A spatially aware policy conflict resolution for information services
Abstract
A pervasive computing environment is characterized by computing capabilities and effective use of smart spaces. Many critical elements of pervasive computing, such as wireless networks are now viably commercial products. Ambient services are known as one of the main types of pervasive information services in which suitable information is presented to the users based on their surrounding geographical environments. Increase in the use of such services may cause service domain overlapping in which many of the users are located in several domains simultaneously. The aim of this paper is to present the best information service composition to such users by considering spatio-temporal contexts and analyses. User’s location, direction and speed were regarded as the most effective spatial contexts. Spatio-temporal topological relationships as well as influenceability relation were used to model the topological context. The proposed methodology was implemented in three nested service domains. Based on the results, composition of the proposed services and the period for service update were described as “good” by 75 and 80 percent of the users, respectively.
1.Introduction
A pervasive computing environment is characterized by computing capabilities and effective use of smart spaces. Many critical elements of pervasive computing such as wireless networks are now viably commercial products. Ambient services are known as one of the main types of pervasive information services in which suitable information is presented to the users based on their surrounding geographical environments as their contexts. In other words, if a person is located in a predetermined domain of a service provider, he or she can receive appropriately relevant services [17]. For each service domain, there is a physical area called “service site” where the services are accessible. It should be noted that a “service site” is different from a “service domain”.
When service domains are characterized by geographic boundaries, domain overlapping may occur; and each user may be located in several domains simultaneously. In this case, what matters is the composition of services presented to the users. For example, similar or same services may be combined, or services of a domain can be given precedence over similar services in other domains [18]. “User context” was used in previous studies conducted on providing relevant services for such users. Context is any information used to characterize the situation of an entity [1]. User context is the information received directly from the user, such as name, age, username, and password. Since in pervasive information services on which this study is focused all of the users have the same privilege, utilizing the user context seems to be unnecessary. The aim of this paper is to provide the best information services for such users by minimizing the user role in providing services. Since such services are generic, the system does not need to identify users. On the other hand, users prefer to maintain privacy in information retrieval on many applications, especially in generic services. Therefore, user-based methods in which users are required to log in seem unnecessary. It is possible to replace the user context with other contexts, such as spatial and temporal ones. A spatial context provides information on the situation of an entity such as location, direction, and speed. For example, the destination of a user can be implicitly understood from his/her movement instead of asking him/her. The advantage of using spatial relationships for providing services is that they are independent from the user context. User privacy is maintained, too.
In order to clarify the aim of this paper, the following example is presented:
“Maria is a tourist who intends to visit a national museum. The service provider of the museum presents some information services such as visiting hours, introduction to various booths, and information on the existing objects. Such information is sent to those who are moving towards the museum. In addition, there is a restaurant near the museum that provides services as well. This restaurant broadcasts its menu to the users nearby. In this scenario, when Maria is located in two areas at the same time, i.e. the museum domain and the restaurant domain, an important issue is how to decide what composition of services should be provided to her at a given time. In such situation, a conflict is more likely to occur as two domains may have many services with different policy patterns sent to Maria at the same time. A large amount of services that may confuse the user is a source of conflict. One solution for resolving this type of conflicts is using Maria’s personal information for selecting relevant services which can be directly received from herself. For instance, based upon information captured from her registration in the system (i.e. name, age, address) we can anticipate her affairs. One of the weak points of this solution that uses personal information is invasion of privacy. In this scenario, maybe Maria would not like the system to accesses to her personal information without her consent. On the other point of view, since both of the above-mentioned services are generic, receiving user profile information seems to be redundant. Given that the generic services are a main type of smart services, we must access the user preferences without her direct supervision. For this aim, we utilize spatial contexts and topological relationships to reduce user intervention in service composition. For instance, when Maria is inside the museum building, she does not need to receive restaurant services. Here, “inside” is a topological relationship that can help the system to eliminate irrelevant services of restaurant”.
The rest of the paper is organized as follows: Section 2 focuses on the works related to service composition and policy conflict resolution. Section 3 presents a new methodology for resolving conflicts in overlapped service domains by utilizing spatial contexts and analyses. Section 4 introduces the case study. Section 5 presents the results and discussions. Finally, the conclusions are provided in Section 6.
2.Related works
Service composition is the construction of complex services from primitive ones, thus enabling rapid and flexible creation of new services. Service composition is the combination of many existing services in order to carry out a larger and more complex task. There have been many published studies on service composition in recent years. For example, to find the exact optimal execution plan, Zeng et al. [30] used linear integer programming, Gao et al. [11] used dynamic programming for linear objective function, while Aiello et al. [3] applied the Backward Breadth First algorithm and Wan et al. [25] adopted an efficient divide-and-conquer approach for service selection. Gaia dealt with conflicts occurring among simultaneously triggered rules in the same application [4]. It uses priority to resolve a conflict, which means, that if there are conflicting rules, the rule with the highest priority wins.
Since the ranking of web service combinations depends on user requirements and willingness for investment of resources, Agarwal and Lamparter [2] considered user constraints and preferences for calculating the rank of a web service composition. Gamha et al. [10] presented a framework for the semantic composition of web services handling user constraints. Karakoc et al. [14] presented an approach based on constraint programming for web service composition in order to model and schedule composite web services under user constraints. Unlike most previous methods, this method does not use pre-defined rules. Lin et al. [16] introduced a fuzzy method to solve the selection of web services in a global and flexible manner. They tried to express user preferences using fuzzy expression. Mokhtar et al. [22] captured both services-related and user-related contexts enabling service composition to be effectively context-sensitive. Yu and Reiff-Marganiec [29] introduced a new concept of composition context to drive runtime service selection and composition. They tried to develop a backward composition context based service selection approach (BCCbSS) for service composition. Ying et al. [28] utilized the event-condition-action (ECA) rules to manage web service composition for multimedia conference systems in the case of updating user needs. The appropriate event will trigger when the business process request changes and allows service rescheduling. Wang et al. [26] offered a framework for dynamic complex service composition based on multi-agent reinforcement learning to obtain adaptivity in a dynamic environment.
Providing the best composition of services requires policy conflict resolution; thus, there is a trend toward resolving conflicts in the ambient intelligent systems [23]. Conflict is a natural disagreement between different attitudes, beliefs, values, or needs [27]. So far, the techniques used for policy conflict resolution have been chiefly role-based; i.e. the fixed and dynamic policies are used in order to detect and resolve conflicts [6,7]. This means that the component of policy conflict resolution can manage and resolve conflicts based on the user group (e.g., general user, power user, or super user) [17]. The conflicts can be resolved according to the role hierarchy [24]. Service presentation can be done according to the importance and priority of services [13], and it is also possible that a user is allowed to receive only the services which have already been defined by the policy author based on his/her role [12,17,23]. One of disadvantages of nearly all mentioned studies is that at first, the user is recognized by the user context (username, password, ID, etc.), and then he/she is assigned to a group. Finally, conflicts are resolved based on the user role.
Our approach differs from previous works because we focus on spatial contexts such as topological relationships. In this approach, policy conflicts can be resolved through spatial contexts and analyses without user’s direct involvement.
3.Methodology
This section presents the architecture of the system and its main components first. Then it focuses on spatio-temporal topological relationships based on influenceability regarded as the basic relation for topological context. Finally, it illustrates the spatial rules for presenting the services.
Fig. 1.
The System Architecture.
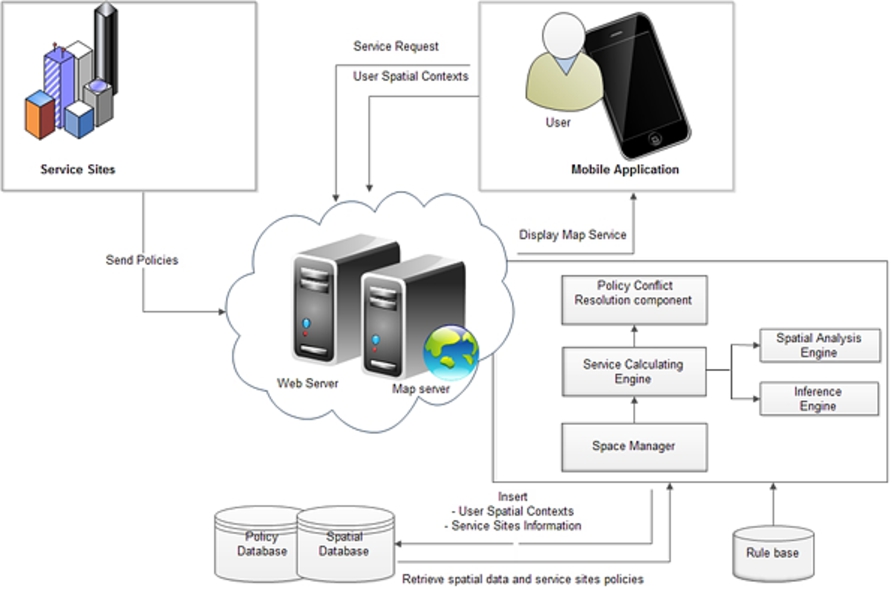
3.1.System architecture
To illustrate a possible implementation of the proposed model, we outline the architecture and key components of our system. The main components of the proposed system are users, service sites, and server center, as illustrated in Fig. 1. The Figure uses arrows to represent the actions by the source component on the destination component.
Users: In this paper, those users located in the multiple domains, briefly called “the users”. In our system, user’s spatial contexts such as location, speed, and direction are obtained via a GPS system. The spatial contexts are sent to the server using a mobile application that installed in the mobile device of the user and the sets of services from the server are received and displayed to the user on the map.
Service sites: These are the next component of the system. Each service site has its own unique policies and sends its information to the server center in four levels with different levels of importance and details. Accordingly, they are ranked from 1 to 4. Determining the importance of the levels depends on the service site policies. This information helps the server center make decisions in different situations. In addition, the information on the working time of service sites is sent to the server. If a user is located in a joint area, the server will ignore non-active service sites.
The server center: It is responsible for calculating services, resolving policy conflicts, and managing the system in general. It consists of four subcomponents, including a spatial database, a policy database, a rule base, and a server. The spatial database is a database repository that stores the user spatial contexts and the details about service sites information. The policy database is a storage component that stores the policies for each service site. The services and their importance are determined by the policy. For example, we can have a policy such as “When the service site is the stadium, the importance of an information service such as the list of the association football competitions is more than the parking map service”. The rule base is a place in which all of the instructions are stored. These rules determine what is and what is not allowed in different situations.
The server itself contains a space manager, a Service Calculation Engine (SCE) and a policy conflict resolution component. Space manager is the main component that is responsible for discovering new users entering the space (overlapped domain) and users leaving the space. When the user enters the space, the space manager initiates a new connection with the client and sends relevant information to that particular client. After that, user’s current contexts are periodically sent to the SCE to calculate which service domains the user is currently in and the composition of services available to each user. Calculations of SCE are done in two engines including spatial analysis engine and inference engine. Creating users models and service sites models as well as determining topological relationships, perform in spatial analysis engine. Inference engine calculates appropriate service composition using rules defined in rule base. The policy conflict resolution component handles conflicts between entities in the system, if any. Since in context of information services, all of users and service sites have the same importance, then policy conflict resolution component, combine the rules from each service site involved in the policy conflict.
3.2.Effective contexts
User location is known as the main spatial context in an ambient service to provide the most relevant responses to user requirements. Users in different locations have different needs and preferences. Consequently, they should receive different combinations of services. In conflict resolution methods, when a user is located in multiple domains, based on the user context and role (e.g. group), he/she can receive “fixed” and “predetermined” services. The aim of this study is to increase privileges of service sites near the user location. Direction of the user movement is another effective context in providing services. The most important reason to regard this criterion as a spatial context is that it can lead to the destination of the user. When a user moves toward a certain service site, it means that he/she needs the services of that site. Consequently, he/she will receive the information relevant to his/her situation.
Speed context is the last effective context in this regard. For two users who are both moving towards the same service site, the time of sending service and details of information will be different. A faster user has less time to receive massive information. Hence, the information should be sent to him/her sooner and in fewer details.
3.3.Topological relationships between users and service sites
A topological relationship is a type of relationship in the space that describes our qualitative relationships with objects in an environment. Our requirement of objects can be a function of such relationships. In other words, we need the objects to which we are more related more than the objects to which we are less related. For instance, we need the services of a store more when we are near it in comparison with the time when we are far from it. Put another way, our requirements of nearby services change according to these relationships. In order to provide a suitable service composition for the user, it is necessary to consider his/her topological relationships with the service sites. Thus, spatio-temporal topological relationships were used in this study. In general, there are two viewpoints in topological relations, named point-set topology [8] and pointless topology [15]. In this paper, an influenceability relation used for modeling the pointless topology.
The spatial casual relation is also called influenceability. It means that objects are in contact with each other and influence other objects [19]. As an example, a moving car influences surrounding objects. An influenceability relation does not coincide with connection relation.
The influenceability relation, symbolized by ≺ is an order and primitive relation which is also an irreflexive, antisymmetric, but transitive relation.
Let
As a reflexive and symmetric relation [5] for two objects x and y, connection can be defined by influenceability:
3.3.1.Spatio-temporal topological relationships
It is assumed that the user and service site are two regions in our model. TPP or NTPP are considered for a user who is located “inside” the service site and DC relation is considered for a user “outside” it. The users who are located inside the service sites will receive all the services (level 1). The other spatio-temporal analyses are “entering” and “leaving” the service site. The users who enter a service site have the highest priority to receive relevant services. Conversely, presenting services to those who are leaving the service site seems to be unnecessary.
As in a similar study [9] for a point-based view, other definitions can be presented for region objects. The following relations can be proposed for entering and leaving the service site:
3.3.2.Influenceability relation modeling
In order to study influenceability relations, the first step is to model the effective objects, such as a user and a service site. The user model in a space-time framework is like a spatio-temporal cone. The spatio-temporal cone can be used as a mobile agent (in a fixed period of time) in pervasive environments [21]. The idea of spatio-temporal cone is borrowed from the light cone in relativity physics. It means that, the mobile agent can travel in the cone because of its speed [20]. The spatio-temporal cone can be defined as a portion of space-time containing all locations which mobile agent can reach from a particular location [20]. The apex of this cone is a user’s current location reported by a navigation system. The period will be defined by the user or the system. With respect to a given event, spatio-temporal cone separates space-time into three parts, inside and on the future spatio-temporal cone, inside and on the past spatio-temporal cone, and elsewhere [21]. In this paper, the focus is on the future part of this cone, because we want to present services in the near future.
Since in the real world, the user can be located just in the space ahead, then the direction of the user movement is applied to prepare the user model. The service site model is a cube (Fig. 2(a)). After the time interval
Fig. 2.
Influenceability of the User and the Service Site Models: (a) In a spatio-temporal framework. (b) At the time t and applying the direction of movement.
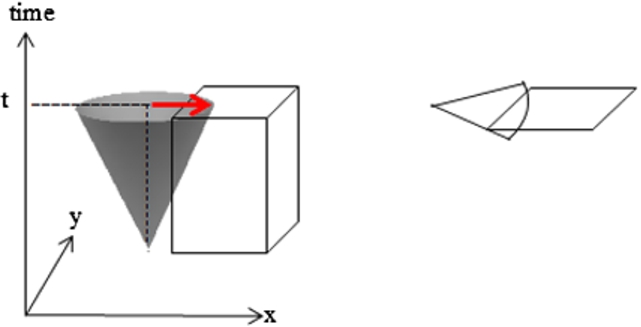
After modeling the objects, the topological relationships are investigated using the influenceability relation. By considering x and y as a user and a service site respectively, the relations indicated in Table 1 express the influence of the user on the service site. If a user influences the service site, its services are in priority to be sent to him/her. Moreover, if a user influences several service sites, then the priority will be allocated to the site which was influenced the most.
Table 1
The Relations Extracted from the Influenceability Relation
| Category | Logical relation |
| Externally Connection | |
| Partially Overlap | |
| Tangential Proper Part | |
| Non Tangential Proper Part |
3.4.The rule base
In order to provide spatially service compositions for the users, six key rules are described in Table 2. The rules are defined as if-then rules, i.e.
If there are … criteria for the user, then the system will send … services to him/her
Table 2
The Rule Base
| If-then | Description | |
| Rule 1 | If the user locates (staying or moving) inside the service site, then priority of the service site is in the level 1. | If some service sites locate in the level 1, then the union of their services will be presented. |
| Rule 2 | If the user enters to the service site after the time | If some service sites locate in the level 2, then the union of their services will be presented. |
| Rule 3 | If the user moves toward the service site and effects on, but doesn’t enter it, then priority of the service site is in the level 3. | If some service sites locate in the level 3, then the site which is most influence is in priority. |
| Rule 4 | If the user moves toward the service site and doesn’t effect on it and doesn’t enter it, then priority of the service site is in level 4. | If some service sites locate in the level 4, then the union of their services will be presented. |
| Rule 5 | If the user leaves the service site, then the services of that site will not be presented. | – |
| Rule 6 | If the user stays out of the service site or his/her speed is near zero, then services of that site will not be presented. | – |
As it can be seen in Table 2, the services will be presented in four levels. Level 1 and level 4 have the most and least priorities, respectively. The information of higher levels has priority over the other ones and will be sent sooner.
Finally, the inference engine selects the suitable rule in different situations based on the rules in the rule base and data obtained (i.e., current location, direction and speed) by tracking users and information obtained (i.e., categorized information and working time) from the service sites.
To illustrate the concept of these rules, we define various scenarios as follows:
1. The customers shopping inside a store would receive the information only related to the same store, whereas there might be some information services of the university being broadcasted near that store.
2. The users entering a stadium would receive the information related to the sport event only, whereas there might be some services around the stadium regarding restaurants, hotels, public transportation, etc.
3. A tourist moving towards a museum is only interested in receiving information on that particular place, whereas there might be a store near the museum providing services as well.
4. The users who were exiting a store would not need to receive services from that store any more.
4.Case study
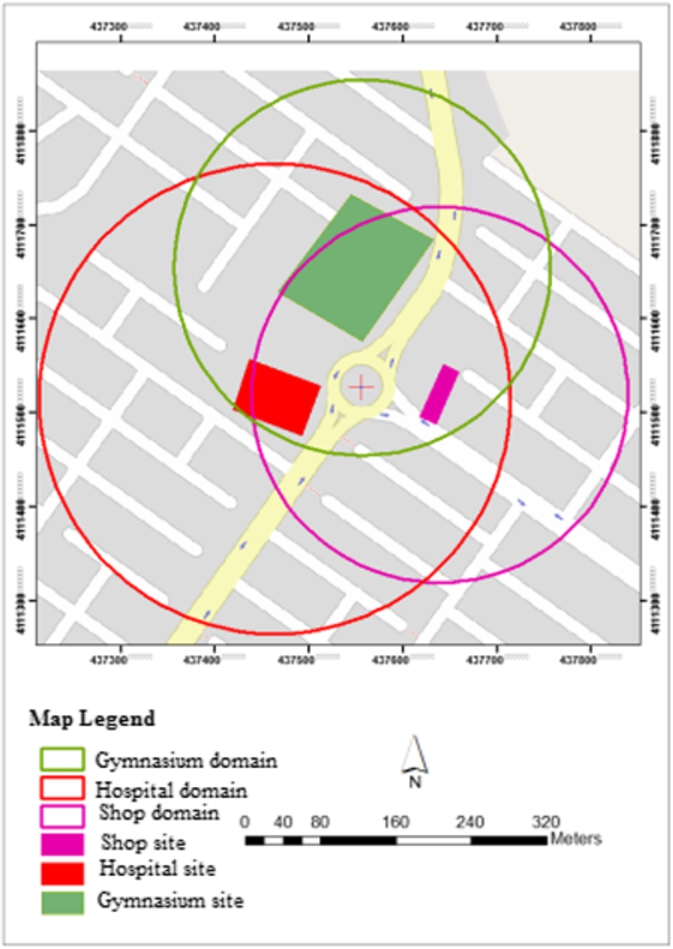
In order to implement the proposed approach, an area was considered consisting three nested domains. The first domain sends information services to the users within a 250-meter radius of a hospital. The second domain sends advertising information including sports fields, class times, and competition dates to the users within a 200-meter radius of a gymnasium located near the hospital. The third domain belongs to a shop near the last two domains. In this domain, the information regarding electronic devices, home appliances, sales, and the bestselling products will be sent to the users within a 200-meter radius of the shop (Fig. 3).
Fig. 3.
Service Sites and Service Domains in the Case Study.
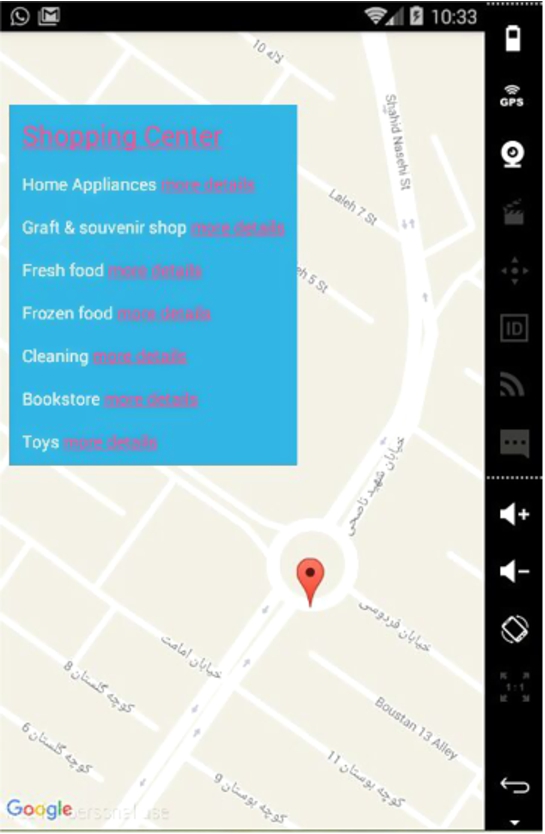
After collecting the data derived by tracking the users by GPS, the server analyzes the topological relationships between the user and the service sites. Furthermore, Android simulator was employed to present services on the user device. A sample output will be something similar to the illustration in Fig. 4.
Fig. 4.
A Sample of the Output.
Now the system performance in different spatial contexts is explained in two scenarios meant consider the important situations.
Scenario 1
A user located in (437549, 4111494) UTM 39S as the start point moves towards the shop at an average speed of 1.1 m/s and in an approximate direction of 10 degrees (Fig. 5). As it can be seen in this figure, in spite of going towards the shop site, the user has no effects on it. Since the shop is active in the time of tracking, the system will present the information to the user in level 4.
Fig. 5.
The Output on the User Device.
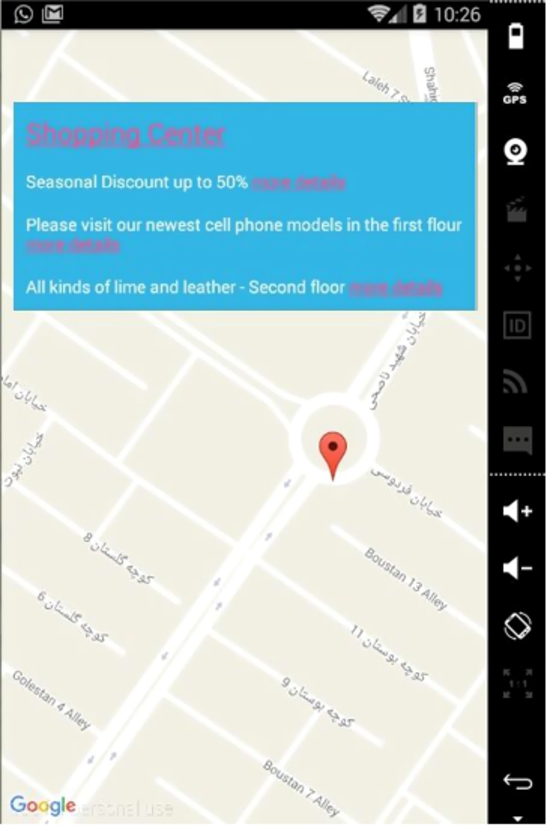
Fig. 6.
The Output on the User Device.
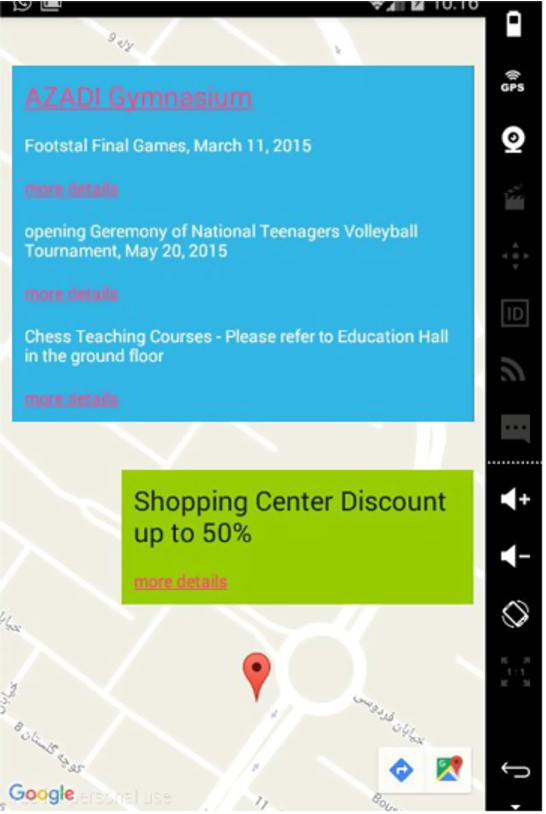
Table 3
The Implementation Results of the Proposed Approach
| Destination | User favorite service | Proposed service | User satisfaction level |
| Moving toward the shop | The shop services | The shop services in (level 4) | Good |
| Entering the hospital | The hospital services | The hospital services in (level 2) | Good |
| Leaving the gymnasium | Don’t receive gymnasium services | The shop services and the hospital services in (level 2) | Average |
| Moving toward the gymnasium and influencing on it | The gymnasium services | The gymnasium services in (level 3) | Good |
| Leaving the shop | Don’t receive the shop services | – | Good |
| Inside the gymnasium | The gymnasium services | The gymnasium services in (level 1) | Good |
| Outside of the service site (the user speed about zero) | – | – | Weak |
Scenario 2
A user located in (437500, 4111502) UTM 39S as the start point, leaves the hospital at an average speed of 1.6 m/s and in an approximate direction of 40 degrees (Fig. 6). In this case, the system does not send the hospital information to the user; however, it sends services of the shop and the gymnasium in level 4. Since the user had declared that he was just willing to receive the gymnasium information, sending the information of the shop is not pleasant to him. When tracking continued and the user got closer to the gymnasium, its information was in priority, and the user was more satisfied with the result.
5.Results and discussions
In this paper, user studies are employed to evaluate recommender systems from a user’s perspective. For this purpose, 40 individuals were asked to move toward their favorite service sites in the multiple domains and select their favorite service sites. Figure 7 shows a sample of user interaction with the system.
Fig. 7.
Selecting Favorite Service Sites by a User.
Fig. 8.
The Users Satisfaction Levels for the Proposed Services.
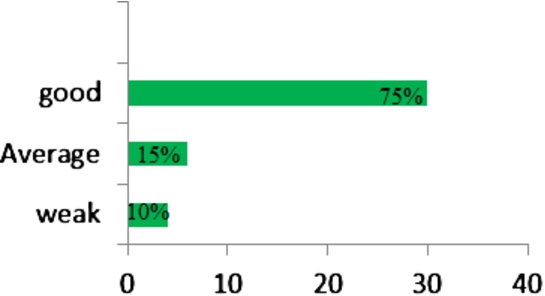
Finally, according to the surveyed test users, their satisfaction levels were described in three categories as good, average, and weak concerning to the presented services. For example, the users in Scenarios 1 and 2 declared that the proposed services were good and average, respectively. The results are shown in Table 3. Based on the results, 75% of the participants were satisfied with the services and described them as good level (Fig. 8).
User satisfaction depends on receiving services at the right time. In this study, because data were collected by spatial sensors, it is faster than the methods based on receiving data from the users (e.g. user context). Therefore, the services are updated at an acceptable time.
The total time required to discover and update the relevant services for a user by the proposed system is as follows:
The updating time for the same system based on the user context is as follows:
As it can be seen in the second method, the times
Fig. 9.
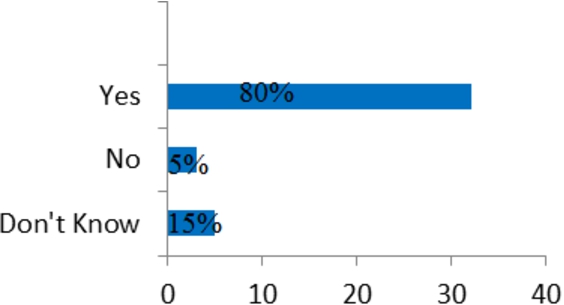
Users Satisfaction Levels for Service Updating Time.
Furthermore, an experiment was conducted to prove that the topological relationships could be regarded as one of the criteria for providing services. For this purpose, the services are provided both with and without considering topological relationships. Then, the mean absolute error (MAE) is taken to measure the error range between the prediction preference value and true preference value. MAE is a commonly used quantity to measure how close forecasts or predictions are to the eventual outcomes. Then MAE was calculated through the following equation:
In order to provide the actual value, participants are asked to rate each service based on their own preference. In this way, 1 is the least favorite, and 5 is the most favorite. The results are shown in Fig. 10.
Fig. 10.
Comparing MAE with and without Considering Topological Relationships.
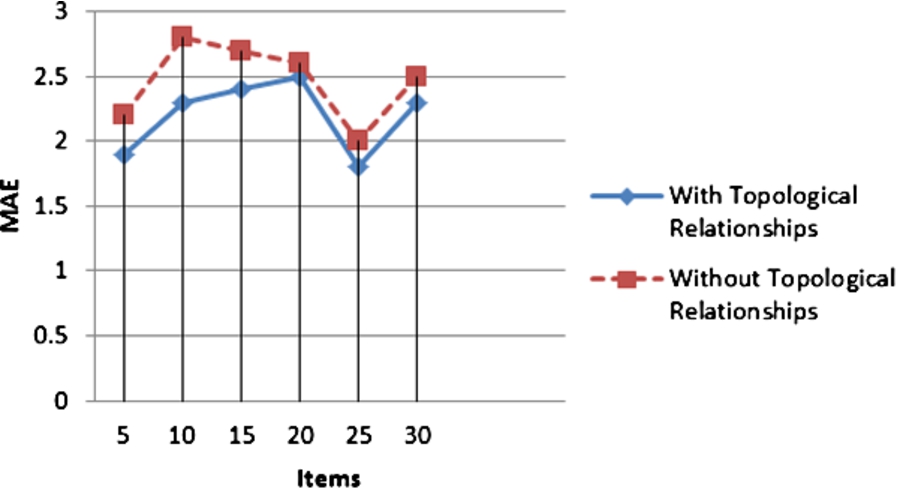
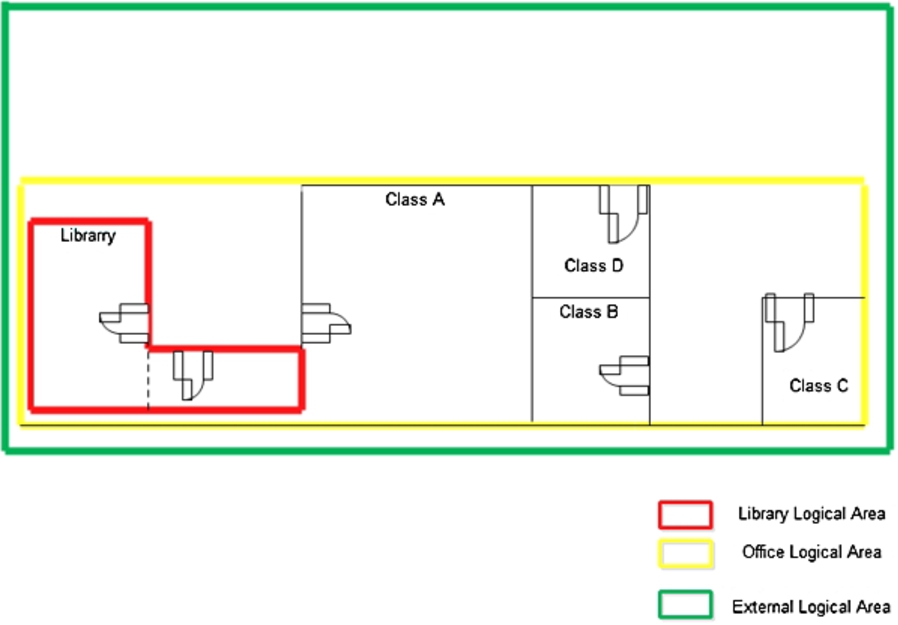
Fig. 11.
A Building Floor at the University Campus.
This comparison confirmed our reasoning to the use of topological relationships. The results indicate that topological relationships can be significantly effective in providing users with services, especially in a mobile environment with respect to continuous changes in spatial relationships between users and objects.
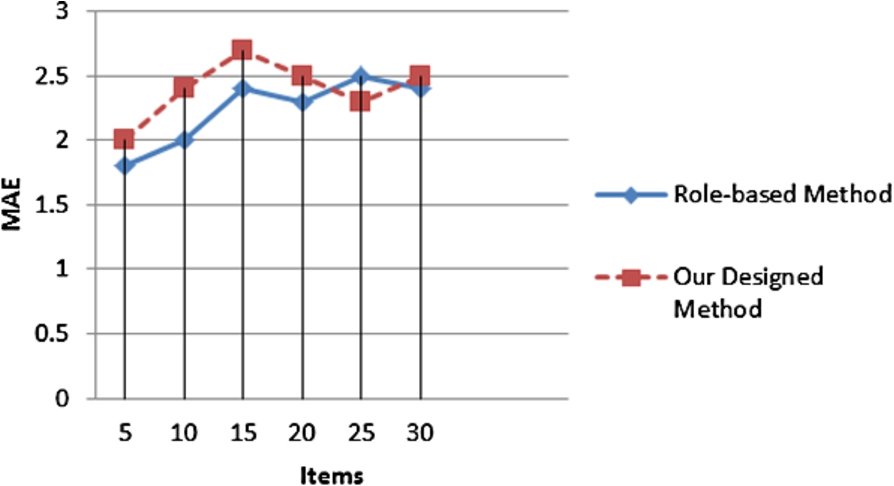
To evaluate the performance of the proposed method, the results are compared with traditional role-based service composition in [18]. The services provided in the current study are generic; however, the services provided in [18] were role-based. In generic services, either no roles are defined, or all of the roles are equally important to the service provider. To compare the two methods, we assume that all of the services are of the same priorities. To do this, we define three logical areas; i.e. Office Logical Area, External Logical Area, and Library Logical Area in a floor area of a section of K.N.Toosi University campus (Fig. 11). Experiments are carried out in both spatial and role-based modes. According to [18], users were divided into three groups (Student, Lecturer, and Administrator). The tables of rules were also taken into account. In this method, users were first asked to log in to the system; so that they could be identified. In the other method, the tables of rules were defined according to the spatial relationships proposed in our study. In this case, users were not required to log in to the system. Then MAE was calculated for them. The result is shown in Fig. 12.
Compared with the role-based method, the proposed method may be a little inaccurate. One reason is that this study is concentrated on information services; however, the services defined in [18] are role-based. It is obvious that if we have more information than users do, the results will be more accurate. Since the results were obtained without needing to log in to the system, and they were simply based on spatial information, the accuracy is acceptable. The main advantage of the proposed method over the role-based method is that it can support mobility, too, because of considering spatial relationships, especially topological relationships. However, such a problem was not considered in [18]. For instance, the proposed method does not send library services to a student who intends to exit the library. However, the method used in [18] sends library services until the user position is not entirely outside the library logical area. This is because this method does not consider user direction and topological relationships.
Fig. 12.
Comparison MAE.
6.Conclusion
Due to the variety of ambient services, they have attracted a great deal of public attention in recent years. Due to domain overlapping, the number of users located in multiple domains is increasing. The important issue about these users is deciding upon the services which should be sent to them. In this study, the spatial contexts and analyses such as spatial topological relationships between the users and service sites were used in the policy conflict resolution. Moreover, spatio-temporal topological relationships and the influenceability relation were utilized in order to model the topological context. Based on the results, 75% of the users were satisfied with the provided services, something which indicates an acceptable performance of the proposed approach in utilizing spatial contexts and analyses.
Another advantage of the proposed approach is using spatial sensors instead of the user contexts. Using spatial sensors makes the system independent from the user. It means that eliminating the time of sending and receiving contextual information between the server and the user will reduce the time of updating the services. In addition, the spatial sensors are easily available and do not impose an overhead time on the system. Time saving is an important advantage of the system, because inappropriate time of updating services will cause conflicts for the users. The results also indicate that 80% of the users were content with the updating time of the services.
References
[1] | G.D. Abowd, A.K. Dey, P.J. Brown, N. Davies, M. Smith and P. Steggles, Towards a better understanding of context and context-awareness, in: Proceeding HUC ’99 Proceedings of the 1st International Symposium on Handheld and Ubiquitous Computing, (1999) , pp. 304–307. doi:10.1007/3-540-48157-5_29. |
[2] | S. Agarwal and S. Lamparter, User preference based automated selection of web service compositions, in: ICSOC Workshop on Dynamic Web Processes, (2005) , pp. 1–12. |
[3] | M. Aiello, E. el Khoury, A. Lazovik and P. Ratelband, Optimal QoS-aware web service composition, in: 2009 IEEE Conference on Commerce and Enterprise Computing, (2009) , pp. 491–494. doi:10.1109/CEC.2009.63. |
[4] | J. Chomicki, J. Lobo and S. Naqvi, Conflict resolution using logic programming, IEEE Transactions on Knowledge and Data Engineering 15: (1) ((2003) ), 244–249. doi:10.1109/TKDE.2003.1161596. |
[5] | A.G. Cohn and J. Renz, Qualitative spatial representation and reasoning, Foundations of Artificial Intelligence 3: ((2008) ), 551–596. doi:10.1016/S1574-6526(07)03013-1. |
[6] | N. Dunlop, J. Indulska and K. Raymond, Dynamic policy model for large evolving enterprises, in: Proceedings Fifth IEEE International Enterprise Distributed Object Computing Conference, (2001) , pp. 193–197. doi:10.1109/EDOC.2001.950439. |
[7] | N. Dunlop, J. Indulska and K. Raymond, Methods for conflict resolution in policy-based management systems, in: Proceeding EDOC ’03 Proceedings of the 7th International Conference on Enterprise Distributed Object Computing, (2003) , pp. 98–109. |
[8] | M.J. Egenhofer and J. Herring, Categorizing binary topological relations between regions, lines, and points in geographic databases, The 9: ((1990) ), 94–1. |
[9] | M. Erwig and M. Schneider, Visual specification of spatio-temporal developments, in: Proceedings 1999 IEEE Symposium on Visual Languages, (1999) , p. 187. doi:10.1109/VL.1999.795895. |
[10] | Y. Gamha, N. Bennacer, G. Naquet, B. Ayeb and L.B. Romdhane, A framework for the semantic composition of web services handling user constraints, in: 2008 IEEE International Conference on Web Services, (2008) , pp. 228–237. doi:10.1109/ICWS.2008.78. |
[11] | Y. Gao, J. Na, B. Zhang, L. Yang and Q. Gong, Optimal web services selection using dynamic programming, in: 11th IEEE Symposium on Computers and Communications (ISCC’06), (2006) , pp. 365–370. |
[12] | Z.C. Johanyák, D. Tikk, S. Kovács and K.W. Wong, Fuzzy rule interpolation Matlab toolbox-FRI toolbox, in: 2006 IEEE International Conference on Fuzzy Systems, (2006) , pp. 351–357. doi:10.1109/FUZZY.2006.1681736. |
[13] | L. Kagal, T. Finin and A. Joshi, A policy language for a pervasive computing environment, in: Proceedings POLICY 2003. IEEE 4th International Workshop on Policies for Distributed Systems and Networks, (2003) , pp. 63–74. doi:10.1109/POLICY.2003.1206958. |
[14] | E. Karakoc and P. Senkul, Composing semantic Web services under constraints, Expert Systems with Applications 36: (8) ((2009) ), 11021–11029. doi:10.1016/j.eswa.2009.02.098. |
[15] | S. Li and M. Ying, Region connection calculus: Its models and composition table, Artificial Intelligence 145: (1) ((2003) ), 121–146. doi:10.1016/S0004-3702(02)00372-7. |
[16] | M. Lin, J. Xie, H. Guo and H. Wang, Solving QoS-driven web service dynamic composition as fuzzy constraint satisfaction, in: 2005 IEEE International Conference on e-Technology, e-Commerce and e-Service, (2005) , pp. 9–14. |
[17] | S. Loke, Context-Aware Pervasive Systems: Architectures for a New Breed of Applications, CRC Press, (2006) . |
[18] | S.W. Loke, S. Krishnaswamy and T.T. Naing, Service domains for ambient services: Concept and experimentation, Mobile Networks and Applications 10: (4) ((2005) ), 395–404. doi:10.1007/s11036-005-1553-1. |
[19] | M.R. Malek, A logic-based framework for qualitative spatial reasoning in mobile GIS environment, Lecture Notes in Artificial Intelligence 3066: ((2004) ), 418–426. |
[20] | M.R. Malek, M.R. Delavar and S. Aliabady, A Mobile Computing Framework for Navigation Tasks: INTECH, Open Access Publisher, (2008) . |
[21] | M.R. Malek and A.U. Frank, A mobile computing approach for navigation purposes, in: Proceeding W2GIS’06 Proceedings of the 6th International Conference on Web and Wireless Geographical Information Systems, (2006) , pp. 123–134. doi:10.1007/11935148_12. |
[22] | S.B. Mokhtar, D. Fournier, N. Georgantas and V. Issarny, Context-aware service composition in pervasive computing environments, in: Rapid Integration of Software Engineering Techniques, Second International Workshop: RISE 2005, (2005) , pp. 129–144. |
[23] | S. Resendes, P. Carreira and A.C. Santos, Conflict detection and resolution in home and building automation systems: A literature review, Journal of Ambient Intelligence and Humanized Computing 5: (5) ((2014) ), 699–715. doi:10.1007/s12652-013-0184-9. |
[24] | G. Rossi, S. Gordillo and A. Fortier, Seamless engineering of location-aware services, in: Proceeding OTM’05 Proceedings of the 2005 OTM Confederated International Conference on On the Move to Meaningful Internet Systems, (2005) , pp. 176–185. |
[25] | C. Wan, C. Ullrich, L. Chen, R. Huang, J. Luo and Z. Shi, On solving QoS-aware service selection problem with service composition, in: 2008 Seventh International Conference on Grid and Cooperative Computing, (2008) , pp. 467–474. doi:10.1109/GCC.2008.75. |
[26] | H. Wang, X. Wang, X. Zhang, Q. Yu and X. Hu, Effective service composition using multi-agent reinforcement learning, Knowledge-Based Systems 92: ((2016) ), 151–168. doi:10.1016/j.knosys.2015.10.022. |
[27] | W. Wang and S. Ting, Development of a computational simulation model for conflict management in team building, International Journal of Engineering Business Management 3: (2) ((2011) ), 9–15. |
[28] | Z. Ying, C. Junliang, C. Bo and Z. Yang, Using ECA rules to manage web service composition for multimedia conference system, in: 2009 2nd IEEE International Conference on Broadband Network & Multimedia Technology, (2009) , pp. 545–549. doi:10.1109/ICBNMT.2009.5347856. |
[29] | H.Q. Yu and S. Reiff-Marganiec, A backwards composition context based service selection approach for service composition, in: 2009 IEEE International Conference on Services Computing, (2009) , pp. 419–426. doi:10.1109/SCC.2009.25. |
[30] | L. Zeng, B. Benatallah, A.H. Ngu, M. Dumas, J. Kalagnanam and H. Chang, Qos-aware middleware for web services composition, IEEE Transactions on software engineering 30: (5) ((2004) ), 311–327. doi:10.1109/TSE.2004.11. |



