that an inclusion constraint can be rewritten as equality constraints over the elements of the set.
6 This captures the property that the Data Server and STP are not colluding parties.
7 The uniqueness of attribute values can be easily achieved through a renaming of attribute values.
8 Recall that the attribute name-value pairs in a query are in plaintext and, thus, we determine which values of an attribute occur in the query.
9 Note that the correctness of the new protocols can be proved under the condition that the input data are binary (0 or 1) as discussed in Section 5.2.
10 The membership and decision policy which have the same complexity when designed in general and optimized versions have not been reported in this table.
11 Note that for all HE-based protocols in the two-party setting (including the HE-based building blocks considered in this work), the party that does not have the secret key adds random noise to the encrypted messages before they are sent to the party possessing the private key.
12 The implementation of the proposed protocols in HE and SFE can be found at https://github.com/IschaStork/he-policy-eval and https://github.com/IschaStork/sfe-policy-eval, respectively.
13 The previous experiments show that, on average, the computation and communication costs of atomic target evaluation (against queries of size 10) are 22 and 72 times worse than the evaluation of heaviest combining operator implementation.
Acknowledgments
This work is supported by the H2020-ECSEL programme of the European Commission through the SECREDAS project (grant no. 783119).
References
[1] | J. Alwen, A. Shelat and I. Visconti, Collusion-free protocols in the mediated model, in: Advances in Cryptology, Springer, (2008) , pp. 497–514. |
[2] | N. Attrapadung, B. Libert and E. de Panafieu, Expressive key-policy attribute-based encryption with constant-size ciphertexts, in: International Conference on Practice and Theory in Public Key Cryptography, (2011) , pp. 90–108. |
[3] | E.B. Barker, L. Chen, A.R. Regenscheid and M.E. Smid, SP 800-56B. Recommendation for pair-wise key establishment schemes using integer factorization cryptography, Technical report, Gaithersburg, MD, United States, 2009. |
[4] | D. Beaver, Efficient multiparty protocols using circuit randomization, in: Advances in Cryptology, (1991) , pp. 420–432. |
[5] | C. Bertolissi, J. den Hartog and N. Zannone, Using provenance for secure data fusion in cooperative systems, in: Proceedings of Symposium on Access Control Models and Technologies, ACM, (2019) , pp. 185–194. |
[6] | J. Bethencourt, A. Sahai and B. Waters, Ciphertext-policy attribute-based encryption, in: Proceedings of IEEE Symposium on Security and Privacy, IEEE, (2007) , pp. 321–334. |
[7] | R. Canetti, Universally composable security: A new paradigm for cryptographic protocols, in: Proceedings of Symposium on Foundations of Computer Science, IEEE, (2001) , pp. 136–145. doi:10.1109/SFCS.2001.959888. |
[8] | M. Chase, Multi-authority attribute based encryption, in: Theory of Cryptography, Springer, (2007) , pp. 515–534. doi:10.1007/978-3-540-70936-7_28. |
[9] | M. Chase and S.S.M. Chow, Improving privacy and security in multi-authority attribute-based encryption, in: Proceedings of ACM Conference on Computer and Communications Security, ACM, (2009) , pp. 121–130. |
[10] | J. Crampton and C. Morisset, PTaCL: A language for attribute-based access control in open systems, in: Principles of Security and Trust, Springer, (2012) , pp. 390–409. |
[11] | J. Cui, H. Zhong, X. Tang and J. Zhang, A fined-grained privacy-preserving access control protocol in wireless sensor networks, in: International Conference on Utility and Cloud Computing, ACM, (2016) , pp. 382–387. doi:10.1145/2996890.3007850. |
[12] | S. Damen, J. den Hartog and N. Zannone, CollAC: Collaborative access control, in: Proceedings of International Conference on Collaboration Technologies and Systems, IEEE, (2014) , pp. 142–149. |
[13] | D. Demmler, T. Schneider and M. Zohner, ABY – A framework for efficient mixed-protocol secure two-party computation, in: Proceedings of Annual Network and Distributed System Security Symposium, (2015) . |
[14] | J. den Hartog and N. Zannone, Collaborative access decisions: Why has my decision not been enforced? in: Information Systems Security, LNCS, Vol. 10063: , Springer, (2016) , pp. 109–130. doi:10.1007/978-3-319-49806-5_6. |
[15] | J. den Hartog and N. Zannone, A policy framework for data fusion and derived data control, in: Proceedings of ACM International Workshop on Attribute Based Access Control, ACM, (2016) , pp. 47–57. |
[16] | Z. Erkin, M. Franz, J. Guajardo, S. Katzenbeisser, I. Lagendijk and T. Toft, Privacy-preserving face recognition, in: Proceedings of International Symposium on Privacy Enhancing Technologies, Springer, (2009) , pp. 235–253. doi:10.1007/978-3-642-03168-7_14. |
[17] | D. Evans, V. Kolesnikov and M. Rosulek, A pragmatic introduction to secure multi-party computation, Found. Trends Priv. Secur. 2: (2–3) ((2018) ), 70–246. doi:10.1561/3300000019. |
[18] | R.L. Fogues, P.K. Murukannaiah, J.M. Such and M.P. Singh, Sharing policies in multiuser privacy scenarios: Incorporating context, preferences, and arguments in decision making, ACM Trans. Comput.-Hum. Interact. 24: (1) ((2017) ), 5–1529. doi:10.1145/3038920. |
[19] | M.J. Freedman, K. Nissim and B. Pinkas, Efficient private matching and set intersection, in: Advances in Cryptology, Springer, (2004) , pp. 1–19. |
[20] | M. Goldberg, How understanding relationships drives better data and analytics, 2016. |
[21] | O. Goldreich, The Foundations of Cryptography – Volume 2, Basic Applications, Cambridge University Press, (2004) . |
[22] | O. Goldreich, S. Micali and A. Wigderson, How to play any mental game or a completeness theorem for protocols with honest majority, in: Proceedings of Annual Symposium on Theory of Computing, ACM, (1987) , pp. 218–229. |
[23] | C. Hazay and M. Venkitasubramaniam, On the power of secure two-party computation, J. Cryptol. 33: (1) ((2020) ), 271–318. doi:10.1007/s00145-019-09314-2. |
[24] | D. He, J. Bu, S. Zhu, M. Yin, Y. Gao, H. Wang, S. Chan and C. Chen, Distributed privacy-preserving access control in a single-owner multi-user sensor network, in: Proceedings of INFOCOM, IEEE, (2011) , pp. 331–335. |
[25] | D. Huang, Q. Dong and Y. Zhu, Attribute-Based Encryption and Access Control, CRC Press, (2020) . |
[26] | P. Ilia, B. Carminati, E. Ferrari, P. Fragopoulou and S. Ioannidis, SAMPAC: Socially-aware collaborative multi-party access control, in: Proceedings of Conference on Data and Application Security and Privacy, ACM, (2017) , pp. 71–82. |
[27] | P. Ilia, I. Polakis, E. Athanasopoulos, F. Maggi and S. Ioannidis, Face/off: Preventing privacy leakage from photos in social networks, in: Proceedings of Conference on Computer and Communications Security, ACM, (2015) , pp. 781–792. |
[28] | Y. Ishai, E. Kushilevitz, M. Prabhakaran, A. Sahai and C.-H. Yu, Secure protocol transformations, in: Advances in Cryptology, Springer, (2016) , pp. 430–458. |
[29] | W.H. Jobe, Functional completeness and canonical forms in many-valued logics, The Journal of Symbolic Logic 27: (4) ((1962) ), 409–422. doi:10.2307/2964548. |
[30] | S. Kamara, P. Mohassel and M. Raykova, Outsourcing multi-party computation, IACR Cryptol. ePrint Arch. 2011: ((2011) ), 272. |
[31] | A. Kapadia, P.P. Tsang and S.W. Smith, Attribute-based publishing with hidden credentials and hidden policies, in: Proceedings of Annual Network and Distributed System Security Symposium, (2007) , pp. 179–192. |
[32] | M. Lepinksi, S. Micali and A. Shelat, Collusion-free protocols, in: Proceedings of Annual Symposium on Theory of Computing, ACM, (2005) , pp. 543–552. |
[33] | J. Li, N. Li and B. Ribeiro, Membership inference attacks and defenses in classification models, 2020. |
[34] | N. Li and W. Winsborough, Towards practical automated trust negotiation, in: Proceedings of International Workshop on Policies for Distributed Systems and Networks, IEEE, (2002) , pp. 92–103. |
[35] | R. Mahmudlu, J. den Hartog and N. Zannone, Data governance and transparency for collaborative systems, in: Data and Applications Security and Privacy, LNCS, Vol. 9766: , Springer, (2016) , pp. 199–216. |
[36] | P. Mohassel and Y. Zhang, SecureML: A system for scalable privacy-preserving machine learning, in: Proceedings of IEEE Symposium on Security and Privacy, IEEE, (2017) , pp. 19–38. |
[37] | C. Morisset, T.A.C. Willemse and N. Zannone, Efficient extended ABAC evaluation, in: Proceedings of Symposium on Access Control Models and Technologies, ACM, (2018) , pp. 149–160. |
[38] | C. Morisset and N. Zannone, Reduction of access control decisions, in: Proceedings of Symposium on Access Control Models and Technologies, ACM, (2014) , pp. 53–62. doi:10.1145/2613087.2613106. |
[39] | M. Naehrig, K. Lauter and V. Vaikuntanathan, Can homomorphic encryption be practical? in: Proceedings of Cloud Computing Security Workshop, ACM, (2011) , pp. 113–124. |
[40] | M. Naor and K. Nissim, Communication complexity and secure function evaluation, CoRR (2001). arXiv:cs/0109011. |
[41] | M. Nateghizad, Z. Erkin and R.L. Lagendijk, Efficient and secure equality tests, in: Proceedings of International Workshop on Information Forensics and Security, (2016) , pp. 1–6. |
[42] | M. Nateghizad, Z. Erkin and R.L. Lagendijk, An efficient privacy-preserving comparison protocol in smart metering systems, EURASIP Journal on Information Security 2016: (1) ((2016) ), 11. doi:10.1186/s13635-016-0033-4. |
[43] | T. Nishide, K. Yoneyama and K. Ohta, Attribute-based encryption with partially hidden encryptor-specified access structures, in: Proceedings of International Conference on Applied Cryptography and Network Security, Springer, (2008) , pp. 111–129. doi:10.1007/978-3-540-68914-0_7. |
[44] | OASIS, eXtensible Access Control Markup Language (XACML) Version 3.0, OASIS Standard, 2013. |
[45] | F. Paci, A.C. Squicciarini and N. Zannone, Survey on access control for community-centered collaborative systems, ACM Comput. Surv. 51: (1) ((2018) ), 6–1638. |
[46] | P. Paillier, Public-key cryptosystems based on composite degree residuosity classes, in: Proceedings of International Conference on Theory and Application of Cryptographic Techniques, Springer, (1999) , pp. 223–238. |
[47] | B. Pinkas, T. Schneider, N.P. Smart and S.C. Williams, Secure two-party computation is practical, in: Advances in Cryptology, LNCS, Vol. 5912: , Springer-Verlag, (2009) , pp. 250–267. |
[48] | S. Rajtmajer, A. Squicciarini, C. Griffin, S. Karumanchi and A. Tyagi, Constrained social-energy minimization for multi-party sharing in online social networks, in: Proceedings of International Conference on Autonomous Agents & Multiagent Systems, International Foundation for Autonomous Agents and Multiagent Systems, (2016) , pp. 680–688. |
[49] | S. Rajtmajer, A. Squicciarini, C. Griffin, S. Karumanchi and A. Tyagi, Constrained social-energy minimization for multi-party sharing in online social networks, in: Proceedings of International Conference on Autonomous Agents & Multiagent Systems, International Foundation for Autonomous Agents and Multiagent Systems, (2016) , pp. 680–688. |
[50] | A. Shamir, Identity-based cryptosystems and signature schemes, in: Advances in Cryptology, LNCS, Vol. 196: , Springer, (1985) , pp. 47–53. doi:10.1007/3-540-39568-7_5. |
[51] | M. Sheikhalishahi, G. Tillem, Z. Erkin and N. Zannone, Privacy-preserving multi-party access control, in: Proceedings of International Workshop on Privacy in the Electronic Society, ACM, (2019) . |
[52] | J.M. Such and N. Criado, Resolving multi-party privacy conflicts in social media, IEEE Transactions on Knowledge and Data Engineering 28: (7) ((2016) ), 1851–1863. doi:10.1109/TKDE.2016.2539165. |
[53] | K. Thomas, C. Grier and D.M. Nicol, UnFriendly: Multi-party privacy risks in social networks, in: Privacy Enhancing Technologies, LNCS, Vol. 6205: , Springer, (2010) , pp. 236–252. doi:10.1007/978-3-642-14527-8_14. |
[54] | D. Trivellato, N. Zannone and S. Etalle, GEM: A distributed goal evaluation algorithm for trust management, Theory and Practice of Logic Programming 14: (3) ((2014) ), 293–337. doi:10.1017/S1471068412000397. |
[55] | J.R. Troncoso-Pastoriza, S. Katzenbeisser, M.U. Celik and A.N. Lemma, A secure multidimensional point inclusion protocol, in: Proceedings of Workshop on Multimedia & Security, (2007) . |
[56] | F. Turkmen, J. den Hartog, S. Ranise and N. Zannone, Formal analysis of XACML policies using SMT, Computers & Security 66: ((2017) ), 185–203. |
[57] | A.C. Yao, Protocols for secure computations, in: Proceedings of Annual Symposium on Foundations of Computer Science, IEEE, (1982) , pp. 160–164. |
[58] | Y. Yao, N. Xiong, J.H. Park, L. Ma and J. Liu, Privacy-preserving max/min query in two-tiered wireless sensor networks, Computers & Mathematics with Applications 65: (9) ((2013) ), 1318–1325. doi:10.1016/j.camwa.2012.02.003. |
[59] | L. Yu, S.M. Motipalli, D. Lee, P. Liu, H. Xu, Q. Liu, J. Tan and B. Luo, My friend leaks my privacy: Modeling and analyzing privacy in social networks, in: Proceedings of Symposium on Access Control Models and Technologies, ACM, (2018) , pp. 93–104. |
[60] | T. Yu, M. Winslett and K.E. Seamons, Supporting structured credentials and sensitive policies through interoperable strategies for automated trust negotiation, ACM Trans. Inf. Syst. Secur. 6: (1) ((2003) ), 1–42. doi:10.1145/605434.605435. |
[61] | Y. Zhang, Q. Chen and S. Zhong, Efficient and privacy-preserving min and kth min computations in mobile sensing systems, IEEE Transactions on Dependable and Secure Computing 14: (1) ((2017) ), 9–21. |
[62] | Y. Zhang, X. Chen, J. Li, D.S. Wong and H. Li, Anonymous attribute-based encryption supporting efficient decryption test, in: Proceedings of ACM SIGSAC Symposium on Information, Computer and Communications Security, ACM, (2013) , pp. 511–516. |



