Same but Different? Developmental Pathways to Demonstrative Targeted Attacks — Qualitative Case Analyses of Adolescent and Young Adult Perpetrators of Targeted School Attacks and Jihadi Terrorist Attacks in Germany
Abstract
Analysis of incidents over the past ten years in Germany reveals that the boundaries between targeted attacks in schools and terrorist attacks are starting to blur. Böckler, Leuschner, Roth, Zick, and Scheithauer (2018) recently presented a set of hypotheses about similarities between the developmental pathways of school attackers and lone actor terrorists. To date there is only a small body of empirical research comparing these two forms of targeted violence in depth. In order to fill this gap, this article presents findings from a qualitative analysis of prosecution files comparing the developmental pathways of German school attackers (N = 7; age range: 13 to 23) and Jihadi attackers (N = 7; age range: 21 to 28 years) who committed their attacks between 2000 and 2013. Using theoretical coding and constant case comparison, the contribution shows that the two phenomena have overlaps in which developmental processes and social mechanisms are similar. Both school attackers and Jihadi attackers frame their act of violence using cultural scripts and perform the attack on a public stage where victims are attacked not on the basis of personal conflicts but because of their symbolic meaning. Taking into account the similarities in the perpetrators’ developmental pathways, the authors propose that it might be more fruitful from an operational perspective to discuss severe target school violence and terrorist attacks under a common concept of demonstrative violence than to artificially assign them to exclusive classes of violence.
Incidents of severe targeted school violence and terrorist attacks are usually considered as distinct social phenomena, although no clear and unequivocal definitions have been formulated for either. Severe targeted school violence is generally understood as targeted attacks committed by (former) school students, where the school is deliberately selected as the location and lethal weapons are used with the intention to kill (e.g. Bondü, Cornell, & Scheithauer, 2011; Bondü & Scheithauer, 2014a). While these incidents are driven by personal motives associated with the school context and usually understood as personal revenge for experiences of humiliation (for example Vossekuil, Fein, Reddy, Borum, & Modzeleski, 2002), terrorist attacks are normally defined as acts of violence directed against a political or societal order (Crenshaw, 2001). Terrorism is always embedded within a communication strategy designed to have far-reaching psychological effects beyond the immediate victim(s), namely by generating public fear within a wider audience. The addressees might be a rival ethnic or religious group, an entire country, a national government, a political party, or public opinion in general (Hoffman, 2006). Hence, terrorism is defined as “asymmetrical deployment of threats and violence against enemies using means that fall outside the forms of political struggle routinely operating within some current regime.” (Tilly, 2004, p. 5).
According to the current state of research (Newman, Fox, Harding, Mehta, & Roth, 2004), differences between severe targeted school violence and terrorist attacks are found in the locations targeted (schools vs. public places), and above all in the motives: tending to be personal in the case of rampage school attackers, political/ideological or religious in the case of extremist or terrorist violence. Additionally, the two phenomena are investigated within different research traditions, exhibiting few points of contact to date.
However, several incidents that have occurred over the past ten years in Europe appear to combine elements of both severe targeted school violence and terrorism. One example is the case of Pekka A., who killed eight people and himself in a school in Jokela, Finland, on November 7, 2007. A media portfolio prepared beforehand included the following statement: “Attack Type: Mass murder, political terrorism (although I chose the school as a target, my motives for the attack are political and much, much deeper and therefore I don’t want this to be called a ‘school shooting’)” (Pekka A., in Oksanen, Nurmi, Vuori, & Räsänen, 2013). Before the attack, Pekka A. had pursued an intense interest in right-wing extremist violence (ibid.). Another relevant case is the Oslo/Utøya attack in 2011, which was characterized by elements of an extremist motivated attack. In their study of the writings of the attacker, Anders B., Sandberg, Oksanen, Berntzen, and Kiilakoski (2014) demonstrate that the attacker was not only influenced by the rhetoric of right-wing Islamophobic groups, but also by the cultural script of school shootings. In advance of the attack, B. withdrew almost completely and restricted his social life to the online context. His preparations for the attacks were comprehensive, drafting numerous statements justifying his actions and presenting himself as the defender of European culture. The modus operandi of his attack at the Workers’ Youth League summer camp on the island of Utøya also showed strong parallels to school shooting cases.
Similarly, in the 2016 attack on the Olympia shopping mall in Munich, Germany, elements typically discussed in connection with severe targeted school violence can be identified (shooting attack on young people by a lone perpetrator, reading of Peter Langman’s Why Kids Kill), as well as features of a right-wing extremist attack (only migrant victims, political message: “wipe out Turks”). The classification of this attack remains politically contested in Germany. While politicians and law enforcement agencies categorize the attack as a rampage shooting, researchers tend to classify it as a case of lone wolf terrorism (Hartleb, 2017). In the past ten years there have also been cases with an Islamist background combining elements of rampage shootings and terrorist attacks. Examples of such incidents in Germany would include the attacks at Frankfurt Airport in 2011 (Böckler, Hoffmann, & Zick, 2015), Würzburg (Meloy & Pollard, 2017), and Ansbach in 2016 (Eddy, 2016).
The occurrence of cases including elements from both phenomena is not surprising, considering the observable changes in terrorist strategies over the past twenty years. For example, in the field of right-wing extremism, American racists Tom Metzger and Alex Curtis propagated “leaderless resistance” as a white resistance strategy in the late 1990s (Borum, Fein, & Vossekuil, 2012; COT, 2007). Similarly, tendencies of individualization of terrorist strategies are also observable in the field of Jihadist terrorism since al-Qaeda called on followers to engage in leaderless or individual jihad (Sageman, 2008). A number of terrorist attacks in the style of a rampage killing by individual perpetrators or small groups later followed such recommendations.
On the other side, cases like the Jokela school shooting demonstrate that at least sometimes a young person committing a targeted attack in a school intended to send a political message and had an affinity to terrorism. Malkki (2014), focusing on the presence of political elements in school shootings, distinguishes three types: Cases with explicit political communication by the perpetrator(s) (type 1), cases in which the perpetrator(s) made references to earlier attackers (type 2), and isolated cases in which the perpetrators made no references at all (type 3). In terms of the motivational structure, type 1 and type 2 appear most comparable with acts of terrorism. As in the field of terrorism, perpetrators of targeted school violence have also influenced a wider audience. Larkin (2009) demonstrates how the school shooting at Columbine High on April 20, 1999, in particular, created a cultural script for later school attacks. Columbine High stood out from other incidents of targeted violence in schools, in the sense that both perpetrators regarded it as a subversive act of political violence in the name of all who experience social repression at school (“revolution of the dispossessed”).
This growing phenomenon of combination of elements of terrorist attack and targeted school attack has initiated a discussion concerning the similarities, with a growing number of comparative studies. Lankford and Hakim (2011) compared American school shooters with Palestinian suicide bombers and found strong parallels in terms of psychological constitution and motivation. The perpetrators in their study share many characteristics in common, such as a highly troubled childhood, social deprivation, and low self-esteem. In both cases, personal crises represent the starting point for the turn to violence, with the underlying motives of avenging injustice and acquiring fame and repute. The study builds on the observation that both groups are homicidal-suicidal. Lankford and Hakim criticize the widespread dichotomy that regards school shooters as psychologically unstable, suicide bombers as extremist but rational. According to their findings, the differences between the two groups are cultural rather than personal in nature. Similar results are found by McCauley, Moskalenko, and Van Son (2013) in their comparative analysis of school shooters and politically motivated attackers: in both cases the perpetrators planned their actions in advance, usually acted alone, and drew their motivation more from emotional/social than material or instrumental needs; biographies in both groups are characterized by depression, despair, and suicidal tendencies. Significant differences exist only in relation to age and marital status: Politically motivated attackers are considerably older and more likely to be married.
Capellan (2015) compared ideological and non-ideological active shooter events in the United States between 1970 und 2014, finding similarities in the demographic and personal profiles, but significant behavioral differences between non-ideological and ideological motivated perpetrators. Capellan’s empirical findings indicate that ideological shooters act more methodically and show higher levels of sophisticated planning, have experienced some kind of military training, and use a greater number of firearms. But for the most part the shooters in both groups were white males in their thirties with dysfunctional adult lives, single or divorced, with lower levels of education and a history of mental illness. Capellan argues that the reason for these similarities is that – whether ideological or non-ideological – shooters were driven by both personal frustrations and aversion towards society, interpreting the two phenomena as subgroups of a homicide type that he calls “lone actor grievance fueled-violence.”
Liem, Van Buuren, De Roy van Zuijdewijn, Schönberger, and Bakker (2018) compared characteristics of lone actor terrorists in Europe in the period 2000–2016 with “ordinary” homicide offenders. The demographics and perpetrator profiles led this group of authors to nearly the same conclusions as Capellan, with the difference that the ideologically motivated perpetrators exhibited higher levels of education than the “ordinary” homicide offenders. It is also noteworthy that ideological lone actors were not usually socially isolated, and operated in dyads and triads more often than “ordinary” homicide offenders, who usually acted alone.
Böckler, Roth, Stetten, and Zick (2014) argued that besides being risky for development, violent behavior is also – temporarily – highly functional and productive for the psychosocial wellbeing of the perpetrator. In order to gain a deeper understanding of the developmental pathways towards school shootings and terrorist attacks, and to comprehend individual motivations, we have to move beyond the mere accumulation of empirical findings. What is needed is a theoretical point of reference that provides some guidance for interpretation and facilitates the important progression from description to explanation. Böckler et al. (2014) point out that – along with the push factors generating pressure to cope with intrapersonal tensions – it is important to look at the pull factors and relational dynamics that make a specific action attractive. From a social psychological point of view, we must therefore also consider (radicalizing) contexts in which narratives and scripts supporting violence are disseminated, and the question of how these contexts are adopted by the perpetrators. This perspective is also reflected in several works focusing on the question of how lonely a lone wolf really is. Borum et al., (2012) note that cases in which the perpetrator plans an attack completely without outside influence, encouragement or inspiration are very rare. In this context van Buuren (2012) points out that also most lone actor terrorists understand themselves as part of a broader community, while virtual spaces, especially social media, often function as a surrogate for offline social networks.
Demonstrative Targeted Violence: A Sensitive Concept
Böckler and colleagues (2018) recently introduced the concept of demonstrative targeted violence to describe the overlap between severe targeted school attacks and terrorist violence. While demonstrative targeted violence generally occurs in a public space, the victims are selected for their symbolic significance to the perpetrator. According to Leuschner (2013) this kind of violence involves a demonstration of the vulnerability and destructibility of what the perpetrator regards as a powerful group or institution: there is always a communicative meaning that transcends the attack itself. Böckler and colleagues (2018) describe such acts of demonstrative targeted violence as an expression of personality in which the perpetrators seek to gain social recognition by presenting their personal and/or social identity on a public stage. This self-staging in turn indicates a social identification with scripts of violence, groups, and/or ideologies. On the other hand, the act of demonstrative violence is also a form of directed communication seeking to draw attention to injustice, to spread fear and panic, or to mobilize others to fight for the same cause. However, it also indicates the perpetrators’ need to justify their actions to themselves and others. Against the background of these fundamental similarities in the modus operandi of severe targeted school attacks and terrorist attacks, Böckler and colleagues (2018) present a theoretically grounded pathway model for the development of demonstrative targeted violence.
While perpetrators of targeted violence in schools and terrorists generally seem to exhibit functional cognitive processing of reality, personal grievances and crises mark the start of a developmental process leading to an act of demonstrative violence. In this context, the planned style of targeted school attacks and terrorist attacks also suggests similarities in the preparation processes, the planning phase, and the acquisition of competence at violence. The existing research on both school shootings and terrorism indicates that the perpetrator’s redefinition of self from victim to self-perceived avenger is associated with self-empowerment for violent action. The perpetrator increasingly moves into a phase of clandestine planning characterized by a state of tension between secret private rituals and public intimation (leakage) (Gill, 2015; Meloy & O’Toole, 2011; Meloy, Mohandie, Knoll, & Hoffmann, 2015). Many investigators have been able to reconstruct different trigger events after which the perpetrator might view the act of violence as necessary, justified, inevitable, and meaningful (Corner & Gill, 2015; Heitmeyer, Böckler, & Seeger 2013; Meloy & Gill, 2016).
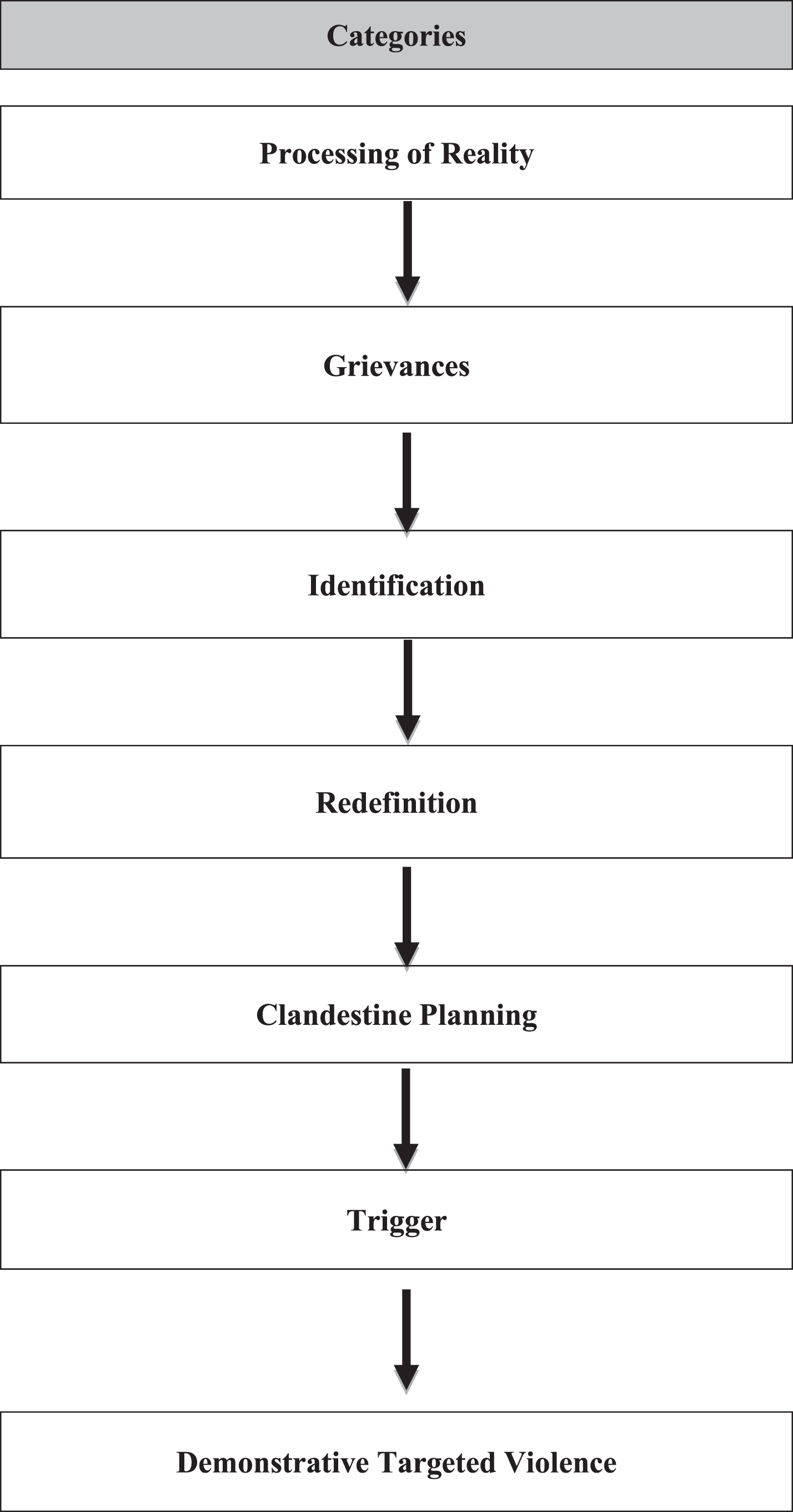
The presented heuristic model (Fig. 1) forms the backbone for our theoretical coding procedure and the constant case comparison. Our aim is not to test the above mentioned model in a hypothetico-deductive manner, but to treat it as a sensitive concept from which we derive an empirically grounded model of perpetrators’ developmental pathways towards demonstrative violence. To use Blumer’s words: “Whereas definitive concepts provide prescriptions of what to see, sensitizing concepts merely suggest directions along which to look (…) they rest on a general sense of what is relevant” (1954, p. 7). We therefore constantly consolidate, modify, and differentiate categories using case comparison and combine these findings with the hypotheses arising fromthe theoretical knowledge in the field (Kelle, 2007).
Figure 1.
Heuristic model - Developmental pathway of school attackers and terrorist attackers.
Method
Sample
Our study is based on data collected within the national research project “TARGET – Case analyses of severe targeted violence” which set out to analyze all incidents of severe targeted violence in Germany between 1999 and 2013. For case recruitment (see Fig. 2) we distinguished two groups: severe targeted school violence comprising attempted or completed attacks in schools, 1. committed by a current or former student of the school, 2. planned and executed with potentially lethal weapons and the intention to kill one or more persons associated with the school, 3. where the attack at least commenced, and 4. when the perpetrator had not yet reached the age of twenty-five; and targeted attacks with ideological or religious background comprising attempted or completed attacks directed against the political order in which perpetrators referred to an ideological or religious worldview.
Figure 2.
Sampling process.
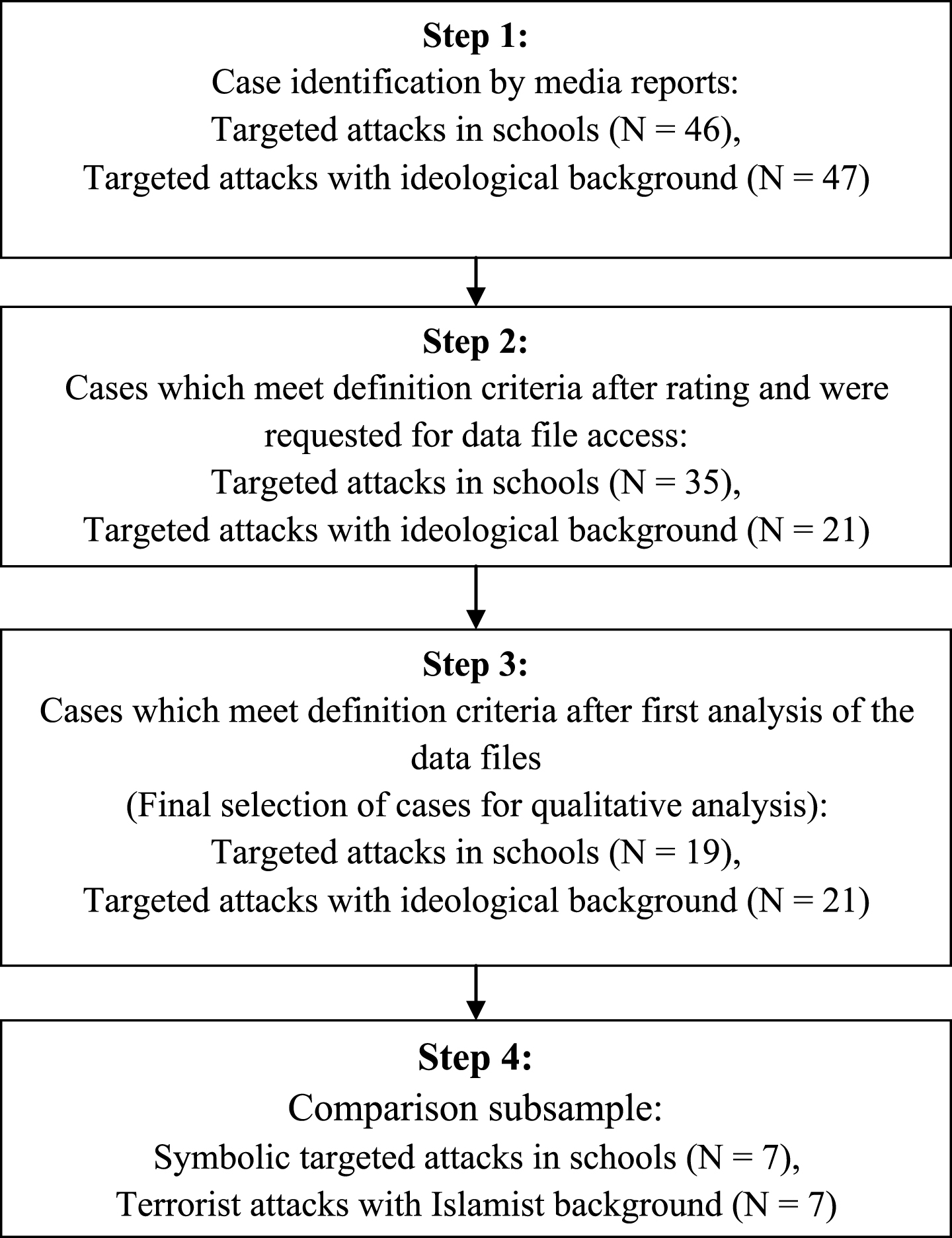
For case identification we conducted systematic recruitment by keyword search with German search terms “Terroranschlag” (terrorist attack), “Amok” (rampage), and “School shooting” (school shooting) in media reports, using the electronic media archives Genios and LexisNexis which cover about 340 German-language newspapers and journals. We identified forty-six targeted attacks in schools and forty-seven targeted attacks with ideological or religious background. In a second step, identified cases were categorized by two separate researchers using the identified media materials and our aforementioned definitions. For deeper investigation we selected thirty-five cases of targeted attack in schools and twenty-one cases of targeted attack with ideological or religious background. In all selected cases, we requested access to the prosecution files. After initial analysis of the documents, we excluded all cases which did not fulfill our criteria (see above). After this third step, we were left with a sample of nineteen (attempted or realized) targeted attacks in schools and twenty-one targeted attacks with ideological background.
For the case analyses and comparisons in the present contribution we used a subsample of symbolic school attacks and homicidal attacks with jihadi terrorist background. Cases of severe targeted school attack were classified as attempted or completed symbolic school attack if victims were chosen for their symbolic meaning as members of the school rather than because of personal conflict. Homicidal attacks with jihadi terrorist background were defined as attempted or completed attacks in which the perpetrator(s) referred to a jihadi movement or organization. We included only perpetrator(s) who had been socialized in Germany before they decided to plan an attack, and excluded cases where the perpetrator(s) entered Germany specifically to commit an act of terrorist violence. Ultimately, seven cases of (attempted) symbolic school attack by single perpetrators were selected (seven perpetrators) (see Table 1), and three cases of (attempted) homicidal attack with jihadi terrorist background (with seven perpetrators) (see Table 2). All incidents investigated occurred inGermany.
Table 1
(Attempted) Homicidal Symbolic Attacks in Schools
| Case Number* | Year | Events |
|---|---|---|
| 1 SA | 2002 | 19-year-old former student shoots dead 12 teachers, two students, one administrative employee, and one police officer at his former school before shooting himself. |
| 2 SA | 2006 | 18-year-old student injures 36 persons at his former school with firearms and smoke bombs, before committing suicide. |
| 3 SA | 2009 | The shooting of a 17-year-old former student resulted in the deaths of twelve people at his former school and three civilians, he killed at a car dealership. His flight lasted several hours. He committed suicide, when he was surrounded by police forces. |
| 4 SA | 2009 | 16-year-old girl plans to stab several teachers and students at her school and set the school on fire using Molotov cocktails. Detected by a classmate, she injures her and fleees from school. She turns herself over to the police the same day. |
| 5 SA | 2009 | 18-year-old perpetrator armed with Molotov cocktails and an axe injures fifteen people, two of them severely. Police quickly arrive on the scene and dtétain him. |
| 6 SA | 2010 | 23-year-old former student armed with a knife and a starter pistol stabs a former teacher to death at his former school. He is arrested shortly thereafter. |
| 7 SA | 2011/2013 | Armed with several knives and an axe, a 13-year old girl lights a fire in the school hallway and threatens to kill classmates. She is arrested without injuring anyone. One and a half year after the first event, after a stay at a psychiatric clinic, she attacks her classmates at her new school using her father’s gas gun. |
* SA = School Attack.
Table 2
(Attempted) Homicidal Attacks with Ideological Islamist Background
| Case Number* | Year | Events |
|---|---|---|
| 1 TER 2 TER | 2006 | Two perpetrators aged 20 (1 TER) and 21 (2 TER), plant explosive devices in two passenger trains. The attack is meant to be a retaliation for the publication of Mohammed caricatures in German newspapers. Due to defects the bombs do not explode and the perpetrators are able escaped to Lebanon. 2 TER is arrested when he returns to Germany, tried and sentenced to life in prison for attempted murder and attempting to cause an explosion. The second perpetrator (1 TER) is later arrested in Lebanon. |
| 3 TER 4 TER 5 TER 6 TER | 2007 | Four perpetrators aged 22 (3 TER, 4 TER), 27 (5 TER) and 28 (6 TER) are arrested while constructing explosive devices to attack US targets. Two of the perpetrators are sentenced to 12 (6 TER) and 11 (5 TER) years for membership of a foreign terrorist organization, conspiracy to mass murder, and coercion. One of the conspirators (3 TER), who tried to shoot a police officer during his arrest, is also convicted of attempted murder and also sentenced to 12 years in prison. The fourth perpetrator (4 TER), who was entrusted with acquiring detonators, is sentenced to five years in prison. |
| 7 TER | 2011 | 21-year-old man with a handgun shoots two US soldiers dead at Frankfurt Airport and severely wounds two others. Sentenced to life in prison for two cases of murder and three cases of attempted murder in conjunction with grievous bodily harm. |
* TER = Terrorist Attack.
The school attackers’ ages ranged from 13 to 23 years (M = 17.72, SD = 2.8); two offenders were female and four committed suicide after the offense. The terrorists’ ages ranged from 20 to 28 years (M = 23.00, SD = 2.9); all were male, none committed suicide in connection with the incident.
Materials and Data Analysis
Data about attacks and perpetrators includes prosecution files and additional material such as interviews with imprisoned perpetrators. All files included witness statements and police reports. For ten perpetrators the files include court judgements and forensic psychological assessments, and for eleven perpetrators personal writings and testimonies. We first ordered all relevant information about the perpetrators chronologically from birth to offense, and prepared biographical case descriptions in order to analyze the developmental trajectories of perpetrators. In the next step, data was coded following the theoretical coding method (Strauss & Corbin, 1990). Two researchers coded the material independently and discussed diverging interpretations until agreement was reached. In this way, biographical trajectories, relevant life events, and turning points were reconstructed for each case, and developmental pathway types were described. For the present paper important concepts and categories gained from inductive analysis were used for an in-depth case comparison of the subsample of cases from both case groups.
Results
According to our theoretical concept (Böckler et al., 2018) we will describe similarities and differences between the two groups of perpetrators in terms of their developmental pathways in the run-up to the violent attacks.
Dispositions and Functional Processing of Reality
In our analysis there is little evidence for the hypothesis that pathways towards targeted attacks in schools or jihadi terroristic attacks are determined by mental disorders. Only in one case of school attack (7 SA) there is evidence for a lack or loss of ability to exercise control in the attack situation caused by schizophrenia. In the sample of terrorist attackers we found no evidence at all of a causal effect of mental disorders. Nevertheless, there is evidence in all cases that mental disorders and specific mental dispositions may have framed the perpetrators’ perception of reality and social relationships. Mental dispositions are understood here as the result of individual’s personality and early socialization experiences. Our case analyses revealed two typical dispositions from early childhood on: aggressive and impulsive tendencies on the one hand, and introverted characters on the other hand. Within the first type, subjects showed aggressive and impulsive tendencies and low self-control as a result of early problems in the family setting (disrespect, domestic violence, or sexual abuse). These individuals also showed early behavioral problems in the peer context and school, often classified as antisocial behavior, attention deficit, and hyperkinetic disorder. While none of the investigated school attackers fell into this category, the sample of jihadi terrorist attackers included four cases in which the subject for example attracted attention with criminal and dissocial behavior in the run up to their radicalization. The second class of perpetrators presents as sensitive, introverted, inwardly focused, and non-assertive in advance of the attack. Some of them had health issues and physical abnormalities (which might have been the cause for low self-esteem), poor social skills, and poor school performance. One school attacker (6 SA) suffered from Klinefelter’s syndrome, which can cause symptoms like small testes, tall stature, gynecomastia, and failure of normal sperm production (Nahata, Rosoklija, Yo, & Cohen, 2013). He was teased continuously by his peers about these physical symptoms, which resulted in low self-esteem and depressive withdrawal. Within their further developmental pathways some of the later perpetrators evolved a compensatory narcissistic or schizoid personality structure. Among the sample of school attackers, all seven cases show some indications of personality anomalies, but there were no proper psychiatric or psychological diagnoses. In the sample of terrorist attackers two individuals showed clear internalized coping behaviors, along with narcissistic personality accentuations in advance of the attack. The cases 2 TER and 7 TER repeatedly experienced depressive and partly suicidal tendencies. In social contexts they presented as reserved and showed very little personal initiative. While withdrawing from society and everyday social life they developed compensatory fantasies of being omnipotent avengers and taking part in violent jihad.
Grievances
For all school attackers and jihadi terrorists in the sample we can identify grievances in socialization contexts (family, peer group, and school), which in some cases culminated in personal crises subjectively perceived as highly significant. In most cases these experiences were associated with major life changes that triggered severe feelings of powerlessness and disorientation.
The Family Context: Problematic Parenting Styles and Lack of Social Support
There is considerable variation in the formal composition of the families in which the perpetrators grew up – ranging from intact nuclear families, single-parent families, to foster families. In all of these socialization contexts problematic social dynamics were identifiable. In the sample of school attackers most parents experienced their child as physically weak and clumsy in interpersonal relationships but in none of these cases did parents actively support the process of identity exploration. Instead they pressured their children toward their own preferred outcomes, such as academic performance, sporting success or masculinity. Thus, personal crisis often resulted from discrepancies between parental expectations and self-awareness. One typical example is a case where the parents always compared the young man with his successful older brother (1 SA). They pressured him to attend a selective academic secondary school. His failure there was the initial trigger event for the later shooting.
In the cases of jihadi terrorists, the subjects felt somehow insecure and disoriented in their families. For both groups, the dominant factor seems to be a familial atmosphere characterized by emotional indifference and a lack of parental involvement. The parents of the later perpetrators were mainly concerned with their own worries and activities, and showed little presence in the life of their children. In some cases family life was overshadowed by burdensome social dynamics derived from parental divorce and associated perceived crises of loyalties (3 TER, 6 TER). Illness and death of significant others (7 TER, 5 TER) and long-term separation (1 TER, 2 TER) were also identifiable factors. 1 TER and 2 TER for example felt totally separated from their family and their familiar culture, before they jointly decided to plant bombs in two German passenger trains. 1 TER and 2 TER came to Germany to study, two years before the incident. Soon they felt overwhelmed by multiple stressors, with spatial separation from their families creating pressure to perform and exposing them to new unknown cultural codes. While 1 TER quickly tried to compensate his feelings of disorientation by escapism in Salafist ideology, 2 TER spent most of his time aimlessly surfing the internet, before 1 TER eventually recruited him for his attackplans.
Our case analyses reveal that perpetrators with migration background (1 TER, 2 TER, 4 TER, 5 TER) often perceived themselves as experiencing a challenging balancing act between two cultures. They perceived Western culture and behavioral codes they were confronted with in school and at work as a world apart from their family life at home. Their parents were not well integrated and – due to lack of language skills – communication between parents and schools was often difficult. Within their Western living contexts, the young people deeply missed functioning role models, as they found themselves forced to face the challenges of everyday life on their own. A futile search for orientation became a central element in the developmental pathways of 4 TER, 5 TER and 7 TER.
5 TER, for example, stated during the police investigation he started to perceive his father as a weak man after he moved to Germany. He was obviously unable to cope with life in German society. 5 TER soon was yearning for other role models, whom he eventually found in the authoritarian but charismatic preachers of a local Salafist group. 7 TER also described his father’s severe illness as a turning point in his life. After a heart attack, his father was unable to work and became increasingly dissatisfied with his situation. During this time, 7 TER started to regard himself as a good-for-nothing: He was unable to contribute any income to the family and, at the same time, failing at school. When he eventually had to repeat a grade, he perceived himself as a complete disappointment for his parents. Due to a great sense of shame, he failed to tell them when he had to repeat a second year, and eventually left school without any qualifications.
The Peer-context: Disrespect and Bullying among Peers
The peer context can be understood as the most important social space in the phase of identity formation. For the school attacker sample, it is obvious that this social space is experienced as problematic and exclusionary from the perspective of the later perpetrator. Nearly all of the later perpetrators felt harassed, persecuted, threatened, or hurt by the majority of their peers. Early experiences of exclusion by peers fuel a process of social withdrawal and create a strong need for public recognition. Several cases illustrate how early experiences of peer exclusion created a continuous point of reference for violent thoughts: One perpetrator wrote in his diary five months before the attack that he had never forgotten the feelings of shame and helplessness when he was beaten on a school excursion six years previously (5 SA). Another perpetrator reported on a psychological counselling website that his experience of public humiliation by his peers was the turning point that generated a strong desire for revenge (2 SA). While all investigated school attacker cases feature at least subjective peer exclusion, such experiences of humiliation were not identified in the sample of terroristattackers.
The School and Workplace Context: School and Work Problems
For both groups, school attackers and jihadi terrorists, formal educational careers were characterized by inadequate performance in school and university, dropout and precarious employment. In these contexts, we identified two central patterns: In the first pattern the perpetrators initially showed no abnormalities in their conduct at school or work. A drop in performance, or withdrawal from peers and colleagues, marked significant changes in their behavior. In two cases in the jihadi terrorist sample (3 TER and 1 TER), classmates reported that the later perpetrators attracted the attention of teachers and peers when they suddenly started to glorify terrorist organizations and violence. Quitting school and work were active decisions by the later perpetrators, triggered by personal crises, a successive orientation towards ideological contexts, and the prioritization of religious practices. For those who quit school early, this pathway continued with precarious employment and uncertain prospects.
In the second pattern, later perpetrators had difficulties coping with school from the start and had to repeat several grades. Some school attackers and some of the Jihadi attackers also experienced heavy parental pressure to perform. In both groups we observed conflicts between the later perpetrators and teachers as well as classmates. In one case of severe targeted school violence, the perpetrator attacked a teacher who he felt had humiliated him seven years previously (6 SA). Another perpetrator who was expelled from school for falsifying a medical certificate only targeted teachers in his shooting attack (1 SA).
While later school attackers showed a cognitive fixation on previous humiliations by peers and teachers, we were not able to identify the same for the terrorist attackers, whose orientation on ideological contexts played a compensatory, structuring and sense-attributing role. In the course of their radicalization process, ideologies, faith-based practices and group dynamics increasingly replaced other everyday activities. Positive social feedback, which the later perpetrators perceived as important for the stabilization of their identity, increasingly came from ideological contexts.
The personal grievances the perpetrators of both groups suffered in the course of their biographies present as very diverse. The common factor is perceived fundamental incongruences between real-self and ideal-self, resulting in severe chronic strains and extreme strategies to cope with them. These grievances produced an “openness” for ideological contexts and alternative worldviews, as constraining ties bonding them to socialization agents outside of radical contexts were absent (Snow, Zurcher, & Ekland-Olson, 1980).
Identification with Ideological and Cultural Scripts and Redefinition of Self-Concepts
Exposure to and confrontation with general mythodologies of violence eventually set the course towards the violent acts. Sutterlüty (2004) describes such mythodologies as scripts in which the use of violence is linked to categories like power, strength, and manhood – for example as presented in many films, computer games, and other cultural products (Kellner, 2013). We identified a strong fascination for such narratives in almost all the investigated school attacks. This was, for example, reflected in intensive reception of action and horror movies, computer games, and in strong identification with warriors, fighters and, in some cases, even mass murderers.
Sutterlüty (2004) points out that perpetrators who refer to such mythodologies of violence often associate their planned deeds with great expectations – namely to gain social recognition by exerting power over others. At the same time, these expectations push them further and further towards the realization of their phantasies. This is true for both groups in our sample – school attackers and jihadi terrorists – with the difference that social relationships and group dynamics played a more central role in the sample of jihadi terrorist attackers. While friendships and social networks preceded the perpetrators’ adoption of jihadi ideology and (in most cases) also their readiness to use violence, later school attackers were directly and more intrinsically motivated to use violence as revenge against those who they felt had humiliated them. If at all, not offline relationships but online social networks and identification with former perpetrators conditioned their adoption of cultural school shooting scripts. However, we were able to identify forms of ideology appropriation for school attackers as well as for jihadi terrorists.
Jihadist Attacks: Radicalization Online, in Friendship Networks, and in Isolated Dyads
For the Jihadi group attackers (1 TER, 2 TER, 3 TER, 4 TER, 5 TER, 6 TER), as well as for the single lone jihadi terrorist (7 TER) in the sample, growing commitment to ideology and the social collective behind it drove the radicalization processes further and further towards violence. The later perpetrators’ active engagement with the ideology was initially rooted in its attractiveness as a rigid and guiding world view and their desire to belong to a social network subjectively perceived as morally superior. The jihadi terrorists in our sample increasingly interpreted their own life in the light of ideological meaning schemes. For example, 7 TER’s turn towards Islam evolved in a period of inner disorientation and depressive mood. Like 3 TER, 4 TER, 5 TER and 6 TER, 7 TER expected to gain inner peace, structure and discipline by devoting himself to religious beliefs and practices. As he had nearly no relationships with other practicing Muslims, 7 TER tried to learn about Islam in a rather autodidactic manner – especially via online social networks. He read the Quran in German but soon recognized he had reached the limits of his ability to comprehend. This changed when he came across Salafist preachers on YouTube who gave him an easy understanding of the religion by reducing its complexity to a binary black and white logic. The algorithms of Facebook and YouTube provided him with more and more neo-Salafist and jihadist content, as well as links to forums like the al-Qaeda Global Islamic Media Front. Over time, 7 TER became increasingly confident in his ideological knowledge and at the end of each day, he was satisfied if he had managed to comply with the strict religious rules and practices. This represented a possibility to prove himself – and by doing so to regain a sense of self-respect. After his attack, investigators found more than one thousand jihadist files on 7 TER’s computer – a majority of them propagating the duty of every Muslim to fight against Western crusaders and unbelievers.
The Role of Social Networks
While most of 7 TER’s radicalization took place in the context of online social networks, pre-existing friendship and kinship ties brought 3 TER, 4 TER, 5 TER and 6 TER into contact with radical and ideological milieus. For example, about five years before his attack, 3 TER was led to a radical form of Islam by an acquaintance with whom he had played basketball. In 3 TER’s words, he had realized that all the pressing questions about life which had haunted him since he was thirteen years old found an answer in Islam. During a period when he felt uprooted, he decided to convert. From this point on, he spent more and more time in groups that propagated a radical interpretation of Islam and sympathized with violent jihad. 6 TER – in contrast – was socialized in a largely Turkish circle of friends. The parents of one of his best friends held extremist beliefs. They repeatedly invited 6 TER for lunch and dinner. Eventually he converted when he was sixteen years old. He stated that conversion to Islam was a rational decision for him, because Islam provided him with more answers than any other religion. It was a decision he made during a time when he was experiencing problems in the family and had several severe conflicts with teachers. 3 TER and 6 TER both quickly found strong connections in the Salafist community where they were entrusted with tasks and functions. 6 TER became an editor of an Islamist publication that glorified violent jihad and the mujahedeen’s fight against the West. In our sample we also identified radicalization processes in close dyadic friendships, as in the cases of 1 TER and 2 TER. Malthaner and Lindekilde (2017) demonstrate the centrality of the building of social bonds that promote intense loyalty, emotional support, and intensive interactions for the radicalization of individuals within small groups and dyads. These new bonds promote increasing isolation from the previous social environment and draw radicalizing individuals closer to radical interpretations.
School Attackers and their Perceived Connectedness: Identification with Other Attackers
While in the sample of Jihadi attackers deep identification with other attackers developed in later stages of radicalization, identification with former attackers and their self-presentation was an initial starting point for most of the school attackers’ pathways towards violence. In drawing on the school shooting script, they changed their interpretative patterns in relation to self and world in a manner similar to the terrorist adopting jihadi ideology. The more they were able to recognize their own experiences in the biographies and self-presentation of former school attackers, the more they considered an attack of their own as an option, a potential solution to their individual problems. Our case studies include personal documents, diary entries and downloaded materials indicating strong identification with former school attackers: In one case a female perpetrator wrote the following in a friendship book at the age ofthirteen:
About me: I hate my life! My major role models: Dylan Klebold & Eric Harris also known as the rampage shooters of Littleton (ReB and VoDKa). I don’t go jogging, I’m running amok. I don’t write poems, I write my suicide note. I don’t like shopping for clothes, I like to buy weapons.(translated by authors, case 4 SA)
Another perpetrator wrote in his diary:
ERIC HARRIS – Probably the most reasonable boy a high school can offer. ERIC HARRIS is god. There is no doubt. It is terrifying how alike Eric is to me. Sometimes it feels like I am living his life again, as if everything is repeating itself. I am not a copy of REB, VoDKa, Steini, Gill, Kinkel, Weise or anybody else! I am the advancement of REB! I learnt from his mistakes, the bombs. I learnt from his whole life. (Perpetrator’s diary; translated by authors, case 2 SA)
The same perpetrator often visited the website: www.wekillem.org, and wrote in his diary that he had read there about the “TCMSD” (Trench Coat Mafia Section Germany), an online fan base of school shooting fans. The diary entry ends with the words: “Outsiders of Germany, unite!” In several cases perpetrators understood themselves as part of an online community of individual outsiders. The school attackers in our German sample who referred to former attacks and perpetrators also started to produce self-presentations (photos, videos, writings) like their role models did in the run-up to their own acts of violence. These productions reflected their desire to create a new definition of self, namely a transformation from victim to morally superior avenger. From a social relational point of view, the radicalization processes of school attackers can best be compared to the radicalization process of the single jihadi lone operator in our sample who radicalized online in the context of a virtual community.
Redefinition of Self
In all cases we found one common feature of the radicalization process, which we describe as a redefinition of self-concept (Böckler et al., 2018). During the process of growing identification with an ideological or a violence-glorifying worldview radicalizing individuals are increasingly motivated to interpret and consolidate their self-concepts in terms of these mythodologies. The process comprises not only growing interest in an alternative radical worldview, but also its habitualization. We identified different forms of such processes: sometimes the redefinition of self is overtly presented and verbalized, in other cases the process proceeded silently and found expression only in behavioral changes. By comparing these redefinition processes we were able to identify typical patterns, which we describe in the following.
From Disrespect and Failure to Recognition and Significance
The first redefinition pattern is focused on public recognition and individual significance and is found in all cases of school attackers. Two slightly different versions can be described: Firstly, in a resistance pattern subjects suffered from experiences of disrespect and a loss of recognition in social relationships, in the family or, more often, in the peer context (2 SA, 4 SA, 5 SA, 6 SA, 7 SA). They regarded themselves as at the mercy of others and felt discriminated and isolated. In this pattern we find a strong desire for revenge for previous slights and social exclusion. Identification with radical opinions and ideology, and with associated role models serves to acquire at least some kind of negative recognition and notoriety. Here we often found a specific date, on which the later perpetrator presented their new self-concept in public in order to capture the interest and attention of the exclusionary reference group. In the second version of this redefinition pattern, feelings of inferiority and a strong discrepancy between ideal self and real capacities are the starting points (1 SA, 3 SA). Typical features include strong parental pressure regarding academic performance or masculinity and assimilation in the ideal self of the later perpetrator. When the subjects realized that they were not able to fulfil the desires generated by their ideal self, they became depressed and suffered self-doubt and fear of failure. From the sample of jihadi attackers, the case of 7 TER is prototypical here. As his father’s illness, his failure in school and his family’s financial difficulties led to extreme feelings of guilt towards his parents, his desire to stabilize his self-worth, to feel useful and needed increased more and more. His orientation towards Islamist content via the internet satisfied his need for clarity and guided him towards new social contexts. In the course of his radicalization his focus shifted more and more from his own personal grievances to the grievances of all Muslims. While he was helpless in the face of his own problems, ideological contexts provided him with possibilities to perform a great service in the fight for the global Muslim community and thereby to identify himself with the mighty mujahedeen and its martyrs. That pattern is also typical for school attackers, who seek to communicate a message through a symbolic attack. However, for school attackers the interest in radical ideology and violence-related scripts is not content-related but emotional – a search for significance and greatness using radical violent means to prove their prowess and demonstrate their abilities. Both version of this redefinition pattern include a shift from self-perception as failure to self-perception as a significant and powerful individual, and a desire for public recognition.
From Nobody to Charismatic Leader
Some of the later perpetrators were deeply concerned about their social impact (2 TER, 5 TER, 6 TER). From early on, they showed a strong desire to prove themselves within social networks; exerting control and influence were central social motives. They were eager to become opinion leaders within most of their social contexts. Their demonstrative identification with extremist beliefs (including intolerance and aggression against non-Muslims, glorification of terrorists) became an important means of self-expression. These perpetrators served as an identification figure for other members of the terrorist group, as they were perceived as determined, self-confident and extremely dominant in social contexts. They therefore had an active influence on the radicalization processes of others, as they set the trend for the violent behavior of the group. At the same time positive social feedback within and from the radical contexts consolidated the radicalization processes of these individuals. For them, radical social spaces advanced to a main source of their emotional and social recognition.
From Loneliness to Social Embeddedness
The commitment of these perpetrators (1 TER, 4 TER) to the extremist contexts arose mainly from social relationships and less from a deep faith in ideology. The central motive for engaging in violent acts was the desire to experience a stronger sense of social belonging. Thus, ideology itself played a subordinate role for this socially dependent type of perpetrator. Perpetrators in this group were searching for other individuals to provide them with orientation and behavioral security. Therefore, they were highly sensitive to the influence of others. The planning of an attack also stemmed more from a sense of increasing commitment towards other people or social networks than from intrinsic ideological beliefs. Each perpetrator in this category had a close relationship to a person who he regarded as an authority figure. As these individuals cut themselves off from networks outside the radical contexts, they became more and more dependent on their mentors. The radicalization process consolidated as a result of their social experiences within the radical contexts, indoctrination and an increasing feeling of commitment towards their confidants.
Clandestine Planning
For both Jihadi attackers and school attackers, a phase of clandestine planning has been identified in the developmental pathway in the run-up to the attack. This phase is characterized by self-empowerment for violent action, increasing thoughts and fantasies about an attack, and clandestine planning (for example acquisition and handling of weapons, construction of bombs) as well as preparation activities (for example reconnaissance of targets). The duration of this phase ranges from two to six months. Our analyses indicate that clandestine planning is a central factor in the genesis of symbolicattacks.
Radicalization in social isolation or within small radical groups is characterized by secrecy, which produces a restriction of everyday interaction and communication. Social relationships beyond the radical social space become weaker and less important. This means that delinquent thoughts and actions of the isolated person or radical group have to remain hidden and protected from discovery by others, especially law enforcement. The fact of secrecy produces decisive aspects affecting escalation: Because the interaction processes with the real or imaginary peer group are hidden and clandestine, they are subject to a disinhibition mechanism that causes steadily growing polarization towards groups and individuals perceived as hostile and confirmation of the perpetrator’s own convictions. This disinhibition mechanism has been described both for face-to-face interactions in clandestine groups and in the context of “online disinhibition” (Suler, 2004) for interactions on the internet.
The permanent danger that high risk activities (attack fantasies, planning, acquisition of weapons, training) may be discovered, requires clandestine social structures in the form of hierarchies and rituals (Mackert, 2011) and associated sanctioning. It leads to the emergence of protective mechanisms: In clandestine groups hierarchies serve to exercise strong control and pressure to conform, in order to exclude actions that could create danger for the entire group (such as betrayal). Rituals, such as collectively committed illegal acts, function as additional protective mechanisms. Functional equivalents to these group processes are observed in connection with both targeted attacks in schools and Jihadi attacks and can be described as private rituals and self-controlling behavior.
Clandestine Planning in Small Groups
Within small groups the group hierarchy and dynamic facilitates the escalation process towards violent attack. In the case of 3 TER, 4 TER, 5 TER and 6 TER, preparation activities eventually oust more or less all everyday life activities of the members several months before the arrest. During their training in a terror camp run by jihadist militants in Pakistan, 3 TER, 4 TER, 5 TER and 6 TER were ordered to execute an attack on German territory. After their return from the Middle East the group procured seven hundred kilograms of chemicals and stored them in a garage rented for that purpose. They also moved to a holiday rental hundreds of kilometers from their respective places of residence in order to finish their bomb-making. With only a few exceptions, the perpetrators’ immediate social environment was not privy to their plans. Wiretap transcripts show that the group had quite ambivalent attitudes towards their mission. At first, they were against attacking civilians in Germany and they desired to fight and die for their brothers and sisters at the front, rather than kill innocents in their home country. But the group managed to overcome these doubts by reinforcing and controlling each other. For example, they imagined how the interior minister would appear on camera after their attack and talk about the most devastating terrorist plot since 9/11. Referring to the popular music casting show, 5 TER stated during the preparations that he felt like he was on “Terrorist Idol” and that he was expecting to receive the death penalty at least deportation to Guantanamo. Collins (2014) describes such dynamics during the perpetrators’ preparation as “clandestine excitement.” We also identified similar processes of isolation and clandestine excitement in the cases of 1 TER and 2 TER. As the dominant part of the terrorist dyad, 1 TER was eager to isolate 2 TER from his fellow students while accelerating his radicalization. While preparing their suitcase bombs they withdrew completely from their social environment. Like 3 TER, 4 TER, 5 TER, and 6 TER, they had an exact idea what would happen after their attack. Their bombs were to explode on the ground while they were sitting in a plane flying towards the Middle East. They adjusted the detonators of the explosive devices according to these plans. With their attack they wanted to recommend themselves to terrorist organizations asrecruits.
Clandestine Planning by Isolated Individuals
Similarly, to clandestine planning in small groups and dyads, isolated actors also build a clandestine space where their fantasies experience confirmation and recognition, upon which further cognitive escalation and self-commitment play out, and where emotional preparation for the act occurs. For school attackers Collins (2014) describes a “deep backstage” where young people create a ritualized hidden arsenal around which their fantasies and activities revolve. Their knowledge of the illegality of the arsenal and their own associated potential to kill creates a clandestine excitement that ultimately supplies the emotional energy for carrying through the attack itself. We found evidence for such hidden arsenals in several cases: perpetrators procured pistols and trained secretly; in two cases they built pipe bombs. In most cases the acquisition of weapons was illegal and the perpetrators created hiding places which they visited periodically. Ownership and handling of real weapons can itself have an escalating and urgency-producing effect where the weapons are experienced as sensually stimulating. They also symbolize the possibility of turning fantasies of power and vengeance into reality.
Another typical element of clandestine planning by isolated individuals is the ritualized writing of diaries in which they absorb themselves in their fantasies and planning thoughts. Sometimes fantasies and writings revolve around public reactions after the planned attack:
“I will be the first to go on a rampage with a blank cartridge pistol. It will restart a discussion about our gun laws but it’s all the same to me.” (Perpetrator’s diary, translated by authors) (diary entry, case 6 SA)
In five out of seven school attack cases (2 SA, 4 SA, 5 SA, 6 SA, 7 SA) we found such writings, showing a ritualized identification with and glorification of the perpetrators of the Columbine School Shooting in Littleton in 1999 (Eric Harris and Dylan Klebold). Former school attackers are the “holy pillars” on the private altars of most of the subjects in our school attack sample (Leuschner, 2016, p. 325). Fans and imitators form a “virtual community” in social networks and discuss the possibilities of violent acts and the pros and cons of different weapons (Böckler & Seeger, 2013).
Strong self-controlling behavior can also be observed in cases of isolated individuals, but in forms that are less consistent and characterized by ambivalence between safeguarding the secret and public intimation (leakage). Alongside secret planning and private rituals, the new self-concept is also expressed outwardly and reflected in visibly altered behavior, for which the term leakage (also leaking) has become established (Meloy & O’Toole, 2011; O’Toole, 1999; cf. Bondü & Scheithauer, 2014b). In our analysis we found that later school attackers created poems, drawings, and even theater plays, or showed weapons they already possessed to others. These communications and the displayed personal redefinition also generate enormous pressure to carry through the attack, because any deviation from the leaked plans and the new role would be experienced as weakness and potentially interpretable as confirmation of the earlier self-definition as victim. One could say that leakage creates a “self-obligation” to carry through the attack. Of course leakage (announcements and hints) must never go as far as to create a danger of the secret attack plans actually being discovered. For this reason, we also always observe self-controlling behaviors in lone actors, such as precautionary measures, diversionary maneuvers, and deception strategies that serve to keep others from discovering the deep backstage. As such, leakage describes the perpetrator’s game of hinting at the secret plans to others while at the same time warding off those who come too close to discovering the secret – which heightens the secret excitement (Leuschner, 2016).
Such leakage can also be identified in connection with lone actor terrorists. As Hoffmann, Glaz-Ocik, Roshdi, and Meloy (2015) relate, especially with lone actor terrorists the desire for self-projection often overpowers the tactical need for discretion, where the attack planning is not subject to the discipline of a group. While 7 TER, for example withdrew more and more from family, peers, and friends, he started to glorify martyrdom and violent jihad via the internet. Furthermore he listened to Islamist nasheed songs that told him to turn away from all infidels. About one year before his attack, he declared his hatred against the West in internet chats and forums where he openly sympathized with terrorists, and described the United States as personified evil, and toyed with the idea of joining the mujahideen in Iraq. Few months before his attack, he started to delete all his non-Muslim friends on Facebook and added to his profile quite a number of strangers whose Facebook page indicated some kind of association with Islam. During this time he focused more and more on the ideological world while other spheres of life receded into the background – as also reflected in the amount of jihadist content he downloaded from the web.
Escalating Triggers
Even if the deep backstage self-obligation and escalation mechanisms described above drive developments to the point of violent action, there is no automatism. Whether an attack is actually carried out will depend inter alia on concrete events that may appear in very different forms both for school attackers and jihadi terrorists. The first and most important trigger is events that generate pressure to act, such as events that suggest a concrete external danger of discovery of attack planning or internal pressure resulting from the escalating dynamic in small groups. In the school attacker sample there is one case where the perpetrator was apprehensive about the discovery of his weapon arsenal by law enforcement (2 SA), two perpetrators feared disclosure of their violent plans by classmates (4 SA, 5 SA). 3 TER, 4 TER, 5 TER, 6 TER attracted the attention of the police when 4 TER and 6 TER reconnoitered a possible target for their attack, a US military base. This led to police observation and house searches. Although 3 TER, 4 TER, 5 TER and 6 TER knew about the surveillance efforts, they nevertheless continued with their attack plans. Besides pressure from law enforcement, we also identified other influencing events that escalated the situation for later perpetrators, for example termination of employment or stressing social events.
Secondly, we must consider events in the social setting that radicalized perpetrators perceive as legitimization of their ideological beliefs and attack planning. These can include events experienced as a massive attack on the in-group and its ideology, such as acts of violence, vilification, and abuse from the out-group. Heitmeyer (2012) argues that such signal events exhibit strong potential for emotional and moral outrage and as such are certainly suited to mobilizing individuals and groups to commit violence. In the case of school attacks, in four cases the perpetrator experienced a disparagement (such as expulsion from school) or social reinforcement (for example father actively supporting the son’s interest in guns) that was interpreted as a legitimation for the attack. While 3 TER, 4 TER, 5 TER and 6 TER intensively discussed the legitimacy of an attack as revenge for Western intervention in the Middle East, 1 TER for example convinced 2 TER that the publishing of Mohammed cartoons in German newspapers was one of the severest possible insults against the Muslim community. 1 TER framed an attack as a necessary retaliation against Western society. Shortly before his attack 7 TER, the lone operator, viewed two videos on YouTube. The first showed the lifeless but smiling faces of martyrs accentuated by a heroric nashid, the second showed a scene from the movie Redacted in which US soldiers rape a Muslim teenager. 7 TER, who was not aware that he was watching a Hollywood movie, was unable to get this scene out of his head. He was sure that it was sign from Allah who wanted 7 TER – as a proof of his faith – to protect his sisters from further abuses. The next day, 7 TER killed two American soldiers at a German airport.
Especially in the case of school attackers, retraumatizing events may reactivate earlier negatively experienced emotional states or negatively connoted self-images (for example victimization experiences). For example, a recent slight or subjectively experienced injustice can reactivate the earlier traumatic experience of loss of status and trigger the actual intention to carry out the attack. In the school attacks sample there are two examples (4 SA, 7 SA) in which the later perpetrators again experience bullying and social exclusion, reactivating their earlier experiences and triggering execution of the attack. Finally, perpetrators may experience loss events as triggers. One example would be the end of an important relationship that previously represented a social connection outside the clandestine radical arena(6 SA).
All four trigger types help the perpetrator to view the act of violence as necessary, justified, inevitable, and meaningful. The decisive concrete trigger or combination of events in a particular case can generally only be determined retrospectively. Attempts to identify generally applicable triggers for acts of violence are therefore pointless. Instead it must be assumed that in each individual case the interaction of individual decisions, positive and negative feedback processes (such as social reflection, feelings of empowerment), changed perception of opportunity costs, and biographical breaks become crystallization points for dominant action patterns and paths towards violence.
Demonstrative Acts of Violence
For a complete understanding the situations of violence have to be described as triads of perpetrator, victims, and third parties (the audience, both immediately present and via the media) (Leuschner, 2016). A closer look at the concrete situations of violence reveals that all perpetrators in both groups chose their victims for their symbolic significance. Hence, we describe targeted attacks in schools and acts of terrorism as demonstrative acts of violence: “Demonstrative violence seeks to spread terror, to earn respect, to dispel boredom. It has a genuine social meaning. […] Violence in this context is self-presentation and self-commendation” (Sofsky, 2002, p. 34; transl. by authors). With respect to the communicative meaning of the acts, two aspects need to be distinguished: Firstly, the communicative meaning can be described as an expression of personality, where the perpetrator seeks to present their own personal and/or social identity, and to generate social recognition. Some terrorism researchers have argued that a terrorist attack is a kind of altruistic violence where an individual becomes a faceless ideological soldier for a group’s cause. However, jihadists are eager to offer possibilities for recruits to become both a soldier for the cause and at the same time famous as an individual (martyr cults, glorification of perpetrators in online magazines like al-Qaeda’s Inspire or the Islamic State’s Dabiq and Rumiyah) – at least within the extremist networks, but often also within society through intense media coverage. Secondly, the acts of violence under consideration here are directed forms of communication. They are bound up with a message which the perpetrators want to share: for example, when the perpetrator refers to ideologies, draws attention to injustice, seeks to spread fear and panic, or hopes to mobilize others to do the same. The success of the act thus depends – from the perpetrator’s perspective – largely on the responses of the social environment, so that the perpetrator must ensure that his/her message is understood (Muschert & Ragnedda, 2011; Waldmann, 2011). For this reason, perpetrators generally seek to shape the public interpretation of their actions through “manifestos”, letters, videos, and personal writings. For our sample that was especially true of the school attackers (2 SA, 3 SA, 4 SA, 5 SA, 6 SA, 7 SA), while the Jihadi attackers mainly focused on attacking symbolic public targets to spread their message. However, at the same time most of terrorist attackers could rely on an extremist organization to take responsibility for the attack. While 3 TER, 4 TER, 5 TER, 6 TER and 7 TER focused their attack on American soldiers, 1 TER and 2 TER chose to attack civilians in general. After 1 TER and 2 TER had excluded a famous German bridge and a soccer stadium as potential targets for practical reasons, they decided to focus on passenger trains – inspired by the al-Qaeda attacks in Madrid and London.
Discussion
To our knowledge, this is the first study to empirically analyze the similarities and differences between school attackers and jihadi terrorists in Germany in the period of 2000 to 2013 using police files and court judgements. The sensitive concept proved to be fruitful for the comparative analysis of the developmental pathways towards targeted demonstrative violence. While the pathways of the perpetrators in both groups were quite similar in general terms, the analysis also brought to light significant variations between the groups in most of the categories (Fig. 3). Findings show that the perpetrators’ perception of reality and developmental pathway may be influenced by mental abnormalities (in both groups) but only in one case (a targeted school attack) was here any indication of mental disorder reducing the ability to exercise control in the attack situation.
Figure 3.
Developmental pathways of school attackers and terrorist attackers.
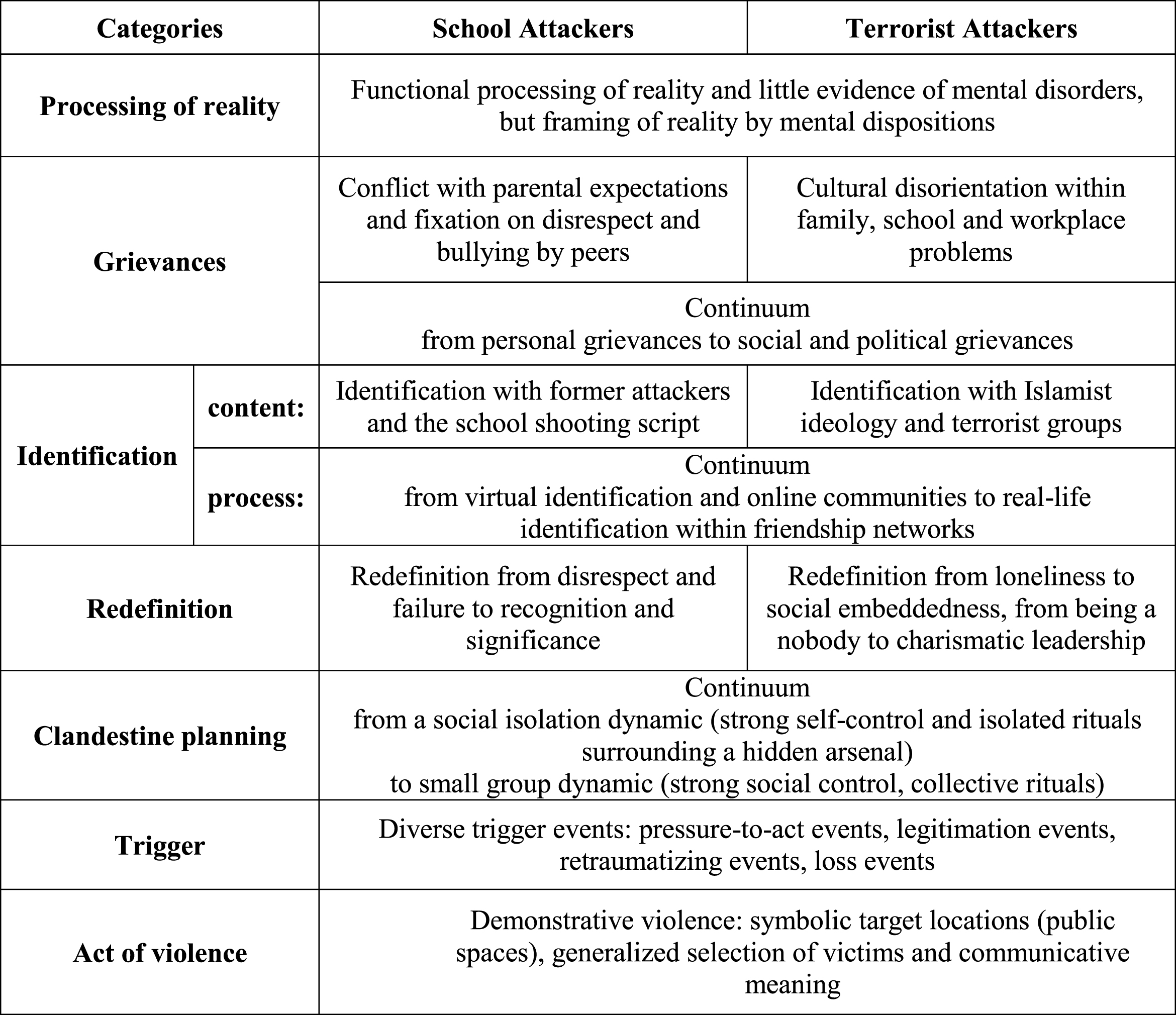
All perpetrators in both groups suffered from grievances in at least one of three socializing contexts (family, peers, school/work), accompanied by fundamental incongruences between their real-self and ideal-self. In most school attack cases and some jihadi terrorist cases, grievances culminated in personal crises that were subjectively perceived as highly significant and triggered further maladaptive development. While the subjective experience of grievance was identified in all cases, its character differs between the groups: School attackers mostly suffered from parental demands and humiliations by peers and teachers, while jihadi terrorists suffered from a lack of role models in their family, identity diffusion between two cultures, and employment problems. These differences may also have to do with the fact that the subjects in the jihadi terrorist sample are on average about five years older than the investigated perpetrators of targeted violence in schools. In other words, the two groups are at different developmental stages (McCormick, Kuo, & Masten, 2011). While the development of a gender identity, a consistent system of norms and values, and the establishment and structuring of social friendships are central developmental tasks in the adolescent phase, the fostering of economic independence, career development, and participation in cultural and political life are important tasks of (young) adult life.
When we understand radicalization in a broad sense with Wilner and Duboulos (2011) as “a personal process in which individuals adopt extreme political, social, and/or religious ideals and aspirations, and where the attainment of particular goals justifies the use of indiscriminate violence” (p. 38), it is noteworthy that individuals in both groups orientate on political-cultural scripts with violent content which obviously offer a possibility to express themselves and to cope with perceived grievances and with central developmental tasks. In this view perpetrators who commit symbolic targeted violence in schools also experience a process of radicalization on their developmental pathway towards violence. Taking the personal grievances of both groups into account it becomes clear that the choice of an Islamist script on the one hand and a school shooting script on the other is biographically reasonable in either case. For the further developmental pathway it is crucial that the confrontation with a suitable violent script occurs in the “right moment” when the individual is seeking a solution for their stressful situation – be it short term (for example failing in school/work, illness of a significant other etc.) or long-term stressors (such as failing to cope with central developmental tasks, disorientation etc.).
Against this background it is important to note that radicalization processes never take place in a social vacuum. This is true for jihadi terrorists as well as school attackers. While real world social networks and friendship ties played a central role as radicalizing social contexts for Jihadi group terrorists, virtual social networks and processes of parasocial identification were crucial for school attackers and the only lone actor terrorist in the sample. The social negotiation of cultural scripts and constant feedback within radical social spaces accompanied the lowering of individual thresholds for use of violence in both groups. Especially for individuals with stronger social anxiety, virtual contexts offered a possibility to approach a radical group from a state of social isolation. While close friendships, social involvement, and the attractiveness of leading a real world group were central motivations to go further along the path towards violence for the terrorist subjects, the desire to cope with social disrespect and failure and to gain (otherwise lacking) social recognition and significance were the drivers for the school attackers and the lone actor terrorist.
In both groups the pathways were consolidated by dynamics of clandestine planning and excitement, accompanied by the restriction of social interactions to radical social spaces. While small group dynamics, mechanisms of group control, and mutual encouragement fostered the radicalization processes of the jihadi terrorist subjects, social withdrawal, private rituals, and leaking were identified as equivalents for the lone actor terrorist and school attackers. Especially the latter mechanisms stimulated fantasies of omnipotence and a new perception of the self in distinction to society. While radical spaces become gradually central for the self-worth of the later perpetrators, the perception of ongoing grievances, everyday challenges, moral outrage and in some cases the stress of law enforcement surveillance served as escalating triggers and increased the pressure on subjects to prove themselves according to the new and redefined violent identity. In the last stage, the execution of targeted violence serves as an initiation ceremony to join a series of other ideological motivated avengers and to demonstrate the radical identity ultimately and irreversibly on a public stage.
From an operational point of view, it makes strong sense to assess terrorist attacks and targeted violence in schools using the concept of demonstrative violence, which allowed us to identify the same core stages – with different dimensional manifestations – in the perpetrators’ developmental pathways for both phenomena (see Fig. 3). That indicates that the two phenomena are not categorically different. Therefore, we agree with Borum et al. (2012) that we should stop devoting resources to scientific definition exercises regarding the number of perpetrators that can be evolved, the kind of outside support which is acceptable or the purity of the political respective ideological motive that is necessary or reasonable to classify an act of violence as terroristic attack or a rampage. As hybrid characteristics are rather the norm than the exception, Borum et al. (2012) argue that it would be much more effective to view these factors “along a continuum instead of forcing unnecessary either-or choices” (p. 393). We propose the same logic for the developmental stages defined in the present paper. Future efforts should focus on identifying and categorizing the characteristics of warning behaviors at each stage and using them for the purpose of early detection. But the model might also be useful for planning effective case management strategies in the deradicalization and threat management context, as the localization of a person of concern in the different stages and sub-dimensions of our pathway model helps to understand the inherent logic of a case, the (social) needs the individual links with his/her behavior, and the social environment which influences the pathway actively or passively. Moreover, the model could sensitize a case manager for potential points of intervention during a process of escalation.
Limitations and Outlook
Especially in the context of the so-called Islamic State, terrorism is a very dynamic phenomenon. We already know that a significant number of the young people who travelled from Germany to Iraq and Syria in order to join jihadist militias between 2013 and 2015 were minors. There is anecdotal evidence that social pressure and influence played a greater role in their decision to fight or to commit attacks in their home country than for the older perpetrators in our sample, who showed significant intrinsic motivation. Nevertheless, we also have to understand the role and pathway of female attackers like Safia S., who tried to kill a policeman at Hannover central station by stabbing him in the neck. Radical female jihadi networks and the recruitment of women are also playing an increasingly important role. However, as most of the criminal proceedings are still pending, researchers have no access to the related police files or court judgements at present. This is also the case for the vast majority of lone operator attacks committed in 2015/2016 when the Islamic State was forced to change its strategy and called on Muslims to stop emigrating to the Caliphate and to fight the infidels in Western countries instead. But current developments indicate that the overlap between terrorist violence and school attacks is increasing rather than decreasing. Without doubt it will be a central task of future research to test this hypothesis against a reliable database and it will be a central topic for future development activities in the domain of preventive interventions (cf. Cornell & Scheithauer, 2011; Leuschner et al., 2017).
As we have developed the presented empirically grounded model of “the developmental pathway towards demonstrative violence” using qualitative comparative analysis, it is open to change and optimization, on the basis of additional cases analyzed through the lens of the current work. We should also ask whether it is possible to categorize other phenomena of targeted violence (for example rampages committed by adults) under the concept of demonstrative violence. In the long run, larger reliable data bases and control groups would be necessary to properly validate a concept like demonstrative violence.
Author’s Notes
Target Research Project: www.target-projekt.de, BMBF funding code 13N12646.
Bio Sketches
Nils Böckler studied educational science and psychology. Currently, he is unit manager for extremism and radicalization at the Institute Psychology and Threat Management in Darmstadt. From 2010 to 2016 he was research assistant at the Institute for Interdisciplinary Research on Conflict and Violence (IKG) at Bielefeld University. His academic work focuses on patterns of online hate and radicalization. Further research interests are school shootings, terrorism (especially by lone operators), extremism, and socialization.
Vincenz Leuschner is professor of Criminology and Sociology at the Berlin School of Economics and Law, Department Police and Security Management. From 2009 to 2016 he was research assistant at Freie Universität Berlin. His research interests are violence research, sociology of social problems, victimology, developmental criminology, crime prevention and security research.
Andreas Zick is director of the Institute for Interdisciplinary Research on Conflict and Violence (IKG) at Bielefeld University and Professor of Socialization and Conflict Research at the Faculty of Educational Science. His research interest concentrates on prejudice and discrimination, intergroup conflicts, acculturation, extremism, and violence.
Herbert Scheithauer is Professor for Developmental and Clinical Psychology at Freie Universität Berlin, Germany, and Head of the Unit “Developmental Science and Applied Developmental Psychology”. His research interests are bullying, cyberbullying, and the development and evaluation of preventive interventions.
References
1 | Blumer, H. ((1954) ). What is wrong with social theory? American Sociological Review, 19: , 3–10. Doi: 10.2307/2088165 |
2 | Böckler N. & Seeger, T. ((2013) ). Revolution of the dispossessed: School shooters and their devotees on the web. In Böckler N. , Seeger T. , Sitzer P. & Heitmeyer W. (Eds.), School shootings: International research, case studies and concepts for prevention (pp. 309–339). New York: Springer. |
3 | Böckler N. , Hoffmann J. & Zick, A. ((2015) ). The Frankfurt airport attack: A case study on the radicalization of a lone-actor terrorist. Journal of Threat Assessment and Management, 2: , 153–163. Doi: 10.1037/tam0000045 |
4 | Böckler N. , Leuschner V. , Roth V. , Zick A. & Scheithauer, H. ((2018) ). Blurred boundaries of lone actor violence: Similarities in the genesis and performance of terrorist attacks and school shootings. Gender and Violence, 5: , 70–80. Doi: 10.1089/vio.2018.0002 |
5 | Böckler N. , Roth V. , Stetten L. & Zick, A. ((2014) ). Targeted school violence and the web of causes: Risk factors and the problems of specificity. Commentary on: “Bullying, romantic rejection, and conflicts with teachers: The crucial role of social dynamics in the development of school shootings - A systematic review”. International Journal of Developmental Science, 8: , 49–51. Doi: 10.3233/DEV-140146 |
6 | Bondü R. , Cornell D. G. & Scheithauer, H. ((2011) ). Student homicidal violence in schools: An international problem. In Cornell, D.G. & Scheithauer, H. (Special Issue Eds.). ((2011) ). Columbine a decade later: The prevention of homicidal violence in schools. New Directions for Youth Development, 129: , 13–30. Doi: 10.1002/yd.384 |
7 | Bondii R. & Scheithauer, H. ((2014) a). Peer and teacher relationships in German school shooters. International Journal of Developmental Science, 8: , 57–63. Doi: 10.3233/DEV-140131 |
8 | Bondii R. & Scheithauer, H. ((2014) b). Leaking and death-threats by students: A study in German schools. School Psychology International, 35: , 592–608. Doi: 10.1177/0143034314552346 |
9 | Borum R. , Fein R. & Vossekuil, B. ((2012) ). A dimensional approach to analyzing lone offender terrorism. Aggression and Violent Behavior, 17: , 389–396. Doi: 10.1016/j.avb.2012.04.003 |
10 | Capellan, J. A. ((2015) ). Lone wolf terrorist or deranged shooter? A study of ideological active shooter events in the United States, 1970-2014. Studies in Conflict & Terrorism, 38: , 395–413. Doi: 10.1080/1057610X.2015.1008341 |
11 | Collins, R. ((2014) ). Micro-sociology of mass rampage killings. Revue de Synthès, 135: , 405–420. Doi: 10.1007/s11873-014-0250-2 |
12 | Cornell D. G. & Scheithauer, H. (Special Issue Eds.). ((2011) ). Columbine a decade later: The prevention of homicidal violence in schools. New Directions for Youth Development, 129: , 1–128. Doi: 10.1002/yd.382 |
13 | Corner E. & Gill, P. ((2015) ). A false dichotomy? Mental illness and lone-actor terrorism. Law and Human Behavior, 39: , 23–34. Doi: 10.1037/lhb0000102 |
14 | COT - Instituut voor Veiligheidsen Crisismanagement (Eds.) ((2007) ). Lone-wolf terrorism. Case study for work package 3 ‘Citizens and governance in a knowledge-based society’, TTSRL. Retrieved from http://www.transnationalterrorism.eu/tekst/publications/Lone-Wolf%20Terrorism.pdf. |
15 | Crenshaw, M. ((2001) ). The causes of terrorism. Comparative Politics, 379–399. Doi: 10.2307/421717 |
16 | Eddy, M. ((2016) ). Suicide bomber in Ansbach, Germany, pledged loyalty to ISIS, officials say. The New York Times Retrieved from https://www.nytimes.com |
17 | Gill, P. ((2015) ). Lone-actor terrorists: A behavioural analysis. London/New York: Routledge. |
18 | Hartleb, F. ((2017) ). Rechtsterrorismus statt Amoklauf. Eine notwendige Neubewertung des Attentats von München am 22. Juli 2016 [Right-wing terrorism instead of rampage. A necessary reassessment of the Munich Attack on 22nd July, 2016]. Kriminalistik, 12/2017: , 715–722. |
19 | Heitmeyer, W. ((2012) ). Deutsche Zustände, Folge 10 [State of affairs in Germany. Volume 10]. Frankfurt am Main: Suhrkamp. |
20 | Heitmeyer W. , Böckler N. & Seeger, T. ((2013) ). Disintegration, losses of control and school shootings. In Böckler N. , Seeger T. , Sitzer P. & Heitmeyer W. (Eds.), School shootings: International research, case studies and concepts for prevention (pp. 27–54). New York: Springer. |
21 | Hoffman, B. ((2006) ). Inside terrorism. New York: Columbia University Press. |
22 | Hoffmann J. , Glaz-Ocik J. , Roshdi K. & Meloy, J.R. ((2015) ). Terrorismus und Anschlage durch radikalisierte Einzeltater [Terrorism and attacks by radicalized lone operators]. In Hoffmann J. & Roshdi K. (Eds.), Amok und andere Formen schwerer Gewalt. Risikoanalyse - Bedrohungsmanagement - Präventionskonzepte [Rampages and other forms of severe violence. Risk-assessment-threat management and concepts for prevention] (pp. 244–265). Stuttgart: Schattauer. |
23 | Kelle, U. ((2007) ). The development of categories: Different approaches in Grounded Theory. In Bryant A. & Charmaz K. (Eds.), The Sage handbook of Grounded Theory (pp. 191–213). Thousand Oaks: Sage. Doi: 10.4135/9781848607941.n9 |
24 | Kellner, D. ((2013) ). School shootings, crises of masculinities, and the reconstruction of education: Some critical perspectives. In Böckler N. , Seeger T. , Sitzer P. & Heitmeyer W. (Eds.), School shootings: International research, case studies and concepts for prevention (pp. 343–364). New York: Springer. Doi: 10.1007/978-1-4614-5526-4_22 |
25 | Langman, P. ((2010) ). Why kids kill: Inside the minds of school shooters. New York: Palgrave Macmillan. |
26 | Lankford A. & Hakim, N. ((2011) ). From Columbine to Palestine: A comparative analysis of rampage shooters in the United States and volunteer suicide bombers in the Middle East. Aggression and Violent Behavior, 16: , 98–107. Doi: 10.1016/j.avb.2010.12.006 |
27 | Larkin, R. W. ((2009) ). The Columbine legacy: Rampage shootings as political acts. American Behavioral Scientist, 52: , 1309–1326. Doi: 10.1177/0002764209332548 |
28 | Leuschner, V. ((2013) ). Exzessive individuelle Gewalt. „School Shootings“ und „Lone Wolf Terrorism“ als soziale Phanomene. [Excessive individual violence - “school shootings“ and “lone wolf terrorism” as social phenomenon]. Berliner Journal fur Soziologie, 23: , 27–49. Doi: 10.1007/s11609-013-0212-9 |
29 | Leuschner, V. ((2016) ). Gewaltsituationen bei Schulamoklaufen [Situations of violence in the course of severe targeted violence in schools]. In Equit C. , Groenemeyer A. & Schmidt, H. (Eds.), Situationen der Gewalt [Situations of violence] (pp. 304–322). Weinheim/Basel: Beltz Juventa. |
30 | Leuschner V. , Fiedler N. , Schultze M. , Ahlig N. , Gobel K. , Sommer F. , Scholl J. , Cornell D. & Scheithauer, H. ((2017) ). Prevention of targeted school violence by responding to students’ psychosocial crises: The NETWASS program. Child Development, 88: , 68–82. Doi: 10.1111/cdev.12690 |
31 | Liem M. , Van Buuren G. , De Roy van Zuijdewijn J. , Schönberger H. & Bakker, E. ((2018) ). European lone actor terrorists versus “common” homicide offenders: An empirical analysis, Homicide Studies, 22: , 45–69. Doi: 10.1177/1088767917736797 |
32 | Mackert, J. ((2011) ). Im Auftrag des Staates. Die geheime Gesellschaft der Folterer [On behalf of the state. The secret society of the torturers]. Berliner Journal für Soziologie, 21: , 431–459. Doi: 10.1007/s11609-011-0165-9 |
33 | Malkki, L. ((2014) ). Political elements in post-Columbine school shootings in Europe and North America. Terrorism and Political Violence, 26: , 185–210. Doi: 10.1080/09546553.2014.849933 |
34 | Malthaner S. & Lindekilde, L. ((2017) ). Analyzing pathways of lone-actor radicalization: A relational approach. In Strohl M. , Englund S. & Burchill R. (Eds.), Constructions of Terrorism (pp. 163–180). Los Angeles: University of California Press. |
35 | McCauley C. , Moskalenko S. & Van Son, B. ((2013) ). Characteristics of lone-wolf violent offenders: A comparison of assassins and school attackers. Perspectives on Terrorism, 7: , 4–24. |
36 | McCormick C. M. , Kuo, S. I-C. & Masten, A. S. ((2011) ). Developmental tasks across the life span. In Fingerman K. L. , Berg C. A. , Smith J. & Antonucci T. C. (Eds.), Handbook of life-span development (pp. 117–139). New York, NY, US: Springer. |
37 | Meloy J. R. & Gill, P. ((2016) ). The lone-actor terrorist and the TRAP-18. Journal of Threat Assessment and Management, 3. Online first: http://discovery.ucl.ac.uk/1477463/. Doi: 10.1037/tam0000061 |
38 | Meloy J. R. & O’Toole, M. E. ((2011) ). The concept of leakage in threat assessment. Behavioral Sciences & the Law, 29: , 513–527. |
39 | Meloy J. R. & Pollard, J. W. ((2017) ). Lone-actor terrorism and impulsivity. Journal of Forensic Sciences, 62: , 1643–1646. Doi: 10.1111/1556-4029.13500 |
40 | Meloy J. R. , Mohandie K. , Knoll J. L. & Hoffmann, J. ((2015) ). The concept of identification in threat assessment. Behavioral Sciences and the Law, 33: , 213–237. Doi: 10.1002/bsl.2166 |
41 | Muschert G. W. & Ragnedda, M. ((2011) ). Media and control of violence: Communication in school shootings. In Haupt H.-G. , Heitmeyer W. , Kirschner A. & Malthaner S. (Eds.), The control of violence in modern society: Multidisciplinary perspectives from school shootings to ethnic violence (pp. 345–361). New York: Springer. Doi: 10.1007/978-1-4419-0383-9-14 |
42 | Nahata L. , Rosoklija I. , Yu R. N. & Cohen, L. E. ((2013) ). Klinefelter Syndrome. Are we missing opportunities for early detection? Clinical Pediatrics, 52: , 936–941. Doi: 10.1177/0009922813493831 |
43 | Newman K. , Fox C. , Harding, D.J. , Mehta J. & Roth, W. ((2004) ). Rampage. The social roots of school shootings. New York: Perseus Books. |
44 | O’Toole, M.E. ((1999) ). The school shooter: A threat assessment perspective. Quantico: Federal Bureau of Investigation. |
45 | Oksanen A. , Nurmi J. , Vuori M. & Rasanen, P. ((2013) ). Jokela: The social roots of a school shooting tragedy in Finland. In Böckler N. , Seeger T. , Sitzer P. & Heitmeyer W. (Eds.), School Shootings: Conceptual framework and international empirical trends (pp. 189–215). New York: Springer. |
46 | Sageman, M. ((2008) ). Leaderless jihad. Philadelphia: University of Pennsylvania Press. |
47 | Sandberg S. , Oksanen A. , Berntzen L. E. & Kiilakoski, T. ((2014) ). Stories in action: The cultural influences of school shootings on the terrorist attacks in Norway. Critical Studies on Terrorism, 7: , 277–296. Doi: 10.1080/17539153.2014.90698 |
48 | Snow D. A. , Zurchner L. A. & Ekland-Olson S. ((1980) ). Social networks and social movements: A microstructural approach to differential recruitment. American Sociological Review, 45: , 787–801. Doi: 10.2307/2094895 |
49 | Sofsky, W. ((2002) ). Zeiten des Schrecken: Amok, Terror, Krieg [Times of fright: Rampage, terror, war]. Frankfurt am Main: Fischer. |
50 | Strauss A. & Corbin J. ((1990) ). Grounded theory: Basics of qualitative research. Thousand Oaks: Sage. |
51 | Suler, J. ((2004) ). The online disinhibition effect. Cyber Psychology & Behavior, 7: , 321–326. Doi: 10.1089/1094931041291295 |
52 | Sutterlüty, F. ((2004) ). Was ist eine „Gewaltkarriere“? [What is a “career of violence”?]. Zeitschrift für Soziologie, 33: , 266–284. Doi: 10.1515/zfsoz-2004-0401 |
53 | Tilly, C. ((2004) ). Terror, terrorism, terrorists. Sociological Theory, 22: , 5–13. Doi: 10.1111/j.1467-9558.2004.00200.x |
54 | van Buuren, J. ((2012) ). Performative violence? The multitude of lone wolf terrorism. Terrorism - An Electronic Journal and Knowledge Base, 1: , 1–23. Retrieved from https://www.terrorismelectronicjournal.org/app/download/5965468782/Jelle+van+Buuren+-+Performative+violence.pdf |
55 | Vossekuil B. , Fein R. A. , Reddy M. , Borum R. & Modzeleski, W. ((2002) ). The final report and findings of the safe school initiative: Implications for the prevention of school attacks in the United States. Washington: U.S. Secret Service and U.S. Department of Education. |
56 | Waldmann, P. ((2011) ). Terrorismus: Provokation der Macht [Terrorism: Provocation of power]. Hamburg: Murmann Verlag. |
57 | Wilner A. S. & Dubouloz, C. J. ((2011) ). Transformative radicalization: Applying learning theory to Islamist radicalization. Studies in Conflict & Terrorism, 34: , 418–438. Doi: 10.1080/1057610X.2011.561472 |




